The right way to become a safe person: from lamer to practical exploit
I welcome, you% habrauzer%. I read here an article on the Habré "Exam for future" Russian hackers "at the Moscow Polytech . " And my brain went into an endless cycle of misunderstanding of what was happening. Whether I now glanced on "hackers" school forum, or really on habr. Excuse me, with this approach, the current generation of Wites will simply not be replaced.
In this article, I would like to write how, in my humble opinion (previously a baghunter on the side of black metal), it would be really worth starting the road. And in no case with Kali linux (as it turns out they teach at the polytechnic of the capital.
If you are interested in part and my way, welcome under cat.
Many steps at users of a habr are already executed, therefore can safely pass to the level. Basically, the post will deal with Windows, since this OS is my specialty, as the most common. I will look at the code here on the example of the buffer overflow vulnerability, but I’ll not get to the finished exploit, this is a separate and very extensive topic.
')
First of all, you should study the operating system in which you work. No matter how trite it may sound, but OS knowledge sometimes presents things that are not reversed.
For example, the UAC bypass in Windows 10 was discovered thanks to one procmon that worked while using eventvwr. It's funny, but the fact of raising the rights was that eventvwr first looked for the registry key in one branch, but did not find it in another. In fact, in the first place, usually nothing was ever found, in the end it was enough to just write down the path to your file and run the eventvwr as soon as the application was started with elevated permissions.
There was not a single byte, but the researchers found a UAC bypass.
So the first is to learn the operating system. Thoroughly. Read different books on its device. Specifically, on Windows, I can advise Mark Russinovich "Internal Windows". A book from the author of such popular utilities as autoruns and procmon
For Windows: play around with programs like RegMon and FileMon. They allow you to make OS "before" and "after" and compare. See what changes make different settings like changing OS settings and the like.
Put the virtual machine and try to “kill” the OS in the most perverted ways, and then fix it.
After that, you can go back to RegMon and FileMon and start running various samples of Malvari. After that, you will already be able to find almost any malware simply by the symptoms.
Malware can be obtained from here:
After you study the operating system in which you work, you can proceed further.
At this stage, learn some programming language. For example, python - it’s pretty good for a newbie and will come in handy for you in writing exploits and fuzzing (which we will look at next).
After that, study C, he will give an understanding of working with memory, teach you to think about performance, and also be useful as a native language.
Further, the assembly language, at least in general principles. What are registers, what is a stack, basic instructions. It is useful when reversing, especially no special knowledge is required for reading.
In this order: python, C / C ++, assembler
At this stage, you must learn to distinguish between bad code and good code. Learn to see the errors, and also know the assembler.
How to check whether you have passed this step? Just tell me what the following code may cause:
This program receives a string in its arguments and encrypts it with a Caesar algorithm with key 5, storing the result in EncryptedStr.
What is wrong with this code and what can it lead to?
Answer:
But this code is from the 2000s. At the moment, it is difficult to exploit the hole, because such techniques as DEP, ASLR, Security Cookies have appeared. However, this also costs. You can read for example, for example, ret2libc
Let's look at the previous example in assembler listing using IDA Pro
No matter how well you rummage, it is difficult even to find me here RCE. But life examples are much more complicated. Therefore, there are special tools - fuzzers.
What is fuzzer? This is alaser from maser-type films, a special software that floods the application with incorrect data in order to find non-standard behavior. That is, we can write such a script, which in all places where input data is received will send random data and see the result. If the result led to a fall, then we found a vulnerability.
For example, for our application, the simplest fuzzer looks like this:
And here is the result:
Read more about phasers here.
Thus, having no source code or disassembling skills can be found vulnerability. You can write fuzzers that generate any kind of input data.
After that you can start writing exploits.
For example, for our application, the simplest exploit will look something like this in the pseudocode.
Where address is the address of the rewritable buffer in memory, and there_shellcode is the shellcode that is executed when the buffer overflows.
How exactly is this found in Google, I just gave a farewell.
My version unlike the article given before the cut is much more extensive and practical. However, more difficult.
Follow what path - by means of the scriptkiddies, or by exploiting - only you choose.
In this article, I would like to write how, in my humble opinion (previously a baghunter on the side of black metal), it would be really worth starting the road. And in no case with Kali linux (as it turns out they teach at the polytechnic of the capital.
If you are interested in part and my way, welcome under cat.
Many steps at users of a habr are already executed, therefore can safely pass to the level. Basically, the post will deal with Windows, since this OS is my specialty, as the most common. I will look at the code here on the example of the buffer overflow vulnerability, but I’ll not get to the finished exploit, this is a separate and very extensive topic.
')
Step 0. From lamer to noob
First of all, you should study the operating system in which you work. No matter how trite it may sound, but OS knowledge sometimes presents things that are not reversed.
For example, the UAC bypass in Windows 10 was discovered thanks to one procmon that worked while using eventvwr. It's funny, but the fact of raising the rights was that eventvwr first looked for the registry key in one branch, but did not find it in another. In fact, in the first place, usually nothing was ever found, in the end it was enough to just write down the path to your file and run the eventvwr as soon as the application was started with elevated permissions.
There was not a single byte, but the researchers found a UAC bypass.
So the first is to learn the operating system. Thoroughly. Read different books on its device. Specifically, on Windows, I can advise Mark Russinovich "Internal Windows". A book from the author of such popular utilities as autoruns and procmon
For Windows: play around with programs like RegMon and FileMon. They allow you to make OS "before" and "after" and compare. See what changes make different settings like changing OS settings and the like.
Put the virtual machine and try to “kill” the OS in the most perverted ways, and then fix it.
After that, you can go back to RegMon and FileMon and start running various samples of Malvari. After that, you will already be able to find almost any malware simply by the symptoms.
Malware can be obtained from here:
Hidden text
Attention! Sites containing links to malicious files
Go at your own risk
Many malware written by ours does not start on the RU machines, put the ENG-machines without the Russian layout on the virtual machine
malwareblacklist.com
malwr.com (registration required)
kernelmode.info (usually well known malware)
Go at your own risk
Many malware written by ours does not start on the RU machines, put the ENG-machines without the Russian layout on the virtual machine
malwareblacklist.com
malwr.com (registration required)
kernelmode.info (usually well known malware)
After you study the operating system in which you work, you can proceed further.
Step 1. From noob to developer
At this stage, learn some programming language. For example, python - it’s pretty good for a newbie and will come in handy for you in writing exploits and fuzzing (which we will look at next).
After that, study C, he will give an understanding of working with memory, teach you to think about performance, and also be useful as a native language.
Further, the assembly language, at least in general principles. What are registers, what is a stack, basic instructions. It is useful when reversing, especially no special knowledge is required for reading.
In this order: python, C / C ++, assembler
Step 2. From the developer to the good developer
At this stage, you must learn to distinguish between bad code and good code. Learn to see the errors, and also know the assembler.
How to check whether you have passed this step? Just tell me what the following code may cause:
#define _CRT_SECURE_NO_WARNINGS #include <stdio.h> #include <stdlib.h> #include <string.h> void Encr(char *in, char *out, int key) { for (int i = 0; i < strlen(in); i++) out[i] = in[i] + key; } int main(int argc, char *argv[]) { char EncryptedStr[10] = { 0 }; if (argc > 1) { Encr(argv[1], EncryptedStr, 5); printf("Encrypted: %s\n", EncryptedStr); } return 0; } This program receives a string in its arguments and encrypts it with a Caesar algorithm with key 5, storing the result in EncryptedStr.
What is wrong with this code and what can it lead to?
Answer:
Hidden text
This program can lead to a buffer overflow if you pass a string longer than 9 (the 10th character is zero). That will overwrite the return address from the function in the stack and allow to execute arbitrary code in the process memory. If this were in the server software - this could lead to the fact that an unauthorized user could execute any code on the server
But this code is from the 2000s. At the moment, it is difficult to exploit the hole, because such techniques as DEP, ASLR, Security Cookies have appeared. However, this also costs. You can read for example, for example, ret2libc
Step 3. From a good developer to a reverse
Let's look at the previous example in assembler listing using IDA Pro
Hidden text
No matter how well you rummage, it is difficult even to find me here RCE. But life examples are much more complicated. Therefore, there are special tools - fuzzers.
What is fuzzer? This is a
For example, for our application, the simplest fuzzer looks like this:
#/usr/bin/python import subprocess i = 0; while True: i += 1 if subprocess.call('test1.exe {0}'.format("A" * i), shell=True) != 0: print 'Crashed with arguments: {0}'.format("A" * i) break print "Finished" And here is the result:
Hidden text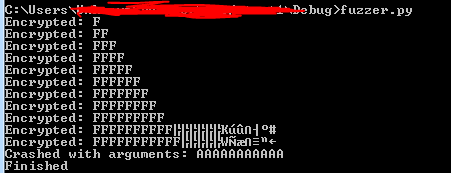
Read more about phasers here.
Thus, having no source code or disassembling skills can be found vulnerability. You can write fuzzers that generate any kind of input data.
From reverser to exploiter
After that you can start writing exploits.
For example, for our application, the simplest exploit will look something like this in the pseudocode.
#/usr/bin/python import subprocess subprocess.call('test1.exe '.format("A" * 10 + address + there_shellcode), shell=True); Where address is the address of the rewritable buffer in memory, and there_shellcode is the shellcode that is executed when the buffer overflows.
How exactly is this found in Google, I just gave a farewell.
Instead of conclusion
My version unlike the article given before the cut is much more extensive and practical. However, more difficult.
Follow what path - by means of the scriptkiddies, or by exploiting - only you choose.
Source: https://habr.com/ru/post/320286/
All Articles