Ransomware Development Projections for 2017
Each of us remembers 2016 in our own way. Physicists - the discovery of gravitational waves predicted by Albert Einstein, politicians - conflicts in the Middle East, musicians - the Nobel Peace Prize to Bob Dylan. IT security experts 2016 remembered the incredible surge of extortionist programs that made not only specialists, but also ordinary citizens learn the answer to the question " What is ransomware? ".

Now it's 2017 in the yard, and there is no doubt that ransomware aka extortion programs will become even more dangerous and will continue their attack on user data. All users will be in danger, and either you or your friends may face this threat tomorrow.
')
“Warned, it means armed”, - we thought, conducted a detailed analysis of one of the latest programs of extortionists, and also prepared a small forecast for the coming year.
I want to start with the forecast, and the “sweet”, in the form of a detailed analysis of the ransomware program, we will leave for later:
2016 was a tough year, but at least extortionists didn’t become the terrible weapon they would become in 2017 and which would be successfully used to blackmail celebrities, government agencies and millions of consumers.
And now, as promised earlier, the dessert is “DeriaLock, seasoned with comments from Acronis”. This ransomware program has several versions. The Christmas version of DeriaLock was mentioned on the BleepingComputer website, and on December 26, 2016 Karsten Hahn from G-Data found another newer version. It is on the latest version of DeriaLock (MD5: 0a7b70efba0aa93d4bc0857b87ac2fcb ) that we decided to stop our attention. We found that it not only blocks the computer, but also encrypts files and, if the user tries to solve the problem by “classic” restarting the computer, deletes them.
The extortioner DeriaLock consists of three functional parts: a screen lock, which first appeared in the Christmas version, a block-encoder and a file deletion module. If you are interested in how the screen lock works, then the detailed information is on BleepingComputer, we will consider the last two parts of the program - the block-encoder and the module for deleting files.
DeriaLock is a .NET application written in Visual Basic and obfuscated. It should be noted that the number of VB.NET encoder blockers has increased significantly over the past few months, which may be due to the opening of access to the source code of the program for educational purposes.
First, note that DeriaLock requires administrator and .NET Framework 4.5 access rights. The user will be asked to confirm an increase in access level if user account control is enabled.
DeriaLock encrypts files using AES-256 symmetric encryption within the following folders:
The block encoder contains a complex password that is used to calculate the 256-bit AES encryption key and the 16-bit initialization vector, which allows you to decrypt files without paying the money to the extortionists.
To create an encryption for the day The first 32 bytes of the hash are the encryption key, the next 16 bytes are the initialization vector.
When the encryption process is completed, the user receives the following message:
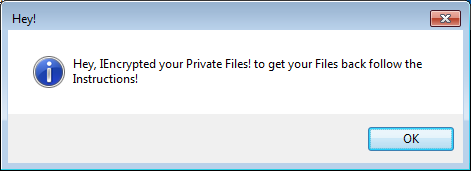
Then DeriaLock shows a message about how to recover files and unlock the system. He also warns the user that trying to solve a problem by restarting the computer may result in the deletion of all files:

Unlike other types of ransomware programs, DeriaLock requires a ransom of $ 30 USD / EUR to Skype’s “ARIZONACODE” account, which may make it the first ransomware program using this payment method.
After making the payment, DeriaLock downloads the file removal module (MD5: 2a95426852af058414bbc9ca236208dd ) from an external server:
Every second the program checks the contents of the file at:
If the digit in the file is “1”, then DeriaLock unlocks the system: deletes the file “C: \ Users \% user% \ AppData \ Roaming \ Microsoft \ Windows \ Start Menu \ Programs \ Startup \ LOGON.exe”, launches the file “Explorer. exe "and closes.
When a user enters a key to unlock in the proposed form, DeriaLock contacts the external server and checks whether the corresponding txt file with the user ID is on the server, for example:
http://arizonacode.bplaced.net/HF/SystemLocker/UNLOCKKEYS/f5515aff329218c79cac09122bd970f2.txt
If there is such a file, the program reads the key from the file and compares it with the key entered by the user in the form. If the two keys match, the computer is unlocked, and the files are decrypted.
If the user decides to restart the system, the file deletion module is activated during system boot:
It also requires admin rights to run.


To protect itself, DeriaLock stops the following processes:
When the system reboots, the loaded file removal module also stops the following processes:
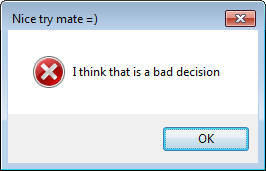
When a user tries to stop an ransomware program, for example, using the Alt-F4 key combination, DariaLock blocks such attempts and displays the following sarcastic message:
Obviously, more than one developer participated in the creation of DeriaLock. The version we are reviewing has an additional machine on the white list, which is absent in previous versions:

As we said above, this malware, even in its latest version, remains fairly simple and allows you to recover your files without paying the ransom. However, we want to emphasize that this still requires some knowledge and skills, so the actions described below will have to be done at your own peril and risk. We warn you that in case of an error you may lose all your data.
To unblock an infected system, proceed in accordance with one of the following scenarios:
If Windows is running in safe mode:
If safe mode is not activated:
A safer way is to create a proxy server to intercept C & C requests from the infected computer.
To decrypt files, proceed in accordance with one of the following scenarios:
or
Acronis Active Protection is able to detect and protect your system from the extortion program DeriaLock. This innovative technology, first used in Acronis True Image 2017 New Generation, is based on behavioral heuristics and easily identifies and stops the malicious activity of DeriaLock. It also allows the user to automatically recover any affected files.
→ Learn More About Acronis Active Protection

Now it's 2017 in the yard, and there is no doubt that ransomware aka extortion programs will become even more dangerous and will continue their attack on user data. All users will be in danger, and either you or your friends may face this threat tomorrow.
')
“Warned, it means armed”, - we thought, conducted a detailed analysis of one of the latest programs of extortionists, and also prepared a small forecast for the coming year.
I want to start with the forecast, and the “sweet”, in the form of a detailed analysis of the ransomware program, we will leave for later:
- The epidemic of ransomware programs will continue to grow exponentially. If in 2016 extortion programs brought about $ 1 billion to their creators, in 2017 this amount will increase to $ 5 billion. The number of different families of ransomware programs will grow significantly, and new “strains” will appear at a staggering rate.
- Because extortionists will become one of the most common types of malware, and the risks of punishment for their distribution will decrease, this will turn out to be a very profitable business. Suppliers of security software, in turn, will need to continue the fight against criminals, who will have at their disposal ever larger amounts and the most advanced technologies.
- The number of "distributors" will continue to grow. One of the principles of the ransomware program is copying the SaaS model (software as a service) - attracting a huge number of small "distributors" whose sole purpose is to infect target computers. It is extremely easy to become a “distributor”; all you need to do is just have a computer and be ready to break the law by making money from users. It is so simple that it does not even require good technological knowledge or the ability to write malware.
- Technology distribution programs, extortionists will be even more insidious and cunning. At the end of 2016, one of the most ingenious distribution schemes became known today: the user was promised to give a free decryption key if he infected two other users with malware. Most likely, the criminals got this idea from the “Bell”, a popular horror film of the early 2000s. The most common type of attack will remain various phishing scams, which will become even more personalized and effective. Instead of blockers, extortionists will use encryptors more often, as more and more users are beginning to understand that blockers can be easily defeated.
- In 2016, cloud storage solutions for backup copies of data were actively used to protect against ransomware programs that attack local storage. In 2017, new versions of extortionists will learn to work in the clouds and will begin to attack, including cloud storage. Users will have to look for cloud providers that can protect data from such attacks.
- Also, there will be new methods of pressure on the victims to make them pay "ransom" for their data. Today, technology allows you to increase the size of the ransom and delete files every hour until the victim pays. In the future, extortion programs will become even more sophisticated. They will begin to threaten the dissemination and publication of confidential (for example, medical or financial), as well as compromising data (search for stories and intimate photographs), if the victim does not pay the ransom immediately.
- First, victims will pay faster, but this trend will quickly fade away when it becomes apparent that the criminals do not keep their word, do not send the decryption key for the ransom, and do not stop their attacks.
- Ransomware developers will continue to invest heavily in developing more resilient code that can bypass all security systems. Fewer security vendors will offer free descramblers, as ransomware developers will learn to use the most reliable encryption schemes.
- Antiviruses, attentiveness and caution of users, white / black lists and other means of protection will not be able to quickly overcome their limitations in the fight against ransomware programs. Nevertheless, new means of protection will appear, and machine learning will become an important weapon in the fight against rapidly developing types of ransomware programs.
- Compliance with strict data protection rules, including the regular creation of local, cloud and autonomous data backups, will remain the only reliable tool to combat extortion programs.
2016 was a tough year, but at least extortionists didn’t become the terrible weapon they would become in 2017 and which would be successfully used to blackmail celebrities, government agencies and millions of consumers.
And now, as promised earlier, the dessert is “DeriaLock, seasoned with comments from Acronis”. This ransomware program has several versions. The Christmas version of DeriaLock was mentioned on the BleepingComputer website, and on December 26, 2016 Karsten Hahn from G-Data found another newer version. It is on the latest version of DeriaLock (MD5: 0a7b70efba0aa93d4bc0857b87ac2fcb ) that we decided to stop our attention. We found that it not only blocks the computer, but also encrypts files and, if the user tries to solve the problem by “classic” restarting the computer, deletes them.
The extortioner DeriaLock consists of three functional parts: a screen lock, which first appeared in the Christmas version, a block-encoder and a file deletion module. If you are interested in how the screen lock works, then the detailed information is on BleepingComputer, we will consider the last two parts of the program - the block-encoder and the module for deleting files.
DeriaLock is a .NET application written in Visual Basic and obfuscated. It should be noted that the number of VB.NET encoder blockers has increased significantly over the past few months, which may be due to the opening of access to the source code of the program for educational purposes.
First, note that DeriaLock requires administrator and .NET Framework 4.5 access rights. The user will be asked to confirm an increase in access level if user account control is enabled.
Encryption functionality
DeriaLock encrypts files using AES-256 symmetric encryption within the following folders:
- Desktop
- Downloads
- My documents
- My music
- My pictures
- D: \
The block encoder contains a complex password that is used to calculate the 256-bit AES encryption key and the 16-bit initialization vector, which allows you to decrypt files without paying the money to the extortionists.
To create an encryption for the day The first 32 bytes of the hash are the encryption key, the next 16 bytes are the initialization vector.
When the encryption process is completed, the user receives the following message:

Then DeriaLock shows a message about how to recover files and unlock the system. He also warns the user that trying to solve a problem by restarting the computer may result in the deletion of all files:

Payment
Unlike other types of ransomware programs, DeriaLock requires a ransom of $ 30 USD / EUR to Skype’s “ARIZONACODE” account, which may make it the first ransomware program using this payment method.
Communication with C & C
After making the payment, DeriaLock downloads the file removal module (MD5: 2a95426852af058414bbc9ca236208dd ) from an external server:

Every second the program checks the contents of the file at:
arizonacode.bplaced.net/HF/SystemLocker/unlock-everybody.txt
If the digit in the file is “1”, then DeriaLock unlocks the system: deletes the file “C: \ Users \% user% \ AppData \ Roaming \ Microsoft \ Windows \ Start Menu \ Programs \ Startup \ LOGON.exe”, launches the file “Explorer. exe "and closes.
When a user enters a key to unlock in the proposed form, DeriaLock contacts the external server and checks whether the corresponding txt file with the user ID is on the server, for example:
http://arizonacode.bplaced.net/HF/SystemLocker/UNLOCKKEYS/f5515aff329218c79cac09122bd970f2.txt
If there is such a file, the program reads the key from the file and compares it with the key entered by the user in the form. If the two keys match, the computer is unlocked, and the files are decrypted.
File Removal Module
If the user decides to restart the system, the file deletion module is activated during system boot:
C: \ Users \% user% \ AppData \ Roaming \ Microsoft \ Windows \ Start Menu \ Programs \ Startup \ LOGON.exe
It also requires admin rights to run.


Self defense
To protect itself, DeriaLock stops the following processes:
- utilman
- procexp
- procexp64
- procexp32
- certmgr
- control
- cscript
When the system reboots, the loaded file removal module also stops the following processes:
- taskmgr
- regedit
- msconfig
- cmd
- explorer
When a user tries to stop an ransomware program, for example, using the Alt-F4 key combination, DariaLock blocks such attempts and displays the following sarcastic message:

Authorship
Obviously, more than one developer participated in the creation of DeriaLock. The version we are reviewing has an additional machine on the white list, which is absent in previous versions:

How to unlock and decrypt
As we said above, this malware, even in its latest version, remains fairly simple and allows you to recover your files without paying the ransom. However, we want to emphasize that this still requires some knowledge and skills, so the actions described below will have to be done at your own peril and risk. We warn you that in case of an error you may lose all your data.
To unblock an infected system, proceed in accordance with one of the following scenarios:
If Windows is running in safe mode:
- Hard-reset the computer.
- Start Windows in safe mode.
- Delete the file:
C: \ Users \% user% \ AppData \ Roaming \ Microsoft \ Windows \ Start Menu \ Programs \ Startup \ LOGON.exe
If safe mode is not activated:
- Hard-reset the computer.
- Open the BIOS.
- Install a suitable device from which you can run a backup system disk.
- Start the computer from the system backup disk.
- Delete the file:
C: \ Users \% user% \ AppData \ Roaming \ Microsoft \ Windows \ Start Menu \ Programs \ Startup \ LOGON.exe
A safer way is to create a proxy server to intercept C & C requests from the infected computer.
- Set the DNS record on the local DNS server “arizonacode.bplaced.net”, which will allow you to redirect all traffic to a local proxy server.
- Create a file with the number “1” in the root directory of the server:
/HF/SystemLocker/unlock-everybody.txt
To decrypt files, proceed in accordance with one of the following scenarios:
- Calculate the encryption key and initialization vector using the above password series and algorithm.
- Write a script that decrypts all files with the extension ".deria".
or
- Set the DNS record on the local DNS server “arizonacode.bplaced.net” that will redirect all traffic to the local proxy server.
- Create the following file with an arbitrary key in the root directory of the web server:
/HF/SystemLocker/UNLOCKKEYS/<ID>.txt - Enter the same key in the form and click on “Submit”.
With Acronis Active Protection, you'll be safe.
Acronis Active Protection is able to detect and protect your system from the extortion program DeriaLock. This innovative technology, first used in Acronis True Image 2017 New Generation, is based on behavioral heuristics and easily identifies and stops the malicious activity of DeriaLock. It also allows the user to automatically recover any affected files.
→ Learn More About Acronis Active Protection
Source: https://habr.com/ru/post/323288/
All Articles