How to enable JTAG debugging via USB
At the end of December 2016, we published material on Habré on the presentation of Positive Technologies experts at the Chaos Communication Congress (33C3) in Hamburg. Maxim Goryachiy and Mark Yermolov told that modern Intel processors allow using the JTAG debugging interface via the USB 3.0 port available on many platforms to gain full control over the system.
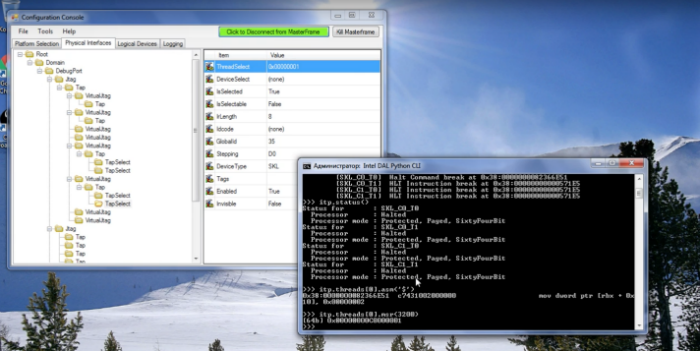
Starting with the Skylake family of processors launched in 2015, Intel has introduced the Direct Connect Interface (DCI) technology, which provides access to JTAG via the popular USB 3.0 port. At the same time, no software or hardware agents are required on the target computer — all that is required is that the DCI interface is activated. Thus, the opportunity to use the capabilities of JTAG on equipment that is commercially available, appeared to ordinary developers
')
Here you can see the slides of the researchers' speeches at 33C3.
The report of the experts of Positive Technologies has caused a serious resonance - leading Russian and foreign media have written about possible attacks on Intel processors via USB. Now, the authors of the study are ready to answer questions and tell more about the internal structure of the JTAG debugging mechanism during their free webinar .
In particular, the following important points will be revealed:
- On which ports the DCI functionality is available;
- How to bypass security through MSR IA32_DEBUG_INTERFACE
The webinar " How to enable JTAG debugging via USB " will be held on Thursday, February 9 at 14:00 . His presenters are Senior Programmers of the Virtualization Technology Department, Maxim Goryachiy and Mark Yermolov. Participation in the webinar is free, registration is required at the link: www.ptsecurity.com/ru-ru/research/webinar/161502/
UPD : Webinar video posted:
Source: https://habr.com/ru/post/321440/
All Articles