7 useful tips on protecting backups from encryption viruses
Today we talk about the problem of virus encryption (ransomware). These programs are designed to pull money from the owners of infected computers, so they are also called “extortionists”.
The problem of encryption viruses affects not only individual personal computers, but reaches the level of data centers. For attacks on the infrastructure of companies apply, for example, Locky, TeslaCrypt and CryptoLocker. Often, viruses exploit the vulnerabilities of web browsers or their plug-ins, as well as proactively open e-mail attachments. Having penetrated into the infrastructure, the extortionist program starts fast distribution and data encryption.
An important component of the data protection strategy has always been the availability of backup copies from which you can perform recovery. Let us consider several recommendations from my colleague Rick Vanover on how to protect the storage of backups from encryptors (regardless of whether you use Veeam solutions or other vendors). So, welcome under cat.
')
This universal recommendation is especially relevant in the era of Trojan-cryptographers.
There are options when the Veeam infrastructure is not included in the domain (as a rule, in small organizations) or enters a domain that is organized specifically for the operation of backup and data protection tools (in larger environments). In any case, it is important to pay attention to authentication and careful separation of the working environment and backup infrastructure.
A very effective way to protect yourself from the penetration of a crypto Trojan is to save backup copies offline (that is, outside the running infrastructure). For example, if you are using Veeam solution, then you can consider the following options:
If you use a dedicated storage system only for storing backups, then usually such storage is used only during the backup window (for example, only at night). In this case, a separate, simple way to transfer a backup to offline will be to set the schedule for automatic powering off / on for the period of time when it is not required.
Alert the distribution of cryptographers using different file protocols. For example, if you keep a repository on Linux, then in this case, when backing up and restoring with Veeam, Linux authentication will be used, and the file system can be either ext3 or ext4 (or another). This way you can additionally protect your backups. Here are some examples of backup storage systems with this approach:
With these options, access to the storage system from the side of Veeam processes will occur within a specific security context.
Hardware snapshots are, so to speak, a “semi-offline” way of storing data in the case of working with the main storage system. If it is possible to create hardware snapshots for storage backup, then it is quite reasonable to use it to prevent encryption attacks.
As you remember, there is a rule “3-2-1” , which requires to store 3 backup copies at least on two types of media, and to keep one of these copies on the backup site (and not at the location of the production infrastructure).

This simple rule will help you in almost any emergency situation in which you need to recover data, and at the same time it does not require the use of any specific technology. In the era of cryptographers, it would be wise to add another one to this rule, implying that one of the carriers should be stored offline. The above options (see clause 2) will help you with the choice of media and storage method, which, in turn, will strengthen your infrastructure in opposition to cryptographers.
One of the threats that cryptographers carry with them is the potential for distribution to other systems. Therefore, it is important to monitor the operation of equipment, processes and applications in order to detect suspicious activity. So, Veeam ONE 9.5 brings to your attention a new built-in alert Possible Possible ransomware activity (the probable activity of the cipher operator). It works if an increased activity is observed in the use of the CPU and an increase in the number of write operations to the disk.
In order to get a recovery point stored on a remote storage system and having its own storage policy (different from the one specified in the backup settings), it is convenient to use the Backup Copy Job transfer job. This task takes data from the backup repository and, on their basis, creates restore points on the remote storage system. For example, if you added another storage system to the backup infrastructure (for example, Linux), then you can create an appropriate repository and then configure the transfer task to work with it.
In conclusion, we can say that there are quite a few methods to combat trojans, the "cryptographer", which allows you to keep your backups intact, and in this post only a part of them was listed. If you have personal experience or constructive ideas on this subject, forgive us in the comments.
Article on Habré about rule 3-2-1 for backup:
→ Part 1
→ Part 2
→ Webinar on the integration of Veeam and HPE StoreOnce (in Russian)
→ The Veeam Knowledge Base Article on EMC Data Domain Integration (in English)
The problem of encryption viruses affects not only individual personal computers, but reaches the level of data centers. For attacks on the infrastructure of companies apply, for example, Locky, TeslaCrypt and CryptoLocker. Often, viruses exploit the vulnerabilities of web browsers or their plug-ins, as well as proactively open e-mail attachments. Having penetrated into the infrastructure, the extortionist program starts fast distribution and data encryption.
An important component of the data protection strategy has always been the availability of backup copies from which you can perform recovery. Let us consider several recommendations from my colleague Rick Vanover on how to protect the storage of backups from encryptors (regardless of whether you use Veeam solutions or other vendors). So, welcome under cat.
')

1. Use a separate account to access the backup storage.
This universal recommendation is especially relevant in the era of Trojan-cryptographers.
- It is reasonable to use dedicated accounts for accessing the backup repository.
- You should avoid assigning access rights to the repository for all sorts of users, except for those who need them to perform backup.
- And, of course, you should not use the domain administrator’s account everywhere.
There are options when the Veeam infrastructure is not included in the domain (as a rule, in small organizations) or enters a domain that is organized specifically for the operation of backup and data protection tools (in larger environments). In any case, it is important to pay attention to authentication and careful separation of the working environment and backup infrastructure.
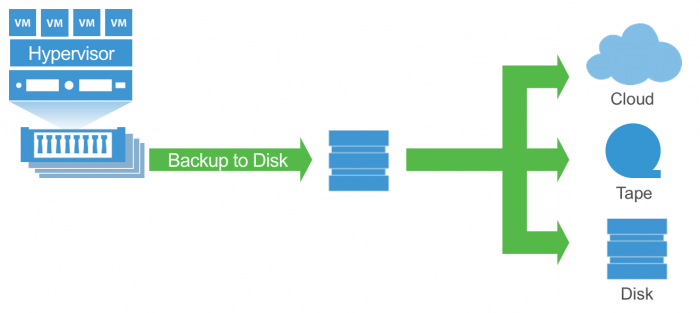
2. Keep backups stored offline (without connecting to the infrastructure)
A very effective way to protect yourself from the penetration of a crypto Trojan is to save backup copies offline (that is, outside the running infrastructure). For example, if you are using Veeam solution, then you can consider the following options:
| Where to store data | Explanation |
|---|---|
| Magnetic tape | Always offline (unless in the process of reading and writing). |
| VM replica | Normally off; in most cases, it will be used in an environment with authentication separate from production (for example, vSphere and Hyper-V hosts in different domains). |
| Hardware snapshots of production storage systems | Can be used for recovery; usually used in an authentication environment separate from production. |
| Cloud Connect backups | Do not connect directly to the backup infrastructure; use a different authentication mechanism. |
| Removable media (for example, external hard drive) | Always offline (unless in the process of reading and writing). |
If you use a dedicated storage system only for storing backups, then usually such storage is used only during the backup window (for example, only at night). In this case, a separate, simple way to transfer a backup to offline will be to set the schedule for automatic powering off / on for the period of time when it is not required.
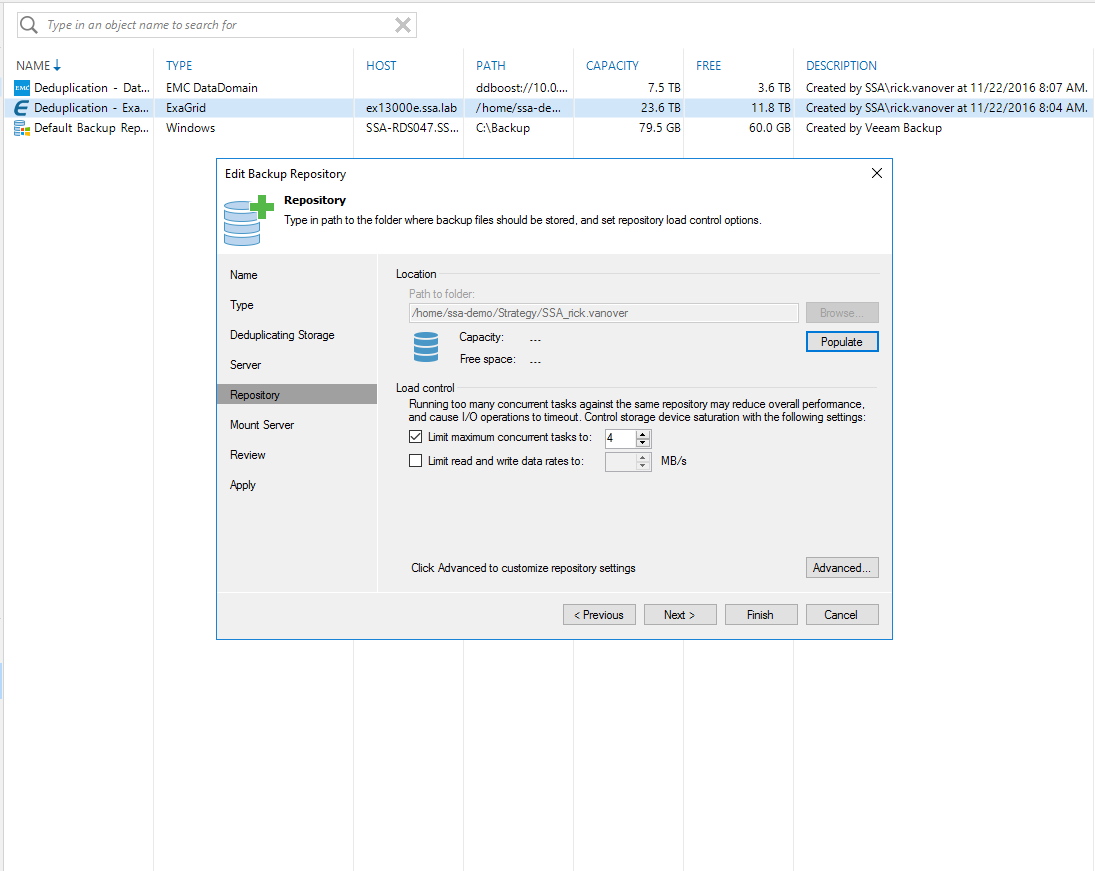
3. Use to store storage backups with different file systems.
Alert the distribution of cryptographers using different file protocols. For example, if you keep a repository on Linux, then in this case, when backing up and restoring with Veeam, Linux authentication will be used, and the file system can be either ext3 or ext4 (or another). This way you can additionally protect your backups. Here are some examples of backup storage systems with this approach:
- Data Domain storage with built-in deduplication and using DDBoost (recommended method) or with NFS mounting in case DDBoost is not used
- Hewlett Packard Enterprise (HPE) StoreOnce storage with built-in deduplication and using Catalyst
- ExaGrid with built-in deduplication and using the Veeam agent
With these options, access to the storage system from the side of Veeam processes will occur within a specific security context.

4. If possible, create hardware snapshots of backup copies
Hardware snapshots are, so to speak, a “semi-offline” way of storing data in the case of working with the main storage system. If it is possible to create hardware snapshots for storage backup, then it is quite reasonable to use it to prevent encryption attacks.
5. Apply the rule "3-2-1-1"
As you remember, there is a rule “3-2-1” , which requires to store 3 backup copies at least on two types of media, and to keep one of these copies on the backup site (and not at the location of the production infrastructure).

This simple rule will help you in almost any emergency situation in which you need to recover data, and at the same time it does not require the use of any specific technology. In the era of cryptographers, it would be wise to add another one to this rule, implying that one of the carriers should be stored offline. The above options (see clause 2) will help you with the choice of media and storage method, which, in turn, will strengthen your infrastructure in opposition to cryptographers.
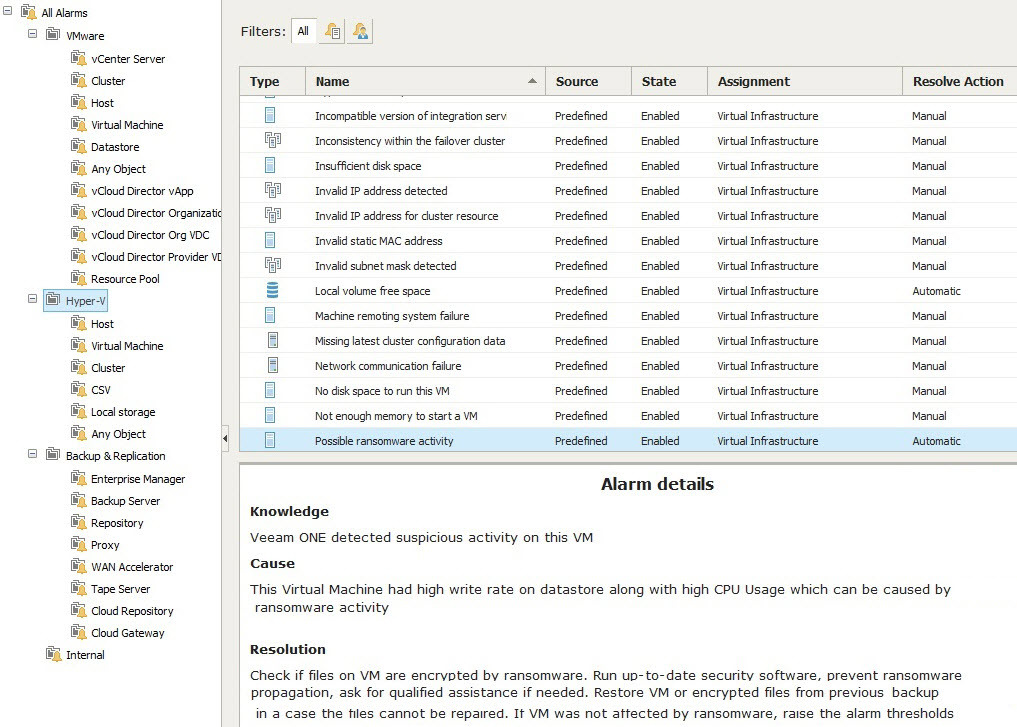
6. Control equipment and software
One of the threats that cryptographers carry with them is the potential for distribution to other systems. Therefore, it is important to monitor the operation of equipment, processes and applications in order to detect suspicious activity. So, Veeam ONE 9.5 brings to your attention a new built-in alert Possible Possible ransomware activity (the probable activity of the cipher operator). It works if an increased activity is observed in the use of the CPU and an increase in the number of write operations to the disk.

7. Enable Backup Backup Job Migration Jobs
In order to get a recovery point stored on a remote storage system and having its own storage policy (different from the one specified in the backup settings), it is convenient to use the Backup Copy Job transfer job. This task takes data from the backup repository and, on their basis, creates restore points on the remote storage system. For example, if you added another storage system to the backup infrastructure (for example, Linux), then you can create an appropriate repository and then configure the transfer task to work with it.
In conclusion, we can say that there are quite a few methods to combat trojans, the "cryptographer", which allows you to keep your backups intact, and in this post only a part of them was listed. If you have personal experience or constructive ideas on this subject, forgive us in the comments.
What else to read and see
Article on Habré about rule 3-2-1 for backup:
→ Part 1
→ Part 2
→ Webinar on the integration of Veeam and HPE StoreOnce (in Russian)
→ The Veeam Knowledge Base Article on EMC Data Domain Integration (in English)
Source: https://habr.com/ru/post/319654/
All Articles