DRM-protected Windows files can be used to de-anonymize a Tor user

Experts from HackerHouse conducted a study of the attack using social engineering through files equipped with Digital Rights Management (DRM) protection. The essence of the attack is to obtain information about the user through the substitution of a DRM signature and the use of a dummy URL, which will automatically open when the file is launched through Windows Media Player.
The implementation of such an attack contributes to the very principle of the DRM-protection, which, when the file is launched, requests the encryption key for the audio or video file on the network server. As a result, a DRM file, if connected to the network, can create an unauthorized request to the address specified by it, which is what attackers use to redirect the user to fake resources.
DRM attacks were known more than a decade ago - in 2005, and many information security experts opposed the use of such willful technology, which, however, is still alive.
If someone decides to de-anonymize the Tor user, it will be enough for him to provide the victim (using social engineering tools) a media file with a modified DRM signature, or rather, with a modified authorization URL. When the file is launched, a request will be created from the real address of the victim.
')
There are two types of similar attacks: “cheap” and “expensive”. With a “cheap” scenario, after the launch of a dangerous DRM file, Windows Media Player will offer the user to go to an external site for authorization with the following redirect URL:
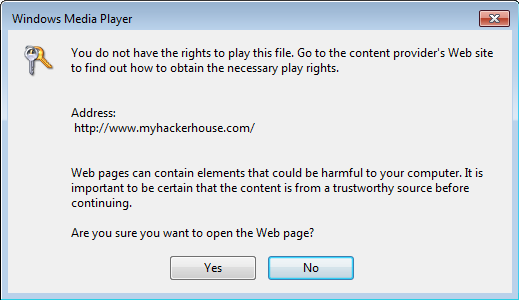
A similar notification appears due to the fact that the file was signed “crookedly”, without the use of specialized software for creating DRM protection, that is, for free. Obviously, if the victim uses Tor, then she will most likely not go to the strange URLs that the player offers him.
But there is a second, “expensive” option when the alert will not appear. This happens when a DRM file is signed by Windows Media Encoder or Microsoft Expression Encoder with the receipt of a real DRM signature. The cost of creating one such file is about $ 10,000.
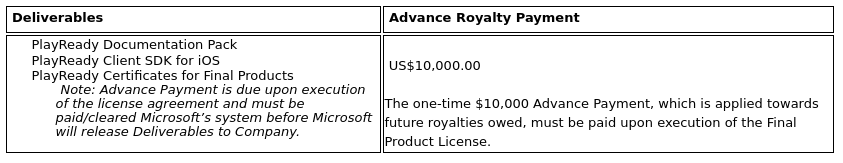
Such a price tag works like a “paywall” against the overwhelming majority of hackers who are not ready to lay out such a sum on a pinpoint attack, which may not take place due to the need to use social engineering techniques (after all, this file must also be fed to the victim).
However, an attack of similar value, the purpose of which is to de-anonymize a user, can be carried out by structures for which $ 10,000 is a drop in their budget. Of course, we are talking about special services, which have long been actively fighting against anonymity on the Internet. In addition, Microsoft is actively cooperating with a number of special services and governments, and the necessary file for the authorities can be created free of charge.
HackerHouse researchers note that this attack is not directed against the Tor or TorBrowser network, but allows interested parties to extract the real ip-address from the victim, that is, to de-anonymize.
Be carefull.
Source: https://habr.com/ru/post/321424/
All Articles