How I set up new utilities for working with electronic signature in Linux

Let's talk a little about the means of electronic signature (EP) using domestic GOST-algorithms in Linux. Despite the fact that various tools and interfaces for working with ES in Linux are even better developed than in Windows, using them is not so easy.
This state of affairs has remained the last few years. But since the end of 2016, the situation has changed for the better. Two products appeared at once that allow you to work with an electronic signature according to the GOST standard and encrypt without using the console - these are Rosa Crypto Tool and Trusted eSign. Both of these cryptographic products use CryptoPro CSP for Linux. Therefore, before turning to the description of the products themselves, let's talk a bit about CryptoPro CSP.
')
CryptoPro CSP for Linux is an ambiguous product. On the one hand, this is one of the most common and powerful certified tools for working with cryptography in both Windows and Linux. On the other hand, it is not so easy for an ordinary person to use its interfaces, even in Windows. And in Linux, only the console interface is available. I hope that CryptoPro is aware of this situation, and in the future we are waiting for new beautiful and convenient interfaces for both Windows and Linux.
To set up we need:
- Favorite Linux distribution. I used Ubuntu Linux 16.04 LTS and ROSA Fresh GNOME R8;
- Certified version of CryptoPro CSP 4.0 R2 for Windows, UNIX and macOS;
- Rutoken EDS 2.0.
Setting "CryptoPro" CSP
Despite the fact that there are some quite good articles on setting up CryptoPro CSP under Linux (for example, here or here ), I will describe my version here. The main reason is that most of the instructions are written for the Crypto Pro CSP version 3.x. And the modern version of CryptoPro CSP 4.0 is not 100% compatible with 3.x. An additional reason is always nice to have full instructions for setting up in one place, and not to switch from one window to another.
Getting Started.
Download CryptoPro CSP for Linux from the official site of CryptoPro - www.cryptopro.ru/downloads
Unpacking CryptoPro CSP for Linux:
tar -zxf ./linux-amd64_deb.tgz Next we have 2 options - automatic installation and manual installation. Automatic installation is started with the command:
sudo ./install.sh or
sudo ./install_gui.sh Here we must pay tribute to the developers of "CryptoPro" - automatic installation for most distributions work out successfully. Although there are nuances. For example, if you are missing some packages, the installation will be completed successfully, although some functionality will not work.
If something went wrong, or for one reason or another you want to use the installation in manual mode, then you need to do:
dpkg -i ./cprocsp-curl-64_4.0.0-4_amd64.deb lsb-cprocsp-base_4.0.0-4_all.deb lsb-cprocsp-capilite-64_4.0.0-4_amd64.deb lsb-cprocsp-kc1-64_4.0.0-4_amd64.deb lsb-cprocsp-rdr-64_4.0.0-4_amd64.deb To install packages in ROSA, use urpmi , instead of dpkg -i .
Install the license for CryptoPro CSP for Linux and check that everything works fine:
cpconfig -license -set <_> cpconfig -license –view We should get something like:
License validity: XXXXX-XXXXX-XXXXX-XXXXX-XXXXX Expires: 3 month(s) 2 day(s) License type: Server. Setup of work with Rutoken EDS 2.0
We make a small digression. To work with electronic signature and encryption, we can not do without key pairs and certificates. Secure storage of private keys is one of the main security factors. But mankind has not yet invented more reliable means of storage than a token or a smart card. I will use Rutoken EDS 2.0, which has a certificate of the FSB and supports the work of both new and old guests.

To work with tokens in Linux, there are a lot of different tools and drivers. To describe all of these tools will need a separate article. Therefore, I will not describe in detail how it works, and why we need these particular packages.
Install packages to work with Rutoken EDS 2.0:
apt-get install libpcsclite1 pcscd libccid We also need to install CryptoPro CSP packages to support the work with tokens:
dpkg -i ./cprocsp-rdr-gui-gtk-64_4.0.0-4_amd64.deb ./cprocsp-rdr-rutoken-64_4.0.0-4_amd64.deb ./cprocsp-rdr-pcsc-64_4.0.0-4_amd64.deb ./lsb-cprocsp-pkcs11-64_4.0.0-4_amd64.deb We get a test certificate
Before you go directly to the work with the signature, you need to generate a key pair and create an electronic signature certificate. If you already have Rutoken with the CryptoPro container, then this part can be safely skipped.
We use the test center of the CryptoPro company at: https://www.cryptopro.ru/certsrv/
Create a certificate request with default settings.
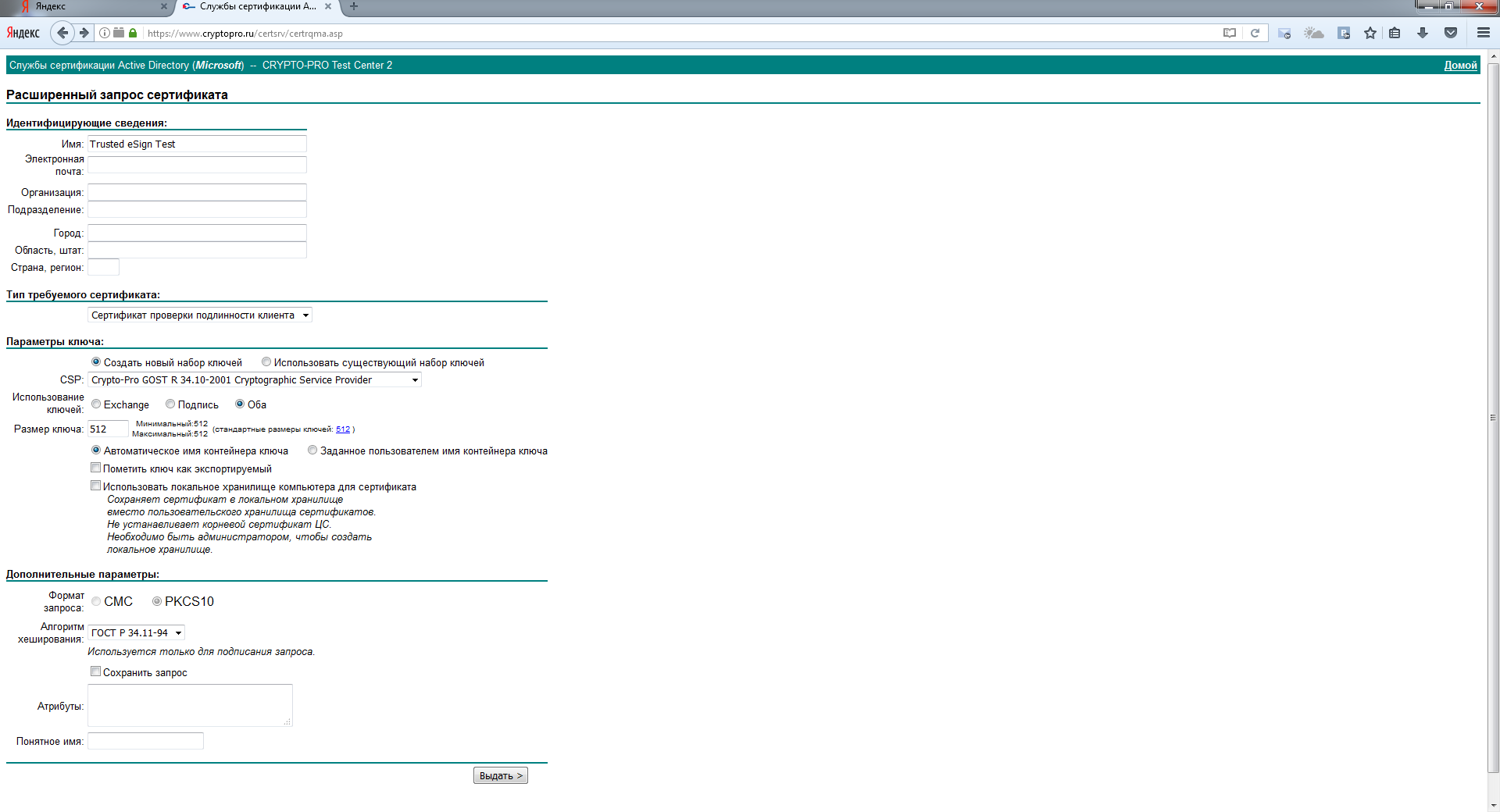
Verify that the certificate was received successfully.
To make sure that CryptoPro CSP saw the token successfully, we run:
list_pcsc We should get something like:
Aktiv Rutoken ECP 00 00 Now we check that the certificate on the token is seen successfully:
csptest -keyset -enum_cont -verifyc -fq We get:
CSP (Type:80) v4.0.9014 KC1 Release Ver:4.0.9842 OS:Linux CPU:AMD64 FastCode:READY:AVX. AcquireContext: OK. HCRYPTPROV: 13476867 \\.\Aktiv Rutoken ECP 00 00\822506788-dfcd-54c9-3a5e-e0a82a2d7f0 OK. Total: SYS: 0,020 sec USR: 0,160 sec UTC: 0,870 sec [ErrorCode: 0x00000000] We write information about this certificate in the CryptoPro certificate store:
csptestf -absorb -cert -pattern 'rutoken' Match: SCARD\rutoken_ecp_351d6671\0A00\62AC OK. Total: SYS: 0,010 sec USR: 0,140 sec UTC: 1,040 sec [ErrorCode: 0x00000000] Check that the certificate has been successfully stored in the repository:
certmgr -list -cert -store uMy Certmgr 1.0 (c) "CryptoPro", 2007-2010. program for managing certificates, CRLs and stores ============================================================================= 1------- Issuer : E=support@cryptopro.ru, C=RU, L=Moscow, O=CRYPTO-PRO LLC, CN=CRYPTO-PRO Test Center 2 Subject : CN=Trusted eSign Test Serial : 0x120019F5D4E16D75F520A0299B00000019F5D4 SHA1 Hash : 0x016f443df01187d5500aff311ece5ea199ff863e SubjKeyID : 204e94f63c68595e4c521357cf1d9279bff6f6e5 Signature Algorithm : 34.11/34.10-2001 PublicKey Algorithm : 34.10-2001 (512 bits) Not valid before : 22/02/2017 10:53:16 UTC Not valid after : 22/05/2017 11:03:16 UTC PrivateKey Link : Yes Container : SCARD\rutoken_ecp_351d6671\0A00\62AC Provider Name : Crypto-Pro GOST R 34.10-2012 KC1 CSP Provider Info : ProvType: 80, KeySpec: 1, Flags: 0x0 CA cert URL : http://testca.cryptopro.ru/CertEnroll/test-ca-2014_CRYPTO-PRO%20Test%20Center%202.crt OCSP URL : http://testca.cryptopro.ru/ocsp/ocsp.srf CDP : http://testca.cryptopro.ru/CertEnroll/CRYPTO-PRO%20Test%20Center%202.crl Extended Key Usage : 1.3.6.1.5.5.7.3.2 ============================================================================= [ErrorCode: 0x00000000] This completes the basic setup, and we can begin to sign or encrypt files using various means. We turn to why this article was conceived.
Signed by means of CryptoPro CSP
CryptoPro CSP includes the csptestf utility, which allows you to perform various cryptographic operations. As I wrote above, this utility has 2 drawbacks:
- Lack of good documentation;
- No graphical user interface.
You can sign with the command:
csptestf –sfsign –sign –in < > -out < > -my 'Trusted eSign Test' –detached –alg GOST94_256 Here,
my is the parameter in which you need to specify the Common Name part of the certificate for signing;
detached - allows you to create a detached signature;
alg GOST94_256 - sets the hash algorithm that will be used when creating the signature.
You can get more detailed information on the possible parameters by running the command:
csptestf –sfsign Such an interface is great for a trained user or to automate script operations.
Now let's talk about utilities that make life easier for ordinary users when working with signature and encryption in Linux.
Rosa Crypto Tool
As the name suggests, this is a utility for working with electronic signature and encryption for the ROSA Linux distribution. The utility is currently available in the Rosa Linux and Alt Linux repositories.
This utility is developed by one person - Mikhail Voznesensky. It has a simple, but user-friendly interface. At the moment, the utility is in active development - since November 2016, I managed to test three versions. The latest version available at the time of writing is 0.2.2. Now the utility only supports working with CryptoPro CSP for Linux, however, support for other crypto-providers will be added soon.
What's inside? The utility is written in Python using PyQt4 for a graphical interface.
You can install it using the "Program Management" in Rosa Linux.
Insert the token and run the utility.
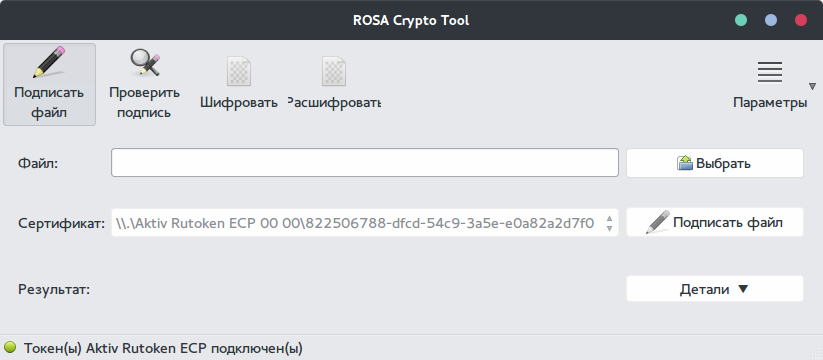
We see that the token was determined successfully and our certificate was found.
The program interface is so simple that it does not make sense to describe and show all its functions in the article. Let's just sign the file.
Select the file and click “Sign the file”. We get this warning.
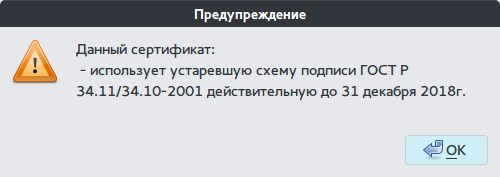
Click "OK" and get information that the file was signed successfully.
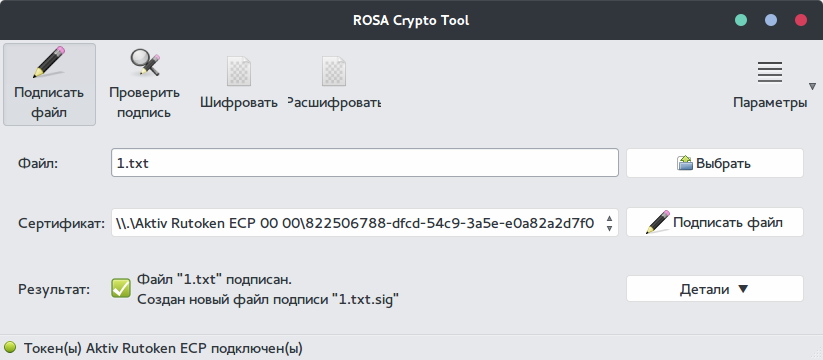
The main advantage of this utility is that it is completely free, in contrast to our next product.
Compared to using CryptoPro CSP from the console:
+ Much easier to use;
- There are no different signature options.
The source code of the program is available in the public repository on ABF:
abf.io/uxteam/rosa-crypto-tool-devel
The version control system used by the SEC IT ROSA is integrated into the build environment and is based on Git. You can easily use any git client.
I hope the developers of other domestic Linux distributions, such as Astra Linux, GosLinux and others, will add rosa-crypto-tool packages to their distributions.
Trust eSign
The second product we’ll talk about is Trusted eSign from Digital Technologies. It is known in the Russian market of information security as a developer of tools for working with signature and encryption for the Windows operating system - "CryptoARM".
The main thing is not to confuse this product with Trusted.eSign - web-service for working with the signature of the same company.
Finding a product on the websites of Digital Technologies is not easy. A small description is in the store http://www.cryptoarm.ru/shop/trusted_esign , the product can also be downloaded in the section “Download Center” on the site trusted.ru - https://trusted.ru/support/downloads/?product= 133
Unfortunately, the product is currently available only as a deb package for 64-bit systems. What is the reason for such a restriction is not clear. Let's hope that in the near future the company will release the rpm package, as well as versions for 32-bit Linux distributions.
We download the deb-package from the official site and install it with the command:
dpkg –i ./trustedesign-x64.deb Launch Trusted eSign.

It is immediately evident that the development was not without a designer. No sarcasm. All actions are done simply and logically, and the appearance pleases the eye. Unfortunately, most of the tools and programs in the field of information security from Russian developers are developed without the involvement of UX-specialists and designers and make their users suffer and cry with bloody tears. It seems that other means of information security simply can not be. “Digital technologies” refute this. Payment for beauty and convenience - the need to pay for a license.
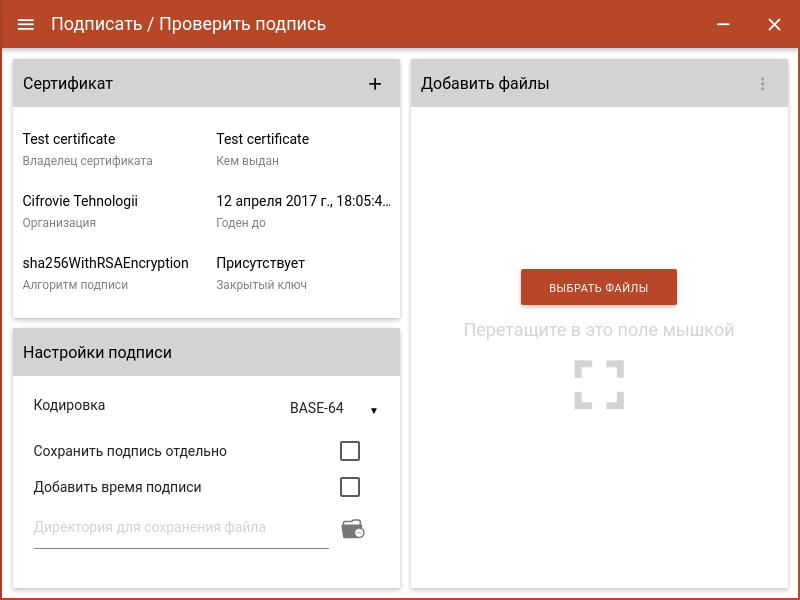
But back to the signature.
Select the section “Electronic Signature”:
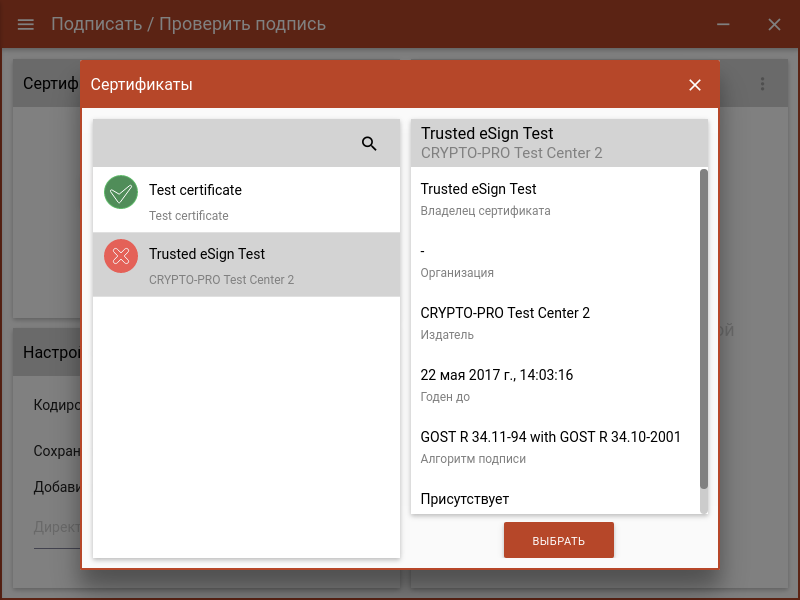
Choose "Certificate for signature":
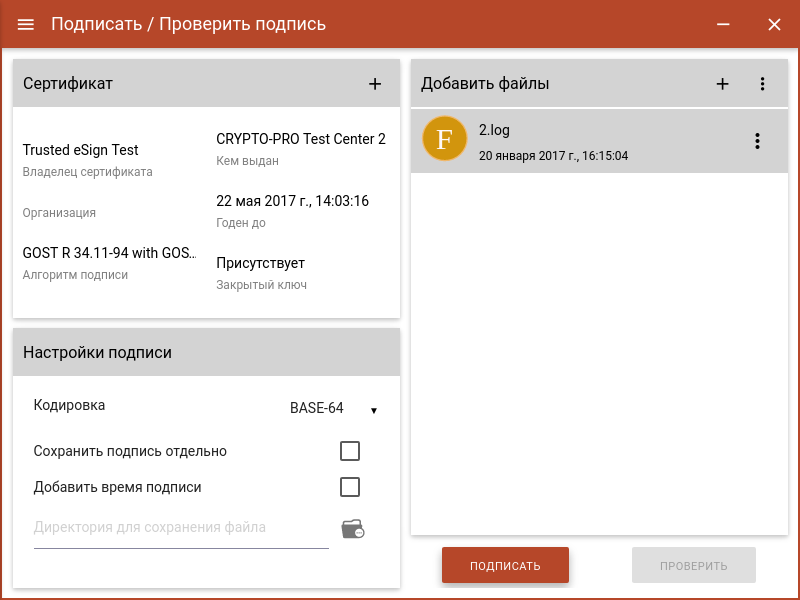
Select the files for the signature and click "Sign":
What is under the hood? I will quote from the site: “The application is created on a modern Electron engine, the OpenSSL library is used to invoke cryptographic operations. Compatible with CryptoPro CSP 4.0 and supports all the cryptographic algorithms implemented in it. For those who are not yet aware of Electron, this is a framework for creating desktop applications on the node.js platform.
Compare Trusted eSign with Rosa crypto tool:
+ More convenient and beautiful interface
- Paid license
Summary
Summarize. In late 2016 - early 2017, there has been a good progress in the means of working with electronic signatures for Linux. Information security begins to turn its face to the user, and every year less and less action is required for such a simple action as signing or encrypting a file using domestic algorithms.
I would like to further note this development of domestic products, given the current trend to replace Windows with Linux in state and municipal organizations. As part of this trend, the use of cryptographic information protection tools for Linux becomes relevant. Good and convenient products of Russian developers will help government organizations and structures to work normally and meet the requirements for import substitution.
Such a development can not but rejoice, especially when it happens under Linux.
PS
Surely there are quite a few users, especially Linux users, who believe that console utilities are enough. As well as information security specialists, who believe that design and convenience are an excess of information security. But I can not agree with them. Console utilities are undoubtedly ideal for automation. But for most users it’s more convenient to work with graphical interfaces. Even in Linux.
Source: https://habr.com/ru/post/323170/
All Articles