Huawei Agile Distributed Wi-Fi Solution: What is it? Part one
Surely many habrahabr users have seen an article on the Huawei blog - Do you have Wi-Fi here? In which it is said not easy fate of corporate WiFi-access, in the context of the ubiquitous growth in the number of wireless devices and network infrastructure, in general.
Here, for example, quotes from it:

The solution to this complex issue was the decision - Huawei Agile Distributed Wi-Fi, which is actually mentioned in the vendor’s article. We, fortunate enough, as I understand it, were among the first in Russia to “touch” this solution live.
For a comprehensive study, we received, so to say, a demo kit consisting of:

A typical application of Agile Distributed WLAN is a scenario with a high concentration of rooms, such as: hotels, dormitory schools, hospitals, ie objects where walls or other structural elements of buildings can lead to a serious Wi-Fi signal attenuation. In other words, where the use of the traditional architecture of WLAN networks is not efficient or prohibitively expensive, due to the need to install a larger number of access points, for better radio coverage.

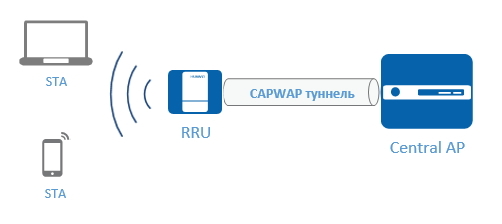
As we already know, Agile Distributed WLAN consists of a central access point, and remote radio modules (RRU). RRUs receive and send “wireless” packets and transparently transmit them to the central access point for processing.
')
The central access point is connected to the RRU via a UTP cable. Compared with the antenna cable used for classic access points, when external antennas are removed, the “copper” provides a greater WLAN deployment distance, allowing you to further spread the RRU from the central access point, thereby reaching to the “dead” zones.
The central access point provides RRU with PoE power, while it can be powered via UPoE itself (belongs to the ADP9430DN-12 model). Also, the RRU can be connected via a PoE switch, provided that IP reachability (Layer2) with the central AP is provided.
And a little more theory on the topic.
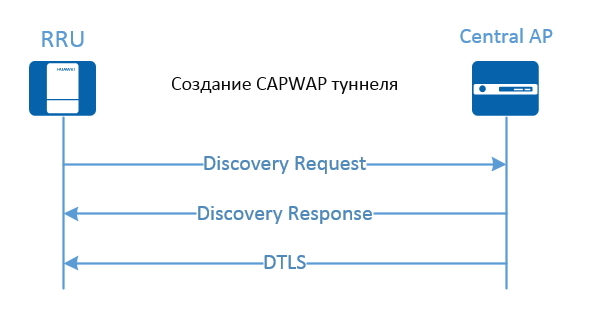
After the radio modules (RRU) are connected and obtained IP addresses from the central access point, they begin to establish CAPWAP (Control And Provisioning of Wireless Access Points) tunnels with a central access point.
CAPWAP tunnels use DTLS (Datagram Transport Layer Security) encryption and so-called “heartbeat detection” detection (it allows you to check and maintain active connections without permanently resuming them) to ensure security.
The Central AP sends control packets and data packets to the radio modules (RRU) in a centralized manner, through CAPWAP tunnels. To improve the reliability of the communication channel and to prevent losses, when the volume of served traffic increases, a high priority is configured for CAPWAP control packets.
In addition, the radio modules (RRU) in the process of their launch are able to determine whether their version of the system software is the same as at the central access point, in accordance with the parameters in the accepted Authentication Response package. If there is no such correspondence, then the radio modules go offline and do not participate in the work.
So, let's proceed directly to the initial setup of the Agile Distributed WLAN system.
What we want to do:
Since, for reasons not clear to us, the package did not have a power supply for the central access point, we decided to power it from an old HP ProCurve PoE switch, while, as already mentioned, the radio modules were powered by PoE from the AD9430DN itself 12.

Thus, the scheme of the organization of communication is as follows:
The default login / password for the console: admin / admin @ huawei

The current version of the system software at the time of writing this article is V200R007C10SPC300:
# Write the device name, management IP addresses, and the default route:
# We configure SSH access to the device, having previously created a user and generated rsa keys:
# Add GE 0/0 / 8..9 interfaces to the managing VLAN100:
# Add uplink GE 0/0/12 interface to the service VLAN101:
# Set up a central access point as a DHCP server for RRU and STA:
# Create an AP group:
# Create a profile for the regulatory domain, country code and apply the profile for the ap-group:
# Assign the management VLAN for the RRU:
# Add radio modules RRU to the configuration (we use the method without authentication):
# We connect the radio modules and check their status:
# Configure WLAN settings (security, ssid, vap):
# Check configuration:
A web interface is also available to configure the system:
The end of the first part.
Here, for example, quotes from it:
According to analysts, already in 2019, the volume of user traffic transmitted via Wi-Fi networks will exceed the volumes attributable to wired connections.

Obviously, if access to the corporate infrastructure via Wi-Fi becomes a priority method of connection, then it will be imposed on more stringent requirements for security, quality of work, flexibility and scaling.
All this entails the need to modernize the WLAN infrastructure and introduce modern Enterprise-level solutions. Here comes the first surprise: for the leadership of virtually any enterprise or company, Wi-Fi simply works wonderfully with the help of a “magic box” that costs 3,000 rubles. And “this is incomprehensible to the mind,” as an access point can cost 30 or more thousand rubles! And also “give you some kind of wireless controller” a wireless controller!
The solution to this complex issue was the decision - Huawei Agile Distributed Wi-Fi, which is actually mentioned in the vendor’s article. We, fortunate enough, as I understand it, were among the first in Russia to “touch” this solution live.
For a comprehensive study, we received, so to say, a demo kit consisting of:
- One Central Access Point (Central AP) - AD9430DN-12
- Two radio modules (RRU - Remote Radio Unit) - R230D.

Concept
A typical application of Agile Distributed WLAN is a scenario with a high concentration of rooms, such as: hotels, dormitory schools, hospitals, ie objects where walls or other structural elements of buildings can lead to a serious Wi-Fi signal attenuation. In other words, where the use of the traditional architecture of WLAN networks is not efficient or prohibitively expensive, due to the need to install a larger number of access points, for better radio coverage.

As we already know, Agile Distributed WLAN consists of a central access point, and remote radio modules (RRU). RRUs receive and send “wireless” packets and transparently transmit them to the central access point for processing.
')
The central access point is connected to the RRU via a UTP cable. Compared with the antenna cable used for classic access points, when external antennas are removed, the “copper” provides a greater WLAN deployment distance, allowing you to further spread the RRU from the central access point, thereby reaching to the “dead” zones.
The central access point provides RRU with PoE power, while it can be powered via UPoE itself (belongs to the ADP9430DN-12 model). Also, the RRU can be connected via a PoE switch, provided that IP reachability (Layer2) with the central AP is provided.
And a little more theory on the topic.
After the radio modules (RRU) are connected and obtained IP addresses from the central access point, they begin to establish CAPWAP (Control And Provisioning of Wireless Access Points) tunnels with a central access point.

CAPWAP tunnels use DTLS (Datagram Transport Layer Security) encryption and so-called “heartbeat detection” detection (it allows you to check and maintain active connections without permanently resuming them) to ensure security.
The Central AP sends control packets and data packets to the radio modules (RRU) in a centralized manner, through CAPWAP tunnels. To improve the reliability of the communication channel and to prevent losses, when the volume of served traffic increases, a high priority is configured for CAPWAP control packets.

In addition, the radio modules (RRU) in the process of their launch are able to determine whether their version of the system software is the same as at the central access point, in accordance with the parameters in the accepted Authentication Response package. If there is no such correspondence, then the radio modules go offline and do not participate in the work.
Initial setup
So, let's proceed directly to the initial setup of the Agile Distributed WLAN system.
What we want to do:
- Assemble a stand from AD9430DN-12 and 2xR230D and test its performance
- Assign IP addresses from our LAN
- Configure WLAN services, using the example of the Small-Scale Network WLAN
- Provide STA Internet access
Since, for reasons not clear to us, the package did not have a power supply for the central access point, we decided to power it from an old HP ProCurve PoE switch, while, as already mentioned, the radio modules were powered by PoE from the AD9430DN itself 12.

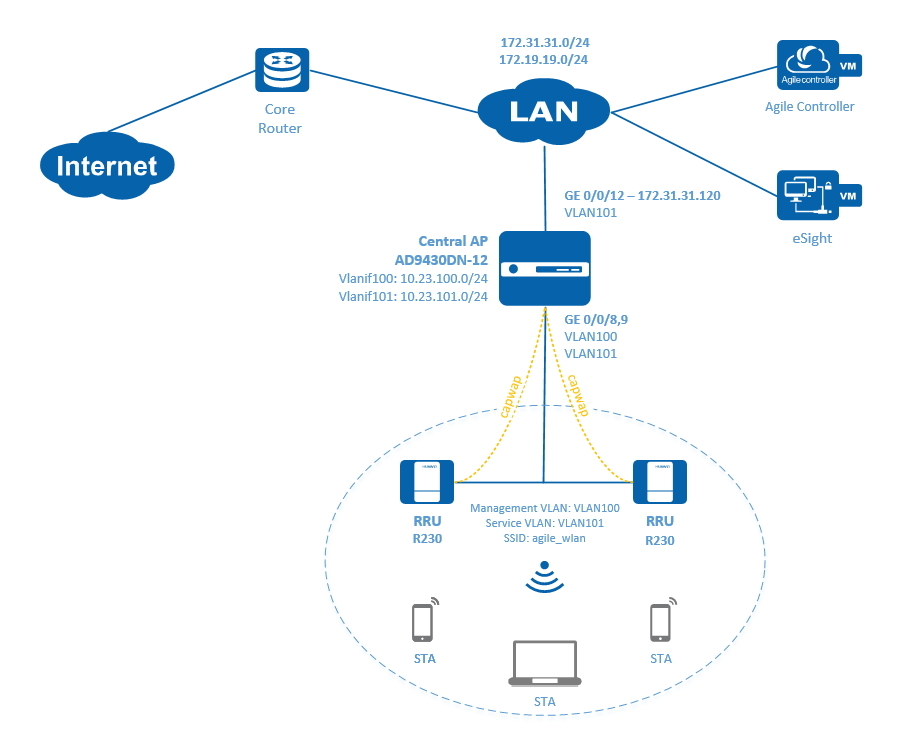
Thus, the scheme of the organization of communication is as follows:
- The central access point of the ADP9430DN-12 GE 0/0/12 uplink interface looks into the LAN-network (Vlanif1, 172.31.31.120)
- R230D radio modules are connected to GE 0/0/8.9 downlink interfaces (Vlanif100, dynamically allocating addresses via DHCP: 10.23.100.0/24)
- Clients connected to a Wi-Fi network (STA) receive addresses via DHCP: 10.23.101.0/24 (Vlanif101)
- SSID: agile_wlan

The default login / password for the console: admin / admin @ huawei

The current version of the system software at the time of writing this article is V200R007C10SPC300:
<Agile_Wlan>display version Huawei Versatile Routing Platform Software VRP (R) software, Version 5.160 (AD9430DN-12 FAT V200R007C10SPC300) Copyright (C) 2011-2016 HUAWEI TECH CO., LTD Huawei AD9430DN-12 Router uptime is 1 week, 0 day, 1 hour, 8 minutes 
CLI
# Write the device name, management IP addresses, and the default route:
<Huawei> system-view [Huawei] sysname Agile_Wlan [AGILE_WLAN] vlan 1 [AGILE_WLAN-vlan1] quit [AGILE_WLAN] interface gigabitethernet 0/0/12 [AGILE_WLAN-GigabitEthernet0/0/12] port link-type trunk [AGILE_WLAN-GigabitEthernet0/0/12] port trunk allow-pass vlan 1 [AGILE_WLAN-GigabitEthernet0/0/12] port trunk pvid vlan 1 [AGILE_WLAN-GigabitEthernet0/0/12] quit [AGILE_WLAN] interface vlanif 1 [AGILE_WLAN-Vlanif1] ip address 172.31.31.120 255.255.255.0 [AGILE_WLAN-Vlanif1] ip route-static 0.0.0.0 0.0.0.0 172.31.31.120 [AGILE_WLAN-Vlanif1] quit # We configure SSH access to the device, having previously created a user and generated rsa keys:
[AGILE_WLAN]rsa local-key-pair create The key name will be: Host RSA keys defined for Host already exist. Confirm to replace them? (y/n):y The range of public key size is (512 ~ 2048). NOTES: If the key modulus is less than 2048, It will introduce potential security risks. Input the bits in the modulus[default = 2048]: Generating keys... ...........................................................................................................................................+++ ....................+++ ..............................................++++++++ ................++++++++ [AGILE_WLAN]user-interface vty 0 4 [AGILE_WLAN-ui-vty0-4]authentication-mode aaa [AGILE_WLAN-ui-vty0-4]protocol inbound ssh [AGILE_WLAN-ui-vty0-4]quit [AGILE_WLAN]aaa [AGILE_WLAN-aaa]local-user user1 password irreversible-cipher Pa$$w0rd [AGILE_WLAN-aaa]local-user user1 privilege level 15 [AGILE_WLAN-aaa]local-user user1 service-type ssh http terminal [AGILE_WLAN]ssh user user1 authentication-type password # Add GE 0/0 / 8..9 interfaces to the managing VLAN100:
[AGILE_WLAN] vlan batch 100 101 [AGILE_WLAN] interface gigabitethernet 0/0/8 [AGILE_WLAN-GigabitEthernet0/0/8] port link-type trunk [AGILE_WLAN-GigabitEthernet0/0/8] port trunk pvid vlan 100 [AGILE_WLAN-GigabitEthernet0/0/8] port trunk allow-pass vlan 100 [AGILE_WLAN-GigabitEthernet0/0/8] quit # Add uplink GE 0/0/12 interface to the service VLAN101:
[AGILE_WLAN] interface gigabitethernet 0/0/12 [AGILE_WLAN-GigabitEthernet0/0/12] port link-type trunk [AGILE_WLAN-GigabitEthernet0/0/12] port trunk allow-pass vlan 101 [AGILE_WLAN-GigabitEthernet0/0/12] quit # Set up a central access point as a DHCP server for RRU and STA:
[AGILE_WLAN] dhcp enable [AGILE_WLAN] interface vlanif 100 [AGILE_WLAN-Vlanif100] ip address 10.23.100.1 24 [AGILE_WLAN-Vlanif100] dhcp select interface [AGILE_WLAN-Vlanif100] quit [AGILE_WLAN] interface vlanif 101 [AGILE_WLAN-Vlanif101] ip address 10.23.101.1 24 [AGILE_WLAN-Vlanif101] dhcp select interface [AGILE_WLAN-Vlanif101] quit # Create an AP group:
[AGILE_WLAN] wlan [AGILE_WLAN-wlan-view] ap-group name ap-group1 [AGILE_WLAN-wlan-ap-group-ap-group1] quit # Create a profile for the regulatory domain, country code and apply the profile for the ap-group:
[AGILE_WLAN-wlan-view] regulatory-domain-profile name domain1 [AGILE_WLAN-wlan-regulate-domain-domain1] country-code ru [AGILE_WLAN-wlan-regulate-domain-domain1] quit [AGILE_WLAN-wlan-view] ap-group name ap-group1 [AGILE_WLAN-wlan-ap-group-ap-group1] regulatory-domain-profile domain1 Warning: Modifying the country code will clear channel, power and antenna gain configurations of the radio and reset the AP. Continu e?[Y/N]:y [AGILE_WLAN-wlan-ap-group-ap-group1] quit [AGILE_WLAN-wlan-view] quit # Assign the management VLAN for the RRU:
[AGILE_WLAN] management-vlan 100 # Add radio modules RRU to the configuration (we use the method without authentication):
[AGILE_WLAN] wlan [AGILE_WLAN-wlan-view] ap auth-mode no-auth [AGILE_WLAN-wlan-view] ap-id 1 [AGILE_WLAN-wlan-view] ap-id 2 [AGILE_WLAN-wlan-ap-1] ap-name area_1 [AGILE_WLAN-wlan-ap-1] ap-group ap-group1 Warning: This operation may cause AP reset. If the country code changes, it will clear channel, power and antenna gain configuration s of the radio, Whether to continue? [Y/N]:y [AGILE_WLAN-wlan-ap-1] quit # We connect the radio modules and check their status:
[Agile_Wlan-wlan-view]display ap all Info: This operation may take a few seconds. Please wait for a moment.done. Total AP information: nor : normal [2] ------------------------------------------------------------------------------------------------------------- ID MAC Name Group IP Type State STA Uptime ------------------------------------------------------------------------------------------------------------- 1 9c50-ee25-2240 9c50-ee25-2240 ap-group1 10.23.100.215 R230D nor 0 4D:0H:25M:16S 2 9c50-ee25-1c00 9c50-ee25-1c00 ap-group1 10.23.100.225 R230D nor 0 4D:0H:25M:53S ------------------------------------------------------------------------------------------------------------- Total: 2 # Configure WLAN settings (security, ssid, vap):
[AGILE_WLAN-wlan-view] security-profile name wlan-security [AGILE_WLAN-wlan-sec-prof-wlan-security] security wpa2 psk pass-phrase 12345678 aes [AGILE_WLAN-wlan-sec-prof-wlan-security] quit [AGILE_WLAN-wlan-view] ssid-profile name wlan-ssid [AGILE_WLAN-wlan-ssid-prof-wlan-ssid] ssid agile_wlan [AGILE_WLAN-wlan-ssid-prof-wlan-ssid] quit [AGILE_WLAN-wlan-view] vap-profile name wlan-vap [AGILE_WLAN-wlan-vap-prof-wlan-vap] service-vlan vlan-id 101 [AGILE_WLAN-wlan-vap-prof-wlan-vap] security-profile wlan-security [AGILE_WLAN-wlan-vap-prof-wlan-vap] ssid-profile wlan-ssid [AGILE_WLAN-wlan-vap-prof-wlan-vap] quit [AGILE_WLAN-wlan-view] ap-group name ap-group1 [AGILE_WLAN-wlan-ap-group-ap-group1] vap-profile wlan-vap wlan 1 radio 0 [AGILE_WLAN-wlan-ap-group-ap-group1] vap-profile wlan-vap wlan 1 radio 1 [AGILE_WLAN-wlan-ap-group-ap-group1] quit # Check configuration:
[Agile_Wlan]display vap ssid agile_wlan Info: This operation may take a few seconds, please wait. WID : WLAN ID ------------------------------------------------------------------------------------- AP ID AP name RfID WID BSSID Status Auth type STA SSID ------------------------------------------------------------------------------------- 1 9c50-ee25-2240 0 1 9C50-EE25-2240 ON Open+Portal 0 agile_wlan 1 9c50-ee25-2240 1 1 9C50-EE25-2250 ON Open+Portal 0 agile_wlan 2 9c50-ee25-1c00 0 1 9C50-EE25-1C00 ON Open+Portal 1 agile_wlan 2 9c50-ee25-1c00 1 1 9C50-EE25-1C10 ON Open+Portal 0 agile_wlan ------------------------------------------------------------------------------------- Total: 4 [Agile_Wlan]display station ssid agile_wlan Rf/WLAN: Radio ID/WLAN ID Rx/Tx: link receive rate/link transmit rate(Mbps) ------------------------------------------------------------------------------------------------- STA MAC AP ID Ap name Rf/WLAN Band Type Rx/Tx RSSI VLAN IP address ------------------------------------------------------------------------------------------------- a8c8-3a05-e343 2 9c50-ee25-1c00 0/1 2.4G 11n 5/2 -83 101 10.23.101.248 ------------------------------------------------------------------------------------------------- Total: 1 2.4G: 1 5G: 0 A web interface is also available to configure the system:


The end of the first part.
Source: https://habr.com/ru/post/320546/
All Articles