Site security by its headers, or what to do if you want to crawl into the insides of each site
Developers are trying to carefully treat their products, minifitsiruyut files, configure the cache, fighting for every millisecond speed. But for some reason, almost everywhere the fact that the very first is sent to the user, namely HTTP headers, is ignored. Somehow I happened to attend courses on information security, and there they were advised to look at them first, since they are often forgotten about them.

I, as alazy programmer who is paranoid every time I visit the site, is interested in information security, I decided to develop this idea. If you're interested, you are welcome.
The first thing I stumbled upon was a great application from the Mozilla developers , which analyzes Headers and many other things and gives a security rating to the site. Very good thing, and it helped me a lot, but it's not always convenient to use it.
')
And I decided to create my own application, which could analyze all the websites I visit on the fly, analyzing HTTP headers and rating it like a Mozilla website. I also wanted it to immediately determine if the server was using vulnerable technologies. And to cook skillfully. But the last feature was subsequently abandoned.
The code can be viewed on GitHub , I would like to thank the noomorph for the advice in JavaScript that is not my core profile. The extension itself is available at the link: HeaderView
To demonstrate the work, you can simply open the Habr, and if you use it shortly after the publication of the article, you will most likely see the following:
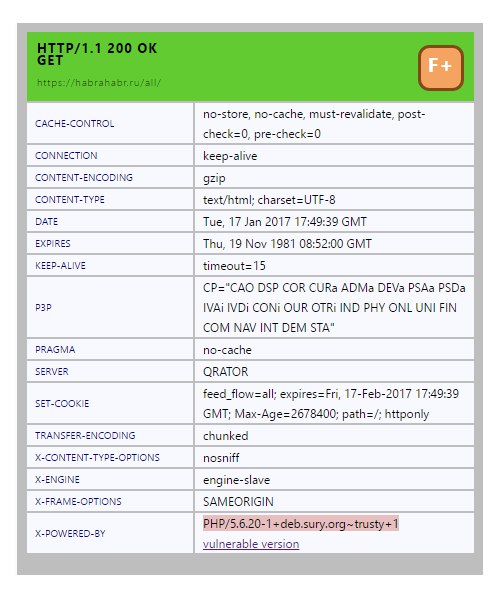
The F + site security rating, on the basis that A is the highest, and F the lowest. Habr has security headers, but at the same time, it shows in what language it works, and the version of this language is a little outdated (at the time of publishing the article, the current version of PHP 5.6.29 is according to official documentation . The extension automatically forms a link by which you can see the vulnerabilities version.
I chose Vulners as a search engine for vulnerabilities, because, firstly, I like it, and secondly, I don’t know others, and if you still have something to tell me, I’ll be happy.
Also, the extension is trying to analyze the server used, but in this case Habr does not show the version, and it is not possible to determine if it is vulnerable.
What is interesting, when switching from Geektimes to Habr, the redirect passes through another server, whose PHP version is slightly newer:
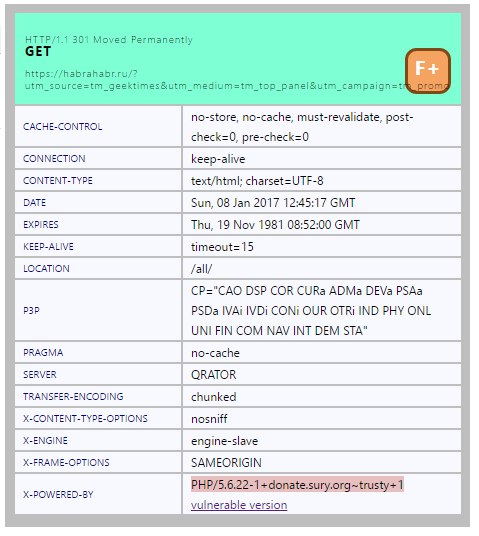
Although not enough.
Thus, I now browse all the sites where I leave personal information or make purchases.
If you have your own resource, it is worth seeing what you communicate to the world, and in a good way it is recommended not only to hide the language / server version, but also not to show what technologies you use. This, of course, does not help to protect against a targeted attack, but is a good tone rule.
I will be glad to tips and ideas what to add, as well as to expand the recognized technologies!

I, as a
The first thing I stumbled upon was a great application from the Mozilla developers , which analyzes Headers and many other things and gives a security rating to the site. Very good thing, and it helped me a lot, but it's not always convenient to use it.
')
And I decided to create my own application, which could analyze all the websites I visit on the fly, analyzing HTTP headers and rating it like a Mozilla website. I also wanted it to immediately determine if the server was using vulnerable technologies. And to cook skillfully. But the last feature was subsequently abandoned.
The code can be viewed on GitHub , I would like to thank the noomorph for the advice in JavaScript that is not my core profile. The extension itself is available at the link: HeaderView
To demonstrate the work, you can simply open the Habr, and if you use it shortly after the publication of the article, you will most likely see the following:

The F + site security rating, on the basis that A is the highest, and F the lowest. Habr has security headers, but at the same time, it shows in what language it works, and the version of this language is a little outdated (at the time of publishing the article, the current version of PHP 5.6.29 is according to official documentation . The extension automatically forms a link by which you can see the vulnerabilities version.
I chose Vulners as a search engine for vulnerabilities, because, firstly, I like it, and secondly, I don’t know others, and if you still have something to tell me, I’ll be happy.
Also, the extension is trying to analyze the server used, but in this case Habr does not show the version, and it is not possible to determine if it is vulnerable.
What is interesting, when switching from Geektimes to Habr, the redirect passes through another server, whose PHP version is slightly newer:

Although not enough.
Thus, I now browse all the sites where I leave personal information or make purchases.
If you have your own resource, it is worth seeing what you communicate to the world, and in a good way it is recommended not only to hide the language / server version, but also not to show what technologies you use. This, of course, does not help to protect against a targeted attack, but is a good tone rule.
I will be glad to tips and ideas what to add, as well as to expand the recognized technologies!
Source: https://habr.com/ru/post/319932/
All Articles