Advanced Threat Protection in Windows Defender
In early February, we told you about the detection of criminals using the ATP service in Windows Defender. In the comments there were various questions regarding the work of the service, so we decided to share a detailed description of its functionality.

In short, the ATP service in Windows Defender is a security service that allows you to detect security threats in your networks, investigate them and take countermeasures. The service is based on a combination of technologies built in Windows 10 and the Microsoft cloud service. These technologies include:
Schematically, these service components are presented below.
')
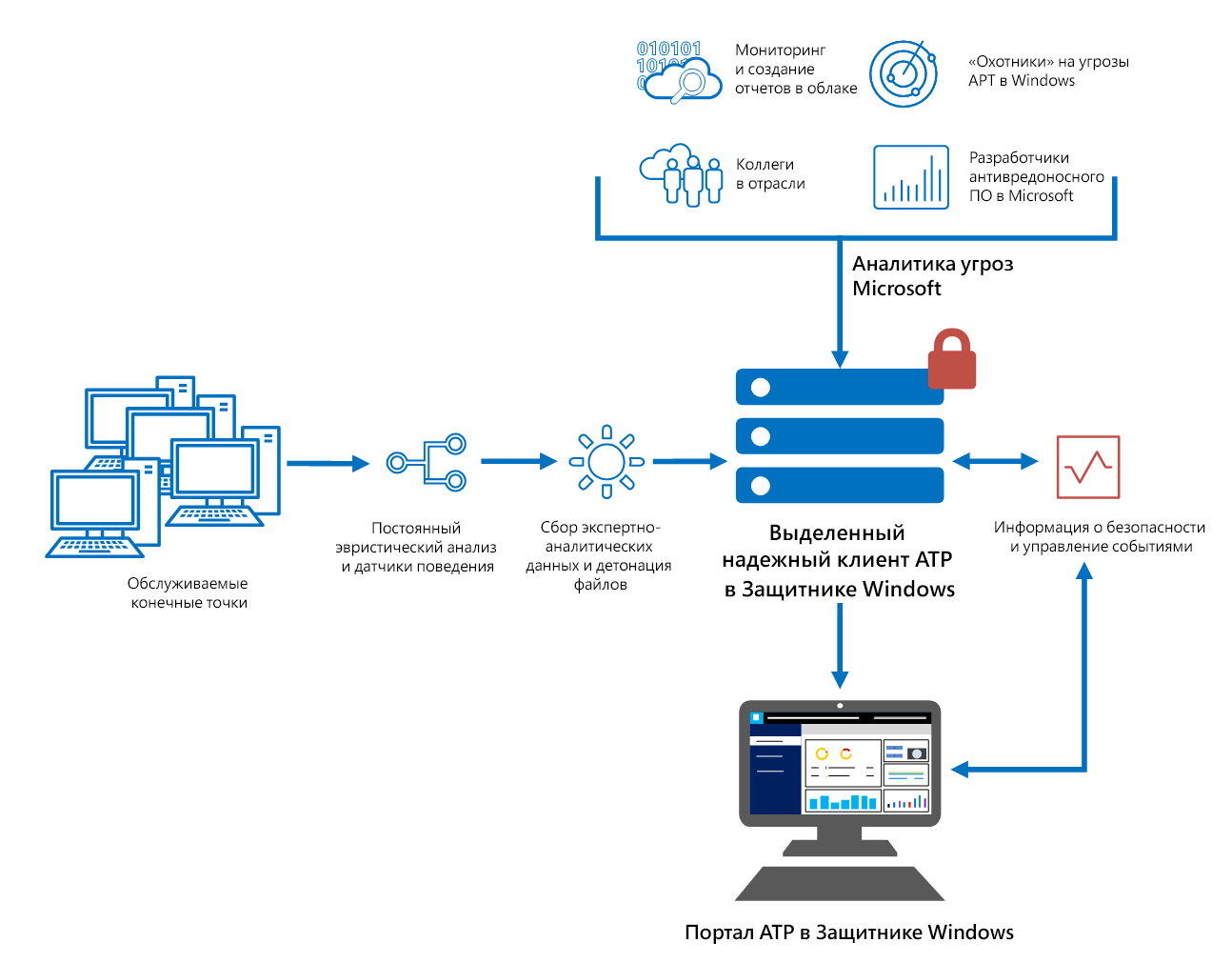
The capabilities of the host research service allow you to receive detailed alerts, understand the nature and scope of a possible invasion.
The ATP service in Windows Defender works with various Windows security technologies:
It can also work in parallel with third-party security solutions.
ATP Portal can be used to monitor and respond to threats. It solves the following tasks:
The portal interface includes four main work areas:
With the settings, everything is quite obvious.
The following views are available in the Navigation Panel:

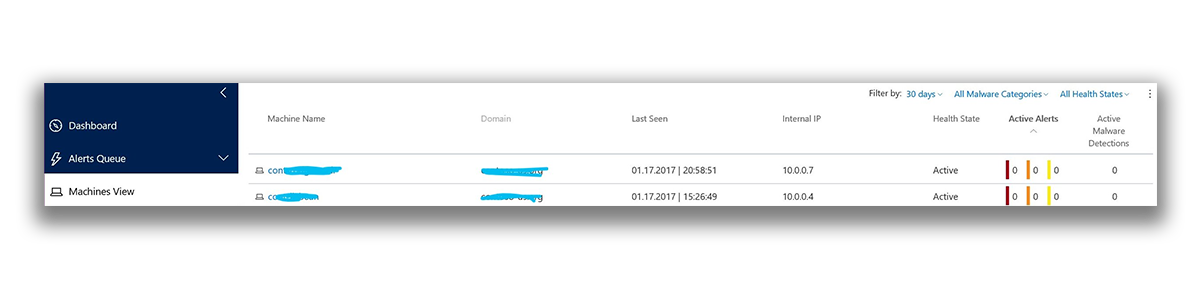
The computers section displays a list of computers that are protected by the ATP service, and some information about them.
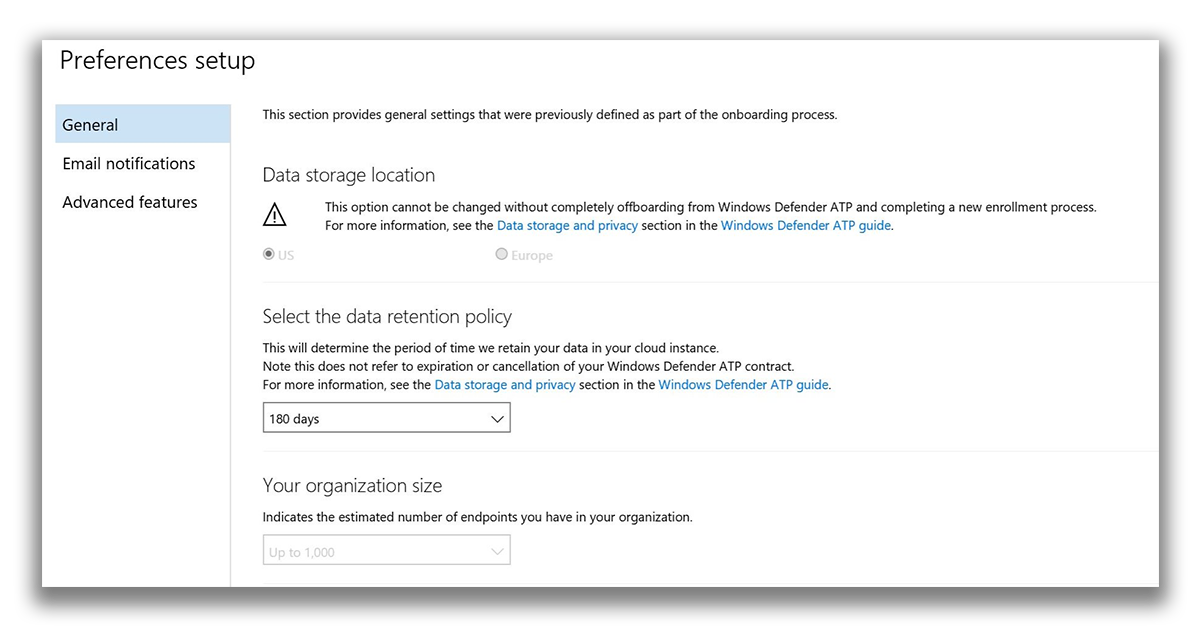
Setting priorities allows you to set up email notifications or a data retention policy (in other words, how much data will be stored in the tenant).
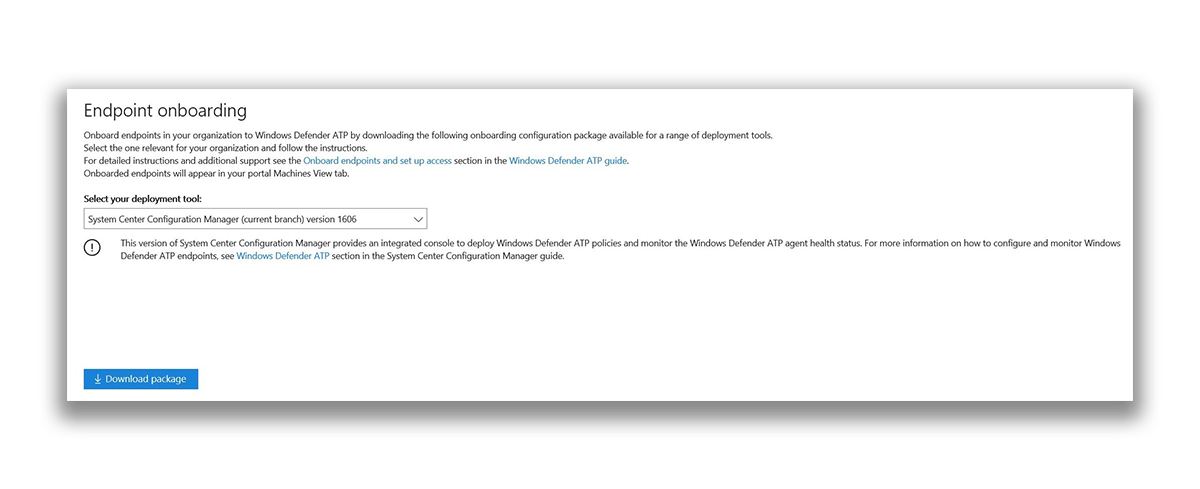
In the host management section , you can download a package to prepare machines for working with ATP.
The ATP service and uses the following conventions:
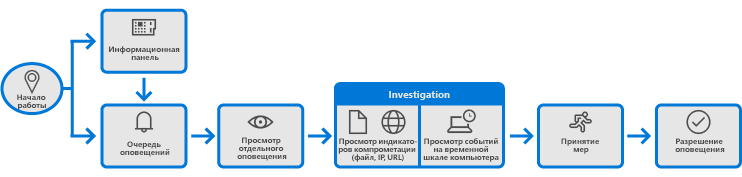
In general, the approach to researching security breaches using ATP can be broken down into the following steps:
Since we start working with ATP with data analysis on the information panel, we will consider it in more detail. Information about alerts and computers allows you to quickly establish the fact, place and time of suspicious activity on the network - this provides the necessary context for understanding the situation. It also displays a summary of event data that helps identify significant events or behavior on a computer. You can also open event and indicator details at a lower level. Active tiles give visual clues to evaluate the overall state of the security systems. Clicking on such a tile opens a detailed view of the corresponding component.
When you click on the ATP Alerts tile, the total number of active ATP alerts on the network for the last 30 days is displayed. Alerts are divided into two groups: New and Running.
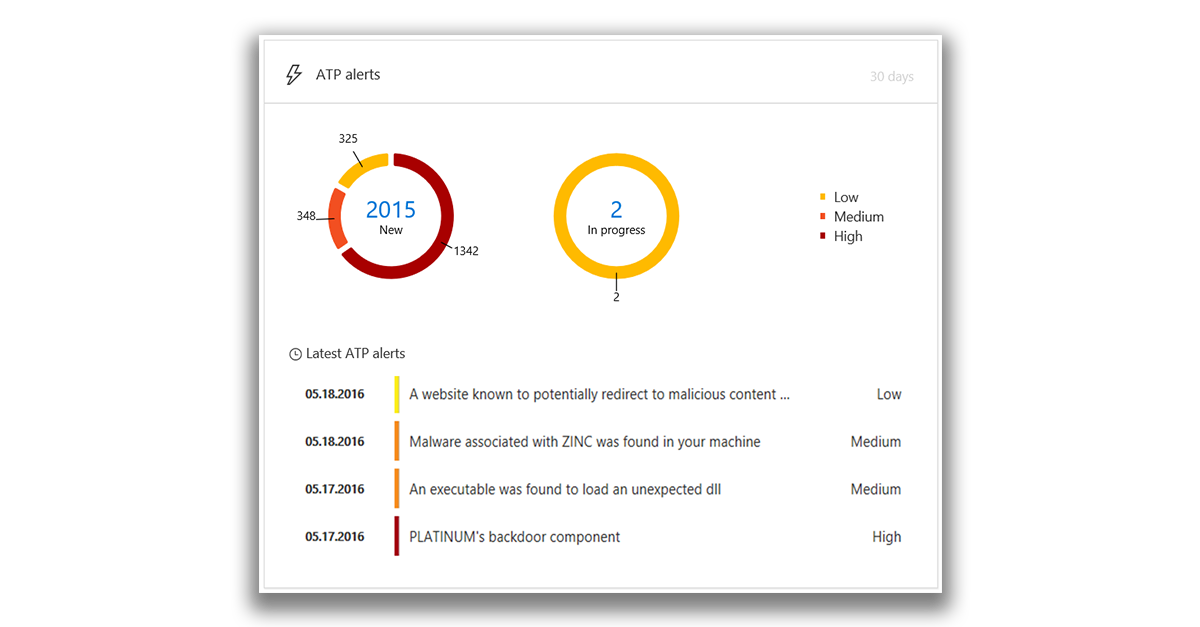
Each group has subcategories by severity level. By clicking on the number inside each, you can display a view of the queue of the corresponding category.
This tile shows a list of computers with the most active alerts. The total number of alerts for each computer is shown in a circle next to the computer name. On the opposite side of the tile, the number of alerts is presented, grouped by severity levels. It is not difficult to guess that dark color is more dangerous, and lighter is less.
The Status tile contains information about whether the service is active and whether there are problems, as well as the number of computers that sent reports to the service in the last 30 days.
Tiles Reports from computers contains a histogram showing the number of computers that sent alerts, by day. You can see the exact number of computers that sent alerts on a particular day by hovering the cursor over the individual columns of the histogram.
Tile Computers with active malware detected is displayed only if Windows Defender is used at your endpoints. Active malware means threats that were actively executed at the time of detection. By hovering the mouse over each of the columns, you can see the number of active malware detected and the number of hosts on which at least one active malware was detected in the last 30 days.

The scheme contains five categories of malware:
Threats are considered active if there is a very high probability that the malware was running on your network, and not just been locally stored on disk.
By clicking on any of these categories, you can go to the Computers view, where the data will be filtered for the relevant category. So you can get detailed information on which computers have active malware detected and how many threats are registered on each of them.
You can manage ATP alerts in Windows Defender as part of regular daily tasks. The alerts are arranged in a queue according to the current status. By default, alerts in the queue are sorted in order from last to oldest. The following table and screen shot show the main areas of the Alert Queue .

You can filter and sort the alert queue (make a summary) to identify the necessary alerts based on certain criteria. Three mechanisms are available for this:
To change the sort order (for example, show the oldest alerts first instead of the new ones), click the sort order icon.
To start the analysis, and get detailed information you need to click on the alert in any queue.
Alert details include the following:
For alerts that have been correlated with the actions of an attacker or a subject, a colored tile is displayed with the name of the subject.
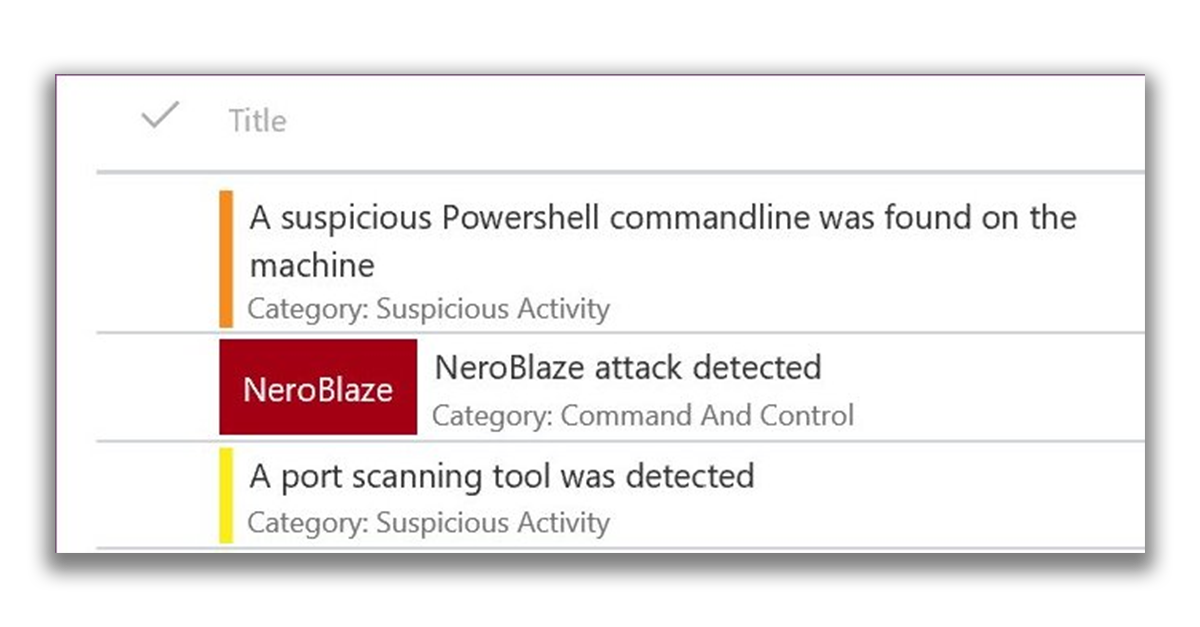
By clicking on the subject's name, you can view the threat analytics profile for him, including a brief overview of the subject, information about his interests or goals, tactics, methods and procedures, as well as information about his activities around the world. A set of recommended responses will also appear.

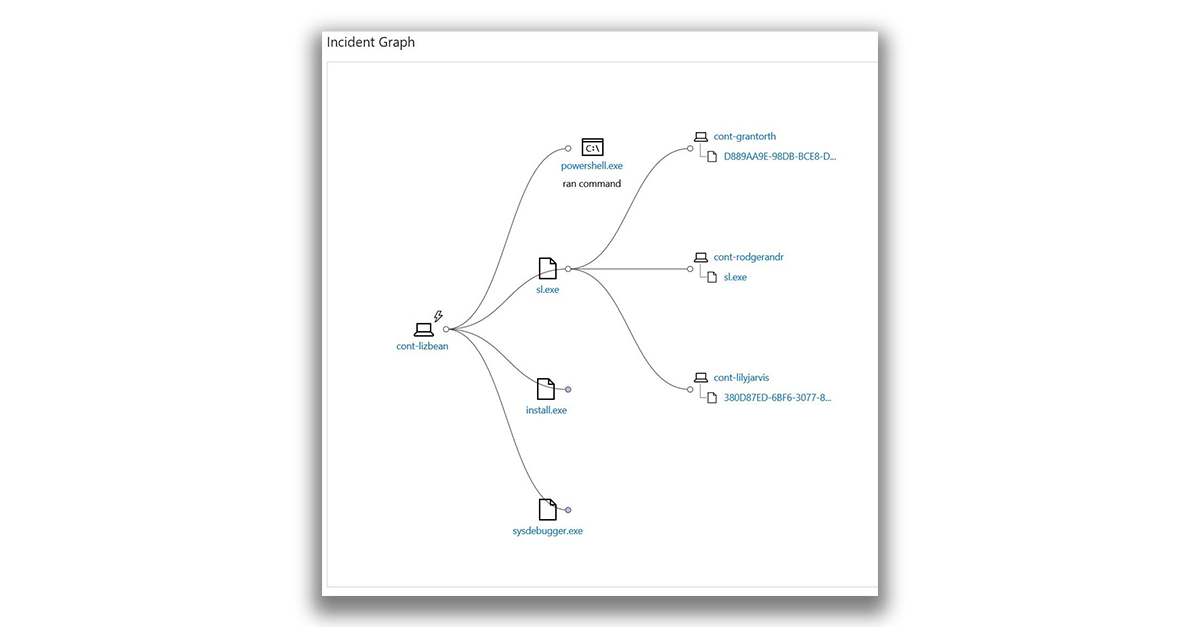
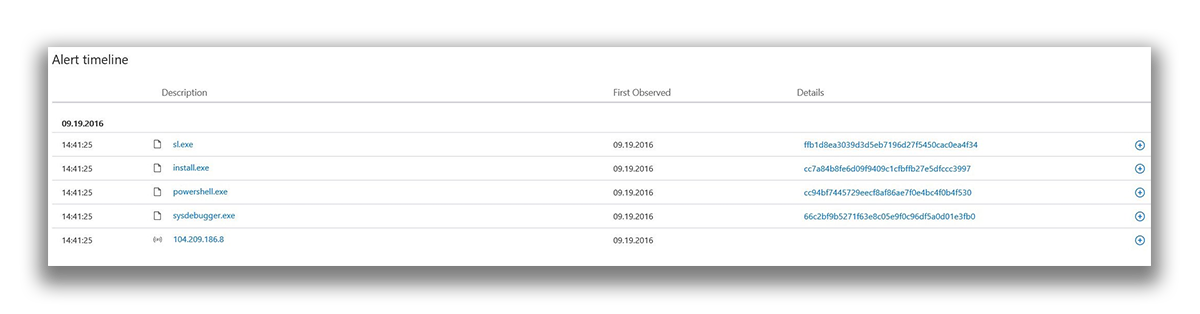
The incident graph includes a visual representation of the location of the alert, the events that led to its creation, and other computers affected by this event. The graph shows the effect of alerts on the source computer, as well as how this event affected the alerts on other computers.
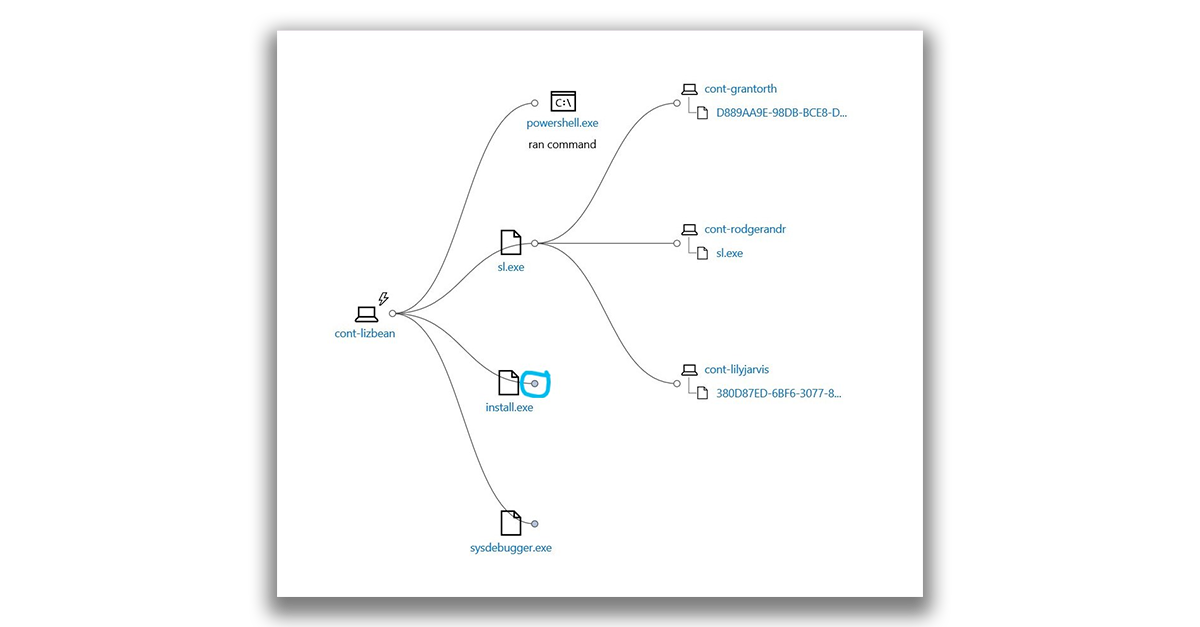
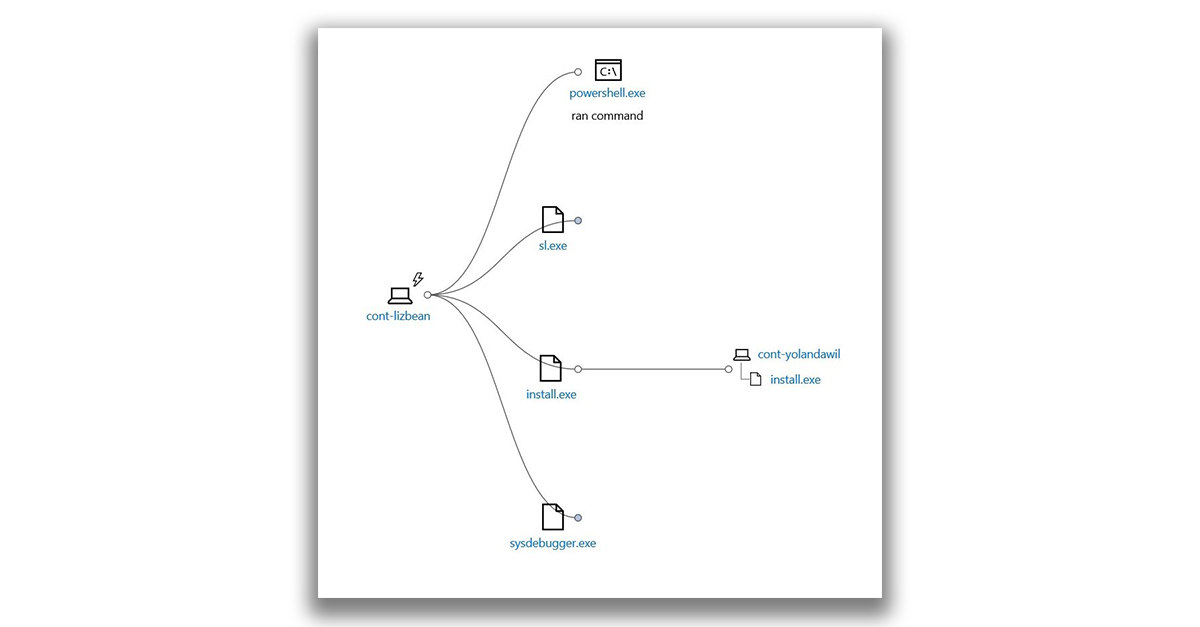
You can click the circle on the incident graph to expand the nodes and view the events or files that are associated with the alert.
We remind you that the ATP service in Windows Defender is built into the core of Windows 10 Corporate, its work can be evaluated for free.

In short, the ATP service in Windows Defender is a security service that allows you to detect security threats in your networks, investigate them and take countermeasures. The service is based on a combination of technologies built in Windows 10 and the Microsoft cloud service. These technologies include:
- Sensors of behavior on the hosts . These sensors are built into Windows 10. They collect and process operating system signals about behavior (for example, process, registry, file, and network interactions) and send data to your private, isolated cloud instance of the ATP service.
- Cloud security analysis . In essence, it makes it possible to convert behavioral signals into analytical data to identify threats, and also helps with recommendations for eliminating them.
- Threat Intelligence . Microsoft has individual experts and data security departments, in addition to this, analyzing threats from partners are used. This allows the ATP service to identify the means, technologies, and methods of attack. Notify users when they find relevant signs in the collected data.
Schematically, these service components are presented below.
')

The capabilities of the host research service allow you to receive detailed alerts, understand the nature and scope of a possible invasion.
The ATP service in Windows Defender works with various Windows security technologies:
- Windows Defender
- Applocker
- Device guard
It can also work in parallel with third-party security solutions.
Overview of Advanced Threat Protection Portal in Windows Defender
ATP Portal can be used to monitor and respond to threats. It solves the following tasks:
- View, sort and classify alerts from hosts.
- Search for additional information related to the detected indicators. These can be specific files or IP addresses.
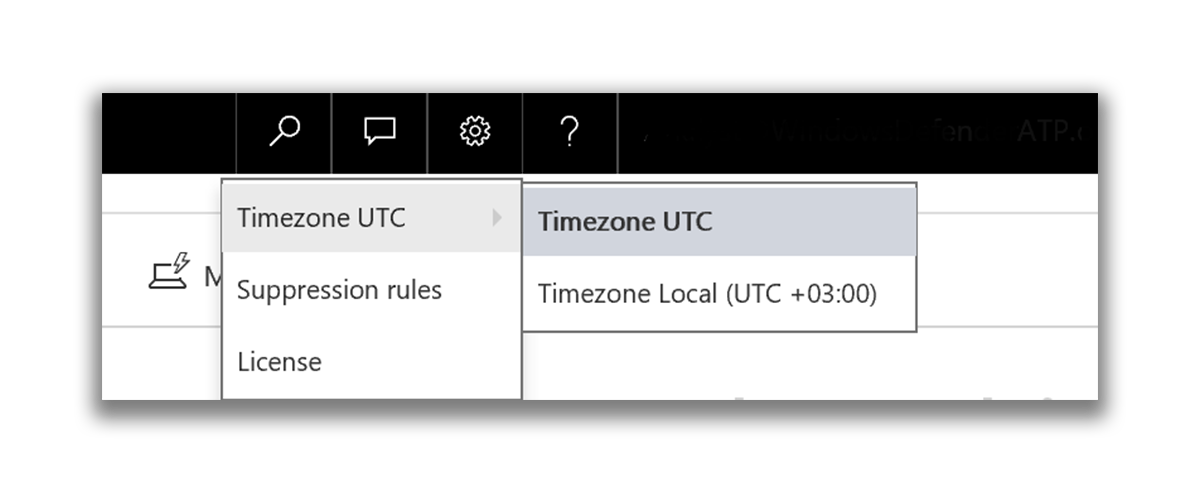
- Change various service settings: time zone and alert rules.
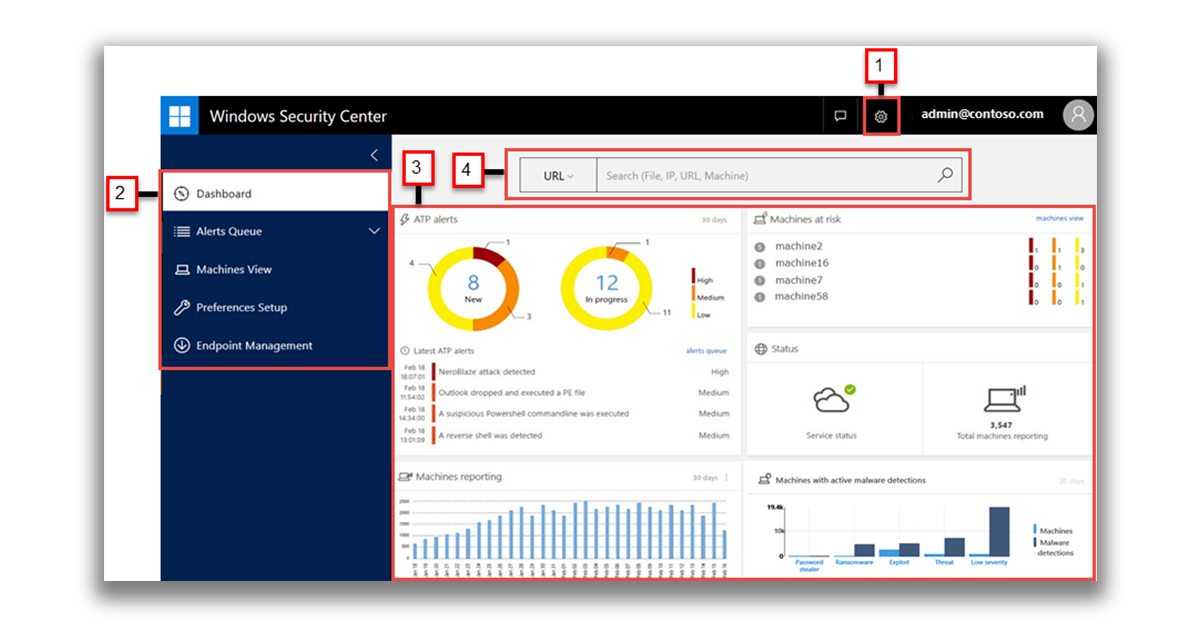
The portal interface includes four main work areas:
- (1) Settings Area
- (2) Navigation area
- (3) Main portal
- (4) Search

With the settings, everything is quite obvious.

The following views are available in the Navigation Panel:
- Information panel (the dashboard itself, which displays basic information);
- Alert queue (New, In process, Allowed and so on).

The computers section displays a list of computers that are protected by the ATP service, and some information about them.

Setting priorities allows you to set up email notifications or a data retention policy (in other words, how much data will be stored in the tenant).

In the host management section , you can download a package to prepare machines for working with ATP.

The ATP service and uses the following conventions:
Alert - a message about the activity that correlates with attacks of increased complexity.
Detection is a sign of a detected malware threat.
Active threat - threats that were actively executed at the time of detection.
Eliminated - the threat was removed from the computer.
Not resolved - the threat is not removed from the computer.
In general, the approach to researching security breaches using ATP can be broken down into the following steps:
- View alerts on a dashboard or alert queue.
- Analysis of indicators of compromise (IOC) or attack (IOA).
- Analysis of the timeline of alerts, behavior and computer events.
- Manage alerts, understand the threat or potential hacking, gather information to determine what action is needed and handle the alert.

View the Advanced Threat Protection Service Dashboard in Windows Defender
Since we start working with ATP with data analysis on the information panel, we will consider it in more detail. Information about alerts and computers allows you to quickly establish the fact, place and time of suspicious activity on the network - this provides the necessary context for understanding the situation. It also displays a summary of event data that helps identify significant events or behavior on a computer. You can also open event and indicator details at a lower level. Active tiles give visual clues to evaluate the overall state of the security systems. Clicking on such a tile opens a detailed view of the corresponding component.
ATP service alerts
When you click on the ATP Alerts tile, the total number of active ATP alerts on the network for the last 30 days is displayed. Alerts are divided into two groups: New and Running.

Each group has subcategories by severity level. By clicking on the number inside each, you can display a view of the queue of the corresponding category.
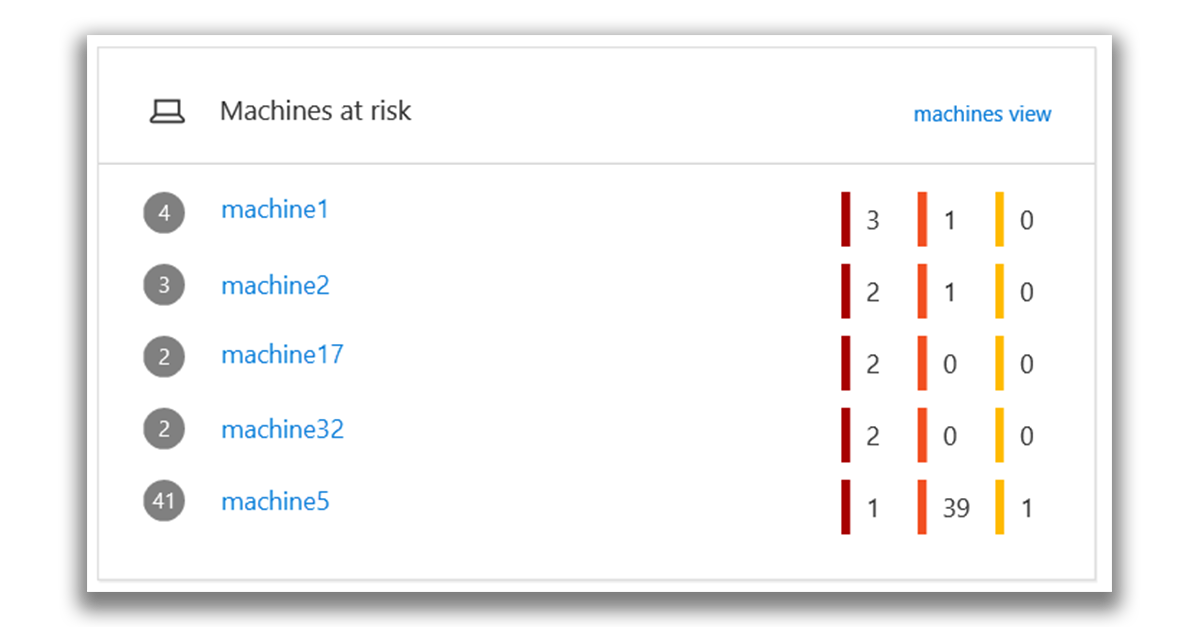
Computers at Risk
This tile shows a list of computers with the most active alerts. The total number of alerts for each computer is shown in a circle next to the computer name. On the opposite side of the tile, the number of alerts is presented, grouped by severity levels. It is not difficult to guess that dark color is more dangerous, and lighter is less.

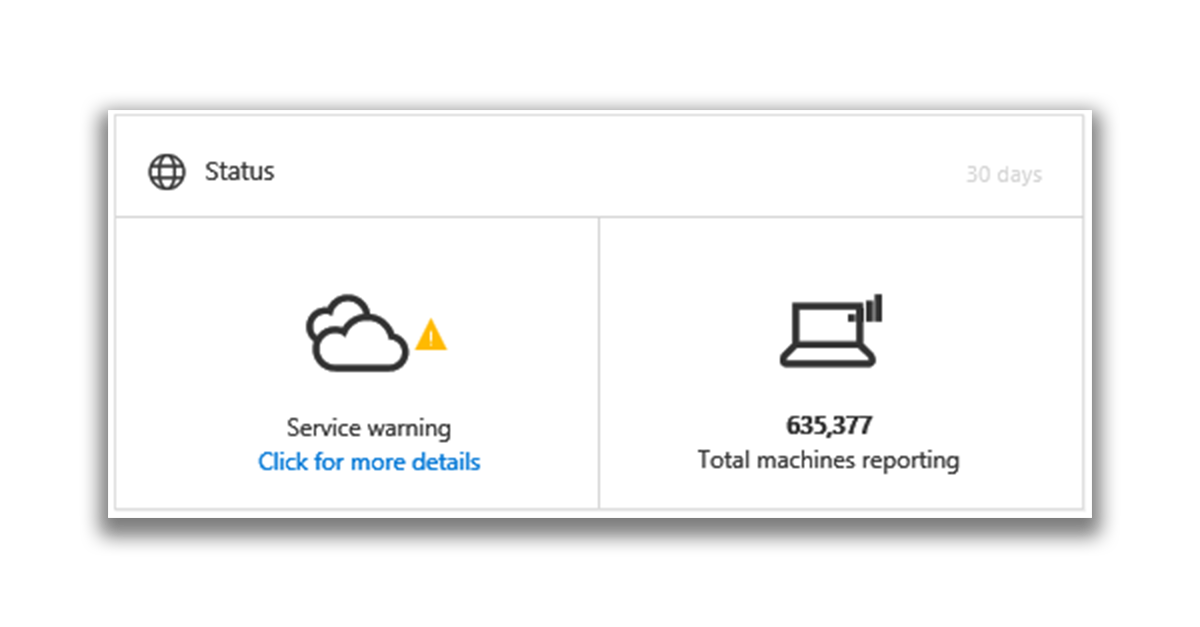
The Status tile contains information about whether the service is active and whether there are problems, as well as the number of computers that sent reports to the service in the last 30 days.

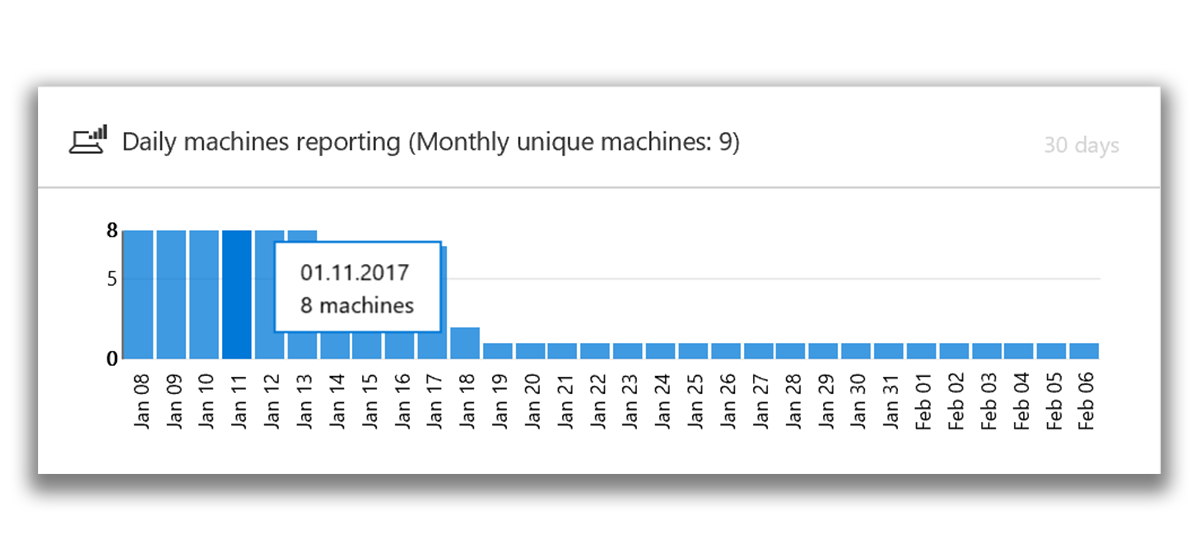
Tiles Reports from computers contains a histogram showing the number of computers that sent alerts, by day. You can see the exact number of computers that sent alerts on a particular day by hovering the cursor over the individual columns of the histogram.

Computers with active malware detected
Tile Computers with active malware detected is displayed only if Windows Defender is used at your endpoints. Active malware means threats that were actively executed at the time of detection. By hovering the mouse over each of the columns, you can see the number of active malware detected and the number of hosts on which at least one active malware was detected in the last 30 days.

The scheme contains five categories of malware:
- Password steal program - threats that steal credentials.
- Blackmailing program - threats aimed at blocking user access to a computer or files and soliciting money to restore access.
- Exploit - threats that exploit software vulnerabilities to infect computers.
- Threat - all other threats that do not belong to the categories of password theft programs, blackmailers and exploits. Trojans, worms, backdoors (“backdoors”) and viruses belong to this category.
- Low severity - threats with low severity, including advertising programs and potentially unwanted programs, such as browser modifiers.
Threats are considered active if there is a very high probability that the malware was running on your network, and not just been locally stored on disk.
By clicking on any of these categories, you can go to the Computers view, where the data will be filtered for the relevant category. So you can get detailed information on which computers have active malware detected and how many threats are registered on each of them.
View and organize your Advanced Threat Protection alert queue
You can manage ATP alerts in Windows Defender as part of regular daily tasks. The alerts are arranged in a queue according to the current status. By default, alerts in the queue are sorted in order from last to oldest. The following table and screen shot show the main areas of the Alert Queue .

Selected area | Region Name | Description |
|---|---|---|
| (one) | Alert Queue | Choose to show New , Running or Allowed alerts. |
| (2) | Alerts | Each alert contains the following data:
Clicking on the alert reveals additional information about the threat, and the timeline moves to the date the alert was created. |
| (3) | Sort and alert filters | Sorting of alerts is possible according to the following parameters:
In addition, the displayed alerts can be filtered by parameters:
|
You can filter and sort the alert queue (make a summary) to identify the necessary alerts based on certain criteria. Three mechanisms are available for this:
- Sort the queue using the drop-down menu in the Sort by field with one of the following options:
- Most recent - sorting alerts by the date of the last appearance at the endpoints.
- Queuing time - sorting alerts by the duration of their queue.
- Severity - sort by severity.
- To filter alerts by severity, you can select one or more checkboxes in the drop-down menu in the Filter by field:
- High (red): threats usually associated with persistent threats of increased complexity (APT). Such alerts indicate a high risk due to the seriousness of the damage that may be caused to hosts.
- Medium (orange): rarely occurring threats, for example, abnormal registry changes, the execution of suspicious files and behavior typical of various phases of attacks.
- Low (yellow): Threats associated with common malicious programs and hacking tools that do not indicate a threat of increased complexity.
- The displayed part of the queue can be limited to various specified periods using the drop-down menu in the date range field (the default value is 6 months ).
To change the sort order (for example, show the oldest alerts first instead of the new ones), click the sort order icon.
Analyzing Advanced Threat Protection Alerts in Windows Defender
To start the analysis, and get detailed information you need to click on the alert in any queue.
Alert details include the following:
- Date and time of the last alert creation.
- Description of the alert.
- Recommended actions.
- Count of the incident.
- Indicators that led to the creation of an alert.
For alerts that have been correlated with the actions of an attacker or a subject, a colored tile is displayed with the name of the subject.

By clicking on the subject's name, you can view the threat analytics profile for him, including a brief overview of the subject, information about his interests or goals, tactics, methods and procedures, as well as information about his activities around the world. A set of recommended responses will also appear.



The incident graph includes a visual representation of the location of the alert, the events that led to its creation, and other computers affected by this event. The graph shows the effect of alerts on the source computer, as well as how this event affected the alerts on other computers.
You can click the circle on the incident graph to expand the nodes and view the events or files that are associated with the alert.


We remind you that the ATP service in Windows Defender is built into the core of Windows 10 Corporate, its work can be evaluated for free.
Source: https://habr.com/ru/post/321698/
All Articles