This is not ransomware, but in any case can “seize” your server.

This week we’ll look at the ransomware (ransomware), which is not really so. And it is not even a malware. But he is able to "seize" your server.
A few days ago, we saw a typical RDP attack through a remote desktop, which led us to believe that it was similar to the attack that we talked about a few months ago and which cyber-criminals used to infect devices with a cryptographer. But we were greatly mistaken.
')
First of all, because instead of data encryption, this “malware” blocked the desktop with a password that the victim does not know. Secondly, it does not require a ransom (!) In exchange for a key or password , but rather seeks to keep the device locked for as long as possible in order to use it for bitcoin mining as long as possible. And, thirdly, it does not use malware as such.
After hackers gained access to your machine using the “brute force” method (for example, in this case, the server received 900 attempts per day), hackers copy a file called BySH01.zip. It, in turn, contains the following files:
1. BySH01.exe (executable file via AutoIt)
2. 7za.exe (legal program: well-known free 7zip utility)
3. tcping.exe (legal program: utility for executing TCP pings)
4. MW_C.7z (file zipped with password), which contains:
- The application is a legal program for the "extraction" of Bitcoons
- Application - legal program to lock the Windows desktop
The hacker launches the file BySH01.exe, and the following interface appears:
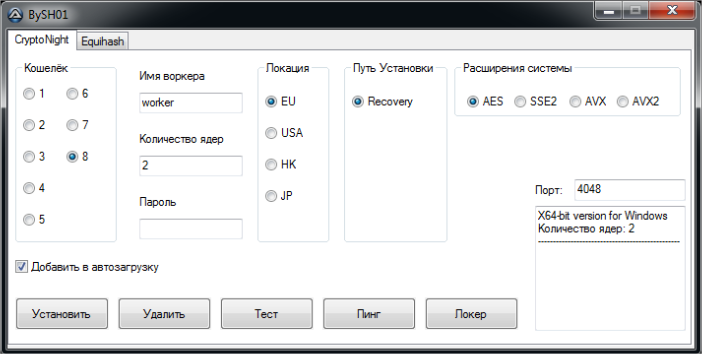
Essentially, a bitcoin mining application uses this interface to configure how many cores to use, what wallet to send bitcoins, etc. After the required settings are selected, the hacker presses the Install button to install and start the bitcoins mining application. The application is called CryptoNight, and it is designed for mining bitcoins using processors.
He then presses the Loker button, which installs and launches the application for locking the desktop. This is a commercial application Desktop Lock Express 2, modified only in such a way that the information shown in the file properties is exactly the same as that of the svchost.exe system file. Finally, it deletes all files used for the attack, with the exception of CryptoNight and Desktop Lock Express 2.

Desktop Lock Express 2: an application used by hackers.
We detected and blocked several attacks in different countries. Similar examples once again show how cyber criminals take advantage of weak passwords that can be picked up using the brute force method for a certain period of time. Malware is no longer required to access the system, so pay attention to using a complex password and protecting against unwanted visitors.
Tips for system administrators
In addition to using solutions like Adaptive Defense , which detect and prevent this type of attack, here’s a couple of tips for all system administrators who are forced to open RDP:
- Configure it to use a nonstandard port. 99.99% of intruders track all Internet connections on TCP and UDP ports 3389. They can track others, but they don’t have to do it, because Most system administrators do not change these ports. Those who do this in combination with complex passwords, take care of the security of the corporate network, so that hackers find it harder to obtain registration data within a reasonable time using the “brute force” method.
- Track failed RDP connection attempts. Thus, it is quite easy to calculate Brute force attacks, since in this case, hackers use automated systems that make new connection attempts every few seconds.
Source: https://habr.com/ru/post/320290/
All Articles