RTM Cybergroup specializes in stealing funds from Russian companies
There are several cyber groups that specialize in stealing funds from Russian companies. We observed attacks with the use of loopholes in security systems, opening access to the network of target objects. Having gained access, attackers study the network structure of the organization and deploy their own tools to steal funds. A classic example of this trend is the hacker groups Buhtrap, Cobalt and Corkow.
The RTM group that this report is about is part of this trend. It uses specially designed malware written in Delphi, which we will look at in more detail in the following sections. The first traces of these tools in the ESET telemetry system were discovered at the end of 2015. As needed, the group loads various new modules into infected systems. The attacks are aimed at the users of RBS systems in Russia and some neighboring countries.
The RTM campaign is targeted at corporate users - this is evident from the processes that attackers are trying to detect in a compromised system. In focus accounting software for working with remote banking systems.
The list of processes of interest to RTM resembles the corresponding list of the Buhtrap group, but at the same time the infection vectors are different for groups. If Buhtrap used fake pages more often, then RTM is a drive-by download attack (attacks on the browser or its components) and spam by email. According to telemetry, the threat is aimed at Russia and several nearby countries (Ukraine, Kazakhstan, the Czech Republic, Germany). However, due to the use of mass distribution mechanisms, malware detection outside the target regions is not surprising.
The total number of malware detections is relatively small. On the other hand, the RTM campaign uses sophisticated programs, which indicates a high targeting of attacks.
We found several bait documents used by RTM, including non-existent contracts, invoices, or tax records. The nature of the lures in combination with the type of software that the attack is aimed at indicates that the attackers “enter” the networks of Russian companies through the accounting department. The Buhtrap group acted in the same way in 2014–2015.
During the study, we were able to interact with several C & C servers. We will list the full list of commands in the following sections, but for now we can say that the client sends data from the keylogger directly to the attacker's server, from which additional commands are then received.
However, the days when you could just connect to the command server and collect all the data of interest are over. We recreated realistic log files to get several relevant commands from the server.
The first one is a request to the bot to transfer the 1c_to_kl.txt file - the transport file of the 1C: Enterprise 8 program, the appearance of which is actively tracked by RTM. 1C interacts with RBS systems by uploading data about outgoing payments to a text file. The file is then sent to the RBS system for automation and execution of the payment order.
The file contains payment details. If the malefactors change the data on outgoing payments, the transfer will go through the false details to the attackers' accounts.
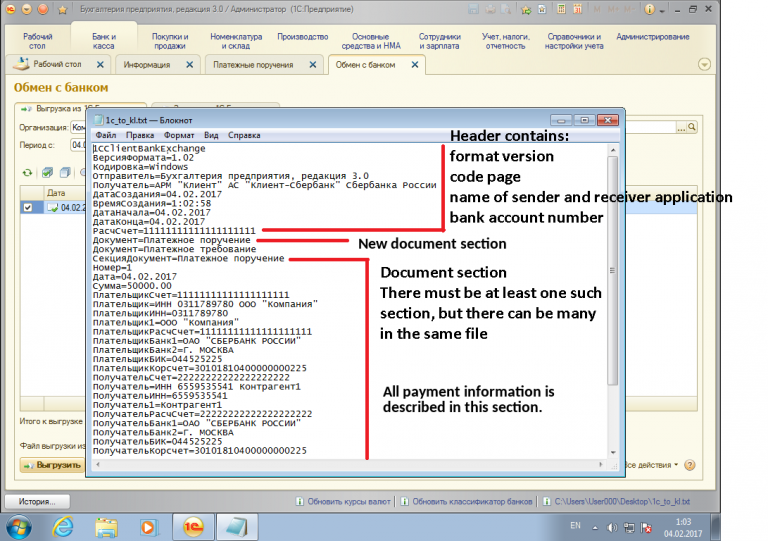
About a month after the request of these files from the command server, we observed loading of the new plug-in 1c_2_kl.dll into the compromised system. The module (DLL) is designed to automatically analyze the file upload by penetrating the processes of accounting software. We will describe it in detail in the following sections.
Interestingly, at the end of 2016, “FinCERT” of the Bank of Russia issued a bulletin with a warning about cybercriminals using upload files 1c_to_kl.txt. The developers of 1C also know about this scheme, they have already made an official statement and listed the precautions.
Other modules were loaded from the command server, in particular, VNC (its 32 and 64-bit versions). It resembles the VNC module that was previously used in Dridex Trojan attacks. This module is supposedly used to remotely connect to an infected computer and study the system in detail. Next, the attackers try to navigate the network, extracting user passwords, gather information and ensure the constant presence of malware.
2. Vectors of infection
The following figure shows the infection vectors found during the study period of the campaign. The group uses a wide range of vectors, but mostly drive-by download and spam attacks. These tools are convenient for targeted attacks, since in the first case, attackers can choose sites visited by potential victims, and in the second case, send email with attachments directly to the right employees of companies.

Malicious software is distributed in several channels, including RIG and Sundown exploit kits or spam mailings, indicating that the attackers have connections with other cyber attackers offering these services.
2.1. How are RTM and Buhtrap related?
The RTM campaign is very similar to Buhtrap. A logical question: how are they related to each other?
In September 2016, we observed the distribution of the RTM sample using the Buhtrap loader. In addition, we found two digital certificates used in both Buhtrap and RTM.
The first one, allegedly issued by DNISTER-M, was used to digitally sign the second form of Delphi (SHA-1: 025C718BA31E43DB1B87DC13F94A61A9338C11CE) and the Buhtrap DLL (SHA-1: 1E2642B454A2C889B6D41116CCD83836666666666666666666666666116CCD838366666666666166116666661661166661166611666116611661166116661166636C11CE

Second, issued us Bit-Tredj, used for signature loaders Buhtrap (SHA-1: 7C1B6B1713BD923FC243DFEC80002FE9B93EB292 and B74F71560E48488D2153AE2FB51207A0AC206E2B), as well as unloading and installation RTM components.
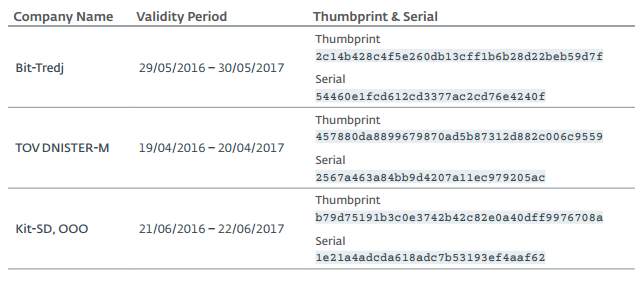
RTM operators use certificates that are common with other malware families, but they also have a unique certificate. According to the ESET telemetry system, it was issued to Kit-SD and was used only to sign some RTM malware (SHA-1: 42A4B04446A20993DDAE98B2BE6D5A797376D4B6).
RTM uses the same loader as Buhtrap, RTM components are loaded from the Buhtrap infrastructure, so the groups have similar network indicators. Nevertheless, according to our estimates, RTM and Buhtrap are different groupings, at least, because RTM is distributed in different ways (not only with the help of an “alien” bootloader).
Despite this, hacker groups use similar principles of work. They target companies that use accounting software, similarly collect information about the system, look for smart card readers, and deploy an array of malicious tools to spy on victims.
3. Evolution
In this section, we will look at the different versions of malware found during the study.
3.1. Versionality
RTM stores configuration data in the registry key, the most interesting part of the botnet-prefix. A list of all the values that we saw in the studied samples is presented in the table below.
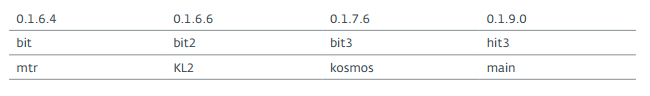
Perhaps the values can be used to record versions of the malware. However, we did not notice any special differences between the versions, such as bit2 and bit3, 0.1.6.4 and 0.1.6.6. Moreover, one of the prefixes exists from the very beginning and has evolved from a typical C & C domain to a .bit domain, as will be shown later.
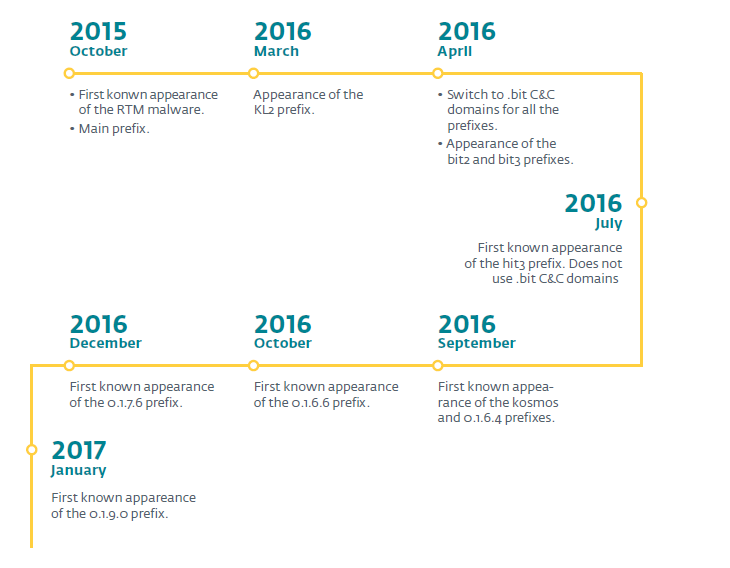
3.2. Schedule
Using telemetry data, we created a graph of the appearance of samples.
4. Technical analysis
In this section, we describe the main functions of the RTM banking trojan, including resilience mechanisms, its own version of the RC4 algorithm, network protocol, spyware functionality, and some other features. In particular, we will focus on samples SHA-1 AA0FA4584768CE9E16D67D8C529233E99FF1BBF0 and 48BC113EC8BA20B8B80CD5D4DA92051A19D1032B.
4.1. Install and save
4.1.1. Implementation
Kernel RTM - DLL, the library is loaded onto the disk using .EXE. The executable file is usually packaged and contains the DLL code. Once launched, it extracts the DLL and starts it using the following command:
rundll32.exe “%PROGRAMDATA%\Winlogon\winlogon.lnk”,DllGetClassObject host 4.1.2. Dll
The main DLL is always loaded onto the disk as winlogon.lnk in the% PROGRAMDATA% \ Winlogon folder. This file extension is usually associated with a shortcut, but the file is actually a DLL written in Delphi, named by the developer core.dll, as shown in the figure below.

Example of the name of the DLL F4C746696B0F5BB565D445EC49DD912993DE6361
Once launched, the trojan activates the stability mechanism. This can be done in two different ways, depending on the privileges of the victim in the system. If you have administrator rights, the Trojan adds the Windows Update entry to the HKLM \ SOFTWARE \ Microsoft \ Windows \ CurrentVersion \ Run registry. Commands contained in Windows Update will run at the beginning of a user session.
HKLM \ SOFTWARE \ Microsoft \ Windows \ CurrentVersion \ Run \ Windows Update [REG_SZ]
= rundll32.exe “% PROGRAMDATA% \ winlogon.lnk”, DllGetClassObject host
The Trojan also tries to add a task to the Windows Task Scheduler. The task will launch the winlogon.lnk DLL with the same parameters as above. Standard user rights allow the Trojan to add a Windows Update entry with the same data to the registry HKCU \ Software \ Microsoft \ Windows \ CurrentVersion \ Run \:
rundll32.exe “%PROGRAMDATA%\winlogon.lnk”,DllGetClassObject host 4.2. Modified RC4 Algorithm
Despite the known flaws, the RC4 algorithm is regularly used by malware authors. Nevertheless, the creators of RTM modified it a bit - probably to complicate the task of virus analysts. The modified version of RC4 is widely used in malicious RTM tools to encrypt strings, network data, configuration, and modules.
4.2.1. Differences
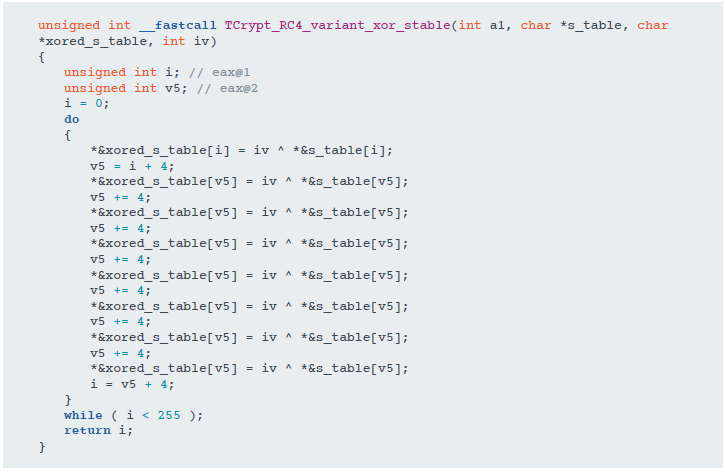
The original RC4 algorithm includes two stages: initialization of the s-block (also known as KSA - Key-Scheduling Algorithm) and generation of a pseudo-random sequence (PRGA - Pseudo-Random Generation Algorithm). The first stage involves the initialization of the s-block using the key; in the second stage, the source text is processed using the s-block for encryption.
The RTM authors added an intermediate step between the initialization of the s-box and encryption. The additional key is a variable and is set at the same time as the data for encryption and decryption. The function that performs this extra step is shown in the figure below.
4.2.2. String Encryption
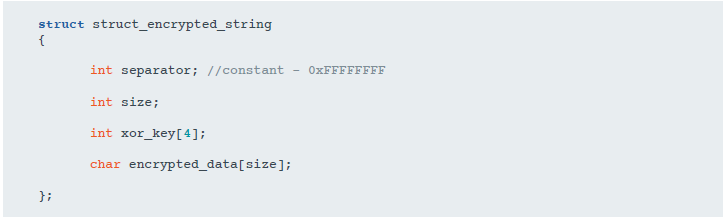
At first glance, there are several readable lines in the main DLL library. The rest are encrypted using the algorithm described above, whose structure is shown in the following figure. We found more than 25 different RC4 keys to encrypt strings in analyzed samples. The XOR key is different for each row. The value of the digital field separating lines is always 0xFFFFFFFF.
At the start of execution, RTM decodes strings into a global variable. When it is necessary to access a string, the trojan dynamically calculates the address of the decrypted strings based on the base address and offset.
The strings contain interesting information about the functions of the malware. Some sample lines are presented in section 6.8.
4.3. Network
The way RTM malware contacts the command server varies from version to version. The first modifications (October 2015 - April 2016) used traditional domain names to update the command list along with the RSS channel on livejournal.com.
Since April 2016, we observed the transition to .bit domains in the telemetry data. This confirms the domain registration date - the first domain RTM fde05d0573da.bit was registered on March 13, 2016.
All the URLs we saw while monitoring the campaign had a common path: /r/z.php. It is rather unusual, and it will help identify RTM requests in network flows.
4.3.1. Channel for commands and control
Older samples used this channel to update their list of command servers. Hosting is on livejournal.com, at the time of preparing the report, it remained at the URL hxxp: // f72bba81c921 (.) Livejournal (.) Com / data / rss.
Livejournal is a Russian-American company providing a platform for blogs. RTM operators create a LiveJournal blog in which they post an article with coded commands - see screenshot.
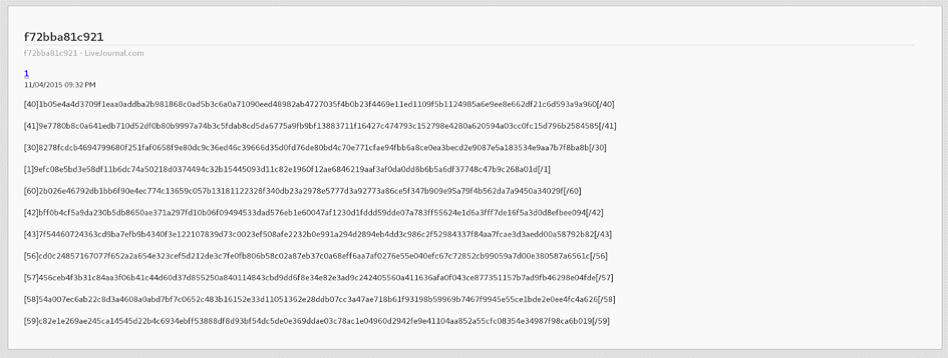
Command and control strings are encoded using the modified RC4 algorithm (Section 4.2). The current version (November 2016) of the channel contains the following command and control server addresses:
- hxxp: // cainmoon (.) net / r / z.php
- hxxp: // rtm (.) dev / 0-3 / z.php
- hxxp: // vpntap (.) top / r / z.php
4.3.2. .Bit domains
In most recent RTM samples, authors connect to C & C domains that use the top level domain TLD .bit. It is not in the list of top-level domains of ICANN (Domain Name and IP Addresses Management Corporation). Instead, it uses the Namecoin system, built on the basis of Bitcoin technology. Malware authors do not often use the .bit TLD for their domains, although an example of such use was previously observed in the version of the Necurs botnet.
Unlike Bitcoin, Namecoin distributed database users have the ability to save data. The main application of this feature is the top-level domain .bit. You can register domains that will be stored in a distributed database. The corresponding entries in the database contain the IP addresses allowed by the domain. This TLD is “censored” because only the registrant can change the resolution of the .bit domain. This means that stopping a malicious domain when using this type of TLD is much more difficult.
RTM Trojan does not build the software needed to read the Namecoin distributed database. It uses central DNS servers, such as dns.dot-bit.org or OpenNic servers, to resolve .bit domains. Therefore, it has the same stability as DNS servers. We observed that some command domains were no longer defined after they were mentioned in the blog entry.
Another advantage of TLD .bit for hackers is cost. To register a domain, operators need to pay only 0.01 NC, which corresponds to $ 0.00185 (as of December 5, 2016). For comparison: domain.com costs at least $ 10.
4.3.3. Protocol
To communicate with the command server, RTM uses HTTP POST requests with data formatted using a custom protocol. The path value is always /r/z.php; Mozilla / 5.0 user agent (compatible; MSIE 9.0; Windows NT 6.1; Trident / 5.0). In requests to the server, the data is formatted as follows, where the offset values are expressed in bytes:
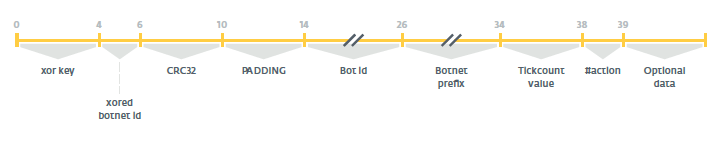
Bytes from 0 to 6 are not encoded; bytes starting at 6 are encoded using the modified RC4 algorithm. The command response package structure is simpler. Bytes are coded from 4 to packet size.
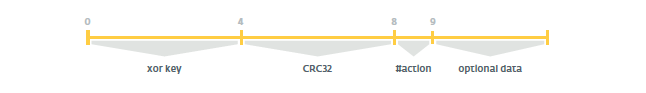
The list of possible byte values of the action is presented in the table below:

The malware always calculates the decrypted CRC32 data and compares it with what is presented in the packet. If they are different, the trojan drops the packet.
Additional data may contain various objects, including a PE file, a file for searching in the file system, or new command URLs.
4.3.4. Panel
We have noticed that RTM uses the panel on command servers. The screenshot below:

4.4. Characteristic feature
RTM is a typical banking trojan. No wonder operators need information about the victim system. On the one hand, the bot collects general information about the OS. On the other hand, it finds out whether the compromised system contains attributes associated with Russian systems of remote banking.
4.4.1. general information
When malware is installed or launched after a reboot, a report containing general information is sent to the command server, including:
- Timezone;
- default system language;
- Authorized user credentials
- process integrity level;
- Username;
- computer name;
- OS version;
- additional installed modules;
- installed antivirus program;
- list of smart card readers.
4.4.2 Remote Banking System
The typical target of a trojan is the RBS system, and RTM is no exception. One of the modules of the program is called TBdo, it performs various tasks, including scanning disks and history of visits.
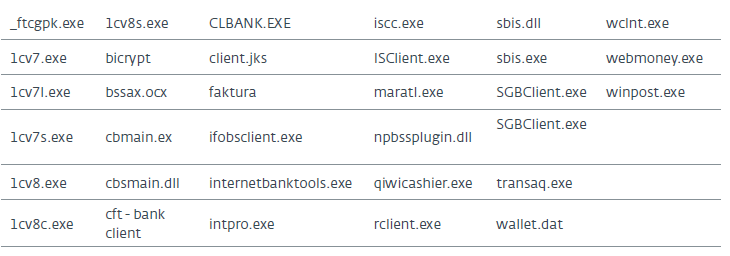
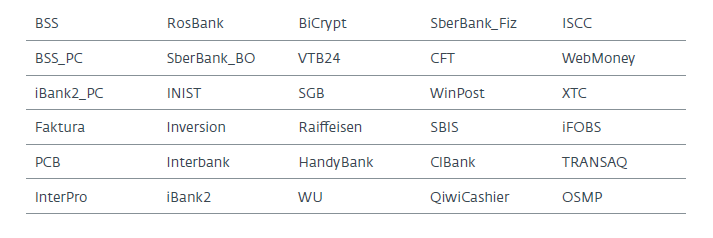
Scanning a disk, the trojan checks whether the banking software is installed on the machine. A complete list of target programs is in the table below. Having found the file of interest, the program sends information to the command server. The following actions depend on the logic given by the command center algorithms (C & C).
RTM also searches for URL patterns in the browser’s browsing history and in open tabs. In addition, the program examines the use of the FindNextUrlCacheEntryA and FindFirstUrlCacheEntryA functions, and also checks each entry for matching the URL to one of the following patterns:
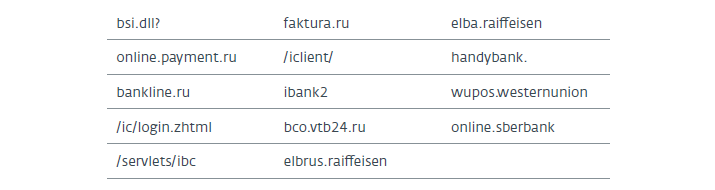
Upon discovering open tabs, the trojan accesses Internet Explorer or Firefox via Dynamic Data Exchange (DDE) to check if the tab matches the pattern.
Checking the history of visits and open tabs is performed in the WHILE loop (a loop with a precondition) with a break of 1 second between checks. Other data that is tracked in real time will be discussed in section 4.5.
If a pattern is found, the program reports this to the command server using a list of rows from the following table:
4.5 Monitoring
During the operation of the Trojan, information about the characteristics of the infected system (including data on the presence of banking software) is sent to the command server. Digital fingerprinting occurs when RTM first launches the monitoring system immediately after the initial scan of the OS.
4.5.1. Remote Banking
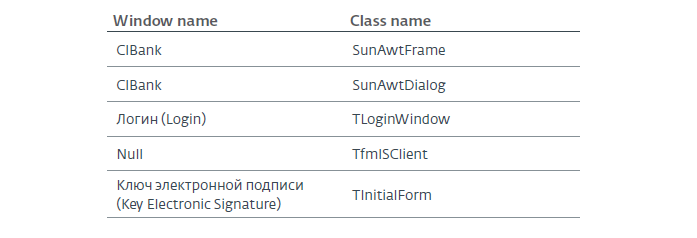
The TBdo module is also responsible for monitoring banking related processes. It uses dynamic data exchange to check tabs in Firefox and Internet Explorer at the time of the initial scan. Another TShell module is used to monitor command windows (Internet Explorer or Explorer).
The module uses the IShellWindows COM interfaces, iWebBrowser, DWebBrowserEvents2 and IConnectionPointContainer to monitor windows. When a user goes to a new web page, the malware marks this. She then compares the URL of the page with the above patterns. When a match is found, the trojan takes six consecutive screenshots with an interval of 5 seconds and sends them to the C & C command server. The program also checks some names of windows related to banking software - the full list below:
4.5.2. Smart card
RTM allows you to monitor smart card readers connected to infected computers. These devices are used in some countries to verify payment orders. If devices of this type are connected to a computer, for a trojan this may indicate the use of the machine for banking transactions.
Unlike other banking Trojans, RTM cannot interact with such smart cards. Perhaps this functionality is included in an additional module that we have not yet seen.
4.5.3. Keylogger
An important part of monitoring an infected PC is intercepting keystrokes. It seems that the RTM developers do not miss any information, as they track not only the usual keys, but also the virtual keyboard and the clipboard.
To do this, use the SetWindowsHookExA function. Attackers register keystrokes or keys corresponding to the virtual keyboard, along with the name and date of the program. The buffer is then sent to the command C & C server.
To intercept the clipboard, use the SetClipboardViewer function. Hackers register the contents of the clipboard when the data is text. Before sending the buffer to the server, the name and date are also recorded.
4.5.4. Screenshots
Another feature of RTM is interception of screenshots. This feature is used when the window monitoring module detects a site or banking software of interest. Screenshots are made using the library of graphic images and transferred to the command server.
4.6. Uninstall
C & C server can stop the operation of malware and clean the computer. The command allows you to clear files and registry entries created during RTM operation. Then, using the DLL library, the malware and the winlogon file are removed, after which the command shuts down the computer. As shown in the figure below, the DLL is removed by developers using erase.dll.

The server can send the destructive uninstall-lock command to the Trojan. In this case, if you have administrator rights, RTM will remove the MBR boot sector on the hard disk. If this fails, the Trojan will attempt to shift the MBR boot sector to a random sector — then the computer will not be able to boot the OS after shutdown. This can lead to a complete reinstallation of the OS, that is, the destruction of evidence.
In the absence of administrative authority, the malware writes .EXEs encoded in the main RTM DLL. The executable file executes the code necessary to shut down the computer and registers the module in the registry section HKCU \ CurrentVersion \ Run. Every time a user starts a session, the computer immediately shuts down.
4.7. configuration file
By default, RTM has almost no configuration file, but the command server can send configuration values that will be stored in the registry and used by the program. The list of configuration keys is presented in the table below:
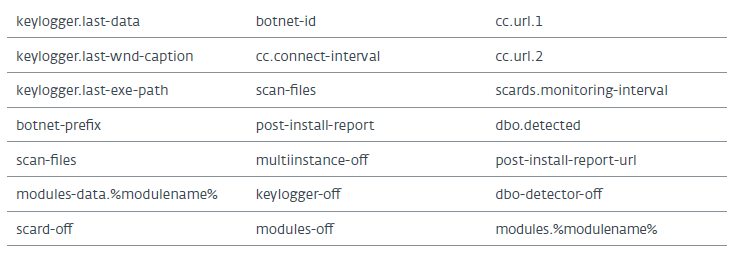
The configuration is stored in the Software [Pseudo-random string] registry key. Each value corresponds to one of the rows presented in the previous table. Values and data are encoded using the RC4 algorithm in RTM.
The data has the same structure as the network or rows. A four-byte XOR key is added at the beginning of the encoded data. For configuration values, the XOR key is different and depends on the size of the value. It can be calculated as follows:
xor_key = (len (config_value) << 24) | (len (config_value) << 16)
| len (config_value) | (len (config_value) << 8)
4.8. Other features
Next, consider the other features that RTM supports.
4.8.1. Additional modules
Trojan includes additional modules that are DLL files. Modules sent from the command C & C server can be executed as external programs, reflected in memory and run in new threads. For storage, the modules are stored in .dtt files and are encoded using the RC4 algorithm with the same key used for network communications.
So far, we have seen the installation of the VNC module (8966319882494077C21F66A8354E2CBCA0370464), the browser data extraction module (03DE8622BE6B2F75A364A275995C3411626C4D9F) and the 1c_2_kl module (B1EE562E1F69CH4C4D9F) (171_6_kl (B1EE562E1F69C6C4D9F) and the module 1c_2_kl (B1EE562E1F69Cht6C4D9F) (CI2_kl (B1EE562E1F6C6D4F9F)), if you are using a 1C_2_kl module (B1EE562E1F69C6D4F9F), you need to apply the default value of 860K4D9F)
To load the VNC module, the command server sends a command requesting connections to the VNC server at a specific IP address on port 44443. The browser's data extraction plugin performs a TBrowserDataCollector, which can read the history of IE. Then it sends the full list of visited URLs to the command C & C server.
The last module found is called 1c_2_kl. It can interact with the 1C Enterprise software package. The module includes two parts: the main part - the DLL and two agents (32-bit and 64-bit), which will be implemented in each process, registering the binding to WH_CBT. Having entered into process 1C, the module binds the functions CreateFile and WriteFile. Whenever the bound CreateFile function is called, the module stores the file path 1c_to_kl.txt in memory. After intercepting the WriteFile call, it calls the WriteFile function and sends the file path 1c_to_kl.txt to the main DLL module, passing it the Windows created WM_COPYDATA message.
The main module of the DLL opens and analyzes the file to determine payment orders. It recognizes the amount and number of transactions contained in the file. This information is sent to the command server. We believe that this module is currently in development, because it contains a debugging message and cannot automatically modify 1c_to_kl.txt.
4.8.2. Privilege escalation
RTM may attempt to elevate privileges by displaying false error messages. Malware mimics the registry scan (see figure below) or uses the real icon of the registry editor. Note the spelling error wait - whait. After a few seconds of scanning, the program displays a false error message.

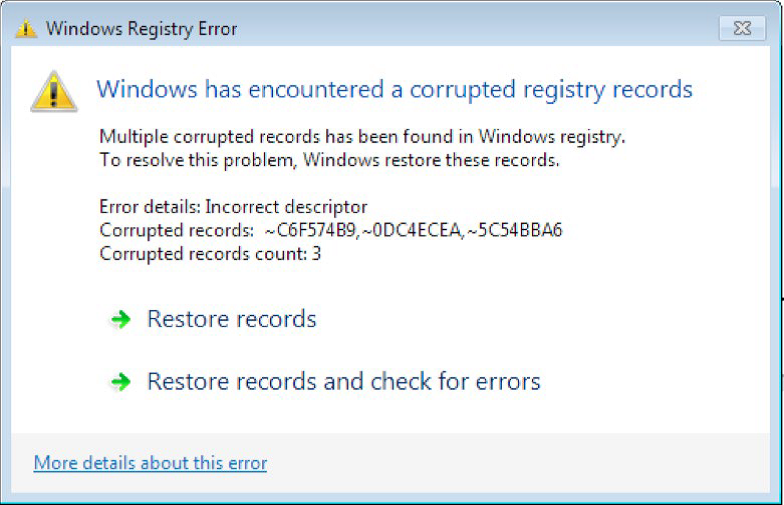
The false message easily deceives the average user, despite the grammatical errors. If the user clicks on one of the two links, RTM will try to elevate its privileges in the system.
After selecting one of the two recovery options, the Trojan launches the DLL using the runas option in the ShellExecute function with administrator privileges. The user will see a real Windows query (see figure below) for elevating permissions. If the user gives the necessary permissions, the trojan will work with administrator privileges.
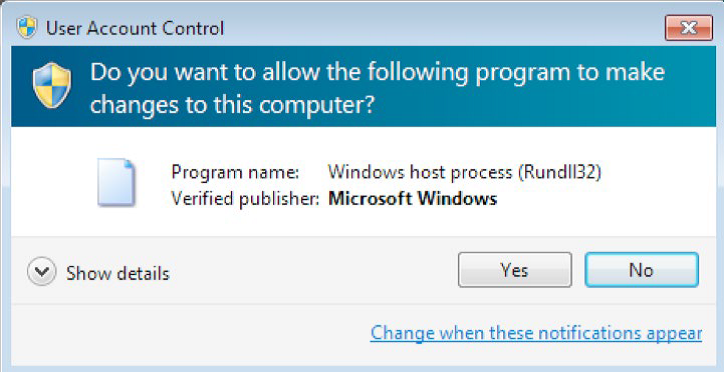
Depending on the default language installed in the system, the trojan displays error messages in Russian or English.
4.8.3. Certificate
RTM can add certificates in the Windows Store and confirm the reliability of the addition by automatically clicking on the "yes" button in the csrss.exe dialog box. This behavior is not new, for example, the banking Trojan Retefe also independently confirms the installation of a new certificate.
4.8.4. Reverse connection
RTM authors also created a Backconnect TCP tunnel. So far we have not seen the function in operation, but it is intended for remote monitoring of infected PCs.
4.8.5. File management node
The command C & C server can send the Trojan a command to modify the Windows host file. The host file is used to create custom DNS permissions.
4.8.6. Find and send file
The server may request to search and download the file in the infected system. For example, during the study we received a request for the file 1c_to_kl.txt. As previously described, this file is generated by the 1C: Enterprise 8 accounting system.
4.8.7. Update
Finally, RTM authors can update the software by sending a new DLL to change the current version.
5. Conclusion
The RTM study shows that the Russian banking system still attracts cyber attackers. Such groups as Buhtrap, Corkow and Carbanak successfully steal money from financial institutions and their clients in Russia. RTM is a new player in this industry.
According to ESET telemetry, malicious RTM tools have been in use since at least the end of 2015. The program has a full range of spyware capabilities, including reading smart cards, intercepting keystrokes and monitoring banking operations, as well as searching for 1C: Enterprise 8 transport files.
The use of a decentralized uncensored top-level domain .bit ensures high infrastructure resilience.
')
Source: https://habr.com/ru/post/322364/
All Articles