Terminal Server User Authentication on FirePOWER

For us, engineers, to monitor the emergence of new versions of FirePOWER is a real pleasure. Each time, opening the regular Release Notes, we are with a sinking heart (and sometimes with a full stop) studying the new features added by the developers.
One of the long-awaited innovations was the Cisco Terminal Server Agent (hereinafter TS Agent). It is intended for correct authentication of users of terminal servers (hereinafter TC). In this article I will tell why it is needed and how it works.
Let me remind you that the authentication problem on the TS is that in most solutions like FirePOWER, it works by the IP address, which is the same for all TS users.
')
For example, Vasily and Peter simultaneously work on a terminal server. According to corporate rules, Vasily can attend social. network, and Pete - no. ITU will not be able to separate the traffic of Vasily and Peter from each other without having additional information other than an IP address. Therefore, either both employees will be denied access to social. network, or both allowed.
There are different ways to solve a problem. For example, the "crutch" option using IP Virtualization technology on the vehicle. In this case, each new session on the vehicle will be assigned a unique IP address. But immediately it is worth noting that this approach has many nuances.
The Cisco WSA Web Proxy introduces the concept of Session-cookies (session fingerprint). Thanks to information from session-cookies, WSA can distinguish users with the same IP address. But there is a drawback: cookies can only be used for browser sessions. Applications that do not support cookies will not work (Skype, TeamViewer, etc.).
Using an agent installed on a vehicle is the most universal method of solving a problem. Identity Agent has long existed for Checkpoint solutions. Now, finally, Cisco has introduced a similar solution for ITU based on FirePOWER. The announcement took place on August 29, 2016 (we mentioned it here, UPD (09/02/2016)). But the agent became available for download only on January 26, 2017. From the official Release Notes for version 6.1 of the FirePOWER Management Center (FMC, FirePOWER control system), information about the terminal agent was removed and migrated to Release Notes for 6.2. Thus, the terminal agent is supported on FMC, starting with version 6.2.
How the agent works
The idea is as simple as slippers. For each TS user, the source tcp / udp ports of the launched sessions are translated to a specific port pool. Yes, yes, it is broadcast. PAT occurs. When the agent is installed on the server, a special low-level driver is added, which deals with the conversion of tcp / udp ports.
User mapping and port pool information is passed to the FMC (FirePOWER Management Center) control center via the REST API.
The agent is downloaded from cisco.com as an installation exe file. After completing the installation on the vehicle, the agent settings window opens:
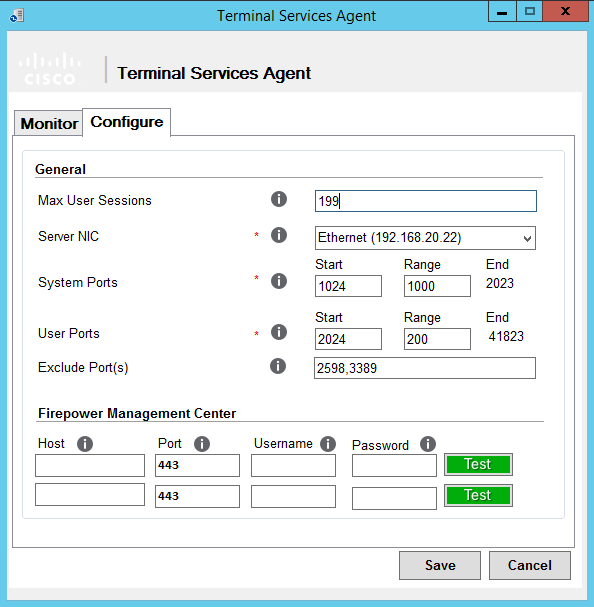
Here we can specify how many users can simultaneously use the server (Max User Sessions). In this version of the agent 199 users - the maximum.
We select the server's network card, and which ports we can and cannot use for broadcasting.
For the system to work, you must specify the IP address of the FMC and the user who has the rights to use REST VDI. By default, the following user roles have rights:
- Access Admin
- Admin
- Network admin
You can create a separate role for the agent on the FMC, which I did for the test.
System → Users → User Roles tab. Click Create User Role:
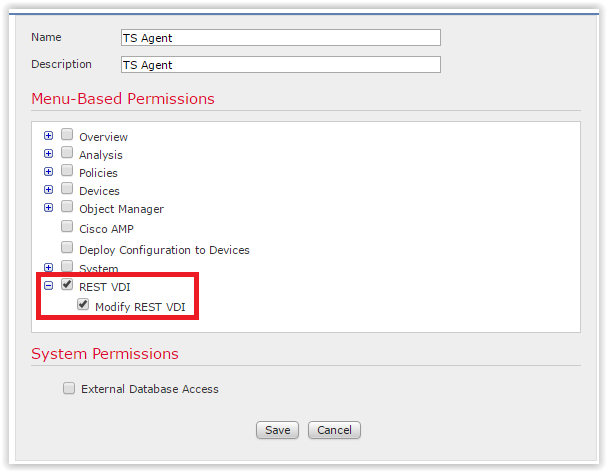
Choose from the submenu "Rest VDI".
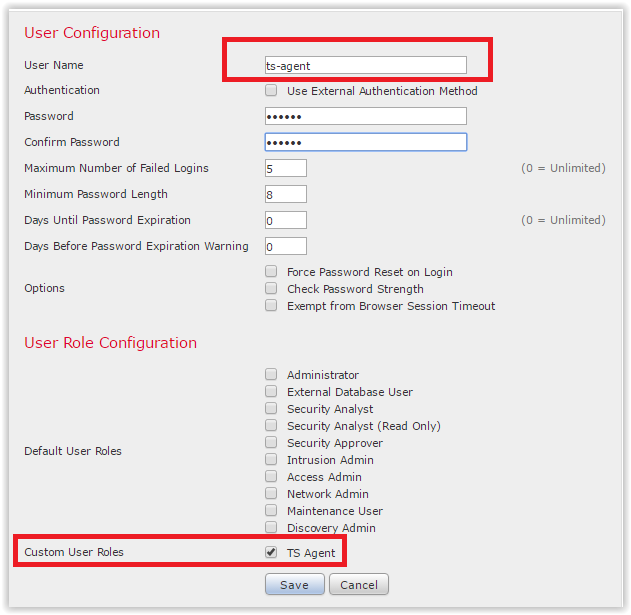
Next, create a user ts-agent and assign the newly created TS Agent role to it. On the Users tab, click Create User:
We return to the agent, enter the IP address of the FMC, the user ts-agent and its password. Click Test:
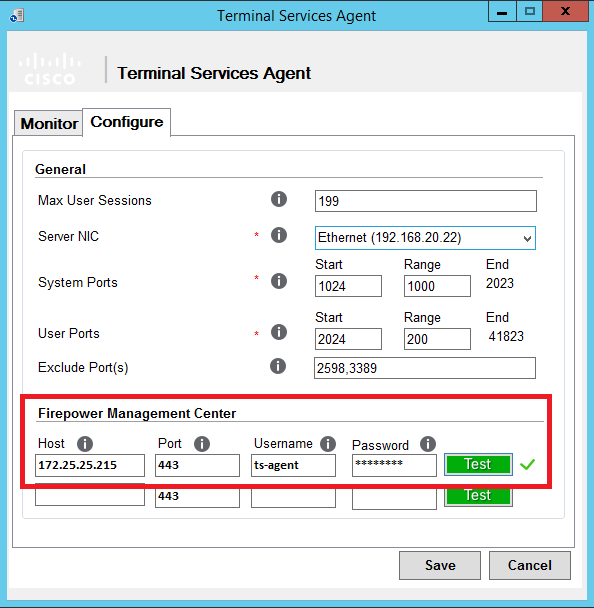
Click Save. Here is the nuance: the agent will ask to restart the server. Do nothing, obey the will of the soulless machine. By the way (or not by the way), making any changes in the settings of the agent also requires a reboot.
All is ready. You can check what happened. We make two rules for access to FMC. The first rule for a group of AD "IT-department", it will be allowed full access to the Internet. The second rule for all other users. According to this rule, we block access to social services. networks. Setup:

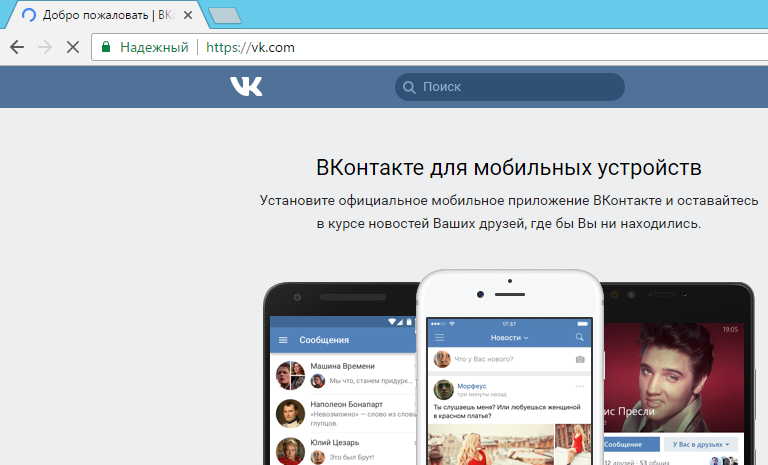
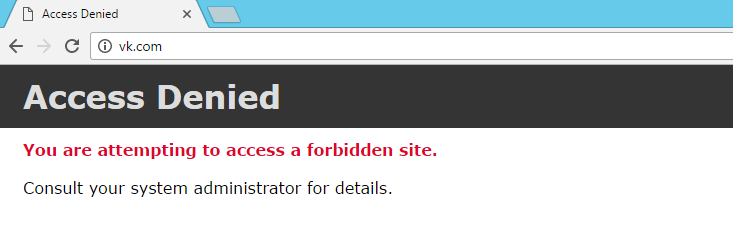
We go under two users on the vehicle. The first user “Uskov” is a member of the IT department. The second user “Vasiliy” is not included in the IT department. Accordingly, for “Uskov” it will be allowed to go to social. network, for "Vasiliy" - is prohibited. We are checking.
For "Uskov":
For Vasiliy:
Fuh, not deceived ciskodely, works! Let's see the logs. The agent can see which port ranges are issued to users:
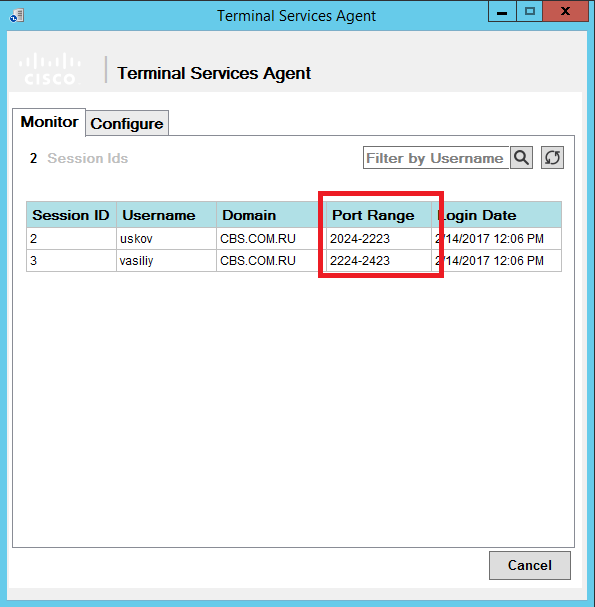
Information on ports appeared on the FMC tab Analysis → Users → User Activity:

Everything works as intended.
What agent is installed on
- Windows Server 2008 R2;
- Windows Server 2012;
- Windows Server 2012 R2.
The following virtualization systems are supported:
- Citrix xendesktop
- Citrix xenapp
- Xen Project Hypervisor
- VMware vSphere Hypervisor / VMware ESXi 6.0
- Windows Terminal Services / Windows Remote Desktop Services (RDS)
Limitations and notes for the first version of the agent (1.0.0-36)
- Up to 199 users on the vehicle;
- Only one TC network card can be used;
- Time on the vehicle must be synchronized with the time on the FMC;
- On FMC, user information obtained from TS Agent is more priority than information from other sources of passive authentication: User Agent and Cisco ISE. This is logical, otherwise there would be no miracle. Active authentication should not be used in conjunction with the TS Agent.
Source: https://habr.com/ru/post/321876/
All Articles