Caution: HSTS
About HSTS on Habré already wrote , this mechanism is included in the generator of configs for web servers from Mozilla. I decided to write this post in one day when I faced the inaccessibility of two large sites at once due to HSTS.
HSTS (HTTP Strict Transport Security) is a protection mechanism against downgrade attacks on TLS, which instructs the browser to always use TLS for sites with appropriate policies. The standard is described in RFC6797 , and there are two types of policies:
The policy is applied from the Strict-Transport-Security HTTP header when you first access the site via HTTPS, it specifies the expiration date and applicability to subdomains:
')
Static policies are hard-coded to the browser and for some sites include binding to a higher-level CA that issued a certificate (for example, google.com, paypal.com, or torproject.org). Moreover, it can act only when the site is opened via TLS, allowing an unprotected connection, but blocking MitM with a certificate substitution.
The list from Chromium is used by all popular browsers (Firefox, Safari and IE 11 + Edge) and anyone can add a website to it if the web server gives a Strict-Transport-Security header with a validity of two years and the preload keyword at the end:
Recently, colleagues complained about the inaccessibility of some sections of the site 1C (dist.1c.ru and partweb.1c.ru). Support assured that everything works, my problem did not reproduce, and even colleagues opened sites from all browsers except the main Chrome. He issued ERR_CONNECTION_TIMED_OUT 20 seconds later and for some reason persistently substituted HTTPS in the URL, even if the address was written entirely with HTTP.
The decision came almost immediately, as they recently mentioned HSTS in the context of corporate MitM. Google by keyword with the first link prompted what to see the cache policy in chrome: // net-internals / # hsts and the guess was confirmed:
The policy included all subdomains, although many of them were available only on port 80 without TLS.
After deleting it, the necessary sections began to open, according to the date of receipt (in the unix time format) in the browser history they found a page with incorrect settings and sent a bug report in 1C.
The second site was ask.mcdonalds.ru, which opened for the first time, but Chrome still showed a warning with the familiar four-letter abbreviation and without the familiar Proceed to (unsafe) button:
The error indicates that the certificate name is inconsistent, expires or is revoked, and the display of the button to open the site is expressly prohibited in the RFC. At the same time, the policy for mcdonalds.ru turned out to be static, which cannot be removed from chrome: // net-internals / # hsts.
You can bypass such a stub in Chrome by typing thisisunsafe (the previous magic word was badidea , and before it is danger ) or by launching a browser with the key --ignore-certificate-errors .
In Firefox, click “Forge About This Site” opposite the site in history, open about: config and create a new Integer with the name “test.currentTimeOffsetSeconds” and value 11491200, and then open the site in a new tab.
Do not include potentially dangerous functions without understanding the principles of their work. You will get the “A” rating in the test from SSL Labs without HSTS, and you can enable it after checking all the functionality via TLS. There will be no way back with a static sheet in the browser, therefore it is better to immediately purchase a certificate with a wildcard.
Chrome and Firefox support an additional protection mechanism: HTTP Public Key Pinning (HPKP) , which allows you to bind the certificate hash and send notification to the owner if the browser receives a certificate from a public CA for its domain with a different hash. He helped uncover several incidents with public CAs, but in practice it is used very rarely because of the high cost of the error.
The composition of hard-core policies in Chromium is interesting: in addition to the fast-food network, several Mail.ru and Yandex domains, there is only UniCredit from the TOP-15 Russian banks. There is no trendy TKS, neither Qiwi, nor WebMoney, and dynamic policies have been enabled only by Qiwi and for the addresses of Internet banks Binbank, IBC, Otkrytie, Raiffeisen and RSHB.
There is also no Telegram, but there is Whatsapp, and in the change log there are requests to delete (!) Mistakenly included sites, where for some time there was a preload in the header.
TL; DR
Check the site for TLS carefully before enabling HSTS, especially if it is a large portal with a bunch of subdomains and managed by different people.
What is HSTS?
HSTS (HTTP Strict Transport Security) is a protection mechanism against downgrade attacks on TLS, which instructs the browser to always use TLS for sites with appropriate policies. The standard is described in RFC6797 , and there are two types of policies:
Dynamic
The policy is applied from the Strict-Transport-Security HTTP header when you first access the site via HTTPS, it specifies the expiration date and applicability to subdomains:
')
Strict-Transport-Security: max-age=15768000; includeSubDomains; Static
Static policies are hard-coded to the browser and for some sites include binding to a higher-level CA that issued a certificate (for example, google.com, paypal.com, or torproject.org). Moreover, it can act only when the site is opened via TLS, allowing an unprotected connection, but blocking MitM with a certificate substitution.
The list from Chromium is used by all popular browsers (Firefox, Safari and IE 11 + Edge) and anyone can add a website to it if the web server gives a Strict-Transport-Security header with a validity of two years and the preload keyword at the end:
Strict-Transport-Security: max-age=63072000; includeSubDomains; preload How to shoot yourself in the leg?
Recently, colleagues complained about the inaccessibility of some sections of the site 1C (dist.1c.ru and partweb.1c.ru). Support assured that everything works, my problem did not reproduce, and even colleagues opened sites from all browsers except the main Chrome. He issued ERR_CONNECTION_TIMED_OUT 20 seconds later and for some reason persistently substituted HTTPS in the URL, even if the address was written entirely with HTTP.
The decision came almost immediately, as they recently mentioned HSTS in the context of corporate MitM. Google by keyword with the first link prompted what to see the cache policy in chrome: // net-internals / # hsts and the guess was confirmed:
dynamic_sts_domain: 1c.ru
Found :
static_sts_domain:
static_upgrade_mode: UNKNOWN
static_sts_include_subdomains:
static_sts_observed:
static_pkp_domain:
static_pkp_include_subdomains:
static_pkp_observed:
static_spki_hashes:
dynamic_sts_domain: 1c.ru
dynamic_upgrade_mode: STRICT
dynamic_sts_include_subdomains: true
dynamic_sts_observed: 1485244696.197302
dynamic_pkp_domain:
dynamic_pkp_include_subdomains:
dynamic_pkp_observed:
dynamic_spki_hashes:
static_sts_domain:
static_upgrade_mode: UNKNOWN
static_sts_include_subdomains:
static_sts_observed:
static_pkp_domain:
static_pkp_include_subdomains:
static_pkp_observed:
static_spki_hashes:
dynamic_sts_domain: 1c.ru
dynamic_upgrade_mode: STRICT
dynamic_sts_include_subdomains: true
dynamic_sts_observed: 1485244696.197302
dynamic_pkp_domain:
dynamic_pkp_include_subdomains:
dynamic_pkp_observed:
dynamic_spki_hashes:
The policy included all subdomains, although many of them were available only on port 80 without TLS.
After deleting it, the necessary sections began to open, according to the date of receipt (in the unix time format) in the browser history they found a page with incorrect settings and sent a bug report in 1C.
The second site was ask.mcdonalds.ru, which opened for the first time, but Chrome still showed a warning with the familiar four-letter abbreviation and without the familiar Proceed to (unsafe) button:
ER_CERT_COMMON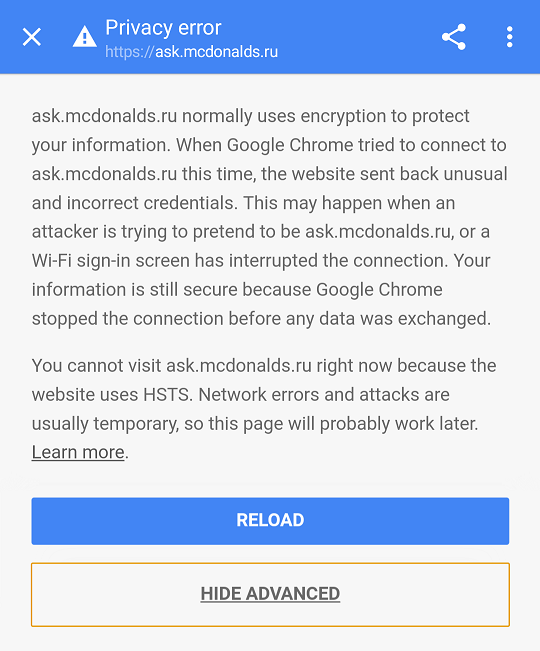

The error indicates that the certificate name is inconsistent, expires or is revoked, and the display of the button to open the site is expressly prohibited in the RFC. At the same time, the policy for mcdonalds.ru turned out to be static, which cannot be removed from chrome: // net-internals / # hsts.
You can bypass such a stub in Chrome by typing thisisunsafe (the previous magic word was badidea , and before it is danger ) or by launching a browser with the key --ignore-certificate-errors .
In Firefox, click “Forge About This Site” opposite the site in history, open about: config and create a new Integer with the name “test.currentTimeOffsetSeconds” and value 11491200, and then open the site in a new tab.
findings
Do not include potentially dangerous functions without understanding the principles of their work. You will get the “A” rating in the test from SSL Labs without HSTS, and you can enable it after checking all the functionality via TLS. There will be no way back with a static sheet in the browser, therefore it is better to immediately purchase a certificate with a wildcard.
PS
Chrome and Firefox support an additional protection mechanism: HTTP Public Key Pinning (HPKP) , which allows you to bind the certificate hash and send notification to the owner if the browser receives a certificate from a public CA for its domain with a different hash. He helped uncover several incidents with public CAs, but in practice it is used very rarely because of the high cost of the error.
Pps
The composition of hard-core policies in Chromium is interesting: in addition to the fast-food network, several Mail.ru and Yandex domains, there is only UniCredit from the TOP-15 Russian banks. There is no trendy TKS, neither Qiwi, nor WebMoney, and dynamic policies have been enabled only by Qiwi and for the addresses of Internet banks Binbank, IBC, Otkrytie, Raiffeisen and RSHB.
There is also no Telegram, but there is Whatsapp, and in the change log there are requests to delete (!) Mistakenly included sites, where for some time there was a preload in the header.
Source: https://habr.com/ru/post/320164/
All Articles