Block file download by extension. Mikrotik RouterOS
Hi Habr! There is a lot of equipment and software that can filter traffic. In my case, this is Mikrotik RB3011UiAS-RM. The task was as follows: to prohibit the download of certain file formats.
It seems to be a simple task, and fast googling led to the decision to block connections through Layer7, because Web Proxy works only with HTTP. And there were examples, but it didn’t work as it should.
upd: the solution only works if the file request is over HTTP from the HTTPS page of the site ( iaon ) ( drsmoll )
According to the results : The example from mp3-tut.net works , but from www.nasa.gov/connect/sounds/index.html does not work .
So, the first link on Mikrotik Layer7 leads to Wiki-Mikrotik .
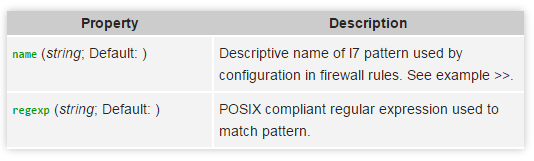
And there we see that in order for Layer7 to work, it is necessary to fill in a regular expression that the router will operate on. There is also a note about using POSIX-compatible regexp.
')
One of the first regexp options:
Does not work! Not all downloads are blocked, sometimes websites are blocked, in the title or in the query string of which there are extension symbols.
Next, a lot of sites were checked from the first three pages of Google. And I came to the conclusion - you have to pick regexp.
And again Google and search. As a result, I came across great sites:
http://web-sniffer.net/
https://regex101.com/
The first gives out what requests go on file loading. The second of this request for a regular expression returns matches.
As a result, I came to the following option:
Consider in detail:
The penultimate clause, with [^ a-zA-Z0-9] is used to allow non-control characters, for example: php.net/manual/ru/function.exec.php
The rule will apply only in the second case.
Yes, the GET line is where the extension will be . will drop it. But in my case it is enough. Users did not complain. And you can add as you please these rules.
Further, to make everything work as it should create rules for the Firewall:
upd: - instead of DROP, specify REJECT-TCP RESET. In this case, the browser receives the response "Connection reset." Allows you to immediately refuse to load the page or frame, which worked the rule, which in turn will speed up the download. (Thanks for the AcidVenom hint)
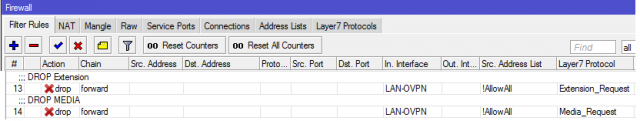
The AllowAll list contains IP addresses to which the rule does not apply.
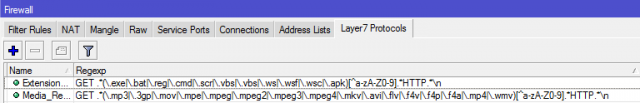
Check the set of regular expressions Layer7:
That's all!
It seems to be a simple task, and fast googling led to the decision to block connections through Layer7, because Web Proxy works only with HTTP. And there were examples, but it didn’t work as it should.
upd: the solution only works if the file request is over HTTP from the HTTPS page of the site ( iaon ) ( drsmoll )
According to the results : The example from mp3-tut.net works , but from www.nasa.gov/connect/sounds/index.html does not work .
So, the first link on Mikrotik Layer7 leads to Wiki-Mikrotik .
And there we see that in order for Layer7 to work, it is necessary to fill in a regular expression that the router will operate on. There is also a note about using POSIX-compatible regexp.
')

One of the first regexp options:
^.+(exe|mp3|mpeg).*$ Does not work! Not all downloads are blocked, sometimes websites are blocked, in the title or in the query string of which there are extension symbols.
Next, a lot of sites were checked from the first three pages of Google. And I came to the conclusion - you have to pick regexp.
And again Google and search. As a result, I came across great sites:
http://web-sniffer.net/
https://regex101.com/
The first gives out what requests go on file loading. The second of this request for a regular expression returns matches.
As a result, I came to the following option:
GET .*(\.exe|\.bat|\.reg|\.cmd|\.scr|\.vbs|\.vbs|\.ws|\.wsf|\.wsc|\.apk)[^a-zA-Z0-9].*HTTP.*\n Consider in detail:
- GET - the beginning of the line in which the request is for something on the site example.com
- . * - any number of characters
- (\ .exe | \ .bat | \ .reg | \ .cmd | \ .scr | \ .vbs | \ .vbs | \ .ws | \ .wsf | \ .wsc | \ .apk) - a list of what we are looking for
- . * - any number of characters
- [^ a-zA-Z0-9] - signs, ^ = NOT included in the set az, AZ, 0-9
- . * HTTP. * \ N - HTTP, framed by any characters ( HTTP. * Optional), and \ n - newline
The penultimate clause, with [^ a-zA-Z0-9] is used to allow non-control characters, for example: php.net/manual/ru/function.exec.php
Connect to 72.52.91.14 on port 80 ... ok
GET /manual/ru/function .exec.php HTTP/1.1
Host: php.netConnect to 72.52.91.14 on port 80 ... ok
GET /manual/ru/function .exe.php HTTP/1.1
Host: php.net
The rule will apply only in the second case.
Yes, the GET line is where the extension will be . will drop it. But in my case it is enough. Users did not complain. And you can add as you please these rules.
Further, to make everything work as it should create rules for the Firewall:
upd: - instead of DROP, specify REJECT-TCP RESET. In this case, the browser receives the response "Connection reset." Allows you to immediately refuse to load the page or frame, which worked the rule, which in turn will speed up the download. (Thanks for the AcidVenom hint)

The AllowAll list contains IP addresses to which the rule does not apply.
Check the set of regular expressions Layer7:

That's all!
Source: https://habr.com/ru/post/321408/
All Articles