Derandomization of the ASLR on any modern processor using JavaScript
Recording cache accesses by the memory management unit (MMU) in the processor as pages are called up using a special pattern designed to detect differences between different levels of the table hierarchy. For example, the “ladder” pattern (on the left) indicates the first level of the hierarchy, that is, PTL1, when calling up 32K pages. For other levels of the hierarchy, there are also methods for identifying
Five researchers from the Free University of Amsterdam (Netherlands) proved the fundamental vulnerability of the ASLR memory protection technique on modern processors. They posted the source code and a detailed description of the AnC attack (ASLR⊕Cache), which affects almost all processors.
The researchers checked AnC on 22 processors of different architectures - and did not find one that would be protected from such an attack on a third-party channel. This is understandable, because in all processors a dynamic translation buffer is used to cache memory addresses, which are translated into virtual addresses. You can protect yourself from this attack only by disabling the processor cache.
Address Space Placement Randomization (ASLR) is a technology used in operating systems that randomly changes the location of important data structures in the process address space, namely, executable file images, loadable libraries, heaps, and stacks. The technology was created to complicate the exploitation of several types of vulnerabilities. It is supposed that it should protect memory from exploits with buffer overflow - ostensibly ASLR will not allow an attacker to know at what specific address data structures are placed after overflow, where you can write the shellcode.
')
In the past, researchers have shown several times that ASLR protection can be circumvented in some cases. For example, if an attacker has full rights in the system, he can break the ASLR at the kernel level of the OS. But in typical conditions - against attack through a browser - ASLR was considered to be quite reliable protection. Now there is no.
In 2016, the same group of Dutch experts showed how to bypass JavaScript ASLR protection in the Microsoft Edge browser using JavaScript, using a third-party memory deduplication channel. Microsoft quickly turned off memory deduplication to protect its users. But this did not solve the ASLR problem at a fundamental level, related to the operation of the memory management unit (MMU) itself in processors.
In modern processors, the MMU module uses cache hierarchy to improve the performance of traversing hierarchical page tables in memory. This is an essential feature of modern processors. The root of the problem is that the L3 cache is available for any third-party applications, including JavaScript scripts from the browser.

Memory organization in a modern Intel processor
Hackers managed to determine by JavaScript means which pages in the page tables most often refer to the MMU module. The accuracy of the determination is quite sufficient for bypassing the ASLR even with an entropy of 36 bits.
Principle of attack
The principle of attack ASLR⊕Cache is based on the fact that as a result of the passage of the MMU on the page tables, they are written to the processor cache. This operation is also carried out during the translation of a virtual address into the corresponding physical address in memory. Thus, a dynamic translation buffer (TLB) in each processor always stores the most recent address translation.
If there is a miss past the TLB cache, then the MMU module will have to go through all the tables of the pages of a particular process (also stored in the main memory) in order to perform the translation. To improve MMU performance in this situation, page tables are cached in the fast cache of the L3 processor to speed up access to them.
It turns out that when using the ASLR security mechanism, the page tables themselves become the keeper of secret information: the initial number of the page table entry (in offset) at each level contains a part of the secret virtual address that was used during the translation.

MMU pass through the page table for translation of the address 0x644b321f4000 to the corresponding memory page on the x86_64 architecture
Hackers developed a special memory scanning technique (they needed better timers than browsers) to determine the cache sets (specific lines in the direct display sectional cache) that the MMU accesses after targeting the page tables when data pointer dereferencing or execution instruction code. Since only certain addresses can correspond to specific sets of caches, obtaining information about these sets gives the initial record numbers of the necessary page table entries at each level of the hierarchy — and thus derandomizes ASLR.
Researchers tested the exploit in Chrome and Firefox on 22 modern processors and showed its successful work.

The success of the attack in Chrome and Firefox and the percentage of false positives
Even built-in protection mechanisms like intentional breakdowns by browser developers of accurate JavaScript timer
performance.now() do not help.
Broken timer performance.now () in Chrome and Firefox
The authors of the exploit wrote their own timer.
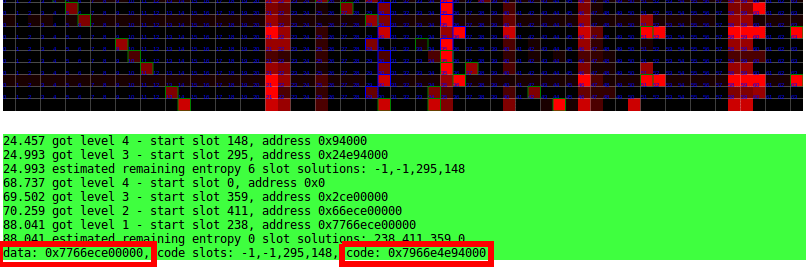
Firefox Attack Show
The attack is tested on the following processors:
| Processor model | Microarchitecture | Year |
| Intel Xeon E3-1240 v5 | Skylake | 2015 |
| Intel Core i7-6700K | Skylake | 2015 |
| Intel Celeron N2840 | Silvermont | 2014 |
| Intel Xeon E5-2658 v2 | Ivy bridge ep | 2013 |
| Intel Atom C2750 | Silvermont | 2013 |
| Intel Core i7-4500U | Haswell | 2013 |
| Intel Core i7-3632QM | Ivy bridge | 2012 |
| Intel Core i7-2620QM | Sandy bridge | 2011 |
| Intel Core i5 M480 | Westmere | 2010 |
| Intel Core i7 920 | Nehalem | 2008 |
| AMD FX-8350 8-Core | Piledriver | 2012 |
| AMD FX-8320 8-Core | Piledriver | 2012 |
| AMD FX-8120 8-Core | Bulldozer | 2011 |
| AMD Athlon II 640 X4 | K10 | 2010 |
| AMD E-350 | Bobcat | 2010 |
| AMD Phenom 9550 4-Core | K10 | 2008 |
| Allwinner A64 | ARM Cortex A53 | 2016 |
| Samsung Exynos 5800 | ARM Cortex A15 | 2014 |
| Samsung Exynos 5800 | ARM Cortex A7 | 2014 |
| Nvidia Tegra K1 CD580M-A1 | ARM Cortex A15 | 2014 |
| Nvidia Tegra K1 CD570M-A1 | ARM Cortex A15; LPAE | 2014 |
At the moment, the AnC attack is documented in four security bulletins:
- CVE-2017-5925 - for Intel processors;
- CVE-2017-5926 - for AMD processors;
- CVE-2017-5927 - for ARM processors;
- CVE-2017-5928 - for javascript-tayer in different browsers.
According to the authors, the only way to protect the user is to use programs like NoScript, which blocks the execution of third-party JavaScript scripts in the browser.
Source: https://habr.com/ru/post/322020/
All Articles