IoT Security: Securing Azure IoT Deployment
We present to your attention the latest article from the series “Security in IoT”, and we also invite you to take part in the conference from Microsoft “Business.IoT: opening the Internet of Things”. This article discusses in detail the security of the IoT infrastructure based on Azure IoT and describes the level of implementation in the process of configuring and deploying individual components. A comparative analysis of various methods is also presented.

1. Azure IoT Suite for those who start from scratch .
2. A comprehensive protection strategy .
3. Security system architecture .
4. Secure your Azure IoT deployment .
Securing your Azure IoT deployment should be assessed across three security areas:
')
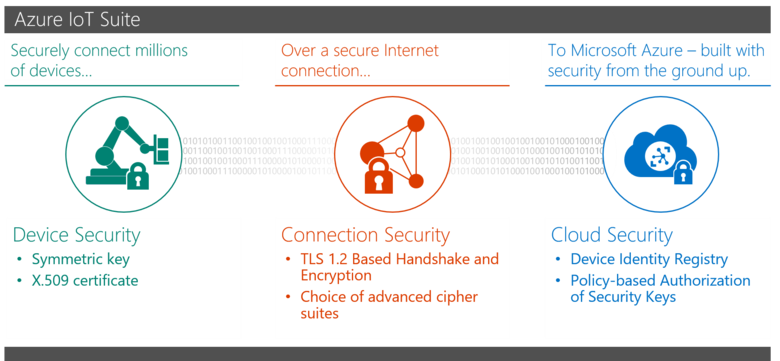
Azure IoT Suite uses two methods to ensure the security of IoT devices:
The security token authenticates all calls sent by the device to the IoT Hub service. For this purpose, a symmetric key connection is configured for each individual call. X.509 certificate based authentication allows you to authenticate the IoT device to the physical layer during the setup of a TLS connection. The security token method can also be used without X.509 certificate-based authentication, although this scenario does not guarantee the same high level of security. The choice of one of the two specified methods mainly depends on the required security level during device authentication, as well as on the availability of secure storage on the device (where the private key will be stored).
IoT Hub uses security tokens to authenticate devices and services, thus avoiding sending keys over the network. In addition, security tokens are limited in time and scope. Azure IoT Hub SDKs create tokens automatically; no special configuration is required. However, sometimes you have to create and use security tokens, for example, in the case of direct use of AMQP, MQTT or HTTP protocols, or when you deploy a token service template.
For more information about the security token structure and how to use it, see the following articles: " Security Token Structure " and " Using SAS Tokens as a Device ."
Each instance of the IoT Hub service contains a device identity registry that can be used to create individual device resources in the service (for example, a queue that contains current messages that are currently sent between the cloud and the device), as well as to set up access to endpoints interacting with the device. IoT Hub credential registry provides secure storage of device credentials as well as solution security keys. By adding white or blacklisted individual device identities or groups of identities, you can fully control access to devices.
IoT Hub supports protocols such as AMQP, MQTT and HTTPS. Each of these protocols uses different security tokens received from the IoT device and sent to the IoT Hub service.
The IoT Hub device identity registry can be used to configure device security credentials and access control. However, if a significant amount of IoT solution resources are already allocated to the user device identity registry and (or) authentication scheme , then by creating a token service, you can integrate the solution into the existing infrastructure using the IoT Hub service.
Using a X.509 certificate based on a device and its associated private and public key pair allows for additional authentication at the physical level. The private key is stored in secure storage on the device. It cannot be detected outside the device. The X.509 certificate contains device information (device ID and other organizational data). The signature of the certificate is created using the private key.
The process of preparing a high level device:
During the process of establishing a secure TLS connection with the IoT Hub service, the IoT device authenticates the service using the root certificate, which is included in the SDK of the device. The certificate for client C SDK is located in the \ c \ certs folder in the repository root. Although these root certificates are issued for a long time, their validity can still expire or they can be revoked. If the certificate cannot be updated on the device, then the subsequent connection of the device to the IoT Hub (or other cloud service) may also be unavailable. These risks can be reduced by effective tools for updating root certificates after deploying an IoT device.
Internet connection protection between the IoT device and the IoT Hub service is provided through the TLS standard. Azure IoT supports TLS 1.2 , TLS 1.1 and TLS 1.0 protocols. TLS 1.0 is supported for backward compatibility only. TLS 1.2 is recommended because this version of the protocol provides the highest level of security.
The following cipher suites are supported in Azure IoT Suite.
Azure IoT Hub allows you to define access control policies for each individual security key. This policy uses the following set of permissions, with which you can configure access to each of the IoT Hub endpoints. Permissions restrict access to the IoT Hub service depending on the required functions.
You can obtain DeviceConnect permissions for IoT Hub using security tokens in two ways: using a device identity key or a shared key access policy. In addition, it is important to note that all functions available on devices are provided by default on endpoints with the prefix / devices / {deviceId} .
Service components can create security tokens only using generic access policies that grant appropriate permissions.
Users are managed in the Azure IoT Hub and other services within the solution using the Azure Active Directory.
The data received by the IoT Hub service can be used by various services (for example, Azure Stream Analytics, blob storage, and so on). These services provide management access.
This article provides an overview of the level of implementation in the design and deployment of an IoT infrastructure using Azure IoT. Configuring the security of each particular component is key to the security of the entire IoT infrastructure. The design tools available in Azure IoT provide some flexibility and choice. However, your own security requirements may apply to any of the options selected. It is recommended to evaluate each of the available options using a risk and cost assessment procedure. We remind you that you can try Microsoft Azure for free here .
On March 30, 2017, Microsoft will host the online conference “Business.IoT: Discovering the Internet of Things” . The program will have two parallel tracks (business and technology) with best practices and recommendations from leading experts in the field of Internet of things, machine learning and predictive analytics.
Among the speakers will be: Mikhail Chernomordikov (Microsoft), Sergey Osipov (MAYKOR-GMCS), Dmitry Bergelson (GuaranaCam), Anna Kulashova (Microsoft), Dmitry Marchenko (Microsoft), Andrei Meluzov (KORUS Consulting) and Vasily Yesipov ( KPMG).
To participate, you must register here .
We would also like to share with you a list of IoT communities for technical specialists:
Events: Meetup.com . Here you can find meetings that are held by the Russian IoT community.
Social networks: VK , Facebook , Telegram channel, Telegram chat .

Cycle of articles "Security in IoT"
1. Azure IoT Suite for those who start from scratch .
2. A comprehensive protection strategy .
3. Security system architecture .
4. Secure your Azure IoT deployment .
Introduction
Securing your Azure IoT deployment should be assessed across three security areas:
')
- Security devices . Ensuring the safety of the IoT device during deployment.
- Connection protection Ensuring data confidentiality and protection against unauthorized changes during transmission between the IoT device and the IoT Hub service.
- Cloud security . Ensuring data security during data transfer and storage in the cloud.

Secure Device Preparation and Authentication
Azure IoT Suite uses two methods to ensure the security of IoT devices:
- Assigning each device a unique identity key (security tokens), which can also be used when communicating with the IoT Hub.
- Installing an X.509 certificate and private key on a device for device authentication in IoT Hub. This authentication method ensures that no one can view the private key on a device outside of that device. This provides a higher level of security.
The security token authenticates all calls sent by the device to the IoT Hub service. For this purpose, a symmetric key connection is configured for each individual call. X.509 certificate based authentication allows you to authenticate the IoT device to the physical layer during the setup of a TLS connection. The security token method can also be used without X.509 certificate-based authentication, although this scenario does not guarantee the same high level of security. The choice of one of the two specified methods mainly depends on the required security level during device authentication, as well as on the availability of secure storage on the device (where the private key will be stored).
Security Tokens IoT Hub Service
IoT Hub uses security tokens to authenticate devices and services, thus avoiding sending keys over the network. In addition, security tokens are limited in time and scope. Azure IoT Hub SDKs create tokens automatically; no special configuration is required. However, sometimes you have to create and use security tokens, for example, in the case of direct use of AMQP, MQTT or HTTP protocols, or when you deploy a token service template.
For more information about the security token structure and how to use it, see the following articles: " Security Token Structure " and " Using SAS Tokens as a Device ."
Each instance of the IoT Hub service contains a device identity registry that can be used to create individual device resources in the service (for example, a queue that contains current messages that are currently sent between the cloud and the device), as well as to set up access to endpoints interacting with the device. IoT Hub credential registry provides secure storage of device credentials as well as solution security keys. By adding white or blacklisted individual device identities or groups of identities, you can fully control access to devices.
IoT Hub supports protocols such as AMQP, MQTT and HTTPS. Each of these protocols uses different security tokens received from the IoT device and sent to the IoT Hub service.
- AMQP protocol . Security with SASL PLAIN and AMQP assertions ({policyName set@sas.root.{iothubName} - for service level tokens Hub; {deviceId} - for tokens used for the device).
- MQTT protocol . CONNECT uses {deviceId} as {ClientId}, {IoThubhostname} / {deviceId} in the Username field; and the SAS token in the Password field.
- HTTP protocol . A valid token is an authorization request header.
The IoT Hub device identity registry can be used to configure device security credentials and access control. However, if a significant amount of IoT solution resources are already allocated to the user device identity registry and (or) authentication scheme , then by creating a token service, you can integrate the solution into the existing infrastructure using the IoT Hub service.
Device authentication based on X.509 certificate
Using a X.509 certificate based on a device and its associated private and public key pair allows for additional authentication at the physical level. The private key is stored in secure storage on the device. It cannot be detected outside the device. The X.509 certificate contains device information (device ID and other organizational data). The signature of the certificate is created using the private key.
The process of preparing a high level device:
- Configuring the connection of the identifier with the physical device-device certificate and / or X.509 certificate, which is associated with the device at the stage of production or commissioning.
- Creation of the corresponding identity record in the IoT Hub device certificate and adding the data about the associated device to the IoT Hub device registry.
- Secure storage of the fingerprint of an X.509 certificate in the IoT Hub device registry.
Root certificate on device
During the process of establishing a secure TLS connection with the IoT Hub service, the IoT device authenticates the service using the root certificate, which is included in the SDK of the device. The certificate for client C SDK is located in the \ c \ certs folder in the repository root. Although these root certificates are issued for a long time, their validity can still expire or they can be revoked. If the certificate cannot be updated on the device, then the subsequent connection of the device to the IoT Hub (or other cloud service) may also be unavailable. These risks can be reduced by effective tools for updating root certificates after deploying an IoT device.
Connection protection
Internet connection protection between the IoT device and the IoT Hub service is provided through the TLS standard. Azure IoT supports TLS 1.2 , TLS 1.1 and TLS 1.0 protocols. TLS 1.0 is supported for backward compatibility only. TLS 1.2 is recommended because this version of the protocol provides the highest level of security.
The following cipher suites are supported in Azure IoT Suite.
Cipher suite | Length |
|---|---|
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (0xc028) ECDH secp384r1 (eq. 7680 bits RSA) FS | 256 |
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (0xc027) ECDH secp256r1 (eq. 3072 bits RSA) FS | 128 |
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (0xc014) ECDH secp384r1 (eq. 7680 bits RSA) FS | 256 |
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (0xc013) ECDH secp256r1 (eq. 3072 bits RSA) FS | 128 |
| TLS_RSA_WITH_AES_256_GCM_SHA384 (0x9d) | 256 |
| TLS_RSA_WITH_AES_128_GCM_SHA256 (0x9c) | 128 |
| TLS_RSA_WITH_AES_256_CBC_SHA256 (0x3d) | 256 |
| TLS_RSA_WITH_AES_128_CBC_SHA256 (0x3c) | 128 |
| TLS_RSA_WITH_AES_256_CBC_SHA (0x35) | 256 |
| TLS_RSA_WITH_AES_128_CBC_SHA (0x2f) | 128 |
| TLS_RSA_WITH_3DES_EDE_CBC_SHA (0xa) | 112 |
Cloud Security
Azure IoT Hub allows you to define access control policies for each individual security key. This policy uses the following set of permissions, with which you can configure access to each of the IoT Hub endpoints. Permissions restrict access to the IoT Hub service depending on the required functions.
- RegistryRead . Provides permission to read the device identity registry .
- RegistryReadWrite . Provides read and write access to the device identity registry.
- ServiceConnect . Provides access to data exchange and monitoring endpoints that interact with the cloud service. For example, this permission allows server-based cloud services to receive messages sent by the device to the cloud, send messages from the device to the cloud, and also receive appropriate delivery confirmations.
- DeviceConnect . Provides access to data exchange endpoints that interact with the device. For example, this permission allows you to send messages from your device to the cloud and receive messages sent from the cloud to your device. This permission is used on devices.
You can obtain DeviceConnect permissions for IoT Hub using security tokens in two ways: using a device identity key or a shared key access policy. In addition, it is important to note that all functions available on devices are provided by default on endpoints with the prefix / devices / {deviceId} .
Service components can create security tokens only using generic access policies that grant appropriate permissions.
Users are managed in the Azure IoT Hub and other services within the solution using the Azure Active Directory.
The data received by the IoT Hub service can be used by various services (for example, Azure Stream Analytics, blob storage, and so on). These services provide management access.
- Azure DocumentDB . Scalable, fully indexable database service that is used to store semi-structured data. It manages device metadata (attributes, configuration, and security settings) when preparing them for operation. DocumentDB provides high performance and throughput in data processing, as well as indexing without regard to the schema and an improved interface for creating SQL queries.
- Azure Stream Analytics . Thanks to streaming processing in the cloud in real time, you can quickly develop and deploy low-cost analytical solutions to analyze data from devices, sensors, infrastructure elements and applications in real time. Data obtained from this fully managed service can be scaled without restriction, while maintaining high throughput, robustness and low latency.
- Azure Application Services . A cloud-based platform for developing powerful web and mobile applications that can connect to data both in the cloud and locally. Development of attractive mobile applications for iOS, Android and Windows platforms. Built-in connectivity to dozens of cloud services and enterprise applications provide the ability to integrate with SaaS applications and enterprise software. Thanks to the ability to write code in any preferred language and IDE interface (.NET, NodeJS, PHP, Python or Java), you can quickly create web applications and APIs.
- Logic applications . The application logic feature in Azure Application Service allows you to integrate an IoT solution into existing business systems and effectively automate workflows. Developers can use logic applications to create workflows that run on a trigger and perform a sequence of actions — rules and operations that use efficient connectors to integrate with existing business processes of a company. Logic applications also provide built-in connectivity to the SaaS ecosystem, the cloud environment, and local applications.
- Binary storage . Reliable and cost-effective cloud storage for data sent by devices to the cloud.
Conclusion
This article provides an overview of the level of implementation in the design and deployment of an IoT infrastructure using Azure IoT. Configuring the security of each particular component is key to the security of the entire IoT infrastructure. The design tools available in Azure IoT provide some flexibility and choice. However, your own security requirements may apply to any of the options selected. It is recommended to evaluate each of the available options using a risk and cost assessment procedure. We remind you that you can try Microsoft Azure for free here .
Business.IoT: discovering the Internet of Things
On March 30, 2017, Microsoft will host the online conference “Business.IoT: Discovering the Internet of Things” . The program will have two parallel tracks (business and technology) with best practices and recommendations from leading experts in the field of Internet of things, machine learning and predictive analytics.
Among the speakers will be: Mikhail Chernomordikov (Microsoft), Sergey Osipov (MAYKOR-GMCS), Dmitry Bergelson (GuaranaCam), Anna Kulashova (Microsoft), Dmitry Marchenko (Microsoft), Andrei Meluzov (KORUS Consulting) and Vasily Yesipov ( KPMG).
To participate, you must register here .
IoT Communities
We would also like to share with you a list of IoT communities for technical specialists:
Events: Meetup.com . Here you can find meetings that are held by the Russian IoT community.
Social networks: VK , Facebook , Telegram channel, Telegram chat .
Source: https://habr.com/ru/post/322600/
All Articles