Criminals discovered using the ATP service in Windows Defender
When in December 2016, a German industrial conglomerate reported that it had been attacked at the beginning of the year, it turned out that a professional criminal group engaged in industrial espionage was behind the data hacking. According to the German press, the attack was carried out on the basis of the file being introduced from the Winnti family, which provided attackers with constant access to the conglomerate network from February 2016.
Under the cat, we will look at the embedded Winnti malicious file in the form in which it was used by two well-known criminal groups BARIUM and LEAD. We will see how they injected the file into various systems, and also find out with what methods the Microsoft researchers tracked it.

To show how to deal with this and similar threats, we will look at how Advanced Threat Protection (ATP) in Windows Defender marks activities related to BARIUM, LEAD and other well-known criminal groups, and provides advanced threat analytics for them. We will follow the installation process of the Winnti file being deployed and study how the ATP service in Windows Defender captures the methods and tools used at this time, providing visual contextual information for investigating the real attack and responding. We will then discuss how centralized response within the enhanced ATP service in Windows Defender, available in Windows 10 Creators Update , allows you to quickly stop threats. In particular, the service blocks communications for management and control purposes, prohibits embedded files from installing additional components and spreading the threat to other computers within the network.
')
Microsoft Threat Intelligence analysts associate Winnti malware with various criminal groups. These conclusions are made on the basis of a number of attack artifacts (collections of malware, related infrastructure, Internet personalities, victim profiles, etc.), through which the Microsoft Intelligent Security Graph categorizes the malicious activity, assigning it to various actors. Each of these groups receives the code name of one of the elements of the periodic table. In the case of this malware, Winnti, it is actively used by the BARIUM and LEAD groups. Despite the common attack tool, the invasion scenarios of these groups are significantly different.
BARIUM begins its attacks by establishing relationships with potential victims on social networks, especially among those who work in the business development department or in the personnel department. Having established personal contact, members of BARIUM go to the target phishing of the victim. Various simple software installation vectors are used for this, including malicious shortcut files (LNK) with hidden content, compiled HTML help files (CHM) or Microsoft Office documents with macros and exploits. At the initial stage of the invasion, an embedded Win32 / Barlaiy file is used, which often uses social network profiles, document co-editing sites and blogs to manage and control. Further, for permanent access, the Winnti file is used. Most of the victims recorded so far worked in the field of electronic games, multimedia and Internet content, although among them there were also employees of technology companies.
The LEAD group, by contrast, has established itself as a professional in industrial espionage. In the past few years, LEAD victims have been:
The goal of LEAD was to steal confidential data, including research materials, technological documents and project plans. LEAD members also stole software signature certificates to sign their malware in subsequent attacks.
In most cases, advanced exploit technologies were not used in LEAD attacks. In addition, the group did not seek to establish contact with the victim before the attack began. Instead, they simply emailed the Winnti installer to potential victims using basic social engineering techniques to convince the recipient to run the embedded malware. In some cases, LEAD accessed the target by recognizing login and access credentials using a brute force attack, executing SQL injection or exploits on unprotected web servers. After that, the Winnti installer was directly copied to the hacked computer.
Microsoft Analytics shows that the threat to Winnti has to do with invasions made over the past 6 months in Asia, Europe, Oceania, the Middle East and the USA (see Figure 1). The latest series of observed attacks occurred in December 2016.

Figure 1. The geography of using Winnti from July to December 2016
Although traditional research is required to track threats such as Winnti, Microsoft Threat Intelligence analysts reach a new level with machine learning. When the attackers used Winnti to maintain access to the web servers, they masked the malicious file as trusted and trusted and left it in plain sight. This happened during two well-known attacks in 2015, when the malicious DLLs implemented the DLL library named ASPNET_FILTER.DLL, which is consistent with the name of the DLL library for the ASP.NET ISAPI filter (see Table 1). And although there were obvious differences between a trusted and malicious file, to filter the latter, you would have to analyze a data set with millions of possible file names, software publishers and certificates. To reduce this set of data and separate meaningful anomalies from innocuous data, Microsoft researchers have resorted to a combination of anomaly detection and managed machine learning.
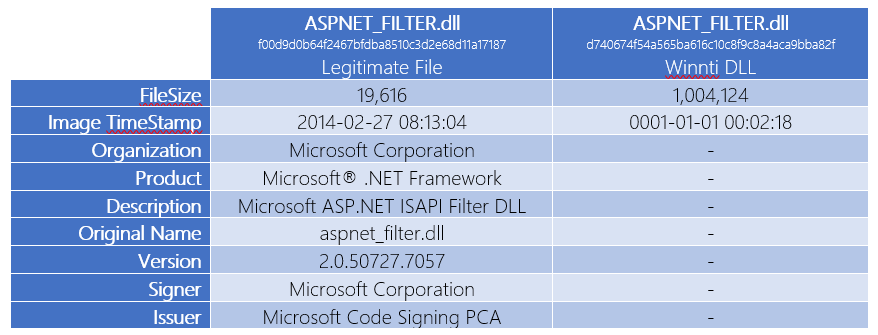
Table 1. Reliable ASPNET_FILTER.dll file and disguised Winnti pattern
ATP in Windows Defender helps network security specialists take a versatile approach to fighting attacks from malicious groups like LEAD and BARIUM. The following examples were developed using the Winnti installer used in the December 2016 attacks.
Microsoft Threat Intelligence specialists continuously monitor the LEAD and BARIUM groups, fixing the tactics, methods and procedures they use in their attacks. Particular attention is paid to the means and infrastructure with which these attacks are carried out. ATP in Windows Defender constantly monitors protected systems, identifying such indicators of malicious activity and notifying them to the presence of personnel from the Security Operations Center (SOC).
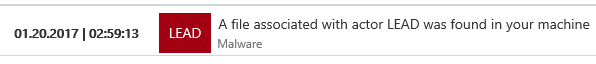
Figure 2. Threat Notification in Windows Defender ATP
To provide a context for such alerts, ATP in Windows Defender also provides a short summary of the group's history, its goals, methods, and tools (see Figure 3), with links to more detailed documentation for tech-savvy users.

Figure 3. Lead group summary and extended documentation
ATP in Windows Defender can also detect previously unknown attacks by tracking indicators of malicious behavior in the system, including:
For example, many families of malware are registered as services during installation in order to preserve presence after reboots. Most malicious programs that operate by such methods change the necessary registry keys in a way that does not match the profile of a reliable program. Winnti is not an exception, and therefore during the Winnti installation process, the ATP service in Windows Defender can create alerts about abnormal behavior (Figure 4).
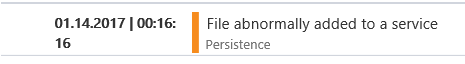
Figure 4. Alert service creation alerts
To improve coverage and reduce false positives, an intelligent security graph is used to distinguish suspicious from innocent behavior. So alerts are generated only with full confidence in the harm of a file or process. At the same time, along with the method of creating the service, the age of the file, its global distribution and the presence of a valid digital signature are taken into account.
ATP contextual information in Windows Defender provides detailed visualized technical information on alerts triggered by a special threat analysis service, tied to action groups, or simply suspicious behavior. Visual information allows SOC personnel to collect information about alerts and related artifacts, understand the magnitude of the flaw, and prepare a comprehensive action plan. The screenshots below show how ATP in Windows Defender clearly displays the Winnti installation, in which the installer drops the DLL to the disk (Figure 5), loads the DLL using rundll32 (Figure 6), configures the DLL as a service (Figure 7) and saves a copy of itself in C: \ Windows \ Help (Figure 8).

Figure 5. Winnti Installer resets the DLL
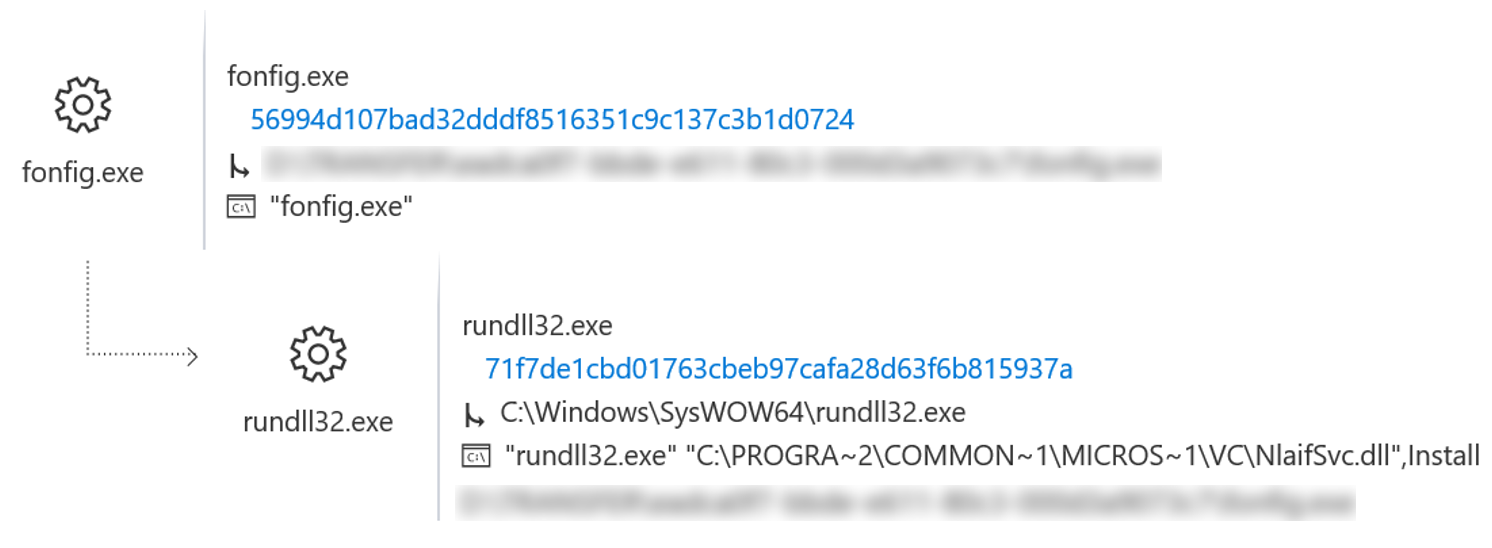
Figure 6. Winnti Installer loads the DLL using rundll32
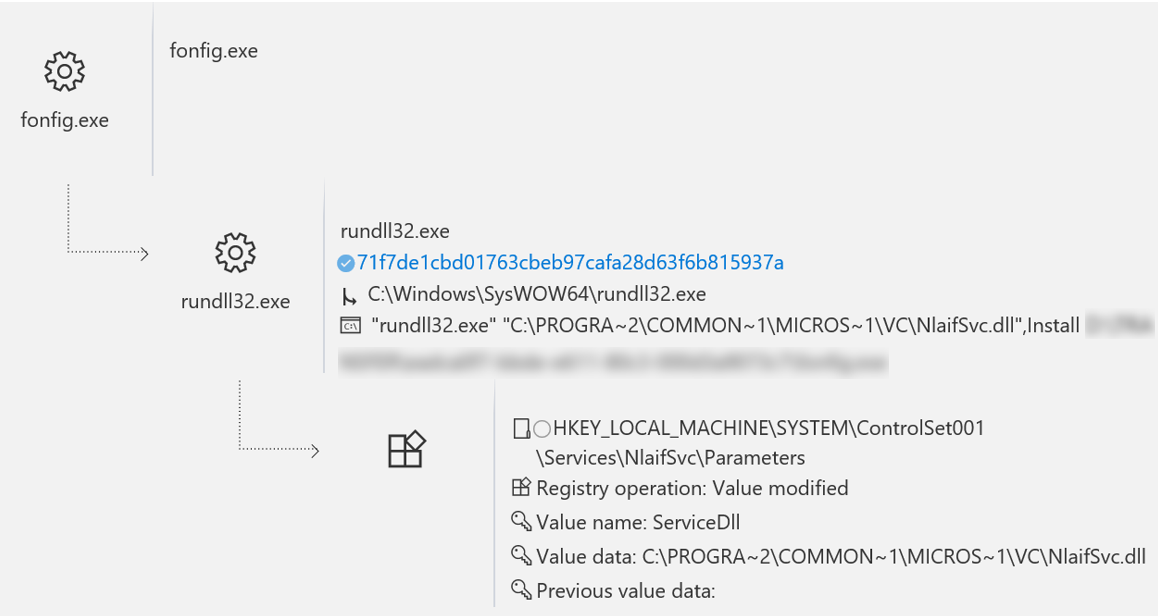
Figure 7. Winnti configures itself as a service for persistence

Figure 8. The installer is copied to C: \ Windows \ Help \
ATP in Windows Defender displays these actions as a process tree on the infected computer’s timeline. Using the process tree, analytics can easily isolate detailed information about how an embedded library is reset by the installer, which command is used to run rundll32.exe and load the DLL, as well as what changes are made to the registry to configure the DLL as a service. This information provides insights into which primary tools can be used to assess the magnitude of the gap.
In Windows 10 Creators Update, there are some additional ATP settings in Windows Defender that give SOC personnel options to immediately eliminate the risks of a detected threat. If an attacker attacks a computer with ATP installed in Windows Defender, SOC personnel can isolate this computer from the network, blocking the management and control of the copy of the malware, thereby preventing the attacker from installing additional malware and switching to other computers on the network. Meanwhile, the connection to the ATP service in Windows Defender is preserved. While the computer is isolated, SOC personnel can command the infected computer to collect operational data, such as the DNS cache or security event logs, which are then used to check alerts, access the intrusion state, and take further action.

Figure 9. Variants of response to the threat to the attacked computer
Stopping and quarantining a copy of Winnti is another answer that allows you to stop the attack on one computer. There is no evidence that LEAD and BARIUM are used for full-scale targeted phishing, so SOC personnel are unlikely to be faced with the fact that several computers will be attacked by malware from these groups at once. However, ATP in Windows Defender also supports blocking copies of malware throughout the enterprise, stopping full-scale attacks in its early stages (Figure 10).

Figure 10. Variants of response to the threat to the Winnti file
According to new reports, the detection and elimination of the risks of attacks on industrial conglomerates may take several months. The time elapsed from the moment of the breach until its discovery may be enough for an attacker to determine the location of important information and copy it.
With advanced post-attack ATP flaw detection in Windows Defender, SOC personnel can reduce this time to several hours or even minutes, significantly reducing the impact of a persistent intruder’s access to the network. ATP in Windows Defender provides comprehensive information about the groups of actions responsible for the attack, allowing clients to understand such aspects of the attack as general applied sociology tricks and regional features of attacks that cannot be obtained through the network and endpoint sensors. With up-to-date visualized information, analysts can study the behavior of malware on infected computers, up to planning a response. Finally, in connection with the upcoming Creators Update, ATP in Windows Defender will have additional capabilities for detecting threats such as Winnti, as well as centralized responses to the threat, such as isolating a computer and blocking files that quickly isolate known points of attack.
The ATP service in Windows Defender is built into the core of Windows 10 Corporate, its performance can be assessed for free .
Under the cat, we will look at the embedded Winnti malicious file in the form in which it was used by two well-known criminal groups BARIUM and LEAD. We will see how they injected the file into various systems, and also find out with what methods the Microsoft researchers tracked it.

To show how to deal with this and similar threats, we will look at how Advanced Threat Protection (ATP) in Windows Defender marks activities related to BARIUM, LEAD and other well-known criminal groups, and provides advanced threat analytics for them. We will follow the installation process of the Winnti file being deployed and study how the ATP service in Windows Defender captures the methods and tools used at this time, providing visual contextual information for investigating the real attack and responding. We will then discuss how centralized response within the enhanced ATP service in Windows Defender, available in Windows 10 Creators Update , allows you to quickly stop threats. In particular, the service blocks communications for management and control purposes, prohibits embedded files from installing additional components and spreading the threat to other computers within the network.
')
Winnti criminal groups: BARIUM and LEAD
Microsoft Threat Intelligence analysts associate Winnti malware with various criminal groups. These conclusions are made on the basis of a number of attack artifacts (collections of malware, related infrastructure, Internet personalities, victim profiles, etc.), through which the Microsoft Intelligent Security Graph categorizes the malicious activity, assigning it to various actors. Each of these groups receives the code name of one of the elements of the periodic table. In the case of this malware, Winnti, it is actively used by the BARIUM and LEAD groups. Despite the common attack tool, the invasion scenarios of these groups are significantly different.
BARIUM begins its attacks by establishing relationships with potential victims on social networks, especially among those who work in the business development department or in the personnel department. Having established personal contact, members of BARIUM go to the target phishing of the victim. Various simple software installation vectors are used for this, including malicious shortcut files (LNK) with hidden content, compiled HTML help files (CHM) or Microsoft Office documents with macros and exploits. At the initial stage of the invasion, an embedded Win32 / Barlaiy file is used, which often uses social network profiles, document co-editing sites and blogs to manage and control. Further, for permanent access, the Winnti file is used. Most of the victims recorded so far worked in the field of electronic games, multimedia and Internet content, although among them there were also employees of technology companies.
The LEAD group, by contrast, has established itself as a professional in industrial espionage. In the past few years, LEAD victims have been:
- Transnational diversified giants in such areas as the production of textiles, chemicals and electronics.
- Pharmaceutical companies.
- A company in the chemical industry.
- University Faculty of Aviation Engineering and Research.
- A company involved in the design and manufacture of automotive engines.
- A cybersecurity company that protects industry control systems.
The goal of LEAD was to steal confidential data, including research materials, technological documents and project plans. LEAD members also stole software signature certificates to sign their malware in subsequent attacks.
In most cases, advanced exploit technologies were not used in LEAD attacks. In addition, the group did not seek to establish contact with the victim before the attack began. Instead, they simply emailed the Winnti installer to potential victims using basic social engineering techniques to convince the recipient to run the embedded malware. In some cases, LEAD accessed the target by recognizing login and access credentials using a brute force attack, executing SQL injection or exploits on unprotected web servers. After that, the Winnti installer was directly copied to the hacked computer.
Spying on Winnti
Microsoft Analytics shows that the threat to Winnti has to do with invasions made over the past 6 months in Asia, Europe, Oceania, the Middle East and the USA (see Figure 1). The latest series of observed attacks occurred in December 2016.

Figure 1. The geography of using Winnti from July to December 2016
Although traditional research is required to track threats such as Winnti, Microsoft Threat Intelligence analysts reach a new level with machine learning. When the attackers used Winnti to maintain access to the web servers, they masked the malicious file as trusted and trusted and left it in plain sight. This happened during two well-known attacks in 2015, when the malicious DLLs implemented the DLL library named ASPNET_FILTER.DLL, which is consistent with the name of the DLL library for the ASP.NET ISAPI filter (see Table 1). And although there were obvious differences between a trusted and malicious file, to filter the latter, you would have to analyze a data set with millions of possible file names, software publishers and certificates. To reduce this set of data and separate meaningful anomalies from innocuous data, Microsoft researchers have resorted to a combination of anomaly detection and managed machine learning.

Table 1. Reliable ASPNET_FILTER.dll file and disguised Winnti pattern
Measures against Winnti attacks
ATP in Windows Defender helps network security specialists take a versatile approach to fighting attacks from malicious groups like LEAD and BARIUM. The following examples were developed using the Winnti installer used in the December 2016 attacks.
Active Invasion Alerts
Microsoft Threat Intelligence specialists continuously monitor the LEAD and BARIUM groups, fixing the tactics, methods and procedures they use in their attacks. Particular attention is paid to the means and infrastructure with which these attacks are carried out. ATP in Windows Defender constantly monitors protected systems, identifying such indicators of malicious activity and notifying them to the presence of personnel from the Security Operations Center (SOC).

Figure 2. Threat Notification in Windows Defender ATP
To provide a context for such alerts, ATP in Windows Defender also provides a short summary of the group's history, its goals, methods, and tools (see Figure 3), with links to more detailed documentation for tech-savvy users.

Figure 3. Lead group summary and extended documentation
ATP in Windows Defender can also detect previously unknown attacks by tracking indicators of malicious behavior in the system, including:
- Install, save and activate malware.
- Hidden processes of management and control (via trojan backdoors).
- Theft of credentials.
- Distribution on other computers within the network.
For example, many families of malware are registered as services during installation in order to preserve presence after reboots. Most malicious programs that operate by such methods change the necessary registry keys in a way that does not match the profile of a reliable program. Winnti is not an exception, and therefore during the Winnti installation process, the ATP service in Windows Defender can create alerts about abnormal behavior (Figure 4).

Figure 4. Alert service creation alerts
To improve coverage and reduce false positives, an intelligent security graph is used to distinguish suspicious from innocent behavior. So alerts are generated only with full confidence in the harm of a file or process. At the same time, along with the method of creating the service, the age of the file, its global distribution and the presence of a valid digital signature are taken into account.
ATP contextual information in Windows Defender provides detailed visualized technical information on alerts triggered by a special threat analysis service, tied to action groups, or simply suspicious behavior. Visual information allows SOC personnel to collect information about alerts and related artifacts, understand the magnitude of the flaw, and prepare a comprehensive action plan. The screenshots below show how ATP in Windows Defender clearly displays the Winnti installation, in which the installer drops the DLL to the disk (Figure 5), loads the DLL using rundll32 (Figure 6), configures the DLL as a service (Figure 7) and saves a copy of itself in C: \ Windows \ Help (Figure 8).

Figure 5. Winnti Installer resets the DLL

Figure 6. Winnti Installer loads the DLL using rundll32

Figure 7. Winnti configures itself as a service for persistence

Figure 8. The installer is copied to C: \ Windows \ Help \
ATP in Windows Defender displays these actions as a process tree on the infected computer’s timeline. Using the process tree, analytics can easily isolate detailed information about how an embedded library is reset by the installer, which command is used to run rundll32.exe and load the DLL, as well as what changes are made to the registry to configure the DLL as a service. This information provides insights into which primary tools can be used to assess the magnitude of the gap.
Options for responding to a threat
In Windows 10 Creators Update, there are some additional ATP settings in Windows Defender that give SOC personnel options to immediately eliminate the risks of a detected threat. If an attacker attacks a computer with ATP installed in Windows Defender, SOC personnel can isolate this computer from the network, blocking the management and control of the copy of the malware, thereby preventing the attacker from installing additional malware and switching to other computers on the network. Meanwhile, the connection to the ATP service in Windows Defender is preserved. While the computer is isolated, SOC personnel can command the infected computer to collect operational data, such as the DNS cache or security event logs, which are then used to check alerts, access the intrusion state, and take further action.

Figure 9. Variants of response to the threat to the attacked computer
Stopping and quarantining a copy of Winnti is another answer that allows you to stop the attack on one computer. There is no evidence that LEAD and BARIUM are used for full-scale targeted phishing, so SOC personnel are unlikely to be faced with the fact that several computers will be attacked by malware from these groups at once. However, ATP in Windows Defender also supports blocking copies of malware throughout the enterprise, stopping full-scale attacks in its early stages (Figure 10).

Figure 10. Variants of response to the threat to the Winnti file
Conclusion: shortened detection time for gaps
According to new reports, the detection and elimination of the risks of attacks on industrial conglomerates may take several months. The time elapsed from the moment of the breach until its discovery may be enough for an attacker to determine the location of important information and copy it.
With advanced post-attack ATP flaw detection in Windows Defender, SOC personnel can reduce this time to several hours or even minutes, significantly reducing the impact of a persistent intruder’s access to the network. ATP in Windows Defender provides comprehensive information about the groups of actions responsible for the attack, allowing clients to understand such aspects of the attack as general applied sociology tricks and regional features of attacks that cannot be obtained through the network and endpoint sensors. With up-to-date visualized information, analysts can study the behavior of malware on infected computers, up to planning a response. Finally, in connection with the upcoming Creators Update, ATP in Windows Defender will have additional capabilities for detecting threats such as Winnti, as well as centralized responses to the threat, such as isolating a computer and blocking files that quickly isolate known points of attack.
The ATP service in Windows Defender is built into the core of Windows 10 Corporate, its performance can be assessed for free .
Source: https://habr.com/ru/post/320980/
All Articles