Configuring the DNS server for North Korean security standards

I’m afraid to imagine how stressful the work of IT specialists Kim Jong-un is, as he, most likely, from those managers who constantly watch your work from behind, constantly touch the screen and hint of a bad expression on his face the disappearance "of all your relatives in three generations, if at least one mistake is made in deploying patches.
We often hear about data leaks from large companies, government hacker support, and the development of non-standard encryption methods, but it must be acknowledged that the most common security problems that occur every day are trivial errors in system configuration.
')
This is what happened with the Democratic People’s Republic of Korea (DPRK) DNS root servers. Due to an accidental configuration error, any Internet user could request from the top-level domain a complete list of Internet-connected servers:
github.com/mandatoryprogrammer/NorthKoreaDNSLeak
Of course, there is little pleasant in the appearance of such a security problem, but it still cannot be called significant, since it did not open access to any systems. Were disclosed only information that these systems exist.
Intruders hacking into networks have many ways to detect internal nodes in these networks, so it cannot be said that the data in the public domain was particularly secret or confidential. However, there are two factors that make you seriously think about this incident.
First: this was definitely not the result of a zero-day attack on the state by the elite “red team”.
Second, the DPRK network consists of only 28 servers. If it were not for this fact, such disclosure would not even get into the news (although, frankly, the network of a country with fewer nodes than the network of a small insurance company from the Midwest causes only laughter).
The empathy of the situation causes its everydayness: this could happen when implementing practically any IT project in a company of any size, from any industry and in any country.
- Apparently, North Korean experts tried to transfer the DNS configuration to an additional server or create a backup copy there. Likewise, you could have done this to prevent your sites from turning off when you tried to create a double connection of DNS services to them.
- The problem was discovered by an automatic system that constantly sends requests to transfer the zone to all top-level domains and many corporations. A real gift for the attacker.
- This is an extremely problem that cannot be noticed from the outside. No one will contact the support service regarding the sudden opportunity to transfer zones outside the network.
Checking whether your network map has been accidentally exported to the Internet is very easy.
If you have DNS zone transfer enabled, which can be accessed from an external address, follow these steps:
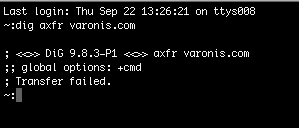
Using the dig utility, run the following command on a computer outside the network:
dig axfr yourdomain.com (arbitrary name server). You should receive a Transfer Failed response:
If you do not have access to dig, you can use the online scanner: hackertarget.com/zone-transfer .
Source: https://habr.com/ru/post/320900/
All Articles