About consumers and types of Threat Intelligence
Every two to three years, a panacea for all ills appears in the “information-secure” world, which will protect both cybercriminals and cyber-activists from industrial espionage and APT attacks. All installed information security systems are declared obsolete and worthless, they are proposed to be urgently replaced. Naturally, not free. Queues are lined up for the miracle cure, there are not enough licenses for everyone. And then the seller wakes up.
A very similar situation is now developing with Threat Intelligence. It is very fashionable, driving, youth, but providers, users and buyers often understand by TI completely different things.

Let's try to figure out what kind of mysterious beast it is, where it so suddenly “jumped out”, why it is needed and who is interested in such intelligence, and whether it is possible to engage in intelligence with a glass of your favorite beer.
What is Threat Intelligence?
Threat Intelligence is regularly and systematically gathering information about threats, improving and enriching it, applying this knowledge to protect and sharing it with those to whom it can be useful. TI is not only a signature database for IDS or rule sets for SIEM. TIs are processes that have owners, goals, requirements, and a clear and measurable (as far as possible) result. TI I will understand precisely in this sense.
It is worth saying that until 2014 there was no threat intelligence. Well, that is, it was, of course, but this impression develops when you look at the topics of speeches of earlier RSA Conference.
And then the real TI boom began! In my list of companies and organizations that offer to purchase or exchange information about threats, intruders and malicious code, 126 lines. And that's not all. Three years ago, analysts of international research companies to the question about the size of the market TI answered: “Get away! There is no such market. There is nothing to consider. Now they (451 Research, MarketsandMarkets, IT-Harvest, IDC and Gartner) estimate this market at 1.5 billion dollars in 2018.
| Forecast | 2013 | 2014 | 2015 | 2016 | 2017 | 2018 | 2019 | 2020 | Annual growth,% |
|---|---|---|---|---|---|---|---|---|---|
| 451 Research | 1.0 | 3.3 | 34.0 | ||||||
| MarketsandMarkets | 3.0 | 5.86 | 14.3 | ||||||
| IT-Harvest | 0.25 | 0.46 | 1.5 | 80.0 | |||||
| IDC | 0.9 | 1.4 | 11.6 | ||||||
| Gartner | 0.25 | 1.5 | 43.1 |
Why is it beneficial to adapt TI processes?
Accelerates response to information security incidents
Thanks to the understanding of cybercriminals and their tools, tactics and procedures (TTP), hypotheses can be quickly proposed and tested. For example, if a response team member knows that certain malware samples (which the antivirus has just found) are aimed at compromising administrative accounts, this is a very strong argument for checking the logs and trying to find suspicious authorizations.
Helps prioritize
For example, the probability of exploitation of a specific detected vulnerability in a specific information system may be low, and the CVSS score is high (in CVSS v.3, the problem was fixed and a probability estimate was introduced). Therefore, it is important to take into account the accepted threat model, the state of the infrastructure and external factors.
In 2015, the SANS Institute conducted a survey of TI consumers from various industries, in which 329 respondents from North, Central and South America, Europe, the Middle East and Australia participated. According to this study, TI consumers record positive changes in several areas of ensuring information security after the implementation of TI processes.
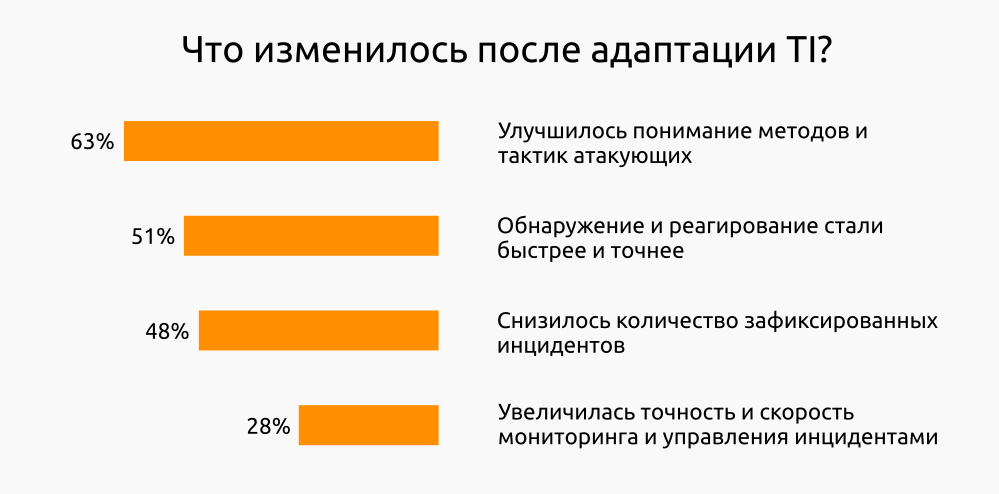
According to the same study, the forms of adaptation are very different.
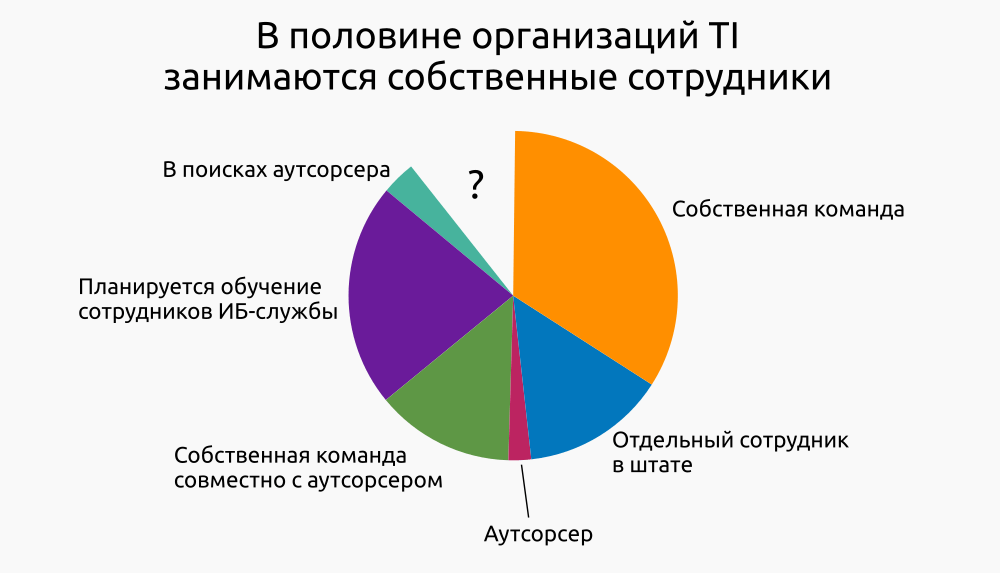
Only in 10% of cases in organizations there are no plans to develop cyber threat intelligence inside the company or such plans are not known.
Types of Threat Intelligence
Globally, there are two types of TI - strategic and tactical (or "technical" - as you like). They are very different in terms of results and methods of using these results.
| Sign of | Strategic TI | Technical TI |
|---|---|---|
| The form | Reports, publications, documents | Rule Sets Settings |
| Is created | By people | Cars or people with cars |
| Consume | People | Cars and people |
| Terms of delivery to the consumer | Days - Months | Seconds - watches |
| Period of utility | Long (a year or more) | Short (until new vulnerability or new exploitation method appears) |
| Assumptions | Hypotheses are possible, but they must be based on some data. | Unacceptable because machines do not understand fuzzy instructions |
| Focus | Planning, decision making | Detection, prioritization, response |
Threat Intelligence consumers
In order not to write a boring text wall, I gathered all the consumers in one table. Each cell indicates the groups of consumers and what results may be most interesting to them.
The same set of TI results may be interesting to different target groups. For example, "Tools, software and" glands "of the attackers" in the table are in the field "Techniques", but, of course, would be interesting and "Tactics".
| Management level | Operational level | |
|---|---|---|
| In the long run | STRATEGIES Top management (Board of Directors) High-level information on changing risks ')
| TECHNOLOGIES Architects and system administrators Tactics, techniques, procedures (TTP)
|
| In the short and long term | TACTICS Heads of information security services Details of specific upcoming and ongoing attacks
| OPERATORS Security officers, SOC staff (Monitoring Center), incident response team, forensics staff Indicators of attack and compromise
|
However, there is another side that is interested in receiving information from the organization - its partners. Often, attackers attack contractors or partners for their real purpose in the hope that their defense will be easier to overcome and gain access to information resources of the target from there. Therefore, it seems logical to organize the exchange of information about attacks and threats between partners.
Threat Intelligence Providers
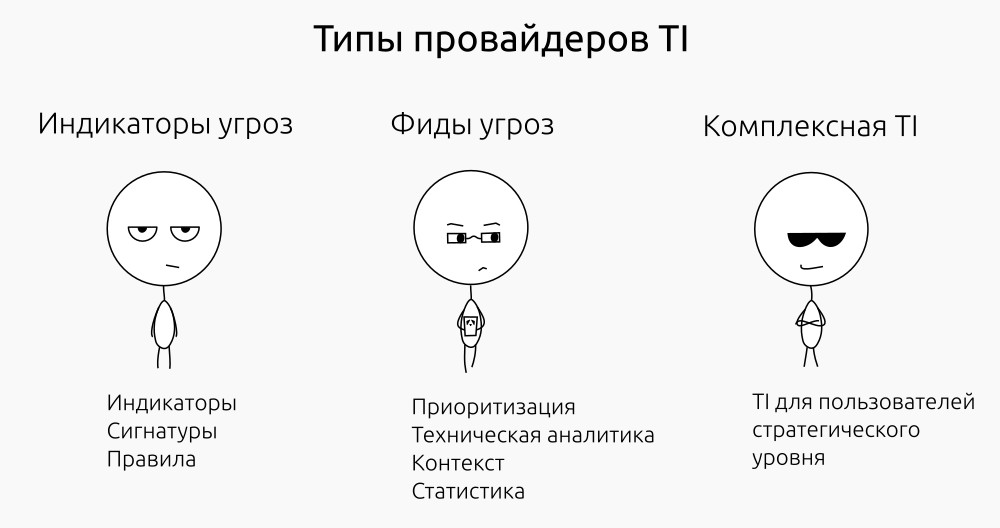
A large number of SZI-vendors and maintainers of open-source projects regularly supply indicators, signatures and attack detection rules for firewalls, antiviruses, IPS / IDS, UTM. In some cases it is raw data, in others it is supplemented with a risk or reputation assessment. Threat indicators are critical to the TI technical level, but often do not provide a context for responding to an incident.
Technology vendors and information security companies provide their threat feeds. They include proven and prioritized threat indicators and technical analysis of malicious code samples, information on botnets, DDoS attacks and other tools and types of malicious activity. Often these feeds are supplemented with statistics and forecasts: for example, “TOP-10 cryptographers” or “List of the largest botnets”, etc.
The main disadvantages of such feeds include the lack of sectoral or regional specificity and low value for TI users of a strategic level.
A small number of companies provide a truly comprehensive TI: proven, consumer-relevant threat indicators, threat feeds and strategic TIs. These usually include:
- Proven and marked (tagged) threat indicators.
- Detailed technical analysis of attack tools.
- Deep research of the enemy, supplemented by information on the "underground" sites and from private sources.
- Assessment of the threat landscape for the industry and individual enterprise.
- Assistance in developing requirements for TI.
- TI, specially prepared for users of different levels within the same organization.
Enjoyment is the main sign of friendship
So said Aristotle. And for safeguards, communication is a way to combine efforts to counter attackers. There is even a more or less well-established English-language term - “beer intelligence”. This is when security guards gather and share their findings and suspicions with each other in an informal setting. So yes, you can explore and have a glass of beer too.
The fourth principle from the definition of TI is “to share them with those to whom they can be useful” is about the exchange of information. And it can be organized not only according to the B2B scheme (bezopasnik-bezopasnik), but also with the help of a trusted third party (organization) that collects, verifies, de-identifies and sends information about threats to all members of the community. Such communities are supported by government or public organizations (for example, CiSP), volunteers (Vulners) and commercial companies (AlienVault Open Threat Exchange).
So is it worth implementing threat intelligence processes in your organization? It is worth it, but only if you know: 1) where to apply and how to evaluate the results of TI; 2) how TI helps IS processes; 3) who will answer the questions posed to the "intelligence officers", and can formulate requirements for TI.
Source: https://habr.com/ru/post/319666/
All Articles