Security Week 06: SCADA open passwords, SMB vulnerability, Google Apps token
For a long time we did not talk about the security of industrial IT systems An independent researcher from Germany, Maxim Rupp, found ( news , research ) serious problems in Honeywell's SCADA system. XL Web II controllers, including those used in manufacturing, energy, and water supply systems, revealed five vulnerabilities, including storing passwords in the clear. Moreover, using a special request to the controller, the attacker can obtain the current password at any time - it is stored on the client side. The code given in the study speaks for itself:
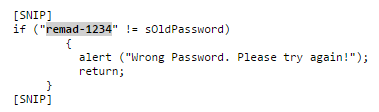
Through parameters in the URL, a mass of commands and settings are transmitted to the system, they are accepted without checks: with a correct request, for example, you can start a new user session, thus disabling the legitimate control device. This story describes well all the traditional features of IT security in the industry. For the update, you need to contact the local vendor unit, the timing for closing the vulnerabilities is large (the information was transmitted back in August last year). However, this is a good example of the interaction of vendors of SCADA-systems with safety guards.
In the implementation of the SMBv3 protocol in Windows, there was a zero-day, Microsoft is slowly solving the problem
News
This strange story began last week. On February 2, researcher Lauren Guffy disclosed vulnerability information in the SMBv3 protocol. He did it in a modern way: he wrote a tweet and laid out proof of concept on GitHab, thus organizing Zero Day. According to him, Microsoft received information in September and planned to release the patch in December, but then decided to postpone the release of the patch until a cumulative patch in February. The vulnerability allows you to remotely cause a denial of service (= blue screen), and was qualified by Microsoft as carrying a small risk.
')
Indeed, in a normal, healthy configuration, the SMB protocol should not be accessible remotely. The question is, why did the researcher do this? His argument is: I do work for them for free, and instead of patching holes, they save them. The argument is so-so, to be honest: a vendor may have a thousand reasons to close a vulnerability sooner or later. The obvious reason to rush is to exploit the hole in-the-wild, but this is clearly not the case here. Yes, sometimes the reason for the delay are organizational problems. In general, this is normal, no?
What about low risk? Everyone agrees that a vulnerability can cause a system crash, but does not lead to the execution of arbitrary code. You can read more about vulnerability and its exploitation in this SANS Institute report.
Based on this vulnerability, another interesting exchange of cues has occurred. In response to a request from journalists for threats related to the vulnerability, Microsoft answered something like the following: Windows is the best platform, we regularly close vulnerabilities, and for better protection we recommend using Windows 10 and Microsoft Edge.

ArsTechnica columnist Dan Goodin has broken out about this caustic article that marketing on vulnerabilities is bad marketing. Moreover, Windows 10 is also subject to this problem. I will add that in this case the same can be said with regard to the researcher: making political statements, at the same time revealing the details of unpatched vulnerability is not ok. Cybersecurity is already saturated with politics, but it's probably better to just close vulnerabilities. Without Marlezonsky ballets and ridiculous demotivators.
Oh wait ...
InGoogle Apps G Suite added authorization by hardware tokens
News Post in a google blog.
In a courageous attempt to bring their cloud services to large organizations on the brows of progress, Google added the ability to authorize using a hardware key to the G Suite services, formerly known as Google Apps. The token can be used in a two-factor authentication system instead of an existing entry system using a security code. As in the similar Facebook announcement last week , support for tokens in mobile devices via Bluetooth is announced (for more, see the Google Support article ).
On January 31, Google announced a series of G Suite innovations aimed at fulfilling the requirements of large corporations for such services. Almost all of them, unsurprisingly, concern security. In particular, it supports Data Loss Prevention technologies, access to service logs, backups, and the like. This is good news for large companies: employees often use cloud services without asking for employer permission. The ability to control a third party service in theory can provide better protection.

"V-572"
Resident harmless virus, standardly infects .EXE files when they are launched for execution. Does not manifest itself. Intercepts int 21h.
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 88.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.

Through parameters in the URL, a mass of commands and settings are transmitted to the system, they are accepted without checks: with a correct request, for example, you can start a new user session, thus disabling the legitimate control device. This story describes well all the traditional features of IT security in the industry. For the update, you need to contact the local vendor unit, the timing for closing the vulnerabilities is large (the information was transmitted back in August last year). However, this is a good example of the interaction of vendors of SCADA-systems with safety guards.
In the implementation of the SMBv3 protocol in Windows, there was a zero-day, Microsoft is slowly solving the problem
News
This strange story began last week. On February 2, researcher Lauren Guffy disclosed vulnerability information in the SMBv3 protocol. He did it in a modern way: he wrote a tweet and laid out proof of concept on GitHab, thus organizing Zero Day. According to him, Microsoft received information in September and planned to release the patch in December, but then decided to postpone the release of the patch until a cumulative patch in February. The vulnerability allows you to remotely cause a denial of service (= blue screen), and was qualified by Microsoft as carrying a small risk.
')
Indeed, in a normal, healthy configuration, the SMB protocol should not be accessible remotely. The question is, why did the researcher do this? His argument is: I do work for them for free, and instead of patching holes, they save them. The argument is so-so, to be honest: a vendor may have a thousand reasons to close a vulnerability sooner or later. The obvious reason to rush is to exploit the hole in-the-wild, but this is clearly not the case here. Yes, sometimes the reason for the delay are organizational problems. In general, this is normal, no?
What about low risk? Everyone agrees that a vulnerability can cause a system crash, but does not lead to the execution of arbitrary code. You can read more about vulnerability and its exploitation in this SANS Institute report.
Based on this vulnerability, another interesting exchange of cues has occurred. In response to a request from journalists for threats related to the vulnerability, Microsoft answered something like the following: Windows is the best platform, we regularly close vulnerabilities, and for better protection we recommend using Windows 10 and Microsoft Edge.

ArsTechnica columnist Dan Goodin has broken out about this caustic article that marketing on vulnerabilities is bad marketing. Moreover, Windows 10 is also subject to this problem. I will add that in this case the same can be said with regard to the researcher: making political statements, at the same time revealing the details of unpatched vulnerability is not ok. Cybersecurity is already saturated with politics, but it's probably better to just close vulnerabilities. Without Marlezonsky ballets and ridiculous demotivators.
Oh wait ...
In
News Post in a google blog.
In a courageous attempt to bring their cloud services to large organizations on the brows of progress, Google added the ability to authorize using a hardware key to the G Suite services, formerly known as Google Apps. The token can be used in a two-factor authentication system instead of an existing entry system using a security code. As in the similar Facebook announcement last week , support for tokens in mobile devices via Bluetooth is announced (for more, see the Google Support article ).
On January 31, Google announced a series of G Suite innovations aimed at fulfilling the requirements of large corporations for such services. Almost all of them, unsurprisingly, concern security. In particular, it supports Data Loss Prevention technologies, access to service logs, backups, and the like. This is good news for large companies: employees often use cloud services without asking for employer permission. The ability to control a third party service in theory can provide better protection.

Antiquities
"V-572"
Resident harmless virus, standardly infects .EXE files when they are launched for execution. Does not manifest itself. Intercepts int 21h.
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 88.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/321526/
All Articles