BLE under the microscope

BLE under the microscope. Part 1
part 2 , part 3In the world there is a wide variety of ways to transmit information "over the air." Recently, the BLE format has become increasingly popular. Today we will look at the features of this protocol and talk about why it is so in demand in the modern world. We also consider the development tools and features of the work of auxiliary applications on windows, android from the company Nordic.
Why came up with BLE
As soon as people learned to transmit information without the aid of wires, the problem of data transmission arose using a battery-powered device. The problem is that he should be helped by another device that will constantly either listen to the broadcast or transmit data. The problem arises if both the receiver and the transmitter are battery powered. In this case, BlueTooth Low Energy (BLE) comes to the rescue. He first entered into the protocol BlueTooth 4.0. At the moment, the BlueTooth 5.0 specification has already been released, but we will mainly consider the BlueTooth 4.0 format, sometimes specifying innovations for the 5.0 format. As one of the devices is usually a smartphone, and the second - the battery gadget. Android supports BLE from version 4.3.
For data transmission and reception, energy is needed, so they increase the data transfer rate in order to be able to transmit more information per unit of time. For this purpose, the information transfer rate in BLE is 1 Mbit / c. However, not only data transfer speed is important. The most important thing in BLE is that communication devices are able to go into synchronous operation. In other words, the devices sleep 99% of the time, then wake up for a very short time, exchange information and fall asleep again. However, before entering this mode, you must go through the synchronization procedure. For this there is a mode of "advertising". We will look at it later. And before plunging into the BLE protocol description, I would like to touch upon the topic of tools for working with the BLE protocol.
Instruments
In order to understand the diversity of packages and requests, we need tools. With their help, we could see the contents of the packages and control the mechanism of interaction between devices. For these purposes, we will use the nRF51822 Development Dongle (PCA10000), a sniffer program and, to display the results, the Wireshark program, which is well known to all sysadmins.
')

Programs are free, but getting yourself a dongle can be a problem. However, without the tools, it will be very problematic to develop such complex devices. At the first stage, the program on the android “nRF Connect” can help.
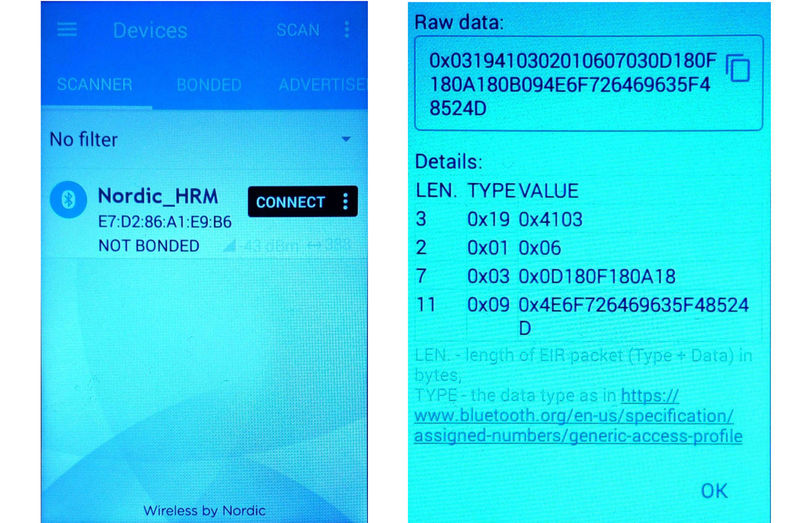
It allows you to scan the air, find and parse the parcels of both attachable and non-attachable devices. Nordic has more tools for developing BLE devices, but these will be enough for us. At the Russian market there is a representative of the company Nordic - the firm “Rutronik” (rutronik24.com, rutronik.com). Through its representatives, you can purchase the necessary chips, debug boards, etc. In addition, there is a forum on the Internet in which representatives of the firm answer the questions of developers.
First, let's talk briefly about how to use our tools. Insert our dongle into the USB connector and launch the ble_sniffer_win program. We will see the next window.
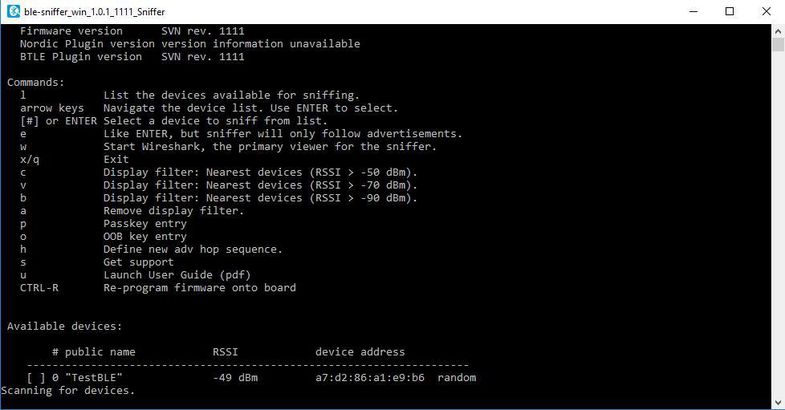
If the dongle sees the BLE device, then information about them will appear below. In this case, there is one device on the air with the name "TestBLE". Its signal level, MAC address and the fact that this address is random is also displayed. Looking ahead, I would like to note that here lies one of the pitfalls for developers. Some phones (LG G3S, Samsung S6) work only with devices whose MAC addresses are registered (public).
The sniffer has two modes of operation. If we press the “w” button on the keyboard, the “Wireshark” program will start. The sniffer will scan three ad channels and display information about all ad devices. If we first press the number on the keyboard, the same as in front of the device of interest to us, then another mode of operation will turn on. In it, the sniffer will monitor the traffic of only one selected device, both on the ad channels and on the working channels.

Using Wireshark, it is easy to get all the information about the package. The program consists of three windows. All received parcels are displayed at the top, detailed information about the selected package is displayed in the second window, and the frame itself is displayed in the third window. In turn, in the second window there are three blocks of information. At the top - the time values of the selected frame, in the second (Nordic BLE sniffer meta) - general information about the frame, such as signal level, frequency channel and some others. The most interesting for us is the third block of information (Bluetooth Low Energy Link Layer). In it you can see the analysis of the frame itself. In the future we will talk about this block of information. First, we analyze the formation of advertising packages.
Advertising
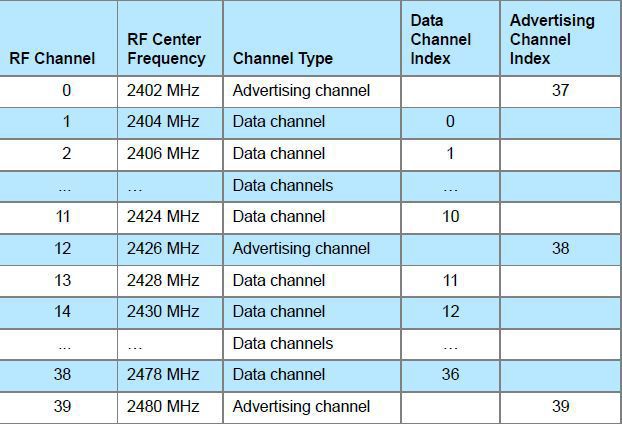
Let's look at the picture below. It shows the frequency distribution of channels for BLE. Advertising channels are 37 (2402 MHz), 38 (2426 MHz) and 39 (2480 MHz) channels. This distribution of advertising channels was not chosen randomly. First, advertising channels fall between Wi-Fi channels (1, 6, 11 channels), which allows even with a low power level to be heard by other devices. Secondly, when we distribute advertising channels far from each other, we receive guaranteed message delivery. This is due to the interference of the signal in the premises. It is known that as a result of reflection of radio signals from the walls, a situation may occur when the receiver and transmitter do not hear each other. However, in our case, when the transmission of advertizing packages goes consistently on three different channels, as far as possible from each other in frequency, this effect is absent.
Now let's consider the format of the advertising package itself. In the specification, data length is measured in octets. For us, this is bytes. The very first byte is the preamble. It consists of alternating zeros and ones. It is necessary to synchronize the transmitter and receiver. Following the preamble are four bytes of the access address (Access Address). After it comes a data packet (PDU). In specification 4.0, the maximum PDU length is 39 bytes, and in version 5.0, the data packet length is increased to 257 bytes. At the end of each ad package are three bytes of checksum (CRC).

Here it should be noted that the Access Address serves to ensure that the devices understand for whom the BLE package is intended. This is a unique access code. If this access code is not familiar to the device, then the packet is ignored. On all advertising channels, unlike workers, it is the same (0x8E89BED6), so all devices on the ad channels see each other.
Consider now the format of the data block PDU. At the very beginning of the PDU packet, there is a 16-bit header. It contains the packet type, the TxAdd, RxAdd flags, as well as the length of the entire PDU field in bytes. RFUs are reserved fields. For the 4.0 specification, it looks like this:

Title:

For specification 5.0, the length of the Payload field has been increased to 255 bytes, and new fields have been added to the header:

Title:

The TxAdd field is just responsible for how the device MAC address will be seen. If this field is one, then the device's MAC will be visible as random. Consider now what are the types of advertising packages. The figure shows a list for specification 4.0. In the 5.0 format, their number is increased, but we will consider what is in both formats.
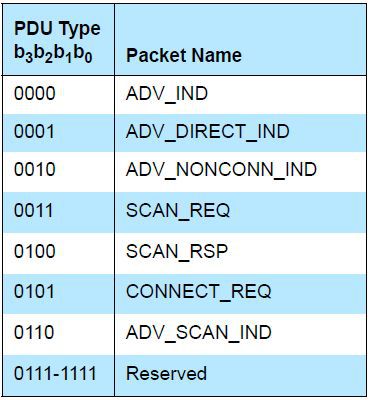
ADV_IND are non-directional packets that send devices ready to join. Most of the gadgets when sending advertising packages use them.
ADV_DIRECT_IND - directed advertising packages of attached devices. Only a specific device with a previously known MAC address can attach and exchange data with them.
ADV_NONCONN_IND - advertising packages that send non-attachable devices. These are lighthouses (beacon). Usually they are used to obtain any reference information. For example, at the entrance to the store may inform about promotions. In addition, by measuring the level of signals from beacons and knowing the map of their location, it is possible to carry out automatic positioning inside buildings. This is true for automated warehouses.
SCAN_REQ, SCAN_RSP, CONNECT_REQ - packets that exchange the device to be connected and the phone in the process of establishing a synchronous connection. These packages and the process of accession will be discussed in the second part of the article.
ADV_SCAN_IND — These packets are sent by a non-attachable device, which can provide additional information in response to a scan request.
In the second part of the article, we will look at the various modes of operation of BLE devices, as well as the mechanism of "connecting" the device to the phone and switching to operating frequencies.
Pecherskikh Vladimir
Source: https://habr.com/ru/post/319244/
All Articles