The debug mechanism in Intel processors allows you to capture them via the USB port
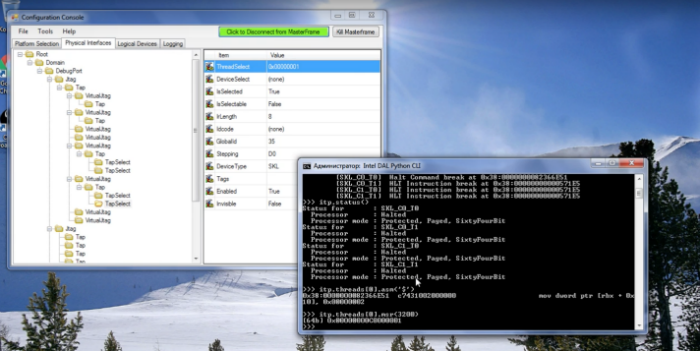
Modern Intel processors allow you to use the debugging interface through the USB 3.0 port available on many platforms to gain complete control over the system, which makes it possible to conduct attacks that are not monitored by modern security systems. A report on these mechanisms, as well as ways to protect against such attacks, was presented by Positive Technologies experts on December 28 at the Chaos Communication Congress (33C3) in Hamburg.
What is the problem
Experts Maxim Goryachiy and Mark Yermolov in their report noted that often similar hardware mechanisms are used as completely legal tools that are introduced at the production stage - for example, special debugging capabilities left by developers for setting up equipment and other "good purposes". However, now such mechanisms are available for attackers, and the price of the issue is so low that to organize such attacks you no longer need to be a state intelligence service and have special equipment.
')
One of these mechanisms was analyzed in detail and shown in the study. As a dangerous opportunity left by the manufacturer, the JTAG (Joint Test Action Group) debugging interface is featured here, access to which is now open via the USB interface. This method of access to the processor works "below" all software, allowing you to perform hardware debugging of hypervisors, OS kernels and drivers. However, the same mechanism can be used for unauthorized intrusions.
In older Intel processors, access to JTAG required the connection of a dedicated device through a debugging socket on some motherboards (ITP-XDP). This complicated access to this technology, including for intruders.
However, starting with the Skylake family of processors launched in 2015, Intel introduced the Direct Connect Interface (DCI) technology, which provides access to the JTAG via the popular USB 3.0 port. At the same time, no software or hardware agents are required on the target computer — all that is required is that the DCI interface is activated. As the researchers found out, this can be done in several ways, and on many modern computers this functionality was available literally “out of the box” - that is, by default, the ability to activate DCI is not blocked.
Below are the presentation slides (also available by reference ):
Demonstration
The report also presented a video showing how easily attackers can get full access to the processor using such a mechanism. According to researchers, this mechanism in Intel processors can lead to a whole class of new “Bad USB” attacks - but the penetration rate will be much deeper.
In conclusion of the report, the experts proposed a number of ways to protect against this threat, which are based on the use of BootGuard and prohibiting the activation of the debugging interface.
Video of performance:
Descriptions of attacks using features of the debugging mechanism of processors were transferred to Intel, but the researchers have not yet received an official response.
Source: https://habr.com/ru/post/318744/
All Articles