Arrested the alleged organizer of the MIRAI botnet attack on the provider Deutsche Telekom
Employees of the British Crime Control Agency (National Crime Agency, NCA) arrested a hacker suspected of organizing a massive MIRAI botnet attack on the German provider Deutsche Telekom last November, affecting more than 900,000 home routers. Compromised devices were used to provide access to the Internet, as well as online TV and telephony services.
The attack lasted two days, during which the subscribers of the provider could not connect to the network. This is how the geographical distribution of the attack looked:
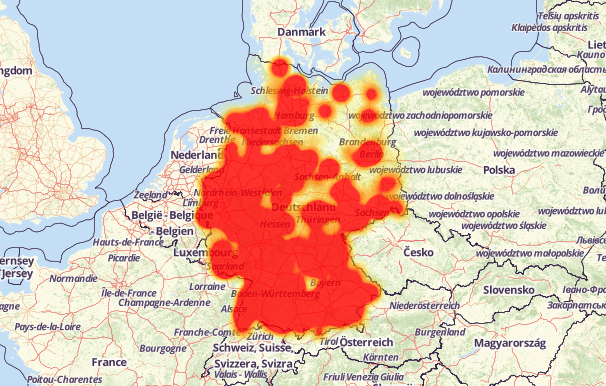
')
Image: Allestoerungen.de
The 29-year-old Briton became a suspect in the attack - he was detained at London's Luton Airport on Wednesday, February 22. According to law enforcement, the attackers created a new version of the MIRAI botnet from compromised devices that were sold on the black markets on the network.
The German Federal Criminal Police Office (Bundeskriminalamt, BKA) issued a statement stating that its owners planned to use the created botnet for conducting custom-made DDoS attacks. German authorities have confirmed to journalists that the suspect will be extradited to Germany, where he faces a ten-year prison sentence.
The attack was possible due to the low level of security of the devices used by Deutsche Telekom - immediately after neutralizing the consequences of the attack, the company announced that it would reconsider business relations with suppliers of vulnerable Speedport routers, the company Arcadyan.
The attack lasted two days, during which the subscribers of the provider could not connect to the network. This is how the geographical distribution of the attack looked:

')
Image: Allestoerungen.de
The 29-year-old Briton became a suspect in the attack - he was detained at London's Luton Airport on Wednesday, February 22. According to law enforcement, the attackers created a new version of the MIRAI botnet from compromised devices that were sold on the black markets on the network.
The German Federal Criminal Police Office (Bundeskriminalamt, BKA) issued a statement stating that its owners planned to use the created botnet for conducting custom-made DDoS attacks. German authorities have confirmed to journalists that the suspect will be extradited to Germany, where he faces a ten-year prison sentence.
The attack was possible due to the low level of security of the devices used by Deutsche Telekom - immediately after neutralizing the consequences of the attack, the company announced that it would reconsider business relations with suppliers of vulnerable Speedport routers, the company Arcadyan.
The security of IoT devices is often at a rather low level - this is because vendors are usually not interested in introducing additional information security measures. They advertise the ease of use of their products, and all additional measures of information security impose restrictions and require resources.
We will talk at a free webinar Positive Technologies “The Internet of Things challenges: will telecoms cope?”
The webinar will be held on Thursday, March 2 at 14:00 . To participate you need to register by the link: www.ptsecurity.com/ru-ru/research/webinar/173988/
Source: https://habr.com/ru/post/322712/
All Articles