Anti-virus protection of the enterprise
In the article How to answer the question - what is a "computer virus", we considered the evolution of this concept. This time we will consider the option of building a layered antivirus protection.
Immediately, we note that in the article you will not find :
Obviously, the construction of a comprehensive protection requires not only installing antivirus software, but also carrying out, incl. on a regular basis, a variety of activities:
')
In order not to “jump wide”, let us leave these questions for the next time, focusing on building precisely the layered antivirus protection.
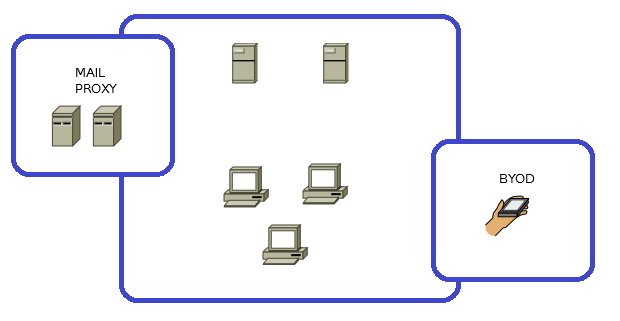
Consider a simplified diagram of the enterprise network. It usually contains user workstations, servers for internal services (AD, file-server, print-server, ERP, etc.) and servers providing communication with the outside world (Mail, Proxy, FTP, etc. .). The chart should take into account such a phenomenon as BYOD.
When choosing an antivirus solution, we consider it necessary to have a single management console for all products, in which you can monitor the status and collect statistics from all nodes, distribute and monitor the status of database updates and other components, it is possible to centrally distribute the antivirus (for most platforms).
Further, in addition to cost, it is advisable to pay attention to the following parameters:
Upon careful consideration of the above parameters, it becomes clear that the choice is only becoming more complicated: WinXP is not in a hurry to leave, at the same time, manufacturers refuse to support it, even among world market leaders, some platforms may have a tick (the Windows line can be supported starting from with Win7, not all Linux / Unix distributions will be able to install the product, special versions of products for mobile platforms or virtualization systems), there are a lot of antivirus comparisons and often only by the detection criterion, but it's enough The accuracy of comparisons and the applicability of the results in your situation may raise questions.
Possession of one antivirus solution, by objective indicators, such as the cost of licenses, staff training, and the allocation of resources for the administration console, is usually cheaper. But this is true in the absence of infections, and it is practically impossible to estimate in advance the scale of the consequences.
We only note that in the event of infection with a new malicious code, it is almost impossible to localize its distribution, and the support service and virlab can help identify the source and cope with the consequences. For this situation, support in the native language and treatment functionality are important.
We propose to consider and evaluate the approach when, to the detriment of the simplicity of managing the anti-virus protection system and the cost of ownership, it is proposed to use echeloned anti-virus protection, which includes solutions from several manufacturers.
Computers, servers and other devices should be divided into classes according to their main use. For the earlier enterprise scheme, these will be:
When divided into classes should not get carried away, the simultaneous support of more than 4 solutions can lead to low knowledge of each of the systems used.
Direct data exchange (files) between devices of the same class should be prohibited and limited to technical measures. In this case, the data (files) from the point of entry into the protected system before use on the next device will be checked by two antiviruses:
This, of course, does not give 100% guarantees against infections, but reduces the risk of epidemics, contributes to the localization and timely detection of infection.
When choosing an antivirus solution for a particular class of devices, which is clearly smaller than the entire fleet of the company, it is easier to choose solutions by the criterion of support for the platforms used.
We would like to pay special attention to the fact that for the class “servers providing communication with the outside world” , unlike other classes, the treatment functionality is almost irrelevant, and the detection is particularly high.
It is a reasonable question - why complicate and theorize, invent classes, implement several anti-virus solutions, taking into account the potential increase in the cost of ownership?
The practice of using several anti-virus solutions using the above or a similar scheme occurs and, as a rule, is justified by the same considerations that are given in the article.
Indicator M4.7 (p. 28 HUNDRED BR IBBS-1.2-2014 )
Immediately, we note that in the article you will not find :
- Comparison of existing solutions on the market with the aim of “finding the best-most antivirus”. Marketers are successfully engaged in such comparisons; it is not difficult to find such “studies”;
- instructions on the settings of a specific software product, which will provide 100% (or 99.999 ...%) protection against all threats.
Obviously, the construction of a comprehensive protection requires not only installing antivirus software, but also carrying out, incl. on a regular basis, a variety of activities:
')
- development and updating of policies, instructions, regulations (reaction to incidents, on the distribution of access rights, requirements for passwords, etc., no matter how one may regard such “paper security”, but this is an important and sometimes a mandatory component);
- user training;
- patch management;
- backup information;
- introduction of additional systems (IPS / IDS, vulnerability scanners, DNS filtering services, etc.)
- Independent contractors may be hired to conduct an audit / pentest.
In order not to “jump wide”, let us leave these questions for the next time, focusing on building precisely the layered antivirus protection.
Consider a simplified diagram of the enterprise network. It usually contains user workstations, servers for internal services (AD, file-server, print-server, ERP, etc.) and servers providing communication with the outside world (Mail, Proxy, FTP, etc. .). The chart should take into account such a phenomenon as BYOD.

What parameters are we looking at?
When choosing an antivirus solution, we consider it necessary to have a single management console for all products, in which you can monitor the status and collect statistics from all nodes, distribute and monitor the status of database updates and other components, it is possible to centrally distribute the antivirus (for most platforms).
Further, in addition to cost, it is advisable to pay attention to the following parameters:
- Coverage of platforms used at the enterprise (types and versions of OS, hardware);
- impact on the performance of the main tasks;
- detection quality (taking into account the scope of the organization’s business and country of location);
- quality of treatment (this parameter is often forgotten);
- availability of qualified technical support, preferably in their native language;
- availability of certificates - if there are relevant requirements.
Upon careful consideration of the above parameters, it becomes clear that the choice is only becoming more complicated: WinXP is not in a hurry to leave, at the same time, manufacturers refuse to support it, even among world market leaders, some platforms may have a tick (the Windows line can be supported starting from with Win7, not all Linux / Unix distributions will be able to install the product, special versions of products for mobile platforms or virtualization systems), there are a lot of antivirus comparisons and often only by the detection criterion, but it's enough The accuracy of comparisons and the applicability of the results in your situation may raise questions.
Single anti-virus solution
Possession of one antivirus solution, by objective indicators, such as the cost of licenses, staff training, and the allocation of resources for the administration console, is usually cheaper. But this is true in the absence of infections, and it is practically impossible to estimate in advance the scale of the consequences.
We only note that in the event of infection with a new malicious code, it is almost impossible to localize its distribution, and the support service and virlab can help identify the source and cope with the consequences. For this situation, support in the native language and treatment functionality are important.
Layered Antivirus Solution
We propose to consider and evaluate the approach when, to the detriment of the simplicity of managing the anti-virus protection system and the cost of ownership, it is proposed to use echeloned anti-virus protection, which includes solutions from several manufacturers.
Computers, servers and other devices should be divided into classes according to their main use. For the earlier enterprise scheme, these will be:
- servers providing communication with the outside world;
- servers providing internal services;
- user workstations (here we will assign BYOD).
When divided into classes should not get carried away, the simultaneous support of more than 4 solutions can lead to low knowledge of each of the systems used.
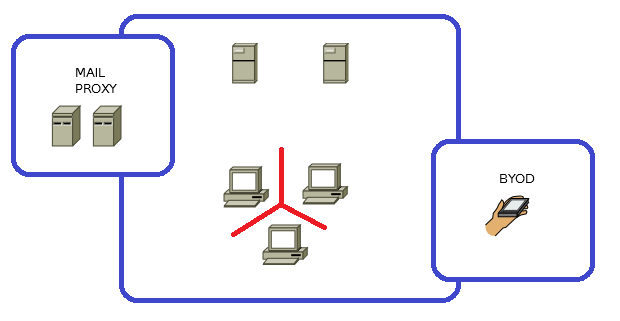
Direct data exchange (files) between devices of the same class should be prohibited and limited to technical measures. In this case, the data (files) from the point of entry into the protected system before use on the next device will be checked by two antiviruses:
- Internet - [antivirus on mail / proxy server] - [antivirus on a workstation];
- Infected removable media - [antivirus on AWP] - [antivirus on server] - [antivirus on AWP];
- Infected removable media - [antivirus on AWP] - [antivirus on mail / proxy server];
- etc.
This, of course, does not give 100% guarantees against infections, but reduces the risk of epidemics, contributes to the localization and timely detection of infection.

When choosing an antivirus solution for a particular class of devices, which is clearly smaller than the entire fleet of the company, it is easier to choose solutions by the criterion of support for the platforms used.
We would like to pay special attention to the fact that for the class “servers providing communication with the outside world” , unlike other classes, the treatment functionality is almost irrelevant, and the detection is particularly high.
Is it too much?
It is a reasonable question - why complicate and theorize, invent classes, implement several anti-virus solutions, taking into account the potential increase in the cost of ownership?
The practice of using several anti-virus solutions using the above or a similar scheme occurs and, as a rule, is justified by the same considerations that are given in the article.
UPD 1
(thanks to muon for the exact link)Indicator M4.7 (p. 28 HUNDRED BR IBBS-1.2-2014 )
Does the RF BS organization organize a centralized, layered antivirus protection system that provides for the use of antivirus protection tools from different manufacturers for:
- workstations;
- server hardware, including email servers;
- firewall hardware?
Source: https://habr.com/ru/post/318436/
All Articles