How effective are the next-generation information security solutions?

Recently, more and more talk about the security solutions of the "next generation", built on Big data using artificial intelligence. But how effective are such solutions? And how to evaluate them? Let's try to figure out the example of Adaptive Defense 360 .
Artificial Intelligence and Big Data are now fashionable words that are used to describe various products in the field of information technology, including information security. The increasing use of these technologies is explained by the fact that, on the one hand, huge amounts of information need to be processed (and these volumes will be constantly growing) for comparing and comparing data, identifying cause-effect relationships, etc. under various sections, and on the other hand , it is required to teach machines to think, think and analyze “as a person”. The latter, among other things, is required in order to more flexibly assess certain situations - this will allow adapting the work of the security solution to the specific needs (and specific user) and, most likely, increase the efficiency of the work of such a solution.
')
Gradually, solutions using artificial intelligence and Big Data began to form a class of “next generation” solutions. Is the game worth the candle?
Who is stronger: attack or defense?
This question will always be relevant, perhaps, always, because our world is in a state of constant development, and the law “for every force of action is a force of resistance” has not been canceled by anyone. Cyber-criminals are improving the techniques and methods of hacking and infection systems, and manufacturers of information security solutions are improving their products to provide a high level of security in the new reality. In general, this is an ongoing war.
We are increasingly seeing various examples of advanced threats, when they are “masked” among other, quite legitimate processes. There were cases when no malicious program was used to attack at all. Moreover, attacks (especially targeted attacks) become “masterpieces” of martial art, when the system is not compromised instantaneously, and the process itself represents a huge number of iterations (at first glance, by the way, quite legitimate) with all sorts of “false” interference. So in the end, it is already impossible to make out what it was from ...
But there are coders, who also do not stand still. After all, it would seem that the operation of archiving files using a password is a completely legitimate operation. Only if it is consciously carried out by the PC user himself. And it would be good if the machine understands who launches this process - the person behind the keyboard, or is it the result of a chain of some program actions.
It turns out that it is necessary to analyze not so much the files themselves and the processes they launch, but the whole chain of interrelated events taking into account the peculiarities of the PC user and the applications launched by him. Those. protection must be adapted to the enterprise.
Do I need signatures?
This question can be answered in two ways: both YES and NO.
On the one hand, signatures are needed so that even before the launch, it is possible to identify the malicious file unequivocally by notifying the user in advance (at the time of downloading, copying, attempting to launch). But let's not forget that signatures exist only for known threats. And what to do with unknown threats? After all, the main problem is precisely to defend against them.
Well, add heuristics and behavioral analysis. But their traditional implementation, again, analyzes only a specific process in isolation from all other processes interrelated with it. Moreover, what to do if the attack does not use a single malicious program? If there is no malicious behavior?
There are still "sandboxes". But again, modern threats have learned to recognize them. As a result, the threat of falling into the sandbox does not manifest its malicious nature. And only after launching it in a real environment ...
You can make white lists of allowed programs (applications, executable files, libraries), and the rest is banned. And remove admin rights. But not always this can be realized, because this can have a very negative impact on the work of certain groups of employees (information security solutions should help to work safely, and not interfere with work in principle). Plus white lists, ideally, should be dynamic and automatically reclassified if necessary.
Well, how then to provide effective and automated protection against unknown threats?
New security model
In addition to the above technologies, it seems unrealistic to solve the set task without artificial intelligence and analyzing a huge amount of information. It is for this reason that the solutions of the “next generation” are based on a new security model based on three basic principles: continuous monitoring of all running processes on the device, automatic correlation of all processes and their classification in terms of severity, and, if necessary, in-depth analysis of behavior by a technical expert . Those. combination of artificial and human intelligence.
As an example, let us take the first and, it seems, the only SaaS solution of the “next generation” that united on a single platform EPP- and EDR-systems using these technologies - this is Adaptive Defense 360, which appeared on the market in 2015. So, hundreds of his sensors, working on each protected computer, in real time collect the required information on each active process and transfer it to the Big Data cloud platform, where it is carefully analyzed using artificial intelligence technologies. Comparing the data for each process, the system automatically establishes a causal relationship: the emergence of each process (that is, what preceded it), the essence of the process itself, and other processes launched by it. Thus, it is possible to determine the entire life cycle of a large process consisting of a set of independent, but it turns out, interrelated processes. In addition, artificial intelligence also tries to take into account the features of the protected object and some nuances of its use.
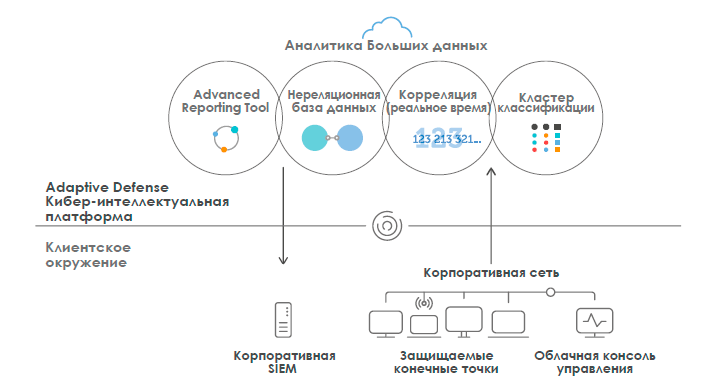
If the process cannot be automatically classified (and the number of such cases is negligible), then information security experts are involved.
As a result, the user is offered three modes of operation of the enhanced protection module against unknown threats:
- Audit: the solution only monitors all processes without any blocking.
- Hardening: the solution blocks all unclassified processes of executable files and applications downloaded from the Internet
- Lock: the solution blocks all unclassified processes of any executable files and applications
In this article we will not dwell in detail on the "insides" of the system: in more detail about the security model you can read here , and about what information is transmitted to the cloud - here .
We are interested in something else: what is the real effectiveness of this solution and how expensive it is.
What to do with new cryptographers?
As an example, we give the case of Spora. In January, our colleagues from G-Data published an interesting analysis of the new coder Spora. It seems that for the first time it was noticed by the guys from ID Ransomware , and basically its distribution zone is Russia. A link with a detailed analysis of one of the samples sent to VirusTotal was published on the forum. This is an HTA file that none of the anti-virus engines presented there had at that time detected: neither Panda Security, nor G-Data, nor anyone else.
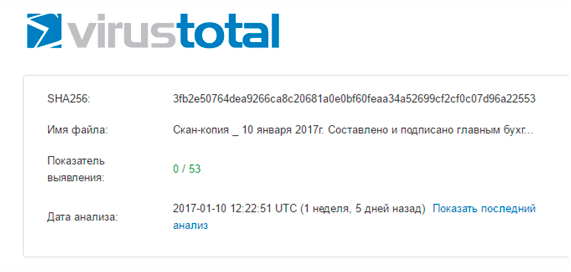
Does this mean that all 53 participants in VirusTotal are not able to detect and block this new threat? Not certainly in that way. This means that at the time of analysis, no one created a signature to locate a file that, in fact, “lives” very little time. But the main thing is to protect users and prevent their infection. And it turns out that it is absolutely not necessary to create signatures to protect users, as in this case under consideration.
After checking the information in our cloud, we saw that the system was able to observe the actions of Spora and, if necessary, block this new “malware” from the first moment it appeared, without creating any signatures for it. We can confirm that indeed, the overwhelming majority of cases of Spora detection were in Russia, although we have seen several cases in Japan.
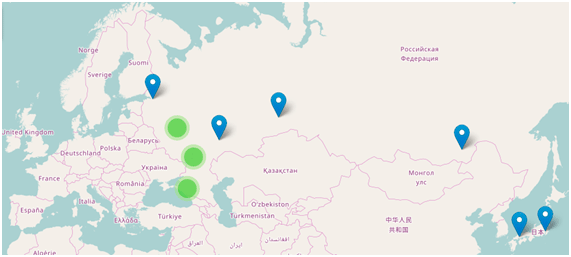
By the way, here is a list of hashes that we saw at that time:
• 312445d2cca1cf82406af567596b9d8c
• acc895318408a212b46bda7ec5944653
• c1f37759c607f4448103a24561127f2e
• c270cf1f2cfeb96d42ced4eeb26bb936
Previous assessment methods are not effective.
Whenever it comes to the effectiveness of an anti-virus, most often it is evaluated when trying to run a malicious file on a computer. If it is blocked, then the antivirus is effective; if not, then it is not effective. By the way, for such rapid tests are often used projects such as VirusTotal. We have nothing against this project, it is necessary and useful as one of the tools of such a rapid test. But more and more often there are cases when a test on the same VirusTotal shows that such an antivirus does not detect this threat, although in reality it still blocks malicious actions triggered by this file.
The fact is that protection is checked when the threat hits the computer, and if the security solution does not detect it at that moment (download, copy), then this does not mean that the solution is ineffective. Users want to stop malicious files before they are launched, but this is the error of the approach itself in modern realities. Alas, it’s impossible to know all the files. It is no longer enough to detect threats at the file level, relying only on signatures, a sandbox and a limited set of proactive rules.
Adaptive Defense 360, tracking, matching, correlating and analyzing the entire chain of processes that were “born” on this computer after running any executable file or application, will be able to block those that are unclassified. At the same time, the system will know which files have become the progenitors of these malicious processes, and therefore will be able to correctly reclassify these original files in real time, increasing the efficiency of future scans. Again, the system works dynamically, and if in the future such malicious processes disappear, then the files themselves will be classified differently.
Ultimately, if an attack consists of multiple operations, then if you block individual suspicious and malicious operations that are part of it, the whole attack will not achieve the goals set for it.
Testing Adaptive Defense 360 in AV-Comparatives
One and a half years after Adaptive Defense 360 entered the market, in December 2016, the independent test lab AV-Comparatives conducted its own testing of Adaptive Defense 360 in order to study its performance in real conditions. What are the results?
Guided by the manufacturer’s recommendations, AV-Comparatives experts installed a small agent, Adaptive Defense 360, on “experimental” computers, for which employees worked for some time in their usual daily routine. Thus, the product, whose extended protection was working at that time in audit mode, was able to recognize the “normal” behavior on all computers, classifying all the processes that were started.
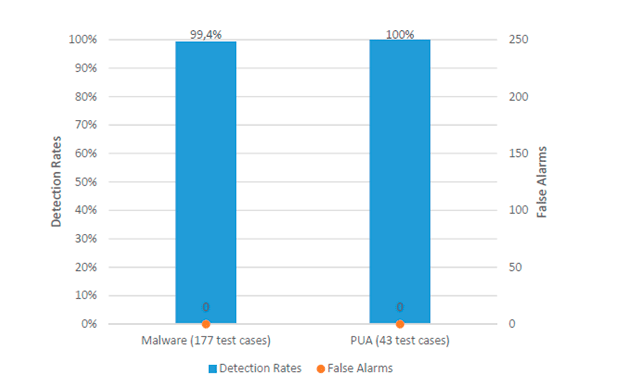
At the end of the adaptation period (Panda recommends 2-3 weeks), an effectiveness test was performed against unknown threats. For this purpose, 177 new malicious websites were used, on which unknown ciphers, backdoors, password hijackers, worms, viruses, trojans, etc. were located. Adaptive Defense 360 blocked 176 threats, and the last unknown threat (password hijacker) was automatically blocked during testing as a result of the analysis of its processes. Finally, all 43 unknown potentially unwanted programs were blocked. No false positives were detected during the testing period. Below is a graph from the AV-Comparatives report.
In addition to the high effectiveness of Adaptive Defense 360 against unknown threats, AV-Comparatives experts also noted the ability to view expert information on each of the incidents. In particular, the real-time life cycle of each incident is shown in the product console, allowing the administrator to see all the processes associated with this incident and the results of their classification. Below is a screenshot with information on the threat life cycle and the results of blocking.

This information is also supplemented by a schedule of activity of the registered processes. In particular, the graph shows all the relationships between the various events and their participants in the incident. Moreover, it is possible to familiarize yourself with the entire chronology of the incident by viewing the development of the incident in animated form.
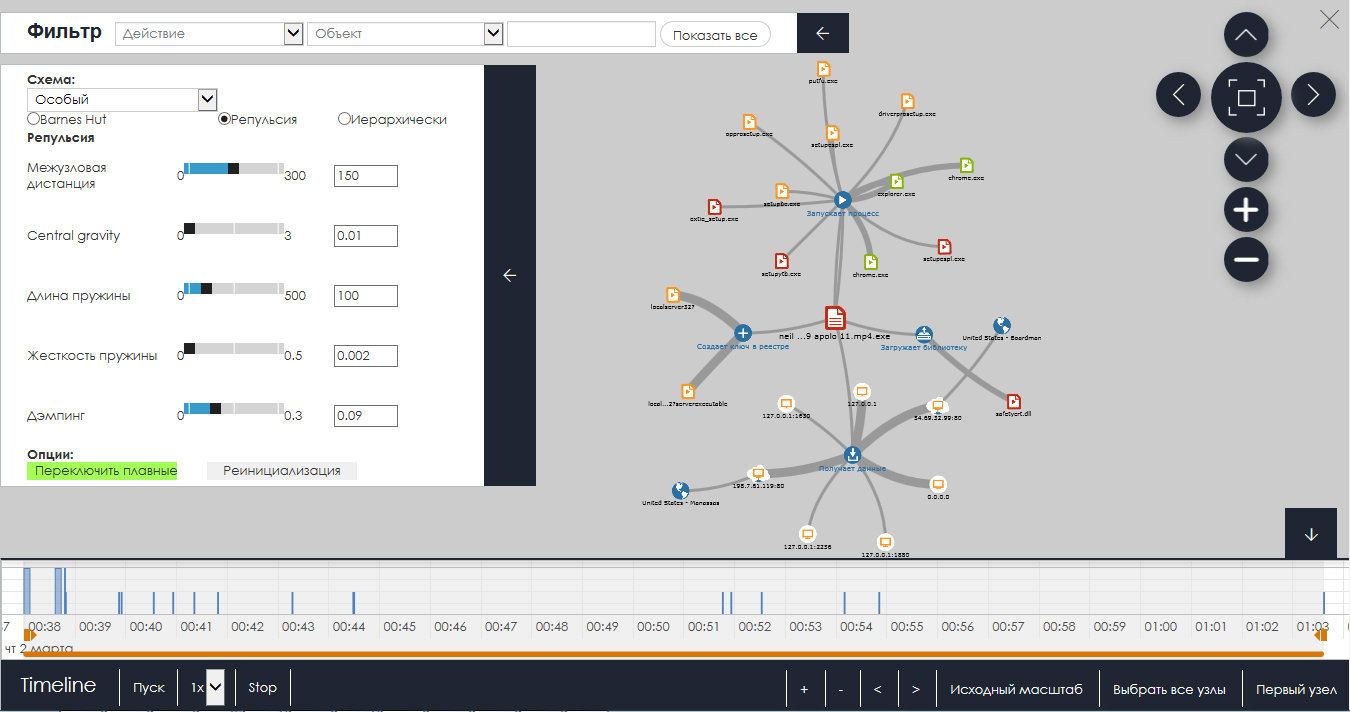
In addition, in their report, AV-Comparatives experts also mentioned the additional utility Advanced Reporting Tool, which in a sense is a simplified model of the SIEM system and is available to users of the corresponding Adaptive Defense 360 license. In due time, we already wrote in detail about this tool. which allows you to get a detailed expert analysis of each process and about who uses computers and how, and what data they are trying to access.
You can read more about the AV-Comparatives report here .
Issue price
Security solutions of the “next generation” are certainly more expensive than traditional antivirus solutions, especially if they (as in the example with Adaptive Defense 360) combine both traditional EPP technologies and EDR technologies with advanced protection features.
For comparison, if traditional corporate anti-virus protection costs between 500 and 1500 rubles per device for 1 year (depending on the number of licenses, product functionality and other delivery conditions), then new solutions may be 2-3 times more expensive.
For example, the Adaptive Defense 360 cost varies from 1000 to 2500 rubles.
But the price difference is much less than the potential loss of infection by unknown threats and data leakage, as well as the cost of recovering encrypted information and / or eliminating security breaches.
Few numbers
• Adaptive Defense 360 has been on the market for about 1.5 years and protects over 1 million computers and servers.
• For all the time not a single device was infected in Lock mode
• Over 2.5 billion events analyzed daily
• 99.98% of processes are classified automatically.
• The rate of classification of new applications - from 0 to 24 hours
• In 2016, over 2.3 million security breaches were blocked.
• Adaptive Defense 360 detected threats in all networks where it was installed, regardless of the protection used
Conclusion
Existing approaches in evaluating the effectiveness of the “next generation” solutions reveal some misunderstanding of users of new realities: we expect blocking of unknown threats until the moment of their launch, but, unfortunately, this is already unlikely. New solutions are based on in-depth analysis and monitoring of precisely active processes, i.e. those processes that are running or trying to start.
Modern malware is very complex and should not be underestimated. Various methods of masking, sophistication of approaches and modern techniques of unknown threats can confuse any traditional anti-virus solution. To effectively deal with them, it is necessary to analyze all events in the context of all interrelated processes, which individually may not pose a danger, but in the aggregate they pursue very specific malicious goals.
According to Gartner experts, by 2019 many traditional EPP solutions will be enhanced with EDR-solutions functionality. And the market is really moving in this direction: many manufacturers have already announced that they will in the near future introduce Big Data, artificial intelligence and other modern technologies into their platforms and solutions.
Adaptive Defense 360 took this step in 2015 to provide continuous protection against all types of attacks, as well as to offer expert analysis tools that can track every action taken at the end point to eliminate and prevent current and future attacks.
We suggest you evaluate the capabilities of Adaptive Defense 360 using a demo console (without the need to install the product).
The demo console is designed to demonstrate Panda Adaptive Defense 360 , which already has certain information on user settings, profiles, etc., which allows you to evaluate the console in a mode as close as possible to real work.
Access demo console
Login: DRUSSIAN_FEDERATION_C13@panda.com
Password: DRUSSIAN # 123
Note: Reset changes in the settings of products that are made when viewing the demo console, occurs daily.
Source: https://habr.com/ru/post/323138/
All Articles