Give me a foothold or secure internet is reality
The main problem of access to information resources of the Internet is that the point of connection to it becomes part of this network and, as a result, becomes publicly available, interacts with it using generally accepted network protocols and interacts with the protected network using the same protocols. No testing methods can prove the absence of software errors (Dijkstra's postulate). Having unlimited access to the Internet connection point, an attacker can use standard network protocols, standard software and errors or errors found in its settings to make unauthorized access through the connection point inside the corporate network with all the ensuing consequences.
Within the framework of the discussed problem, there are two most likely ways to violate the confidentiality of information:
 To paraphrase Archimedes, who said, “give me a foothold and I will turn the Earth over”, you can say “give me the point of connecting your network to the Internet and I will hack your network.”
To paraphrase Archimedes, who said, “give me a foothold and I will turn the Earth over”, you can say “give me the point of connecting your network to the Internet and I will hack your network.”
')
Since the public network (in this case, the Internet) is outside the control of security administrators of automated systems of state authorities and organizations of the Russian Federation, the only way to manage the risk of listening to traffic while passing through a public network is to use cryptographic tools. Such means may be VPN, encrypted tunnels, and when accessing portals, tls / https protocol can be used.
A more serious threat is penetration into the computational networks of state authorities and organizations of the Russian Federation through points of connection to the public network, when there is a possibility not only access to confidential information, but also the possibility of its destruction, when no cryptographic protection will save from damage.
Managing the risk of penetration into a LAN through a public network connection point includes the resolution of two main technical issues:
- hiding the structure of the internal corporate network;
- protection of the connection point to the corporate network from unauthorized access.
However, if we consider the Internet (or any other public network) not as an IP network, but as some substance that provides a set of services (email, transport medium, ftp server, Web server, portal of public services, etc. .), it turns out that you can find technical solutions that allow these services to be used without providing an access point to the attacker.
And so, in order to prevent unauthorized access from the Internet to the user's computer or to the corporate network, following Archimedes' postulate, the attacker must be denied access to the LAN access point or the protected computer. How to do it?
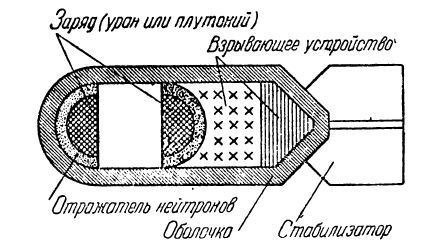 Today, everyone probably knows that two hemispheres are used in atomic bombs. And until they merged into one deadly ball, this two hemisphere bomb poses no threat.
Today, everyone probably knows that two hemispheres are used in atomic bombs. And until they merged into one deadly ball, this two hemisphere bomb poses no threat.
By analogy with the atomic bomb, the point of connection to the Internet can also be made up of two "hemispheres" - two servers that exchange data with each other over a high-speed interface, for example, IEE1394:
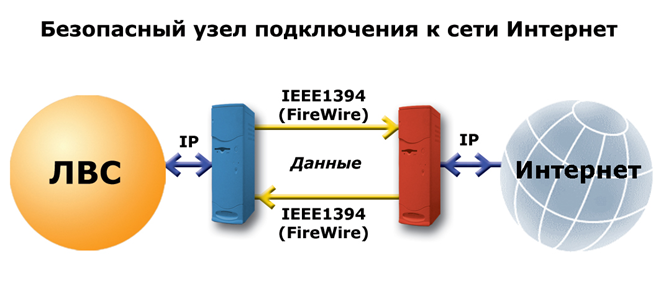
As can be seen from the figure, it separates local and public networks and does not lead to the appearance of any possibilities for access via any network protocols from the Internet LAN network, and also does not allow access of LAN users to the Internet.
For simplicity, we will call the implementation of such a connection a binary Internet connection point or Shield point a safe / secure connection point:
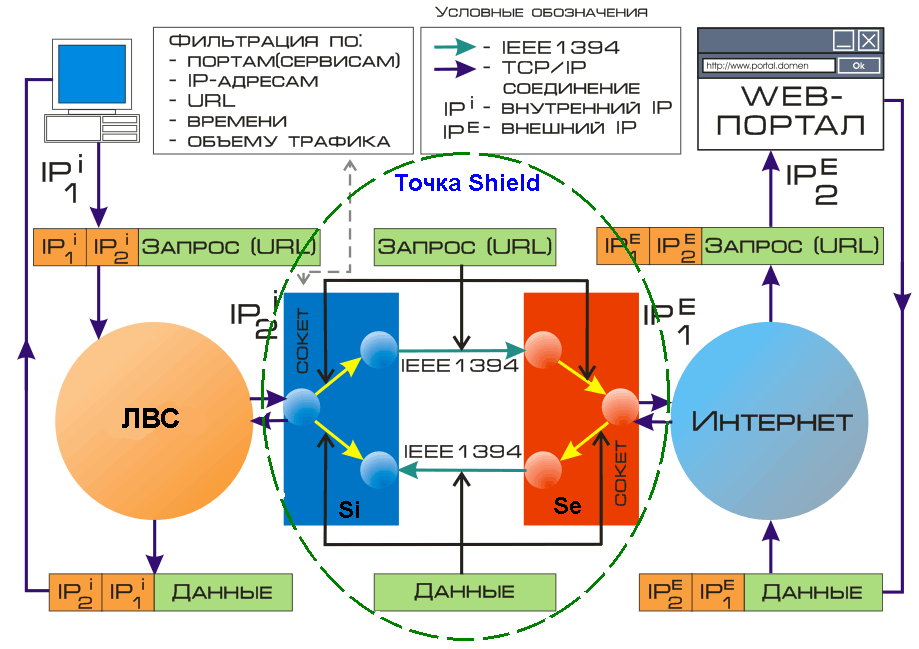
On the internal server Si there is no information about the public network. Similarly, on the external server Se, there is no information about the internal LAN. This is one of the reasons for the impossibility of a breakthrough from the Internet to the internal LAN, and, conversely, from the internal LAN to the public network. Even if an intruder in an open network becomes aware of any address on the internal network, using it, he can go anywhere, just not into the internal network.
Thus, the connection point Shield provides:
The Shield connection point can be viewed as a proxy server when LAN users access the web resources of the Internet using browsers.
The weak link is the external server Se access point Shield, which is directly connected to the Internet. An attacker can gain control over this server, but he cannot achieve his goal of penetrating a LAN and causing damage to it. But since this will be immediately known to the LAN administrator (for example, communication with the outside world will disappear), you can always go to the backup channel and restore communication with the outside world.
Within the framework of the discussed problem, there are two most likely ways to violate the confidentiality of information:
- Listening and reconstruction of the traffic of transmitted data between corporate networks at some point of the public network;
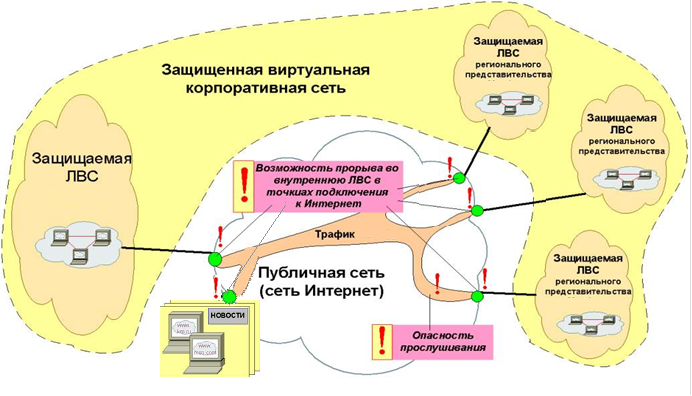
- Penetration into the corporate network at the point of connection to the public network and / or disruption of its normal operation.
 To paraphrase Archimedes, who said, “give me a foothold and I will turn the Earth over”, you can say “give me the point of connecting your network to the Internet and I will hack your network.”
To paraphrase Archimedes, who said, “give me a foothold and I will turn the Earth over”, you can say “give me the point of connecting your network to the Internet and I will hack your network.”')
Since the public network (in this case, the Internet) is outside the control of security administrators of automated systems of state authorities and organizations of the Russian Federation, the only way to manage the risk of listening to traffic while passing through a public network is to use cryptographic tools. Such means may be VPN, encrypted tunnels, and when accessing portals, tls / https protocol can be used.
A more serious threat is penetration into the computational networks of state authorities and organizations of the Russian Federation through points of connection to the public network, when there is a possibility not only access to confidential information, but also the possibility of its destruction, when no cryptographic protection will save from damage.
Managing the risk of penetration into a LAN through a public network connection point includes the resolution of two main technical issues:
- hiding the structure of the internal corporate network;
- protection of the connection point to the corporate network from unauthorized access.
However, if we consider the Internet (or any other public network) not as an IP network, but as some substance that provides a set of services (email, transport medium, ftp server, Web server, portal of public services, etc. .), it turns out that you can find technical solutions that allow these services to be used without providing an access point to the attacker.
And so, in order to prevent unauthorized access from the Internet to the user's computer or to the corporate network, following Archimedes' postulate, the attacker must be denied access to the LAN access point or the protected computer. How to do it?
 Today, everyone probably knows that two hemispheres are used in atomic bombs. And until they merged into one deadly ball, this two hemisphere bomb poses no threat.
Today, everyone probably knows that two hemispheres are used in atomic bombs. And until they merged into one deadly ball, this two hemisphere bomb poses no threat.By analogy with the atomic bomb, the point of connection to the Internet can also be made up of two "hemispheres" - two servers that exchange data with each other over a high-speed interface, for example, IEE1394:

As can be seen from the figure, it separates local and public networks and does not lead to the appearance of any possibilities for access via any network protocols from the Internet LAN network, and also does not allow access of LAN users to the Internet.
For simplicity, we will call the implementation of such a connection a binary Internet connection point or Shield point a safe / secure connection point:

On the internal server Si there is no information about the public network. Similarly, on the external server Se, there is no information about the internal LAN. This is one of the reasons for the impossibility of a breakthrough from the Internet to the internal LAN, and, conversely, from the internal LAN to the public network. Even if an intruder in an open network becomes aware of any address on the internal network, using it, he can go anywhere, just not into the internal network.
Thus, the connection point Shield provides:
- The lack of interaction at the network level between the internal Si and the external Se servers and, as a consequence, the preservation of the independence of the protected and public computer networks, to the extent that they can have the same IP addressing;
- Transparency for both standard protocols (http, https, ftp, ssl, pop3, etc.), as well as the ability to write custom protocols for client-server systems;
- Access of users of protected computer networks to various public network services in the absence of network interaction between protected and public networks;
- The possibility of separate administration of the external and internal gateways: the administrator of the external gateway does not have access (does not know the password) to the internal gateway and vice versa.
The Shield connection point can be viewed as a proxy server when LAN users access the web resources of the Internet using browsers.
The weak link is the external server Se access point Shield, which is directly connected to the Internet. An attacker can gain control over this server, but he cannot achieve his goal of penetrating a LAN and causing damage to it. But since this will be immediately known to the LAN administrator (for example, communication with the outside world will disappear), you can always go to the backup channel and restore communication with the outside world.
Source: https://habr.com/ru/post/320374/
All Articles