Google launches Key Transparency, a tool for verifying crypto keys
Reliable cryptography is the basis of the modern Internet. Without cryptography, there is no secure connection, the possibility of making secure transactions on the Internet is lost. We can not trust even the interlocutor, if not established a secure connection.
According to Google , there is a serious flaw in the current public cryptography infrastructure. The fact is that if the server is compromised with the keys, users have to manually check the keys with the interlocutor. This is extremely inconvenient and does not work in practice. Because of such difficulties, some cryptographic enthusiasts completely abandon PGP - and they can be fully understood.
')
Google has come up with a solution: it offers everyone to use the Key Transparency transparent key finder.
What is the problem?
The problem is that the PGP trust network for encrypting email was created over 20 years ago, and many users are still unable or unwilling to use it.
The problem was well described by cryptographic specialist Filippo Valsord in his article “ I refused PGP ”:
I have never, never, used the trust network for validating a public key. And remember, I have a well-connected key. I did not conduct a formal study, but I’m pretty sure that everyone who used PGP to communicate with me did or could do (if asked) one of the following things:
- pulled the most liked key from the key server, most likely not even via TLS;
- uses another key if he responds with the words "this is my new key";
- Forward a letter in clear text, if you ask him to excuse like "I'm on a trip."
Trips and travels are especially hostile to long-term keys, making this type of start impossible from scratch .
Moreover, I am not even sure that there is an intruder against whom long-term keys make sense. Your usual average enemy will probably not be able to conduct a MitM attack on private messages on Twitter (this means that you can opportunistically use personal messages to exchange fingerprints of public keys, while still maintaining privacy). Mossad will do the Mossad stuff with your car, no matter what key you use.
After all, in our time I care more about outright secrecy, the possibility of refusal and ephemerality than about unbreakable trust. Are you sure you can protect a durable key forever? Because when an attacker decides to make you his target and succeeds, he will have access not only to all your messages from now on, but to all past messages too.
Surely many will agree with this opinion.
What can I say, if the author of PGP does not use PGP .
Messengers , file sharing programs and software update delivery systems suffer from the same key exchange problem.
Google’s Security and Privacy Engineering, Ryan Hurst and Gary Belvin, write in the official blog that one of the tasks of the Key Transparency system developed is to make the system easier. Create an infrastructure that will allow even non-experts reliably use cryptographic tools.
The idea is that the connection between the person’s online identifier and his public keys should be automatically verified and made available for public scrutiny. The user must see all the keys associated with a specific account, and any attempt to substitute information by a third party - a hacker or government agencies - should be immediately visible. This infrastructure at the same time ensures that the sender always uses the same public keys of the recipient that are verified and linked to his account to encrypt the message.
Key Transparency
“Key Transparency is a transparent, publicly accessible directory that will allow developers to easily create systems of any kind with independently verifiable account data,” write Ryan Hirst and Gary Belvin. - It can be used in various scenarios where data needs to be encrypted or authenticated. It can be used to develop user-friendly security features, while at the same time supporting important user needs like account recovery. ”
According to the authors, when developing Key Transparency, they combined the properties of Certificate Transparency and CONIKS .
Google Certificate Transparency is an open framework for monitoring and auditing SSL certificates in near real time. If the certificate authority has mistakenly or deliberately issued new SSL certificates, then they will be quickly detected by Certificate Transparency. The system also determines if the certification authority issues fake certificates.
On the other hand, CONIKS is a key management system for end users, so that they can maintain secure end-to-end encryption channels even if there is no trust in the provider or server. That is, CONIKS stores user encryption keys in such a way that they are available for verification, and any replacement of keys is instantly fixed.
Google's Key Transparency combines Certificate Transparency and CONIKS. Or you can say that this is a proprietary version of CONIKS from Google, modeled on Certificate Transparency.
In more detail, the properties of the Key Transparency system are described on this page . If we describe the principle in two words, then two people should get the same result when they request the same public key for the same account at the same time. This means that in this case there is no third party intervention that replaces this account for one of the users (Man in the Middle).
Google implemented an automatic check of this kind in the Key Transparency system, creating a Merkle tree, which calculates a single hash for the entire database with user accounts and their public keys, and the resulting hash is distributed between users.
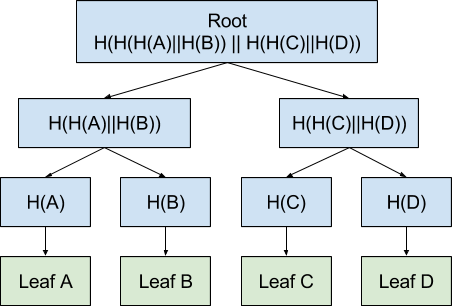
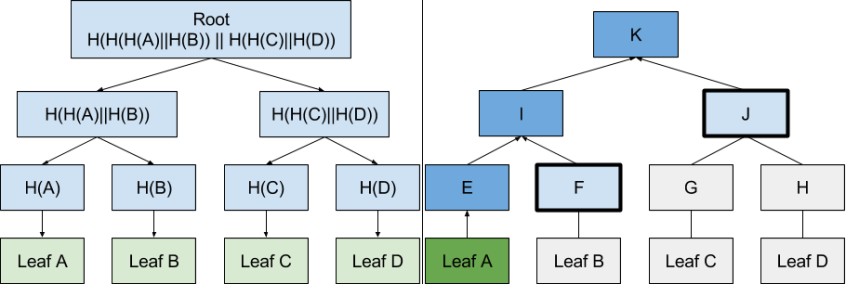
The structure of the hash is thought out for efficient practical use of the information contained in the hash. Applications can quickly verify that certain results are part of a hash. This is shown in the illustration below.
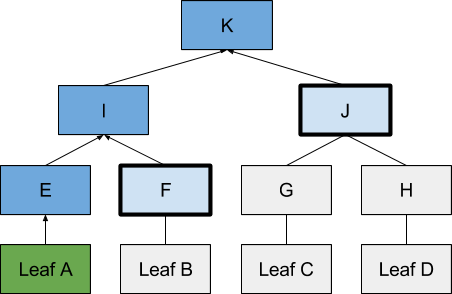
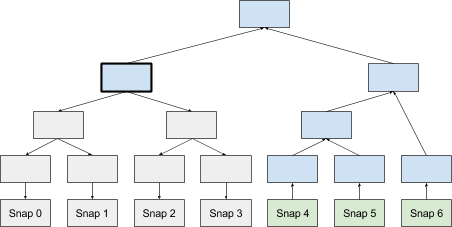
The merkle tree hash proves that sheet A is part of hash K. Verification is done by hashing sheet A and combining the resulting hash E with intermediate nodes F and J to calculate K
As shown in the diagrams, everything works quite simply - and effectively at the same time. For each user there is a leaf in the Merkle tree: the nodes are numbered from 0 to 2,256 −1.
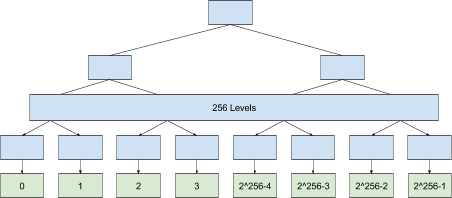
Thus, when a user verifies the identity of the recipient before sending a message, using the Key Transparency system, he can be sure that the recipient’s public keys right now correspond to his account.
Google proposes to implement to the application developers the following messages to automatically discover new keys:
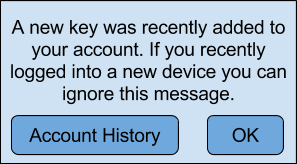
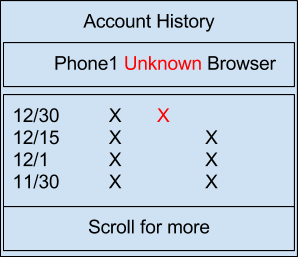
To update the database, a new Merkle tree is built every few seconds and a new hash is calculated.
To eliminate the substitution of data in Key Transparency, all old photographs of the Merkle trees replenish the new Merkle tree with the same structure as the regular Merkle tree in the Certificate Transparency system. The tree is filled from left to right, so that its structure contains evidence that each new version is a modified state of the previous version.
In the repository on Github published instructions for installing and using the Key Transparency client and launching the Key Transparency cluster.
Source: https://habr.com/ru/post/319470/
All Articles