Solving Winter CrackMe Problems
As you know, an important part of the fight against cyber threats is the study of malicious files, which virus analysts are doing here — the brave guys (and girls!) From the Anti-Malware Team. Based on their experience, they regularly create special simulators, CrackMe, which novice analysts can use to test their knowledge.
Not so long ago, we announced the competition CrackMe, which was held in the framework of the event-platform CoLaboratory. Now that the competition is over and all decisions have been made, we can consider the tasks in more detail.

')
ATTENTION: If you did not have time to participate in the competition, but nevertheless want to try your hand - do not read the information under the cut. There we describe the problem solving algorithm. Download the latest CrackMe tasks here .
So, winter CRACKME # 1 from Kaspersky Lab. When you run the file, we are greeted by such a plain window with the requirement to enter data for the solution.

It is required to enter the e-mail under which you registered on the site and pick up the key for it. If you enter an incorrect value, the window swears - you have to decide.

For our fascinating research, we will use (drumming!) Only IDA Pro, that's all so simple.
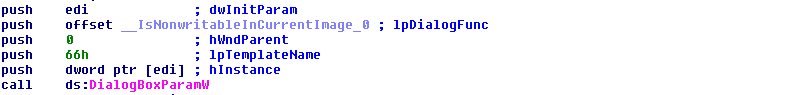
As a result, we see quite a standard picture for the window application. Before us is a fragment of WinMain, which does all the magic.The DialogBoxParamW function accepts bla-bla-bla as input parameters. I think it is unnecessary to repeat the documentation, so just go to the address that contains the function that will do something if we click the "Check" button.
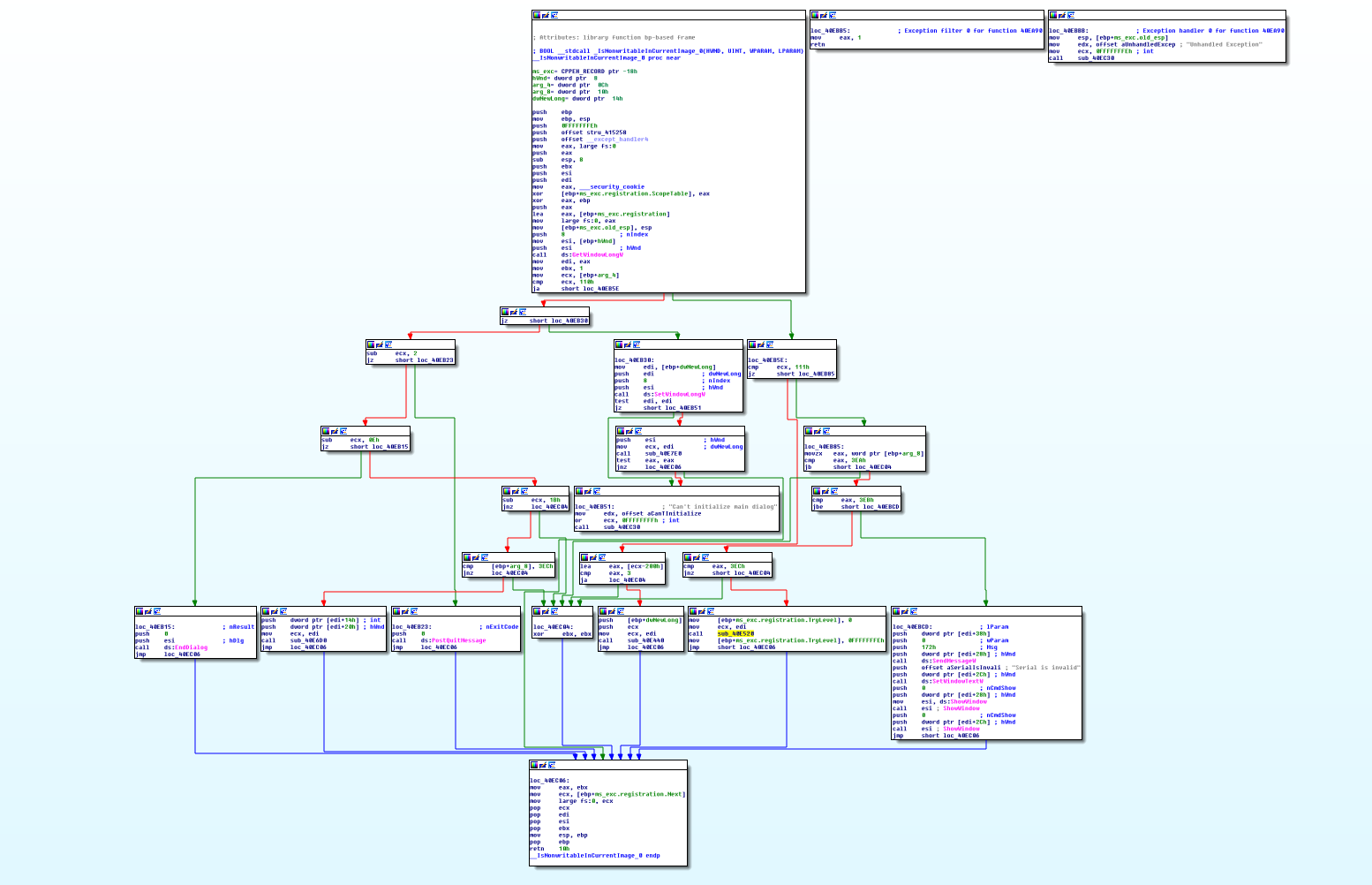
To understand how simple everything is, look at the picture above, where that magic function is displayed. In fact, this is just a jumble of code that shows us the message "Serial is invalid" if we enter incorrect data. The abundance of standard names of various structures, for example, “ms_exc.registration.TryLevel” suggests that Crackme is written in C ++, this is exactly what a construction (try-catch) looks like from the inside, and most likely, this code will be surrounded by appeals to this structure manipulates input data.
If, in parallel with reading, you followed the train of thought in the IDA window, then you probably already found the place we needed.
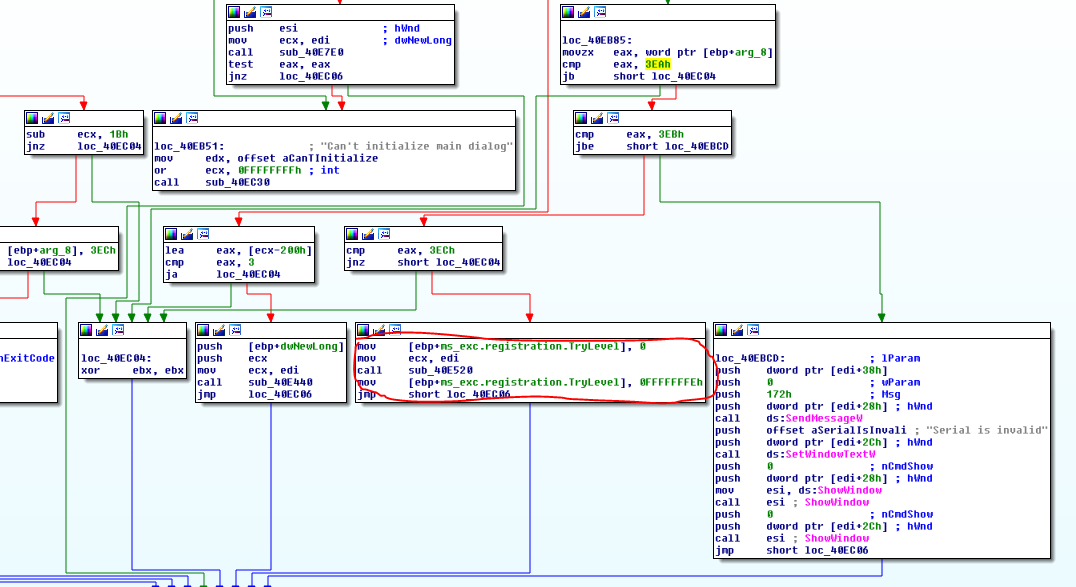
We are moving to a single function between calls to ms_exc.registration.TryLevel and voila - we are on the main function that determines whether we have found the key for our mail correctly or not.

To concentrate attention and beautifully display, the vertices of the graph are grouped in the figure above so that it can be seen which part is responsible for what. The usual if-else design.
Focusing on the top of the GetText And Check graph. The only thing we will pay attention to from this grouped block is this piece of listing.

If you look closely at the commands that are above, we will see that the resulting EMail and Serial fields are stored in memory. The picture above shows the commands that enter the addresses of the received data in the ECX and EDX registers, respectively. And then the test begins, in fact, this is its graph and is shown below.
Impressive, but the huge size of a graph with multiple branches can simply be a way to confuse the code with garbage commands. Therefore, we are not upset, we take a shovel and go to look for treasure.
We begin to sift the "ground". Immediately striking is the large number of commands from the address 0040DC00 to 0040DC86, which, at first glance, do something mathematically important to verify our key. However, if you take a closer look, you can understand that these are pairs of commands that compensate for each other’s actions. The whole range can be represented as one big nop-command, skip it. Take the next module filled with meaning. The code contained in this module was not recognized as standard, but all operations performed by it simply translate strings between Wide string into just string.

For convenience, we will rename the called functions, and we will keep the analysis of the internals for particularly inquisitive readers. Particular attention is paid only to the function with the conditional name "Md5". Why did we call her that? Let's look inside and, in order not to overload the article with pictures and explanations of each line of the listing, we will look only at the necessary piece.
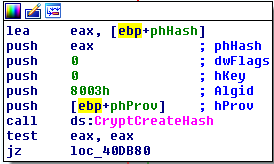
The code is straightforward enough, therefore, in order to understand what is happening, you simply need to read the names of the WinApi functions. In the picture you see a block from which we can determine WHAT for the algorithm is generally implemented by this function. Having rummaged in official documentation, we find value 8003h for a constant of "CALG_MD5". Comments are superfluous.
Refer to the following module.

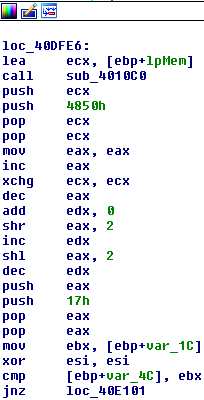
It contains a cycle. It shows that the cycle iterates over the sequence of data in memory using two variables, the values of which are indented from each other in 16 positions. Each element of the sequence performs an XOR operation with an element that is 16 characters apart. From the result obtained, MD5 is calculated.
The following module for review looks like this:
The module makes a comparison of two variables, is littered with commands, at the end compares the values of a variable and the value of the ebx register (a condition for comparing lengths of sequences?). As a result, a transition is made to the cycle, which is presented in the module in the image below. It performs a comparison on a sequence of 16 characters, increasing the counter by one if it matches and decreasing by one otherwise. (This is a comparison operation of the received Serial with the original one, which was calculated and stored in memory).
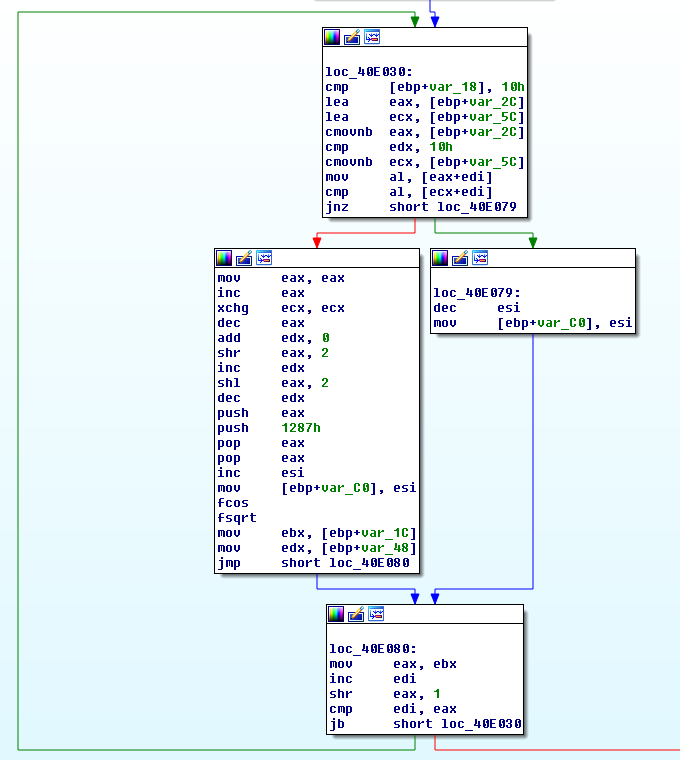
After this cycle, initialization occurs, and we see the mirror cycle, which starts not from zero, but from the 16th character. Figure below.

After processing in a sequence loop, among the garbage code and standard procedures, there is a module that makes a decision based on a comparison of two variables. You should not even get a lot of insight into the disassembled code. This is a comparison of the coincidence of two Serial strings and the calculated value based on the entered mail. The picture of the module is presented below.

To check the results of our research, we will try to carry out our own manipulations with the entered email address:
1. get Md5 amount from the address;
2. divide in half the amount received and perform the xor operation,
3. again calculate Md5 from the result.
As an experimental mail was used: sam@kakoitodomen.com
The following have been used as Serial: BB23F6DFA9375ED119237AAC4DE31BCD
The result is in the picture below.

Here is such a simple CRACKME.
In the second crack we are given a binary file (PE 32-bit). And again it is required to select the correct Serial for EMail.
To start, open this file in the aforementioned IDA . It is also useful to use Hex-Rays (a convenient decompiler that supports many architectures) when analyzing.
We can find a place in which the serial is tested.
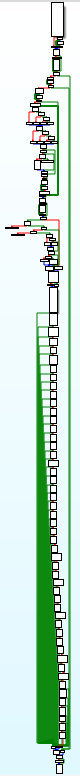
At 40E960 (not including the ASLR) is a test function.
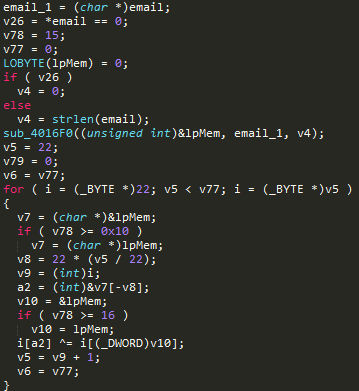
At the beginning you can see that the e-mail is compressed to a size of 22 bytes by the xor of all characters whose positions are equal modulo 22. In the case of a shortage, it is expanded by zero bytes.
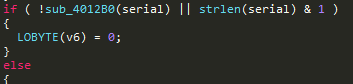
Then it is checked that the serial number is in hexadecimal number system, it is translated into bytes and the xor operation with the mail address is also performed on it.

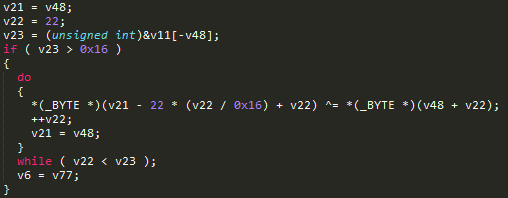
Then there is a check that the resulting xor-sum satisfies the SLAE , in which the ASCII character codes of some internal secret value are used.


There are many equations in SLAEs, therefore it is necessary to consider some method of automatic solution. To do this, you can use a computer math system (for example, NumPy ), or the so-called SMT solver z3 , which instantly finds a solution. Also, SLAE can be solved using the angr framework, which already contains z3 inside.
In the author's decision is used z3. But do not forget that any SLAE can be solved on a piece of paper by the Gauss method, you just have to try.
Having solved the SLAE, we get the secret value "KL_F4n7a5tiC_chAl1eN63", which this xor of everything with everything should be equal to.
Example:
EMail: sample@kaspersky.com
Serial: 382d3236580b770a540719262d10033842520a233633

Well that's all. We have dismantled two of the three CrackMe winter seasons from Kaspersky Lab. But we will not reveal all the secrets. It is likely that we will use the third CrackMe as a test task in the future. So, if you want to make a career as a virus analyst - try to solve it yourself.
More CrackMe, evening meetings, hakatons and other events soon on our site . Join now!
Not so long ago, we announced the competition CrackMe, which was held in the framework of the event-platform CoLaboratory. Now that the competition is over and all decisions have been made, we can consider the tasks in more detail.

')
ATTENTION: If you did not have time to participate in the competition, but nevertheless want to try your hand - do not read the information under the cut. There we describe the problem solving algorithm. Download the latest CrackMe tasks here .
CRACKME Solution # 1
So, winter CRACKME # 1 from Kaspersky Lab. When you run the file, we are greeted by such a plain window with the requirement to enter data for the solution.

It is required to enter the e-mail under which you registered on the site and pick up the key for it. If you enter an incorrect value, the window swears - you have to decide.

For our fascinating research, we will use (drumming!) Only IDA Pro, that's all so simple.

As a result, we see quite a standard picture for the window application. Before us is a fragment of WinMain, which does all the magic.

To understand how simple everything is, look at the picture above, where that magic function is displayed. In fact, this is just a jumble of code that shows us the message "Serial is invalid" if we enter incorrect data. The abundance of standard names of various structures, for example, “ms_exc.registration.TryLevel” suggests that Crackme is written in C ++, this is exactly what a construction (try-catch) looks like from the inside, and most likely, this code will be surrounded by appeals to this structure manipulates input data.
If, in parallel with reading, you followed the train of thought in the IDA window, then you probably already found the place we needed.

We are moving to a single function between calls to ms_exc.registration.TryLevel and voila - we are on the main function that determines whether we have found the key for our mail correctly or not.

To concentrate attention and beautifully display, the vertices of the graph are grouped in the figure above so that it can be seen which part is responsible for what. The usual if-else design.
Focusing on the top of the GetText And Check graph. The only thing we will pay attention to from this grouped block is this piece of listing.

If you look closely at the commands that are above, we will see that the resulting EMail and Serial fields are stored in memory. The picture above shows the commands that enter the addresses of the received data in the ECX and EDX registers, respectively. And then the test begins, in fact, this is its graph and is shown below.

Impressive, but the huge size of a graph with multiple branches can simply be a way to confuse the code with garbage commands. Therefore, we are not upset, we take a shovel and go to look for treasure.
We begin to sift the "ground". Immediately striking is the large number of commands from the address 0040DC00 to 0040DC86, which, at first glance, do something mathematically important to verify our key. However, if you take a closer look, you can understand that these are pairs of commands that compensate for each other’s actions. The whole range can be represented as one big nop-command, skip it. Take the next module filled with meaning. The code contained in this module was not recognized as standard, but all operations performed by it simply translate strings between Wide string into just string.

For convenience, we will rename the called functions, and we will keep the analysis of the internals for particularly inquisitive readers. Particular attention is paid only to the function with the conditional name "Md5". Why did we call her that? Let's look inside and, in order not to overload the article with pictures and explanations of each line of the listing, we will look only at the necessary piece.

The code is straightforward enough, therefore, in order to understand what is happening, you simply need to read the names of the WinApi functions. In the picture you see a block from which we can determine WHAT for the algorithm is generally implemented by this function. Having rummaged in official documentation, we find value 8003h for a constant of "CALG_MD5". Comments are superfluous.
Refer to the following module.

It contains a cycle. It shows that the cycle iterates over the sequence of data in memory using two variables, the values of which are indented from each other in 16 positions. Each element of the sequence performs an XOR operation with an element that is 16 characters apart. From the result obtained, MD5 is calculated.
The following module for review looks like this:

The module makes a comparison of two variables, is littered with commands, at the end compares the values of a variable and the value of the ebx register (a condition for comparing lengths of sequences?). As a result, a transition is made to the cycle, which is presented in the module in the image below. It performs a comparison on a sequence of 16 characters, increasing the counter by one if it matches and decreasing by one otherwise. (This is a comparison operation of the received Serial with the original one, which was calculated and stored in memory).

After this cycle, initialization occurs, and we see the mirror cycle, which starts not from zero, but from the 16th character. Figure below.

After processing in a sequence loop, among the garbage code and standard procedures, there is a module that makes a decision based on a comparison of two variables. You should not even get a lot of insight into the disassembled code. This is a comparison of the coincidence of two Serial strings and the calculated value based on the entered mail. The picture of the module is presented below.

To check the results of our research, we will try to carry out our own manipulations with the entered email address:
1. get Md5 amount from the address;
2. divide in half the amount received and perform the xor operation,
3. again calculate Md5 from the result.
As an experimental mail was used: sam@kakoitodomen.com
The following have been used as Serial: BB23F6DFA9375ED119237AAC4DE31BCD
The result is in the picture below.

Here is such a simple CRACKME.
CRACKME Solution # 2
In the second crack we are given a binary file (PE 32-bit). And again it is required to select the correct Serial for EMail.

To start, open this file in the aforementioned IDA . It is also useful to use Hex-Rays (a convenient decompiler that supports many architectures) when analyzing.
We can find a place in which the serial is tested.

At 40E960 (not including the ASLR) is a test function.

At the beginning you can see that the e-mail is compressed to a size of 22 bytes by the xor of all characters whose positions are equal modulo 22. In the case of a shortage, it is expanded by zero bytes.

Then it is checked that the serial number is in hexadecimal number system, it is translated into bytes and the xor operation with the mail address is also performed on it.



Then there is a check that the resulting xor-sum satisfies the SLAE , in which the ASCII character codes of some internal secret value are used.


There are many equations in SLAEs, therefore it is necessary to consider some method of automatic solution. To do this, you can use a computer math system (for example, NumPy ), or the so-called SMT solver z3 , which instantly finds a solution. Also, SLAE can be solved using the angr framework, which already contains z3 inside.
In the author's decision is used z3. But do not forget that any SLAE can be solved on a piece of paper by the Gauss method, you just have to try.
Having solved the SLAE, we get the secret value "KL_F4n7a5tiC_chAl1eN63", which this xor of everything with everything should be equal to.
Example:
EMail: sample@kaspersky.com
Serial: 382d3236580b770a540719262d10033842520a233633

Well that's all. We have dismantled two of the three CrackMe winter seasons from Kaspersky Lab. But we will not reveal all the secrets. It is likely that we will use the third CrackMe as a test task in the future. So, if you want to make a career as a virus analyst - try to solve it yourself.
More CrackMe, evening meetings, hakatons and other events soon on our site . Join now!
Source: https://habr.com/ru/post/323116/
All Articles