Setting up DKIM / SPF / DMARC records or defending against spoofing
Greetings, Habr! This article will be a guide for setting up DKIM / SPF / DMARC records. And it prompted me to write this article a complete lack of documentation in Russian. All articles on this topic that were found by me were extremely not informative.
DKIM (DomainKeys Identified Mail) is an e-mail authentication method based on digital signature authentication. The public key is stored TXT domain records.
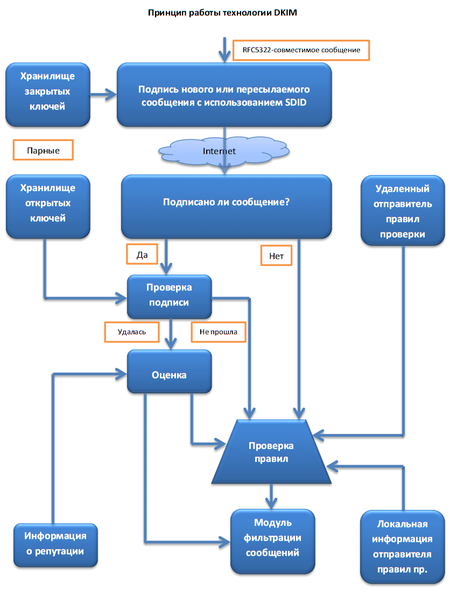
DKIM is necessary for mail services to check whether the sender is true or not. Those. protects the recipient of the letter from various fraudulent letters (which are sent with the substitution of the sender's address).
')
For this we need to create a pair of keys:
Or you can use the online service, which I strongly advise.
Next, you need to specify the path with the private key in the configuration file (for this, it is better to read the documentation) of the mail server and the public key in DNS.
An example of entries is
Where
possible:
It is also worth registering the ADSP record, which allows you to understand whether the letter must be signed or not.
There may be three values:
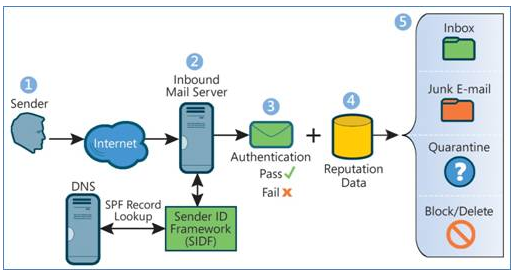
SPF (Sender Policy Framework) is an extension to the protocol for sending email via SMTP. SPF is defined in RFC 7208 ( Wiki ). If in simple terms, SPF is a mechanism for authenticating a message by checking the sending server. As for me, this technology is useful in combination in others (DKIM and DMARC)
An example of a regular SPF record is
Here:
(for a and mx, you can specify another domain, for example, if the value is
You can also add individual ip addresses using
Domain-based Message Authentication, Reporting and Conformance (message identification, reporting and matching by domain name) or DMARC is a technical specification created by a group of organizations designed to reduce the number of spam and phishing e-mails, based on the identification of the sender's email domains to based on the rules and characteristics set on the recipient's mail server ( Wiki ). That is, the mail server decides for itself whether the message is good or bad (say, based on the policies above) and acts according to the DMARC record.

A typical entry is:
It takes no action other than preparing and sending a report.
Now more about the tags:
The
We learned how to configure DKIM / SPF / DMARC and resist spoofing. Unfortunately, this does not guarantee security in the event of a hacking server or sending letters to servers that do not support these technologies. Fortunately, popular services still support them (and some are the initiators of these policies).
This article is just an instruction for self-tuning records, a kind of documentation. There are no intentional examples, because each server is unique and requires its own configuration.
I will be glad to constructive criticism and revisions.
1. DKIM
DKIM (DomainKeys Identified Mail) is an e-mail authentication method based on digital signature authentication. The public key is stored TXT domain records.

Why is it needed?
DKIM is necessary for mail services to check whether the sender is true or not. Those. protects the recipient of the letter from various fraudulent letters (which are sent with the substitution of the sender's address).
')
Configure DKIM signature and DNS records
For this we need to create a pair of keys:
openssl genrsa -out private.pem 1024 // 1024 openssl rsa -pubout -in private.pem -out public.pem // Or you can use the online service, which I strongly advise.
Next, you need to specify the path with the private key in the configuration file (for this, it is better to read the documentation) of the mail server and the public key in DNS.
An example of entries is
mail._domainkey.your.tld TXT "v=DKIM1; k=rsa; t=s; p=< >"
Where
mail - selector. You can specify multiple entries with different selectors, where each entry will have its own key. It is used when multiple servers are involved. (each server has its own key)v - version of DKIM, always takes the value v=DKIM1 . (required argument)k - key type, always k=rsa . (at least for now)p is the public key encoded in base64. (required argument)t - Flags:t=y - test mode. These differ from unsigned and are only needed to track the results.t=s - means that the record will be used only for the domain to which the record belongs, it is not recommended if subdomains are used.possible:
h - preferred hash algorithm, can take the values h = sha1 and h = sha256s - Type of service using DKIM. Accepts s=email (email) and s=* (all services). By default, "*".; - separator.It is also worth registering the ADSP record, which allows you to understand whether the letter must be signed or not.
_adsp._domainkey.example.com. TXT "dkim=all"There may be three values:
all - All letters must be signeddiscardable - Do not accept letters without a signatureunknown - Unknown (which, in fact, is similar to the absence of a record)2. SPF
SPF (Sender Policy Framework) is an extension to the protocol for sending email via SMTP. SPF is defined in RFC 7208 ( Wiki ). If in simple terms, SPF is a mechanism for authenticating a message by checking the sending server. As for me, this technology is useful in combination in others (DKIM and DMARC)

Configuring SPF Records
An example of a regular SPF record is
your.tld. TXT "v=spf1 a mx ~all" your.tld. TXT "v=spf1 a mx ~all"Here:
v=spf1 is the version, always spf1a - allows to send letters from the address that is specified in the A and \ or AAAA records of the sender's domainmx - allows you to send emails from the address specified in the mx domain record(for a and mx, you can specify another domain, for example, if the value is
a:example.com , it will be allowed and the record is not the sender's domain, but example.com )You can also add individual ip addresses using
ip4: and ip6: For example, ip4:1.1.1.1 ip6: 2001:0DB8:AA10:0001:0000:0000:0000:00FB . There is also include: ( include:spf.example.com ), which allows you to additionally connect spf records from another domain. All this can be combined through a space. If you just need to use an entry from another domain, not complementing it, then it is best to use redirect: ( redirect:spf.example.com )-all - means what will happen with letters that do not comply with the policy: "-" - reject, "+" - skip, "~" - additional checks, "?" - neutral.3.DMARC
Domain-based Message Authentication, Reporting and Conformance (message identification, reporting and matching by domain name) or DMARC is a technical specification created by a group of organizations designed to reduce the number of spam and phishing e-mails, based on the identification of the sender's email domains to based on the rules and characteristics set on the recipient's mail server ( Wiki ). That is, the mail server decides for itself whether the message is good or bad (say, based on the policies above) and acts according to the DMARC record.

Configuring DMARC Records
A typical entry is:
_dmarc.your.tld TXT "v=DMARC1; p=none; rua=mailto:postmaster@your.tld"It takes no action other than preparing and sending a report.
Now more about the tags:
v - version, takes the value v=DMARC1 (required)p - rule for domain. (Required) May be none , quarantine and reject , wherep=none does nothing but prepare reportsp=quarantine adds a letter to SPAMp=reject rejects the letterThe
sp is responsible for subdomains and takes the same values as paspf and adkim allow you to check for matching records and can take the values r and s , where r - relaxed is a softer check than s - strict.pct is responsible for the number of letters to be filtered, indicated as a percentage, for example, pct=20 will filter 20% of letters.rua - allows you to send daily reports to email, example: rua=mailto:postmaster@your.tld , you can also specify several rua=mailto:postmaster@your.tld mailto:dmarc@your.tld a space ( rua=mailto:postmaster@your.tld mailto:dmarc@your.tld )Report example
<record> <row> <source_ip>1.1.1.1</source_ip> <count>1</count> <policy_evaluated> <disposition>none</disposition> </policy_evaluated> </row> <identities> <header_from>your.tld</header_from> </identities> <auth_results> <dkim> <domain>your.tld</domain> <result>pass</result> <human_result></human_result> </dkim> <spf> <domain>your.tld</domain> <result>pass</result> </spf> </auth_results> </record> <record> <row> <source_ip>1.1.1.1</source_ip> <count>1</count> <policy_evaluated> <disposition>none</disposition> <reason> <type>forwarded</type> <comment></comment> </reason> </policy_evaluated> </row> <identities> <header_from>your.tld</header_from> </identities> <auth_results> <dkim> <domain>your.tld</domain> <result>pass</result> <human_result></human_result> </dkim> <spf> <domain>your.tld</domain> <result>pass</result> </spf> </auth_results> </record> ruf - email reports that are not DMARC validated. Otherwise, everything is the same as above.Epilogue
We learned how to configure DKIM / SPF / DMARC and resist spoofing. Unfortunately, this does not guarantee security in the event of a hacking server or sending letters to servers that do not support these technologies. Fortunately, popular services still support them (and some are the initiators of these policies).
This article is just an instruction for self-tuning records, a kind of documentation. There are no intentional examples, because each server is unique and requires its own configuration.
I will be glad to constructive criticism and revisions.
Source: https://habr.com/ru/post/322616/
All Articles