Analysis of the interaction of mobile Android applications with the social networks API Facebook, Instagram, VKontakte
 It’s no secret that most large server-side services use some kind of API ( Application Programming Interface ) to interact with different clients.
It’s no secret that most large server-side services use some kind of API ( Application Programming Interface ) to interact with different clients.At the “face-to-face” NeoQUEST-2016, Maxim Khazov spoke about various approaches to the definition and use of hidden server API-functions using the example of such popular services as VKontakte, Instagram, Facebook.
In this article we will focus on the main points of the report and share all electronic materials: video recording of the performance, presentation, as well as demonstrations of attacks for each of the considered social networks (everything is under the cut).
')
Let us hint: “walks” on social networks are still coming up to the participants of NeoQUEST-2017 , registration for the online-stage of which is in full swing!
How did that sound on NeoQUEST?
Immediately, as promised, we share the presentation ( tyk ) and the report:
Why define an API?
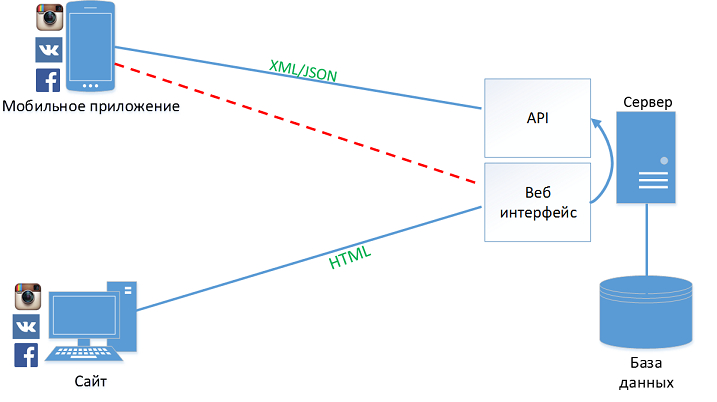
There are two main goals in this case:
- Search for vulnerabilities (on the server side or in the interaction protocol).
- Automate actions on social networks (all your favorite “bots”).
Such bots can be called "chameleons", as they will mimic under the official mobile service application, performing the same requests with the same structure. On the server side, it will not be easy to distinguish such a bot from the real user of the mobile application.
How to learn API?
There are 3 main areas:
- Examination of documentation (well, if it is!);
- Analysis of network traffic (the easiest way, then selected as the main);
- Reverse engineering of a mobile application (the most “hardcore” way, but sometimes you can't do without it).
Examples and Demonstrations
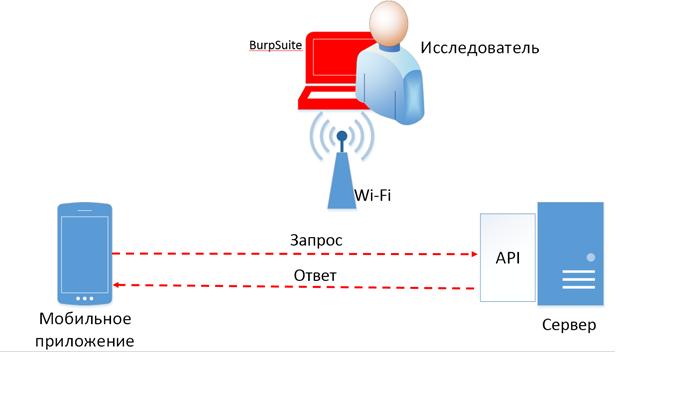
For demonstrations, a controlled Wi-Fi point was used, as well as a proxy for Burp Suite HTTP requests. In this case, all tested applications interacted with the API using the HTTP protocol and its modifications.
IMPORTANT!
The study was conducted in the spring-summer of 2016, currently there may be changes in the architecture of applications and interaction protocols (for example, from November 2016 the VKontakte Android application no longer supports the HTTP protocol).
VKontakte and unprotected HTTP protocol
VKontakte Android mobile application by default uses the HTTP protocol, which means (as shown in the first part of the report, the video of which is at the end of the article):
- The application is vulnerable to attacks such as Man in the Middle (MITM). However, the API provides some measures of protection against modification and repeat requests.
- It is not difficult to analyze the API used by the application (although there are already open documentation for it).
The demonstration shows the interception of unencrypted traffic and finding in it a request to the API responsible for sending the message.
Instagram and HTTPS
In the second part of the report, the Instagram application for Android was reviewed, and it uses the secure HTTPS protocol (HTTP + SSL) to interact with the API. This means that in the general case (in the absence of access to the device by the researcher and a fairly modern version of TLS), the interaction protocol is not vulnerable to MITM attacks.
But, having access to the phone, you can install your root certificate on it and easily decrypt traffic by replacing certificates for HTTPS connections (BurpSuite can do this automatically). The demonstration shows the interception of encrypted traffic after installing on the phone a monitored root certificate and finding in it a request to the API responsible for the photo's likes.
Instagram has a publicly documented API for developers. It sets strict enough limits for key functions (likes, subscriptions, posting, etc.). As it turned out, the Instagram application uses a different, private API, in which, of course, there are no such limits.
What is interesting about this private API in terms of “botany”? The main difference between the private API is that all important requests are signed with a private key (unique for the application version). Since the key is stored inside the application, you can get it using reverse engineering of the application.
Facebook and SSL Pinning
In the third part of the report, a Facebook application for Android was reviewed. This application uses a secure protocol HTTPS + add-on called SSL Pinning to interact with the API.
SSL Pinning - the implementation of the SSL server certificate API in the mobile application code. This technology is designed to protect against interception of traffic by installing a root certificate on the device and replacing certificates.
However, SSL Pinning can be disabled (and even in different ways):
- With the help of decompiling and modification of the application (complex method).
- Modifying low-level SSL functions on the device (requires root access, does not always work stably). Android SSL Bypass, iOS SSL KillSwitch programs work exactly according to this principle.
The report demonstrated how to disable SSL Pinning in a Facebook mobile application for Android (by removing one of the libraries used by the application - libsslx.so) and the subsequent successful interception of traffic.
As it turned out during the traffic analysis, the Facebook mobile application uses some undocumented API methods (including for registering accounts and logging in to the system).
An undocumented API method was also found that allows you to get your Facebook user ID by phone number. Here is a demonstration of the possible automated use of the obtained undocumented methods:
Finally
If you wish, you can always analyze the interaction protocol between the mobile application and the server. The use of additional security tools (such as SSL Pinning) can only somewhat complicate the work of the researcher. Therefore, developers should avoid using privileged undocumented API methods in the application (especially if there is a public and documented API).
In addition, it is possible to make a bot that will send exactly the same requests as the official mobile application. To combat such bots, we can recommend complicating the structure of requests to the API and carefully analyze all the parameters of requests on the server side.
At the “confrontation” NeoQUEST-2017 , which will be held on June 29 in St. Petersburg , as always, there will be cool reports on the most current trends in cybersecurity, modern protection mechanisms and ways to circumvent them.
If you are not from St. Petersburg, feel free to plan your vacation for June and come! White nights, movable bridges,
Source: https://habr.com/ru/post/320650/
All Articles