DDoS attacks: attack and defense
News headlines today are full of messages about Distributed Denial of Service (DDoS) attacks. Distributed denial of service attacks are susceptible to any organization present on the Internet. The question is not whether you are attacked or not, but when it will happen. Government agencies, media and e-commerce sites, sites of companies, commercial and non-profit organizations are all potential targets of DDoS attacks .

According to the Central Bank, in 2016, the number of DDoS attacks on Russian financial institutions almost doubled. In November, DDoS attacks were directed at five large Russian banks. At the end of last year, the Central Bank reported on DDoS attacks on financial institutions, including the Central Bank. “The purpose of the attacks was disrupting the services and, as a result, undermining the credibility of these organizations. These attacks were notable for the fact that this was the first large-scale use of the Internet of things in Russia. Basically, Internet video cameras and home routers were involved in the attack, ”noted the security services of large banks.
At the same time, DDoS attacks did not bring significant damage to the banks - they are well protected, therefore such attacks, although they brought trouble, were not critical and did not disrupt any services. Nevertheless, it can be stated that the anti-banking activity of hackers has increased significantly.
')
In February 2017, the technical services of the Ministry of Health of Russia reflected the largest DDoS-attack in recent years, which reached 4 million requests per minute in peak mode. DDoS attacks on state registries were also undertaken, but they were also unsuccessful and did not lead to any data changes.
However, the victims of DDoS attacks are as many organizations and companies that possess such a powerful "defense." In 2017, an increase in damage from cyber threats - extortion programs, DDoS and attacks on Internet of things devices is expected to increase.

IoT devices are becoming increasingly popular as tools for DDoS attacks. A significant event was the DDoS attack undertaken in September 2016 with the help of the malicious code Mirai. In it, hundreds of thousands of cameras and other devices from video surveillance systems acted as means of attack.
It was carried out against the French hosting provider OVH. It was a powerful DDoS attack - almost 1 Tbit / s. Hackers with the help of a botnet used 150 thousand IoT devices, mainly video surveillance cameras. Attacks using the Mirai botnet marked the beginning of the emergence of many botnets from IoT devices. According to experts, in 2017, IoT botnets will continue to be one of the main threats in cyberspace.
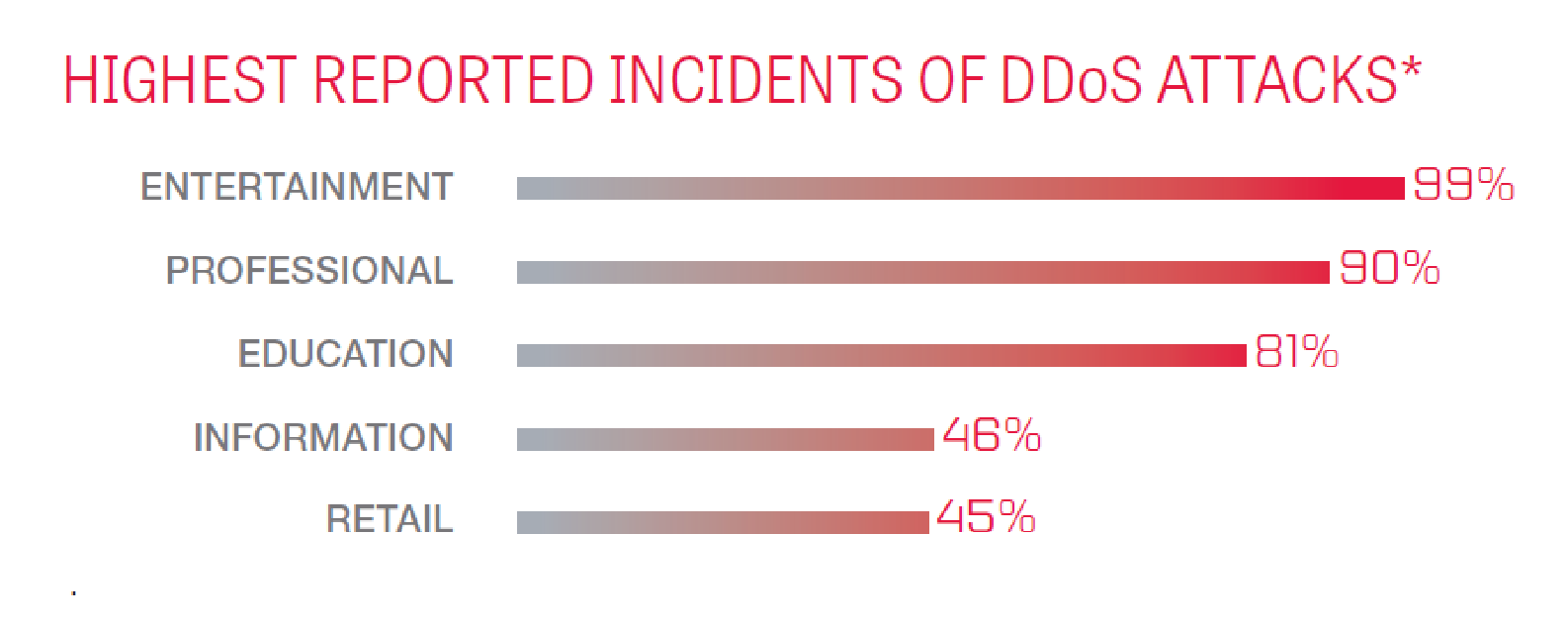
According to the 2016 Verizon data breach incident report (DBIR), the number of DDoS attacks increased markedly last year. In the world, the entertainment industry, professional organizations, education, IT, and retail suffer most of all.
A notable trend of DDoS attacks is the expansion of the “list of victims”. It now includes representatives of almost all industries. In addition, improved methods of attack.
According to Nexusguard, at the end of 2016, the number of mixed-type DDoS attacks increased noticeably — using several vulnerabilities at once. Most often they were subject to financial and government organizations. The main motive of cybercriminals (70% of cases) is data theft or the threat of their destruction for the purpose of ransom. Less often - political or social goals. That is why defense strategy is important. She can prepare for an attack and minimize its consequences, reduce financial and reputational risks.
What are the consequences of a ddos attack? During the attack, the victim loses clients due to the slow work or complete inaccessibility of the site, the reputation of the business suffers. The service provider can block the victim's IP address to minimize damage to other clients. To restore everything, it will take time, and possibly money.

According to a HaltDos survey , DDoS attacks are considered by half of organizations as one of the most serious cyber threats. The danger of DDoS is even higher than the risk of unauthorized access, viruses, fraud and phishing, not to mention other threats.
The average losses from DDoS-attacks around the world are estimated at 50 thousand dollars for small organizations and almost 500 thousand dollars for large enterprises. Addressing the effects of DDoS attacks will require additional staff time, diverting resources from other security projects, developing a software update plan, upgrading equipment, etc.

The reputation of the attacked organization may suffer not only because of the poor performance of the site, but also because of the theft of personal data or financial information.

According to a survey by HaltDos , the number of DDoS attacks is growing annually by 200%, 2,000 attacks of this type are reported daily in the world. The cost of organizing a DDoS attack of weekly duration is only about $ 150, and the casualties of the victim exceed, on average, $ 40,000 per hour.
The main types of DDoS attacks are: massive attacks, attacks at the protocol level, and attacks at the application level. In any case, the goal is to disable the site or to steal data. Another type of cybercrime is the threat of a DDoS attack for ransom. Such hacker groups as Armada Collective, Lizard Squad, RedDoor and ezBTC are famous for this.
The organization of DDoS attacks has become much simpler: there are now widely available automated tools that practically do not require special knowledge from cybercriminals. There are also paid DDoS services for an anonymous target attack. For example, the vDOS service offers its services without checking whether the customer is the owner of the site, who wants to test it "under load", or is this done for the purpose of attack.

DDoS attacks are attacks from many sources that prevent legitimate users from accessing the site under attack. To this end, a huge number of requests are sent to the attacked system, which it cannot handle. Usually compromised systems are used for this purpose.
The annual growth in the number of DDoS attacks is estimated at 50% (according to www.leaseweb.com ), but data from different sources diverge, and not all incidents are known. The average power of DDoS attacks Layer 3/4 has increased in recent years from 20 to several hundred GB / s. Although massive DDoS attacks and attacks at the protocol level are already unpleasant, cybercriminals increasingly combine them with Layer 7 DDoS attacks, that is, at the application level, which are aimed at changing or stealing data. Such "multi-vector" attacks can be very effective.

Multi-vector attacks account for about 27% of the total DDoS attacks.
In the case of a mass DDoS attack (volume based), a large number of requests are used, often sent from legitimate IP addresses, so that the site “chokes” in traffic. The purpose of such attacks is to “score” all available bandwidth and block legitimate traffic.
In the case of a protocol-level attack (for example, UDP or ICMP), the goal is to exhaust system resources. To do this, open requests are sent, for example, TCP / IP requests with fake IP, and as a result of the exhaustion of network resources, it becomes impossible to process legitimate requests. Typical representatives are DDoS attacks, known in narrow circles as Smurf DDos, Ping of Death and SYN flood. Another type of protocol-level DDoS attacks is to send a large number of fragmented packets that the system cannot cope with.
Layer 7 DDoS attacks are sending innocuous-looking requests that appear as the result of normal user actions. Usually botnets and automated tools are used to implement them. Notable examples are Slowloris, Apache Killer, Cross-site scripting, SQL-injection, Remote file injection.
In 2012–2014, most of the massive DDoS attacks were Stateless attacks (without memorizing states and session tracking) —they used the UDP protocol. In the case of Stateless, many packets circulate in one session (for example, opening a page). Who started the session (requested page), stateless devices, as a rule, do not know.
UDP protocol is susceptible to spoofing — replacing an address. For example, if you want to attack the DNS server at 56.26.56.26 using the DNS Amplification attack, you can create a set of packets with the sender address 56.26.56.26 and send them to DNS servers around the world. These servers will send a response to 56.26.56.26.
The same method works for NTP servers, devices with SSDP support. NTP is perhaps the most popular method: in the second half of 2016, it was used in 97.5% of DDoS attacks.
The Best Current Practice (BCP) 38 rule recommends that providers configure gateways to prevent spoofing — the sender's address, the source network is controlled. But not all countries follow this practice. In addition, attackers bypass the control of BCP 38, switching to Stateful attacks, at the TCP level. According to F5 Security Operations Center (SOC), such attacks have dominated in the past five years. In 2016, there were twice as many TCP attacks as UDP attacks.
Layer 7 attacks are mostly resorted to by professional hackers. The principle is as follows: a “heavy” URL (with a PDF file or a request to a large database) is taken and repeated tens or hundreds of times per second. Layer 7 attacks have hard consequences and are difficult to recognize. Now they make up about 10% of DDoS attacks.

The ratio of different types of DDoS attacks according to the Verizon Data Breach Investigations Report (DBIR) (2016).
Often, DDoS attacks coincide with periods of peak traffic, for example, the days of online sales. Large streams of personal and financial data at this time attract hackers.
Domain Name System (Domain Name System, DNS) plays a fundamental role in site performance and availability. Ultimately - in the success of your business. Unfortunately, the DNS infrastructure often becomes the target of DDoS attacks. By suppressing the DNS infrastructure, attackers can damage your site, your company's reputation and affect its financial performance. To counter modern threats, the DNS infrastructure must be very stable and scalable.

Essentially, DNS is a distributed database that, among other things, associates the easy-to-read site names with IP addresses, which allows the user to get to the desired site after entering the URL. The first user interaction with the site begins with DNS requests sent to the DNS server with the Internet address of your site. Their processing can take up to 50% of the load time of a web page. Thus, a decrease in DNS performance can lead to users leaving the site and losses to business. If your DNS server stops responding as a result of a DDoS attack, then no one can get to the site.
DDoS attacks are hard to detect, especially at the beginning when traffic looks normal. DNS infrastructure can be subject to various types of DDoS attacks. Sometimes it is a direct attack on DNS servers. In other cases, exploits are used, using DNS systems to attack other elements of the IT infrastructure or services.

In DNS Reflection attacks, the target is subjected to massive false DNS responses. For this, botnets are used, infecting hundreds and thousands of computers. Each bot in such a network generates several DNS requests, but uses the same IP address of the target (spoofing) as the source IP. The DNS service is responsible for this IP address.
When this is achieved a double effect. The target system is bombarded by thousands and millions of DNS responses, and a DNS server can “lie down” without coping with the load. The DNS query itself is usually less than 50 bytes, the answer is ten times longer. In addition, DNS messages may contain a lot of other information.
Suppose the attacker issued 100,000 short DNS queries of 50 bytes each (only 5 MB). If each answer contains 1 Kbyte, then in total it is already 100 MB. Hence the name - Amplification (gain). The combination of DNS Reflection and Amplification attacks can have very serious consequences.

Requests look like normal traffic, and responses are a lot of large messages sent to the target system.
How to protect against DDoS-attacks, what steps to take? First of all, do not postpone it "for later." Some measures should be taken into account when configuring the network, starting servers and deploying software. And each subsequent change should not increase the vulnerability to DDoS attacks.

How to protect the DNS infrastructure from DDoS attacks? Ordinary firewalls and IPS will not help here, they are powerless against a comprehensive DDoS attack on DNS. In fact, firewalls and intrusion prevention systems themselves are vulnerable to DDoS attacks.

Cloud traffic clearing services can come to the rescue: it is sent to a certain center, where it is checked and redirected back to its destination. These services are useful for TCP traffic. Those who manage their own DNS infrastructure themselves can take the following measures to mitigate the effects of DDoS attacks.
The best way to protect DNS from DDoS attacks is to use the geographically distributed network Anycast. Distributed DNS networks can be implemented using two different approaches: Unicast or Anycast addressing. The first approach is much easier to implement, but the second is much more resistant to DDoS attacks.
In the case of Unicast, each of your company's DNS servers receives a unique IP address. DNS maintains a table of DNS servers for your domain and the corresponding IP addresses. When a user enters a URL, one of the IP addresses is randomly selected to fulfill the request.
With the Anycast addressing scheme, different DNS servers use a common IP address. When the user enters the URL, the collective address of the DNS servers is returned. The IP network routes the request to the nearest server.
Anycast provides fundamental security advantages over Unicast. Unicast provides the IP addresses of individual servers, so attackers can initiate targeted attacks on specific physical servers and virtual machines, and when the resources of this system are exhausted, the service fails. Anycast can help mitigate DDoS attacks by distributing requests among a group of servers. Anycast is also useful to isolate the effects of an attack.
Designing, deploying and operating a global Anycast network takes time, money and know-how. Most IT organizations do not have the expertise and finance to do this. It is possible to entrust the maintenance of the infrastructure of a DNS provider to a provider of managed services that specializes in DNS. They have the necessary knowledge to protect the DNS from DDoS attacks.
Managed DNS service providers operate large-scale Anycast networks and have points of presence around the world. Network security experts monitor the network 24/7/365 and use special tools to mitigate the effects of DDoS attacks.

Some hosting providers also offer DDoS protection services: network traffic analysis is performed 24/7, so your site will be relatively secure. Such protection is able to withstand powerful attacks - up to 1500 Gbit / s. Paid for this traffic.
Another option is IP address security. The provider places the IP address that the client has selected as protected, in a special network analyzer. When attacking, traffic to the client is matched with known attack patterns. As a result, the client receives only pure, filtered traffic. Thus, site users may not know that an attack was made on it. To organize this, a distributed network of filtering nodes is created so that for each attack you can select the closest node and minimize the delay in traffic transmission.
The result of using DDoS protection services will be the timely detection and prevention of DDoS attacks, the continuity of the site’s operation and its constant availability to users, the minimization of financial and reputational losses from site or portal downtime.

Who is attacked?
According to the Central Bank, in 2016, the number of DDoS attacks on Russian financial institutions almost doubled. In November, DDoS attacks were directed at five large Russian banks. At the end of last year, the Central Bank reported on DDoS attacks on financial institutions, including the Central Bank. “The purpose of the attacks was disrupting the services and, as a result, undermining the credibility of these organizations. These attacks were notable for the fact that this was the first large-scale use of the Internet of things in Russia. Basically, Internet video cameras and home routers were involved in the attack, ”noted the security services of large banks.
At the same time, DDoS attacks did not bring significant damage to the banks - they are well protected, therefore such attacks, although they brought trouble, were not critical and did not disrupt any services. Nevertheless, it can be stated that the anti-banking activity of hackers has increased significantly.
')
In February 2017, the technical services of the Ministry of Health of Russia reflected the largest DDoS-attack in recent years, which reached 4 million requests per minute in peak mode. DDoS attacks on state registries were also undertaken, but they were also unsuccessful and did not lead to any data changes.
However, the victims of DDoS attacks are as many organizations and companies that possess such a powerful "defense." In 2017, an increase in damage from cyber threats - extortion programs, DDoS and attacks on Internet of things devices is expected to increase.

IoT devices are becoming increasingly popular as tools for DDoS attacks. A significant event was the DDoS attack undertaken in September 2016 with the help of the malicious code Mirai. In it, hundreds of thousands of cameras and other devices from video surveillance systems acted as means of attack.
It was carried out against the French hosting provider OVH. It was a powerful DDoS attack - almost 1 Tbit / s. Hackers with the help of a botnet used 150 thousand IoT devices, mainly video surveillance cameras. Attacks using the Mirai botnet marked the beginning of the emergence of many botnets from IoT devices. According to experts, in 2017, IoT botnets will continue to be one of the main threats in cyberspace.

According to the 2016 Verizon data breach incident report (DBIR), the number of DDoS attacks increased markedly last year. In the world, the entertainment industry, professional organizations, education, IT, and retail suffer most of all.
A notable trend of DDoS attacks is the expansion of the “list of victims”. It now includes representatives of almost all industries. In addition, improved methods of attack.
According to Nexusguard, at the end of 2016, the number of mixed-type DDoS attacks increased noticeably — using several vulnerabilities at once. Most often they were subject to financial and government organizations. The main motive of cybercriminals (70% of cases) is data theft or the threat of their destruction for the purpose of ransom. Less often - political or social goals. That is why defense strategy is important. She can prepare for an attack and minimize its consequences, reduce financial and reputational risks.
Consequences of attacks
What are the consequences of a ddos attack? During the attack, the victim loses clients due to the slow work or complete inaccessibility of the site, the reputation of the business suffers. The service provider can block the victim's IP address to minimize damage to other clients. To restore everything, it will take time, and possibly money.

According to a HaltDos survey , DDoS attacks are considered by half of organizations as one of the most serious cyber threats. The danger of DDoS is even higher than the risk of unauthorized access, viruses, fraud and phishing, not to mention other threats.
The average losses from DDoS-attacks around the world are estimated at 50 thousand dollars for small organizations and almost 500 thousand dollars for large enterprises. Addressing the effects of DDoS attacks will require additional staff time, diverting resources from other security projects, developing a software update plan, upgrading equipment, etc.

The reputation of the attacked organization may suffer not only because of the poor performance of the site, but also because of the theft of personal data or financial information.

According to a survey by HaltDos , the number of DDoS attacks is growing annually by 200%, 2,000 attacks of this type are reported daily in the world. The cost of organizing a DDoS attack of weekly duration is only about $ 150, and the casualties of the victim exceed, on average, $ 40,000 per hour.
Types of DDoS Attacks
The main types of DDoS attacks are: massive attacks, attacks at the protocol level, and attacks at the application level. In any case, the goal is to disable the site or to steal data. Another type of cybercrime is the threat of a DDoS attack for ransom. Such hacker groups as Armada Collective, Lizard Squad, RedDoor and ezBTC are famous for this.
The organization of DDoS attacks has become much simpler: there are now widely available automated tools that practically do not require special knowledge from cybercriminals. There are also paid DDoS services for an anonymous target attack. For example, the vDOS service offers its services without checking whether the customer is the owner of the site, who wants to test it "under load", or is this done for the purpose of attack.

DDoS attacks are attacks from many sources that prevent legitimate users from accessing the site under attack. To this end, a huge number of requests are sent to the attacked system, which it cannot handle. Usually compromised systems are used for this purpose.
The annual growth in the number of DDoS attacks is estimated at 50% (according to www.leaseweb.com ), but data from different sources diverge, and not all incidents are known. The average power of DDoS attacks Layer 3/4 has increased in recent years from 20 to several hundred GB / s. Although massive DDoS attacks and attacks at the protocol level are already unpleasant, cybercriminals increasingly combine them with Layer 7 DDoS attacks, that is, at the application level, which are aimed at changing or stealing data. Such "multi-vector" attacks can be very effective.

Multi-vector attacks account for about 27% of the total DDoS attacks.
In the case of a mass DDoS attack (volume based), a large number of requests are used, often sent from legitimate IP addresses, so that the site “chokes” in traffic. The purpose of such attacks is to “score” all available bandwidth and block legitimate traffic.
In the case of a protocol-level attack (for example, UDP or ICMP), the goal is to exhaust system resources. To do this, open requests are sent, for example, TCP / IP requests with fake IP, and as a result of the exhaustion of network resources, it becomes impossible to process legitimate requests. Typical representatives are DDoS attacks, known in narrow circles as Smurf DDos, Ping of Death and SYN flood. Another type of protocol-level DDoS attacks is to send a large number of fragmented packets that the system cannot cope with.
Layer 7 DDoS attacks are sending innocuous-looking requests that appear as the result of normal user actions. Usually botnets and automated tools are used to implement them. Notable examples are Slowloris, Apache Killer, Cross-site scripting, SQL-injection, Remote file injection.
In 2012–2014, most of the massive DDoS attacks were Stateless attacks (without memorizing states and session tracking) —they used the UDP protocol. In the case of Stateless, many packets circulate in one session (for example, opening a page). Who started the session (requested page), stateless devices, as a rule, do not know.
UDP protocol is susceptible to spoofing — replacing an address. For example, if you want to attack the DNS server at 56.26.56.26 using the DNS Amplification attack, you can create a set of packets with the sender address 56.26.56.26 and send them to DNS servers around the world. These servers will send a response to 56.26.56.26.
The same method works for NTP servers, devices with SSDP support. NTP is perhaps the most popular method: in the second half of 2016, it was used in 97.5% of DDoS attacks.
The Best Current Practice (BCP) 38 rule recommends that providers configure gateways to prevent spoofing — the sender's address, the source network is controlled. But not all countries follow this practice. In addition, attackers bypass the control of BCP 38, switching to Stateful attacks, at the TCP level. According to F5 Security Operations Center (SOC), such attacks have dominated in the past five years. In 2016, there were twice as many TCP attacks as UDP attacks.
Layer 7 attacks are mostly resorted to by professional hackers. The principle is as follows: a “heavy” URL (with a PDF file or a request to a large database) is taken and repeated tens or hundreds of times per second. Layer 7 attacks have hard consequences and are difficult to recognize. Now they make up about 10% of DDoS attacks.

The ratio of different types of DDoS attacks according to the Verizon Data Breach Investigations Report (DBIR) (2016).
Often, DDoS attacks coincide with periods of peak traffic, for example, the days of online sales. Large streams of personal and financial data at this time attract hackers.
DDoS attacks on DNS
Domain Name System (Domain Name System, DNS) plays a fundamental role in site performance and availability. Ultimately - in the success of your business. Unfortunately, the DNS infrastructure often becomes the target of DDoS attacks. By suppressing the DNS infrastructure, attackers can damage your site, your company's reputation and affect its financial performance. To counter modern threats, the DNS infrastructure must be very stable and scalable.

Essentially, DNS is a distributed database that, among other things, associates the easy-to-read site names with IP addresses, which allows the user to get to the desired site after entering the URL. The first user interaction with the site begins with DNS requests sent to the DNS server with the Internet address of your site. Their processing can take up to 50% of the load time of a web page. Thus, a decrease in DNS performance can lead to users leaving the site and losses to business. If your DNS server stops responding as a result of a DDoS attack, then no one can get to the site.
DDoS attacks are hard to detect, especially at the beginning when traffic looks normal. DNS infrastructure can be subject to various types of DDoS attacks. Sometimes it is a direct attack on DNS servers. In other cases, exploits are used, using DNS systems to attack other elements of the IT infrastructure or services.

In DNS Reflection attacks, the target is subjected to massive false DNS responses. For this, botnets are used, infecting hundreds and thousands of computers. Each bot in such a network generates several DNS requests, but uses the same IP address of the target (spoofing) as the source IP. The DNS service is responsible for this IP address.
When this is achieved a double effect. The target system is bombarded by thousands and millions of DNS responses, and a DNS server can “lie down” without coping with the load. The DNS query itself is usually less than 50 bytes, the answer is ten times longer. In addition, DNS messages may contain a lot of other information.
Suppose the attacker issued 100,000 short DNS queries of 50 bytes each (only 5 MB). If each answer contains 1 Kbyte, then in total it is already 100 MB. Hence the name - Amplification (gain). The combination of DNS Reflection and Amplification attacks can have very serious consequences.

Requests look like normal traffic, and responses are a lot of large messages sent to the target system.
How to protect against DDoS attacks?
How to protect against DDoS-attacks, what steps to take? First of all, do not postpone it "for later." Some measures should be taken into account when configuring the network, starting servers and deploying software. And each subsequent change should not increase the vulnerability to DDoS attacks.

- Security code. When writing software, security considerations must be taken into account. It is recommended to follow the standards of "secure coding" and thoroughly test the software to avoid typical errors and vulnerabilities, such as cross-site scripts and SQL injections.
- Develop an action plan for software upgrades. There should always be a possibility of a “rollback” in the event that something goes wrong.
- Update software in a timely manner. If it was possible to roll updates, but there were problems, see p.2.
- Do not forget about access restriction. Admin accounts and / or should be protected by strong and regularly changed passwords. Also required is a periodic audit of access rights, timely deletion of accounts of retired employees.
- The admin interface should be accessible only from the internal network or via VPN. Close VPN access for retired and especially dismissed employees in a timely manner.
- Include disaster recovery for DDoS attacks. The plan should include ways of identifying the fact of such an attack, contacts for communication with an Internet or hosting provider, and an “escalation problem” tree for each department.
- Scanning for vulnerabilities will help identify problems in your infrastructure and software, reducing risks. A simple OWASP Top 10 Vulnerability test will reveal the most critical problems. Penetration tests will also be useful - they will help to find weak spots.
- Hardware protection against DDoS attacks can be expensive. If your budget does not provide this, then a good alternative is to protect against DDoS “on demand”. This service can be enabled by simply changing the traffic routing scheme in an emergency, or it is constantly protected.
- Use a CDN partner. Content Delivery Networks allow you to deliver site content via a distributed network. Traffic is distributed across multiple servers, reducing the delay in accessing users, including geographically remote ones. Thus, although the main advantage of a CDN is speed, it also serves as a barrier between the main server and users.
- Use Web Application Firewall - firewall for web applications. It monitors traffic between the site or application and the browser, checking the legitimacy of requests. Working at the application level, WAF can detect attacks on stored patterns and detect unusual behavior. Application-level attacks are not uncommon in e-commerce. As with the CDN, you can use WAF services in the cloud. However, configuring rules requires some experience. Ideally, all major applications should be secured with WAF.
DNS security
How to protect the DNS infrastructure from DDoS attacks? Ordinary firewalls and IPS will not help here, they are powerless against a comprehensive DDoS attack on DNS. In fact, firewalls and intrusion prevention systems themselves are vulnerable to DDoS attacks.

Cloud traffic clearing services can come to the rescue: it is sent to a certain center, where it is checked and redirected back to its destination. These services are useful for TCP traffic. Those who manage their own DNS infrastructure themselves can take the following measures to mitigate the effects of DDoS attacks.
- Monitoring DNS servers for suspicious activity is the first step in protecting the DNS infrastructure. Commercial DNS solutions and open source products such as BIND provide real-time statistics that can be used to detect DDoS attacks. Monitoring DDoS attacks can be a resource-intensive task. It is best to create a basic infrastructure profile under normal operating conditions and then update it from time to time as infrastructure develops and traffic patterns change.
- Additional DNS server resources will help to cope with small-scale attacks due to redundancy of the DNS infrastructure. Server resources and network resources should suffice not to handle a larger volume of requests. Of course, redundancy costs money. You pay for server and network resources that are not normally used under normal conditions. And with a significant "margin" of power, this approach is unlikely to be effective.
- Enabling DNS Response Rate Limiting (RRL) will reduce the likelihood that the server will be involved in the DDoS Reflection attack - it will decrease the speed of its reaction to repeated requests. RRLs are supported by many DNS implementations.
- Use high availability configurations. You can protect against DDoS attacks by deploying DNS on a high availability server (HA). If one physical server “falls” as a result of the attack, the DNS service can be restored on the backup server.
The best way to protect DNS from DDoS attacks is to use the geographically distributed network Anycast. Distributed DNS networks can be implemented using two different approaches: Unicast or Anycast addressing. The first approach is much easier to implement, but the second is much more resistant to DDoS attacks.
In the case of Unicast, each of your company's DNS servers receives a unique IP address. DNS maintains a table of DNS servers for your domain and the corresponding IP addresses. When a user enters a URL, one of the IP addresses is randomly selected to fulfill the request.
With the Anycast addressing scheme, different DNS servers use a common IP address. When the user enters the URL, the collective address of the DNS servers is returned. The IP network routes the request to the nearest server.
Anycast provides fundamental security advantages over Unicast. Unicast provides the IP addresses of individual servers, so attackers can initiate targeted attacks on specific physical servers and virtual machines, and when the resources of this system are exhausted, the service fails. Anycast can help mitigate DDoS attacks by distributing requests among a group of servers. Anycast is also useful to isolate the effects of an attack.
DDoS protection provided by the provider
Designing, deploying and operating a global Anycast network takes time, money and know-how. Most IT organizations do not have the expertise and finance to do this. It is possible to entrust the maintenance of the infrastructure of a DNS provider to a provider of managed services that specializes in DNS. They have the necessary knowledge to protect the DNS from DDoS attacks.
Managed DNS service providers operate large-scale Anycast networks and have points of presence around the world. Network security experts monitor the network 24/7/365 and use special tools to mitigate the effects of DDoS attacks.

Some hosting providers also offer DDoS protection services: network traffic analysis is performed 24/7, so your site will be relatively secure. Such protection is able to withstand powerful attacks - up to 1500 Gbit / s. Paid for this traffic.
Another option is IP address security. The provider places the IP address that the client has selected as protected, in a special network analyzer. When attacking, traffic to the client is matched with known attack patterns. As a result, the client receives only pure, filtered traffic. Thus, site users may not know that an attack was made on it. To organize this, a distributed network of filtering nodes is created so that for each attack you can select the closest node and minimize the delay in traffic transmission.
The result of using DDoS protection services will be the timely detection and prevention of DDoS attacks, the continuity of the site’s operation and its constant availability to users, the minimization of financial and reputational losses from site or portal downtime.
Source: https://habr.com/ru/post/321992/
All Articles