How to hack telecom providers: analysis of a real attack

Image: Kevin Spencer | Flickr
Very often, cybercriminals use common mechanics for hacking, as well as weaknesses in the protection and vulnerability of IT systems. This thesis is confirmed by the example of one of the investigations into the attack on a telecommunications company from Eastern Europe - we will tell you more about it today.
')
The first stage of the attack: breaking the perimeter
As a rule, attacks on corporate infrastructure take place in two stages: first, the attacker hacks the network perimeter resources from the Internet, and then, once inside the internal network, it is fixed in the infrastructure and gains access to critical information and systems.
In this case, the attacker was able to identify publicly available services of the company and discovered a vulnerability in one of them - this was helped by the use of the Acunetix automated vulnerability scanner.
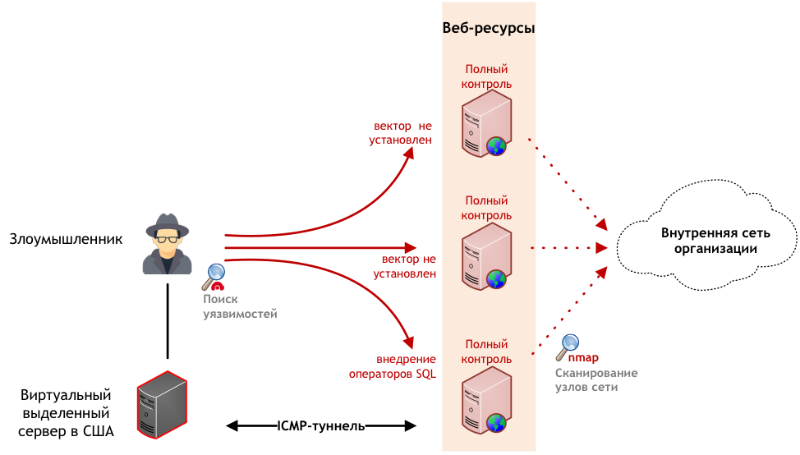
At the same time, the hacker practically did not hide his actions - when analyzing the incident, an abnormal increase in the number of requests was detected in the logs of the web server. But even such careless actions were not revealed by representatives of the company - the attack developed over the course of several months. There were a lot of suspicious activity records in the event logs, but nobody even analyzed them from time to time.
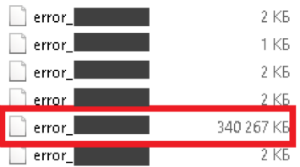
Web Server Error Logs
As a result of the scan, the attacker was able to find in a web application of the company a critical vulnerability, “the introduction of SQL statements.” Having exploited it, the hacker received not only root access to the database with accounts of all users, including administrators, but also the ability to execute commands on the server with DBMS privileges.
The attacked server was connected to the internal network, which opened access to its other resources. Network interaction during the attack was carried out via an ICMP tunnel — data was transferred to an external dedicated server leased in the United States. During the investigation, it turned out that the attacker had compromised only three web servers, having obtained access to them with local administrator rights — these machines became the entry points to the organization’s internal network.
The second stage: the development of attacks in the internal network
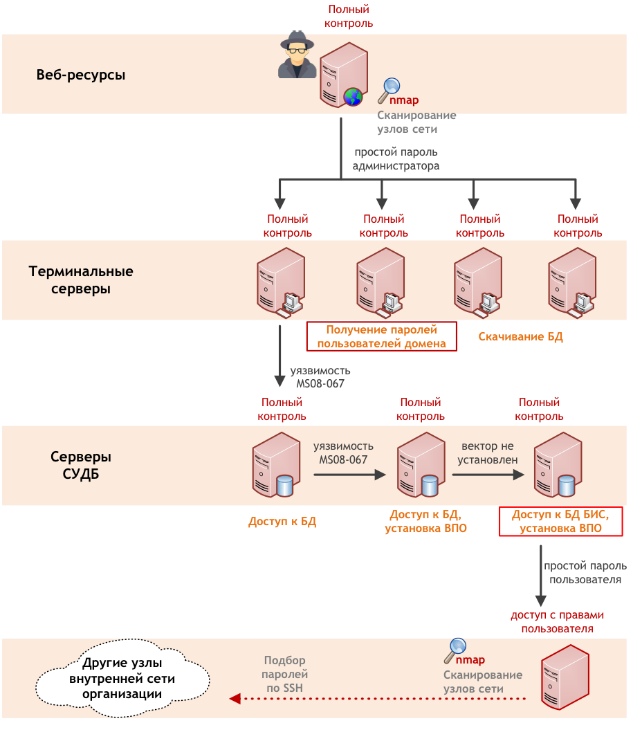
Having penetrated into the internal network, the attacker began to search for targets for the development of the attack - using the nmap network scanner, he was able to detect open connection interfaces for network services (TCP and UDP) on active nodes, identify software versions used for banners, and identify potentially vulnerable services. In parallel, he was engaged in the search for web applications and manual analysis of the company's resources.
Terminal servers were selected as the next target, providing users with resources for various tasks. Due to insufficient isolation of user sessions, the compromise of one account could lead to the compromise of accounts of other terminal server users. Because of the use of dictionary passwords for local administrator accounts, the attacker easily gained privileged access to several terminal servers at once and downloaded the contents of the databases hosted on them.
In addition, the privileges obtained on one of the servers allowed creating a memory dump of the lsass process - it corresponds to a service that is part of Windows and is responsible for authenticating local users of the computer. From the memory dump using the common mimikatz utility, a lot of credentials (including open passwords) of users authenticated on this server, including privileged ones, were extracted. Among the data obtained were service accounts to support terminal servers, as well as various domain accounts.
The privilege level obtained by the attacker allowed the attack to be easily developed using the credentials of legitimate users. In just one month, he managed to compromise a multitude of resources. For example, during the attack, information was obtained about the identifiers and password hashes of users of the Windows operating system (SAM database), configuration and addressing data of the network, information about user accounts, cryptographic keys of base stations, and other information.
Next, the attack developed in the direction of several servers running an outdated version of Windows - they were based on databases and LSI resources. To obtain anonymous access with system privileges to these servers, the attacker took advantage of the critical vulnerability MS08-067, details of which were published back in 2008, at the same time a public exploit was published. The servers were completely compromised, and the contents of the databases were stolen.
Investigation
The incident was revealed when the attack had already been developing for a long time - the company's specialists noticed numerous attempts to select SSH credentials for internal nodes from compromised DBMS services registered on weekends. At the first stage of the investigation, they identified the compromised resources on their own, and then involved specialists from Positive Technologies. The investigation revealed that by this time the attacker had access to the internal nodes of the corporate network for 5 months already.
Emergency measures, which included changing passwords for compromised accounts, as well as turning off or isolating compromised infrastructure, made it possible to stop the development of the attack. At the same time, it continued until all the identified channels of interaction between the intruder and sites on the Internet, from which the attack was conducted, were not blocked. However, all this does not exclude the fact that an attacker may have an alternative way of accessing the network.
How could problems be avoided
The attack affected key divisions of the organization, with a high probability that the interests and data of the organization’s clients were affected. But with all this, the attack could have been easily prevented if the protection of corporate resources were at a higher level.
For example, if centralized monitoring was implemented by the affected organization using the Security Event Correlation and Consolidation System (SIEM) system , the security service would receive timely notification of events related to the launch of the attack and be able to take the necessary measures to prevent the incident.
Reflecting the attack even at the stage of an attacker's hacking to search for vulnerabilities could be a firewall application level (WAF) - for example, PT AF . Such a tool allows you to block hacking attempts and identify chains of development of real attacks, transfer information about the events to the SIEM to notify security personnel and the subsequent rapid response.
The risks of such incidents can be minimized by introducing well-known information security measures, including analyzing the security of web applications and eliminating found vulnerabilities, introducing a strict password policy, applying current OS versions, as well as network segmentation and strict access control.
The full report on the results of the investigation of the described incident is available at: www.ptsecurity.com/upload/corporate/ru-ru/analytics/Telecom-Incident-Investigation-rus.pdf
Source: https://habr.com/ru/post/323292/
All Articles