Information security on mobile devices - consumer view
Mobile devices are rapidly becoming the main way of our interaction with the outside world - the ability to constantly stay in touch is an integral part of our life today, our phones and all kinds of wearable devices expand our capabilities when purchasing products, receiving banking services, entertainment, video recording and photographing important moments of our life and, of course, the possibility of communication.
At the same time, thanks to mobile devices and applications, brands gained a fundamentally new way to make themselves known, and this in turn led to phenomenal levels of growth in mobile technology over the past decade. Unfortunately, the rapid increase in mobile technology penetration leads to increased opportunities for cybercriminals.

Today, mobile devices offer users more and more valuable services that require careful attention to security (including, for example, mobile banking, payments, and mobile identifiers). Accordingly, hackers are well aware that by organizing a leak of authentication data through a mobile device, they will be able to gain unauthorized access to online resources of high value. In particular, hackers will try to gain access to financial information, credentials for access to social networks, to contract data in mobile networks. One way or another, sometimes this may be enough to fully implement the identity theft. This threat is becoming especially relevant now, when we are seeing an increase in the number of new mobile applications - according to a study by the Application Resource Center (Applause), 90% of companies intend to increase their investment in mobile application development by the end of this year.
')
There is an undeniable need to protect corporate resources right now, including the intellectual property of companies and personal data of users, especially given the large number of devices in use today that can run malicious code. If we do not pay enough attention to this, then in fact we leave the end users and, in particular, the companies in the center of attention of the attackers, who have more and more resources at their disposal today and who are increasingly using the latest technologies in their work. They are experts in spreading malicious software, they deliberately use unofficial application repositories, embed malicious code in emails, send malicious SMS and infect browsers, and they are ready to take advantage of any weakness or vulnerability. That is why application vendors should carefully consider such threats and take all necessary measures to help consumers feel safe by offering solutions that provide reliable protection against these vulnerabilities.
But how do we understand exactly what security technology is needed in a particular case? How do we understand what is most in demand among end users, and what constitutes the greatest threat to them? How do we know which security solutions they will use? What exactly will be most convenient for them? All these are important questions that require answers, which is why we decided to conduct a survey by interviewing more than 1,300 smartphone users from the adult population in the six largest markets in the world: in Brazil, the United Kingdom, South Africa, Singapore, the Netherlands and the USA.
We asked consumers to talk about how they use their mobile devices and share their security expectations. We wanted to find out how consumer experiences will affect those who develop applications and infrastructure for mobile applications and services, namely, banks, government agencies, and any large enterprises that create applications for users. The results of this study allowed us to gain a deeper understanding of what exactly the users need to ensure information security of the future mobile revolution.

After the survey, we summarized and analyzed the data, collecting the results into a report. 66% of respondents say that they would commit more transactions if they knew for sure that their mobile devices pay due attention to security issues, to such an extent that as many as 70% of end users are not against having digital ID cards on their smartphones, but only with provided that all applications on their phones are fully protected from hacker attacks and vulnerabilities.
Other interesting survey results:
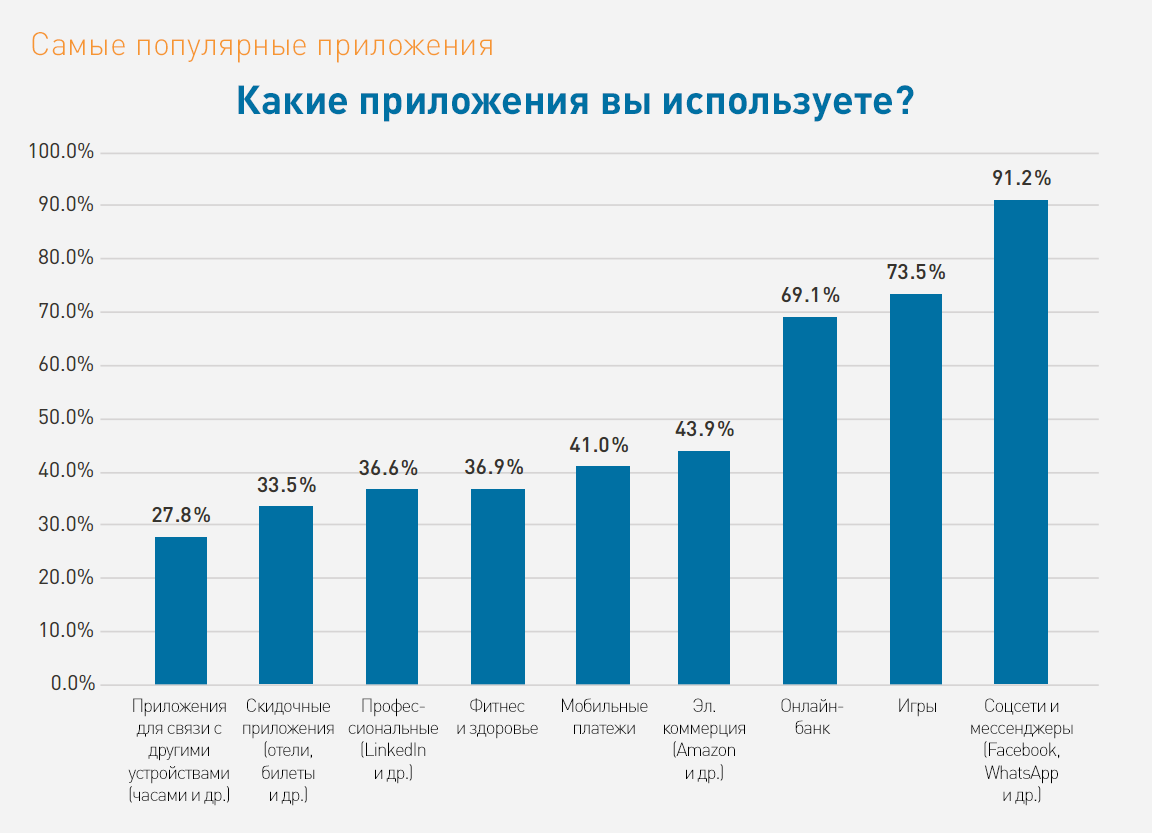

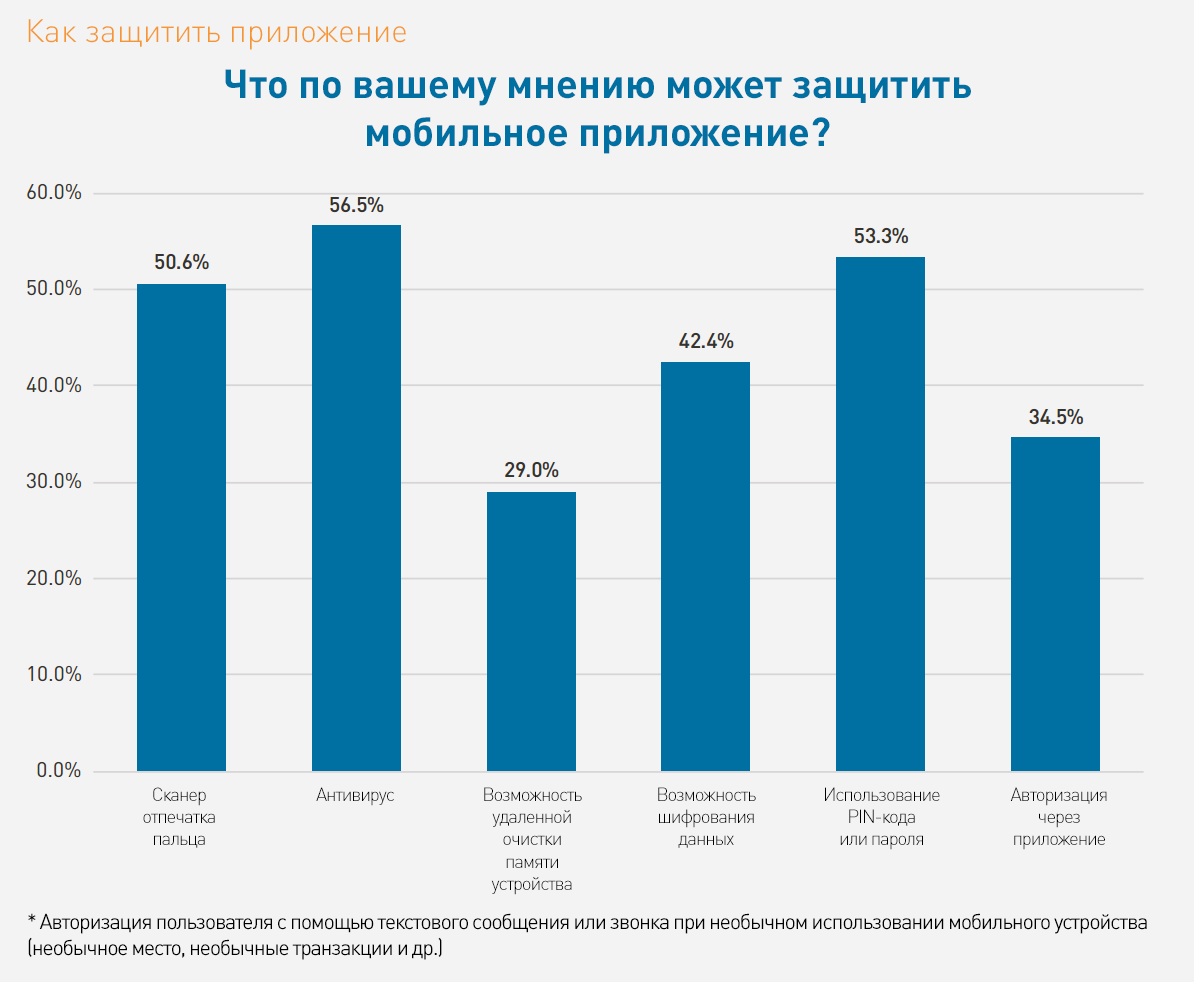
How to protect against threats?
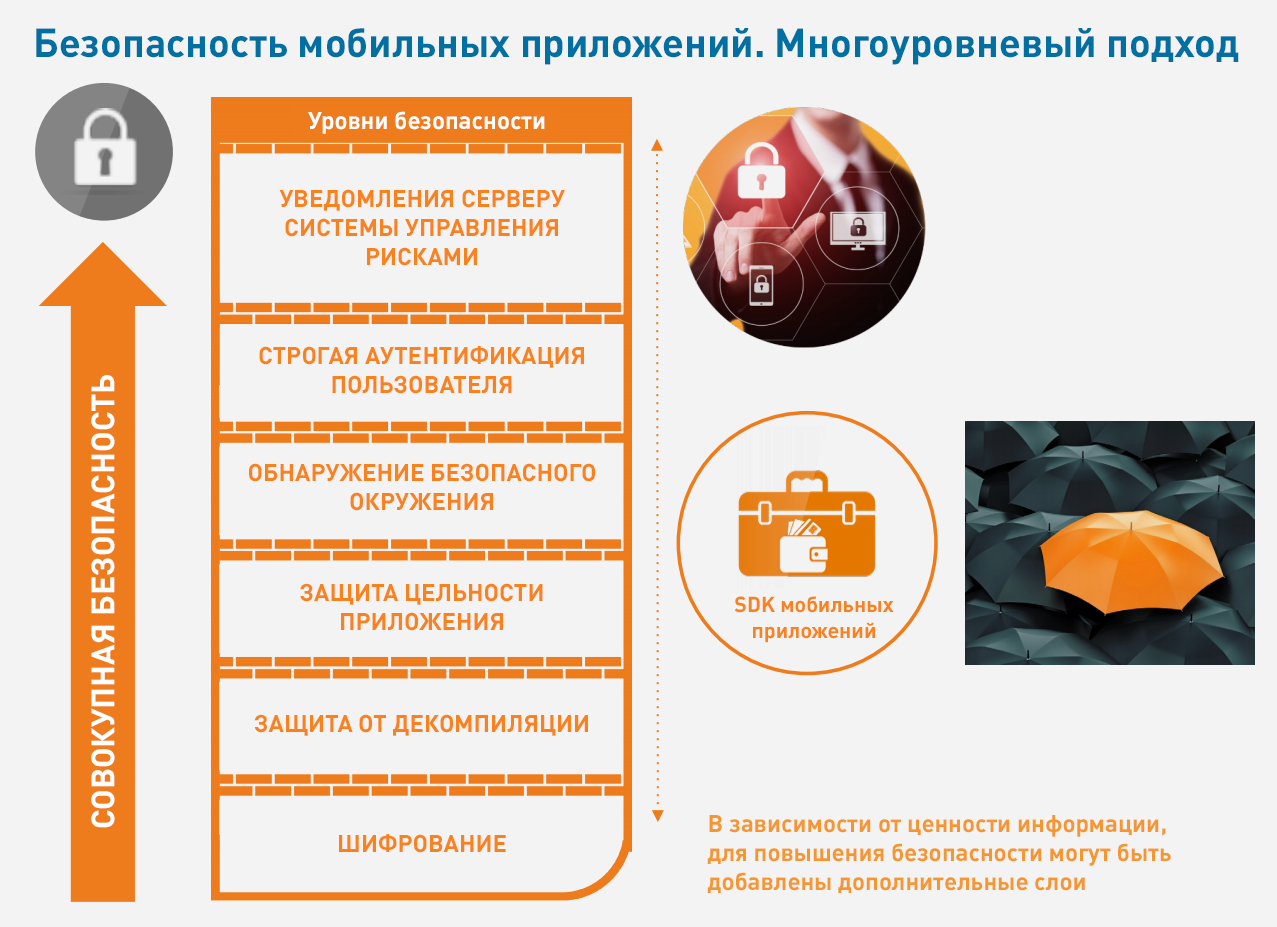
Obviously, the growth potential has not yet been exhausted. The only question is to ensure security for those who are ready to expand the scope of their smartphones. Our study with answers to the question of how this can be achieved, and recommendations for achieving consumer confidence is available here (eng.)
At the same time, thanks to mobile devices and applications, brands gained a fundamentally new way to make themselves known, and this in turn led to phenomenal levels of growth in mobile technology over the past decade. Unfortunately, the rapid increase in mobile technology penetration leads to increased opportunities for cybercriminals.

Today, mobile devices offer users more and more valuable services that require careful attention to security (including, for example, mobile banking, payments, and mobile identifiers). Accordingly, hackers are well aware that by organizing a leak of authentication data through a mobile device, they will be able to gain unauthorized access to online resources of high value. In particular, hackers will try to gain access to financial information, credentials for access to social networks, to contract data in mobile networks. One way or another, sometimes this may be enough to fully implement the identity theft. This threat is becoming especially relevant now, when we are seeing an increase in the number of new mobile applications - according to a study by the Application Resource Center (Applause), 90% of companies intend to increase their investment in mobile application development by the end of this year.
')
There is an undeniable need to protect corporate resources right now, including the intellectual property of companies and personal data of users, especially given the large number of devices in use today that can run malicious code. If we do not pay enough attention to this, then in fact we leave the end users and, in particular, the companies in the center of attention of the attackers, who have more and more resources at their disposal today and who are increasingly using the latest technologies in their work. They are experts in spreading malicious software, they deliberately use unofficial application repositories, embed malicious code in emails, send malicious SMS and infect browsers, and they are ready to take advantage of any weakness or vulnerability. That is why application vendors should carefully consider such threats and take all necessary measures to help consumers feel safe by offering solutions that provide reliable protection against these vulnerabilities.
But how do we understand exactly what security technology is needed in a particular case? How do we understand what is most in demand among end users, and what constitutes the greatest threat to them? How do we know which security solutions they will use? What exactly will be most convenient for them? All these are important questions that require answers, which is why we decided to conduct a survey by interviewing more than 1,300 smartphone users from the adult population in the six largest markets in the world: in Brazil, the United Kingdom, South Africa, Singapore, the Netherlands and the USA.
We asked consumers to talk about how they use their mobile devices and share their security expectations. We wanted to find out how consumer experiences will affect those who develop applications and infrastructure for mobile applications and services, namely, banks, government agencies, and any large enterprises that create applications for users. The results of this study allowed us to gain a deeper understanding of what exactly the users need to ensure information security of the future mobile revolution.

After the survey, we summarized and analyzed the data, collecting the results into a report. 66% of respondents say that they would commit more transactions if they knew for sure that their mobile devices pay due attention to security issues, to such an extent that as many as 70% of end users are not against having digital ID cards on their smartphones, but only with provided that all applications on their phones are fully protected from hacker attacks and vulnerabilities.
Other interesting survey results:



How to protect against threats?

Obviously, the growth potential has not yet been exhausted. The only question is to ensure security for those who are ready to expand the scope of their smartphones. Our study with answers to the question of how this can be achieved, and recommendations for achieving consumer confidence is available here (eng.)
Source: https://habr.com/ru/post/319366/
All Articles