Ping and some of its parameters
“Why do the ping team use the Loose, Strict, Record, Timestamp, and Verbose options?” I met this question recently in a vendor exam. They allow you to influence the routing of ICMP packets and collect information about L3 transit devices. But being engaged in network technologies for a long time, I almost never used them.
It became not quite clear to me why such a question is generally present in the test. After returning home, I decided to find out, what if I really constantly lose sight of something important?
The ping utility is well known to all of us. In addition to the standard "ping 8.8.8.8", you can use various options, among which there are of us. Their name and description are about the same for vendors.
')
Of the most used, I would note the following.
There are a number of other options left overboard (timeout, ToS, etc.), which I personally almost never use.
- Number of packages sent
Instead of the specified number of default packets (for example, in Windows - four, in Cisco equipment - five), we can send the right one. This also includes many of the favorite “-t” options in Windows, which starts the endless sending of packets. - Source interface
First of all relevant for network equipment. By default, when using the ping command, the device sends a packet with the address of the nearest interface to the destination point. In the case of testing NAT functions or checking VPN, there is a need to send ICMP packets from another interface. Another classic example: how to prove to a colleague that his firewall is enabled on the host, and not the network is buggy. We launch ping from a kernel of a network without interface instructions - pinged. With the indication of the nearest interface - not pinged. - DF bit setting
A packet with a DF bit set (= 1) cannot be fragmented. This option is useful for determining the maximum allowable frame size (MTU) between two points. Usually used in conjunction with the parameters below. - Package size
You can vary the size of the package. Together with the installation of the DF-bit helps in determining the MTU. We send a large packet - 1500 bytes. Does not pass. We send a little less - 1300. Passes. We send 1400. And so on. In general, the dichotomy method and MTU are defined.
On Windows, we specify the size of the ICMP packet data segment. On Cisco devices, the size of the IP packet including headers. - Variation of package size in the specified range
For those who do not like the method of dichotomy, this mode may be useful. We specify the initial value of the packet size, final and step. Next, the device sends packets, gradually increasing their size. The main thing is not to forget to set the DF-bit, otherwise everything is for nothing.
There are a number of other options left overboard (timeout, ToS, etc.), which I personally almost never use.
Loose, Strict, Record, Timestamp, Verbose options are included in the ping utility on many network devices. There is support in Windows.
Record (Record Route)
An ICMP packet with the Record option records the IP addresses of outgoing interfaces as it passes through L3 devices. This is done both in the direction of the destination, and back. This is useful, for example, when diagnosing problems related to asynchronous routing. It turns out like traceroute, only better.
"Options"
I use the word “options” in two contexts: ping command options and options in the ICMP packet. In the case of ICMP, options are additional parameters that are set in the IPv4 header (hereinafter we will simply indicate IP) in the Options field. Therefore it is more correct, of course, to talk about the IP options. ICMP just uses them in their work.
But it's too early to rejoice: the maximum number of entries is nine. And they include data on the IP-addresses of devices in both directions. This is due to the restriction that the information about IP-addresses is stored not in the package body, but in the header. The option field cannot be too large. It is limited to 40 bytes. We, in the end, on the network need to drive useful data, not headers. Only nine entries are placed in this volume (4 bytes for each IPv4 address). The remaining (40-4 * 9) = 4 bytes go to the mark about the type of option, length, and so on. Attributes. Let me remind you that the maximum size of an entire IPv4 header is 60 bytes.
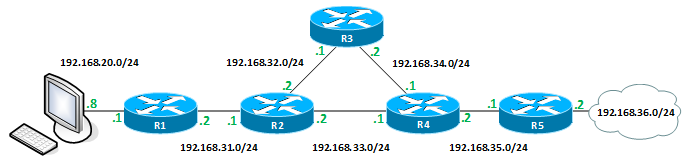
We start from a PC running Windows ping with the option Record Route (-r) to the address 192.168.36.2:
C: \ Users \ user> ping -n 1 -r 9 192.168.36.2
192.168.36.2 32 : 192.168.36.2: =32 =12 TTL=252 : 192.168.31.2 -> 192.168.32.2 -> 192.168.34.2 -> 192.168.35.2 -> 192.168.36.2 -> 192.168.35.1 -> 192.168.33.1 -> 192.168.31.1 -> 192.168.20.1 Ping 192.168.36.2: : = 1, = 1, = 0 (0% ) - : = 12, = 12 , = 12 ICMP Echo Request with Record Route (Type = 7) in the IP header:
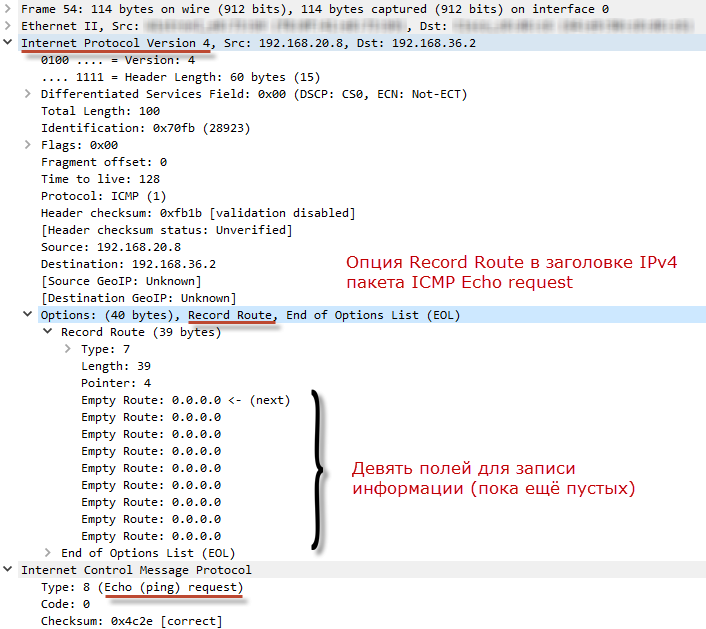
ICMP Echo Request comes to the recipient. On the way, addresses of transit devices are added to it. The recipient takes the filled fields of the IP header option, copies them to ICMP Echo Reply and sends them back. While ICMP Echo reply gets to the initiator of the ping, it will acquire records of the return route.
In the ICMP Echo Reply response packet, which the PC will receive, the Record Route option will already be filled:
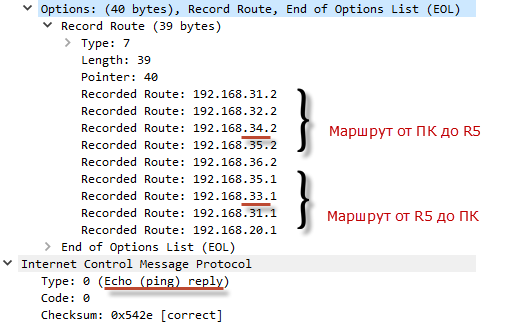
You may notice that asymmetric routing takes place in our network.
Example ping with the Record option on Cisco networking equipment.
R1#ping Protocol [ip]: Target IP address: 192.168.36.2 Repeat count [5]: 1 Datagram size [100]: Timeout in seconds [2]: Extended commands [n]: y Source address or interface: Type of service [0]: Set DF bit in IP header? [no]: Validate reply data? [no]: Data pattern [0xABCD]: Loose, Strict, Record, Timestamp, Verbose[none]: R Number of hops [ 9 ]: Loose, Strict, Record, Timestamp, Verbose[RV]: Sweep range of sizes [n]: Type escape sequence to abort. Sending 1, 100-byte ICMP Echos to 192.168.36.2, timeout is 2 seconds: Packet sent with a source address of 192.168.20.1 Packet has IP options: Total option bytes= 39, padded length=40 Record route: <*> (0.0.0.0) (0.0.0.0) (0.0.0.0) (0.0.0.0) (0.0.0.0) (0.0.0.0) (0.0.0.0) (0.0.0.0) (0.0.0.0) Reply to request 0 (3 ms). Received packet has options Total option bytes= 40, padded length=40 Record route: (192.168.31.2) (192.168.32.2) (192.168.34.2) (192.168.35.2) (192.168.36.2) (192.168.35.1) (192.168.33.1) (192.168.31.1) (192.168.31.2) <*> End of list Success rate is 100 percent (1/1), round-trip min/avg/max = 3/3/3 ms Timestamp
When an ICMP packet with the Timestamp option passes through an L3 device, it writes a label indicating the current time to it. The scheme of work is similar to the Record option, only time is put instead of the address. As in the previous case, the packet can contain only nine time records (for Windows OS, four, since, in addition to the time stamp, the device’s IP address is added).
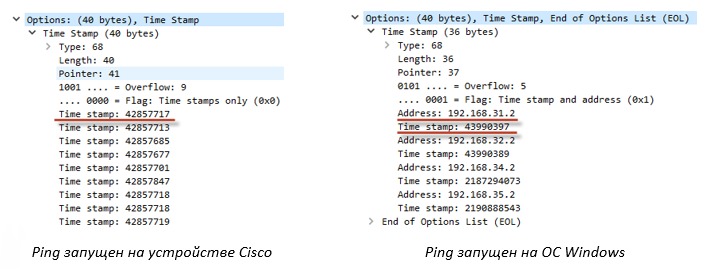
The time in the package is in the UNIX time format. Data analysis has at least some sense if all devices are synchronized in time (in our example this is not the case).
Example ping with the Timestamp (-s) option on a PC running Windows.
C:\Users\user>ping -n 1 -s 4 192.168.36.2 192.168.36.2 32 : 192.168.36.2: =32 =4 TTL=252 : 192.168.31.2 : 43990397 -> 192.168.32.2 : 43990389 -> 192.168.34.2 : 2187294073 -> 192.168.35.2 : 2190888543 Ping 192.168.36.2: : = 1, = 1, = 0 (0% ) - : = 4, = 4 , = 4 Strict (Strict Source Route)
When using this option, a list of IP addresses of L3 devices is specified, through which the ICMP packet must pass. And it is in the sequence that we have indicated. Records, according to tradition, a maximum of nine.
The option works simply: on each hop, the destination IP address changes to the one we specified when running the ping utility.
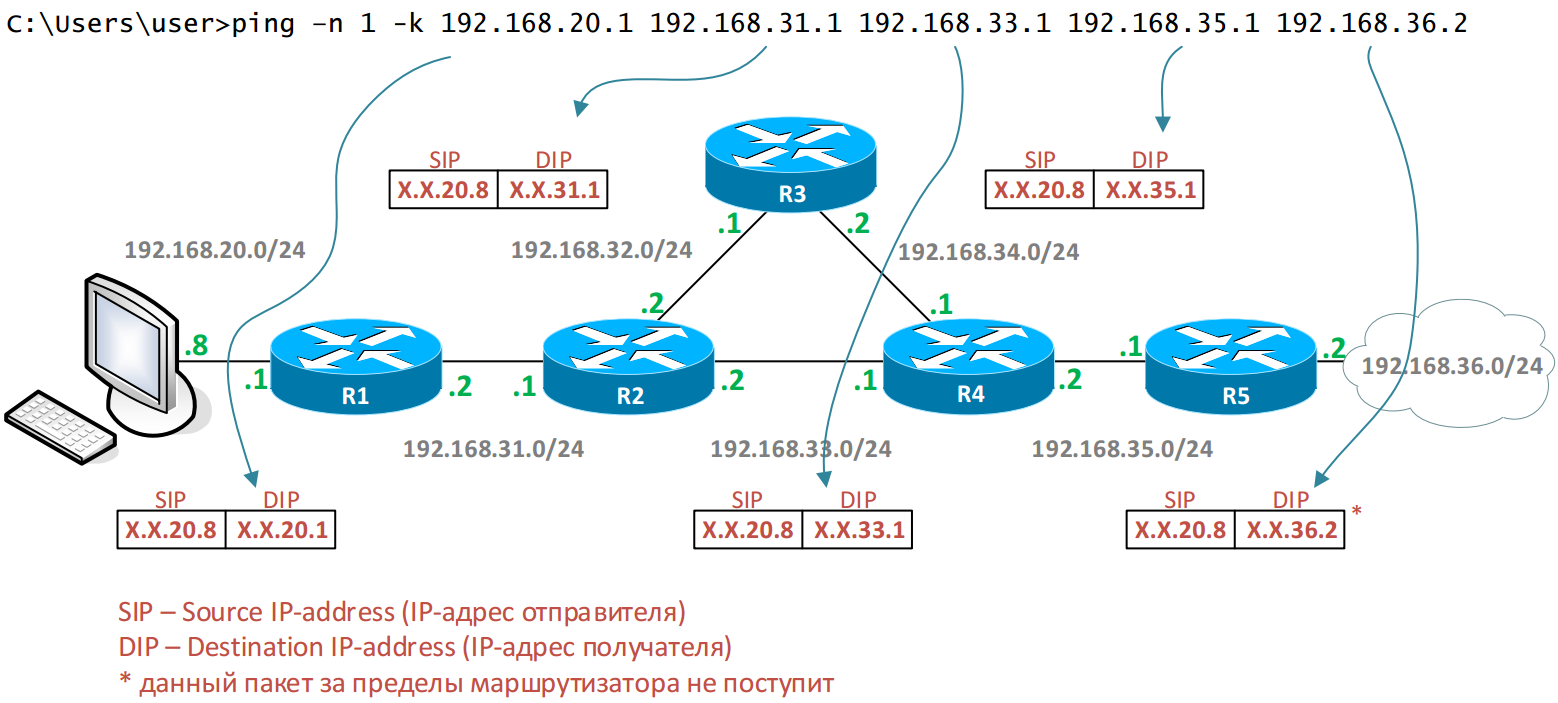
All addresses are stored in the IP header of our ICMP packet. Therefore, each transit device can spy on them. This scheme allows you to bypass the current routing rules on each device, since in fact we have a packet forwarded to a neighboring device.
In our scheme, R2 has a route to the network 192.168.36.0/24 via R3. But since we have hardcoded devices in the ICMP packet options, R2 will transfer it directly to R4.
Run the ping utility with the -k (Strict Source Route) option in Windows OS and prescribe device addresses.
C: \ Users \ user> ping –n 1 -k 192.168.20.1 192.168.31.1 192.168.33.1 192.168.35.1 192.168.36.2
192.168.36.2 32 : 192.168.36.2: =32 =5 TTL=252 : 192.168.35.1 -> 192.168.33.1 -> 192.168.31.1 -> 192.168.20.1 Ping 192.168.36.2: : = 1, = 1, = 0 (0% ) - : = 5, = 5 , = 5 The ICMP Echo Request package with the Strict Source Route option (Type = 137) in the IP header on our PC looks like this:
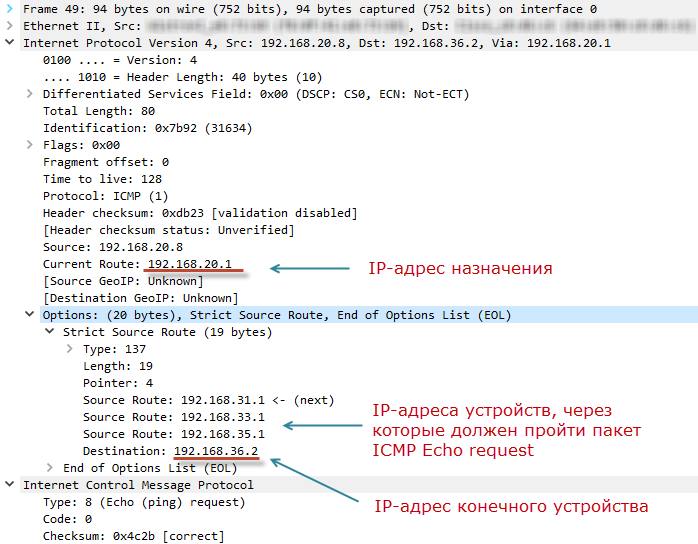
The PC has substituted 192.168.20.1 as the recipient address. The remaining addresses of the transit devices were safely packed into the fields of the IP options (Source Route entries). The destination device address is added to the Destination entry.
The same package, after it passes R1:
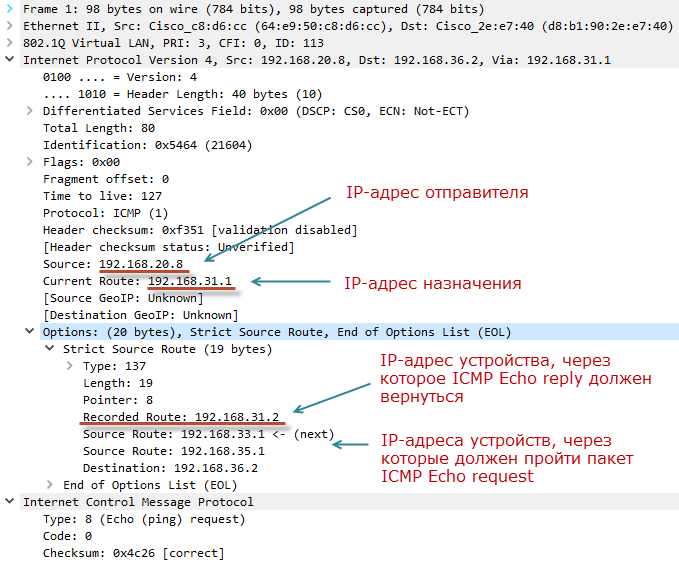
The sender's IP address remains unchanged. Recipient's IP address changed to a new one - 192.168.31.1. This value is taken from the Source Route field when the ICMP packet has just arrived at R1.
It is important to note that R1 has added a new entry in the options field - Recorded Route. There is substituted the IP address of the interface R1. This field is required for the return packet (ICMP Echo reply) to return along the same route as the ICMP Echo request. Similarly, will do the rest of the device. Therefore, when the ICMP packet goes to R5, the Strict Source Route option will contain a list of IP addresses of interests through which the response packet must pass.
ICMP Echo reply received by PC:
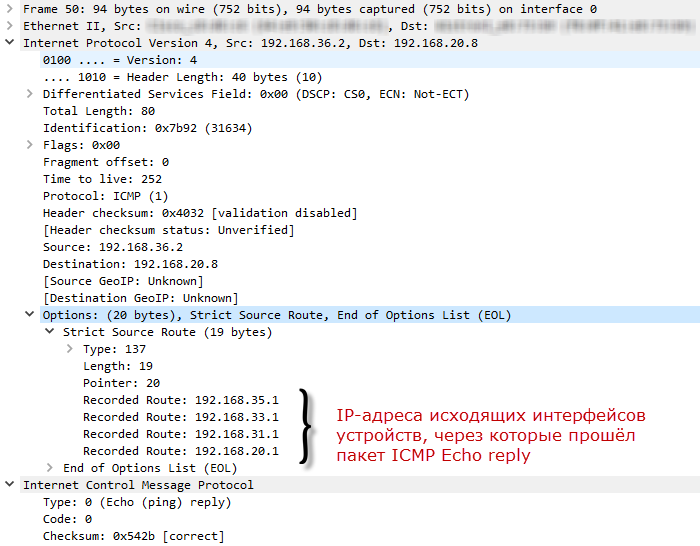
The Recorded Route field is rewritten as the ICMP Echo reply packet proceeds, since there is always an outgoing interface address for the current packet. Therefore, when R1 receives ICMP Echo reply, it will replace 192.168.31.2 with 192.168.20.1.
If in the ping command we omit one of the addresses, for example, the last one (192.168.35.1 - R5), R4 will have to send the packet immediately to the device with the address 192.168.36.2. But since this network is not local to it, R4 will report that the specified node is unreachable. It will not route the packet normally.
To handle the Record option on network equipment, source routing mode must be enabled. For example, on Cisco hardware, it is enabled by default.
Loose (Loose Source Route)
This option is essentially very similar to the Strict option. But, unlike Strict, in the Loose option, it is not the hard route of the ICMP packet that is set, but only selective devices. Those. The packet can be routed by other devices. The maximum number of addresses is nine.
The scheme of work is similar to the previous case. The difference is that a packet with the Loose option can be routed by transit devices according to the usual rules.
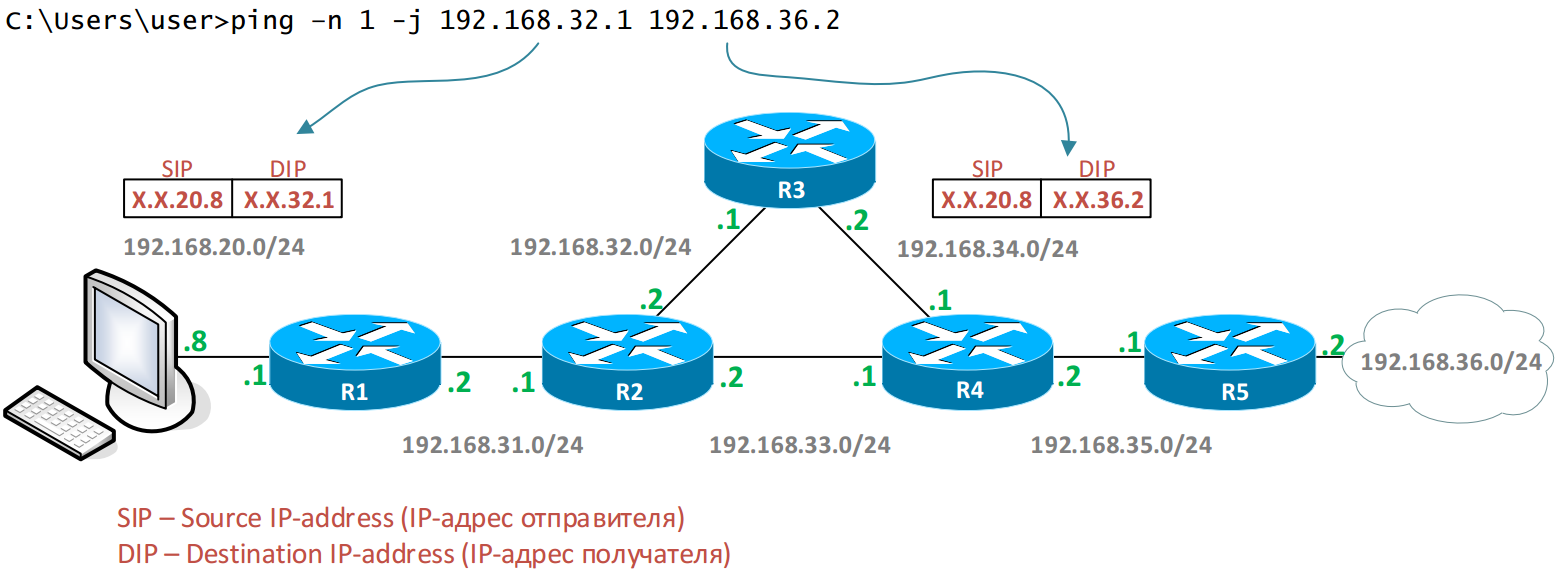
Run the ping utility with the -j (Loose Source Route) option in Windows OS and prescribe device addresses.
C: \ Users \ user> ping -n 1 -j 192.168.32.1 192.168.36.2
192.168.36.2 32 : 192.168.36.2: =32 =4 TTL=250 : 192.168.32.1 Ping 192.168.36.2: : = 1, = 1, = 0 (0% ) - : = 4, = 4 , = 4 The ICMP Echo Request with the Loose Source Route option (Type = 131) in the IP header on our PC looks like this:
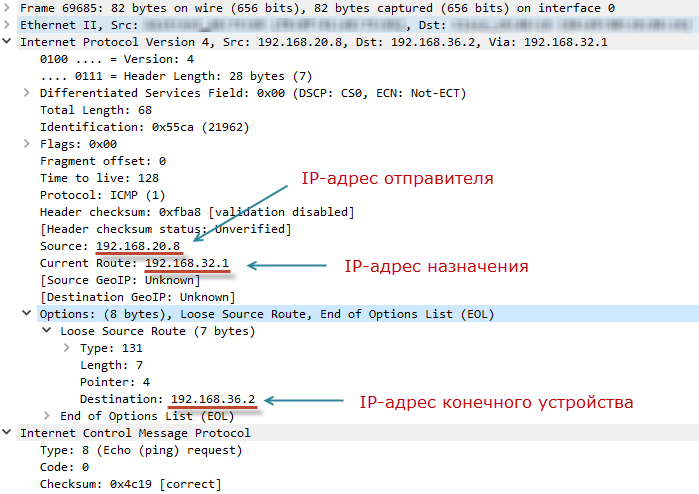
The PC has substituted the address R3 (192.168.32.1) as the recipient. In this case, the address of the end device R5 (192.168.36.2) indicated in the option IP (record Destination). Next, the packet is routed to the network according to the usual rules, until it reaches R3. R3 will substitute the address R5 as the destination address and, in the options, register its address through which the return packet should return (Recorded Route entry). Then send it to the network.
The ICMP Echo reply response packet is not of particular interest, since it is similar to the previously discussed. In the options, the address of the outgoing R3 interface (Recorded Route entry) through which the packet passed is indicated.
Verbose
This option is activated automatically when you select any of the previously described. Provides a more detailed display of information on the screen. It does not affect the ICMP packet itself. In Windows, there is no such option in the ping command.
So that we can take advantage of these options, the middleware must support them. There will be no problem with this. It is not necessary to attribute all this “rocket science” to the innovations of the IT world. The conclusion is: the options Loose, Strict, Record, Timestamp can be useful, even with the restriction of "nine". If it were not for the following nuances related to security.
The first. The Record and Timestamp options can be safely used for online reconnaissance. With their help, you can explore the network topology, get fingerprints, which determine the OS and the type of device through which the packet with these options passed.
The second. The Loose and Strict options allow you to control the movement of the packet, ignoring standard routing rules. This provides ample opportunities for attempts to penetrate different network segments, where in the case of normal access routing should not be. It is also possible to conduct intelligence to analyze the network topology. Perform bandwidth utilization attacks on specific network segments. There are many options.
Third. A part of network equipment processes packages with installed options programmatically at the control-plane level (without using various traffic routing optimization schemes), which unconditionally loads the CPU. This means that it is possible to carry out a DoS attack on such a device.
Many vendors (there is even a separate RFC 7126 ) do not recommend packages with the specified options. Options offer different. Up to drop such packets. True, some of the manufacturers have dissonances: on the one hand, we recommend discarding such packages, on the other hand , “Record is a very useful option”.
A quick attempt to verify compliance with these recommendations with a couple of Internet providers showed that some of the options still work. But source routing is disabled everywhere.
It turns out an interesting conclusion. Loose, Strict, Timestamp, Record options can be useful in diagnosing network problems. But the issue of security levels it out.
As a result, I still have a sense of misunderstanding. Why the question sounded at the beginning was present in the test? The Record option is relatively useful even if the network depth is shallow. The remaining options are in question.
Finally, a small survey. Have a nice day, everyone!
Source: https://habr.com/ru/post/322386/
All Articles