Hacking on board the aircraft

During the 5 years that I have been working at IOActive, I have been able to visit many interesting places thousands of kilometers from home. Therefore, flight for me has become commonplace. You might think that this is nothing special, but not for me, as a person who is afraid to fly. Not to say that I managed to get rid of this phobia; after a dozen flights, my palms are still sweating on takeoff, but I have come to terms with it, even, one might say, I sometimes like to fly ... and hack the systems right from the side.
To overcome the fear I was helped to study the functionality of the aircraft and getting used to the noise, jumps and turbulence. This article will explain how the onboard systems work, in particular, about the On-Board Entertainment and Information System (BRIS) developed by Panasonic Avionics.
Two years ago, while I was flying from Warsaw to Dubai, I decided to play a little with BRIS. And when I clicked to a certain place in one of the upper corners of the screen, I saw the following debugger details:
---- Interactive: ek_seatappbase_1280x768_01.01.18.01.cram Content: ek_seatappcontent_1280x768.01.01.8.01.cram Engine: qtengine_01.14.0.01.squash LRU Type: 196 2 IP: 172.17.148.48 Media Player Auto Popup Enabled: false ----- 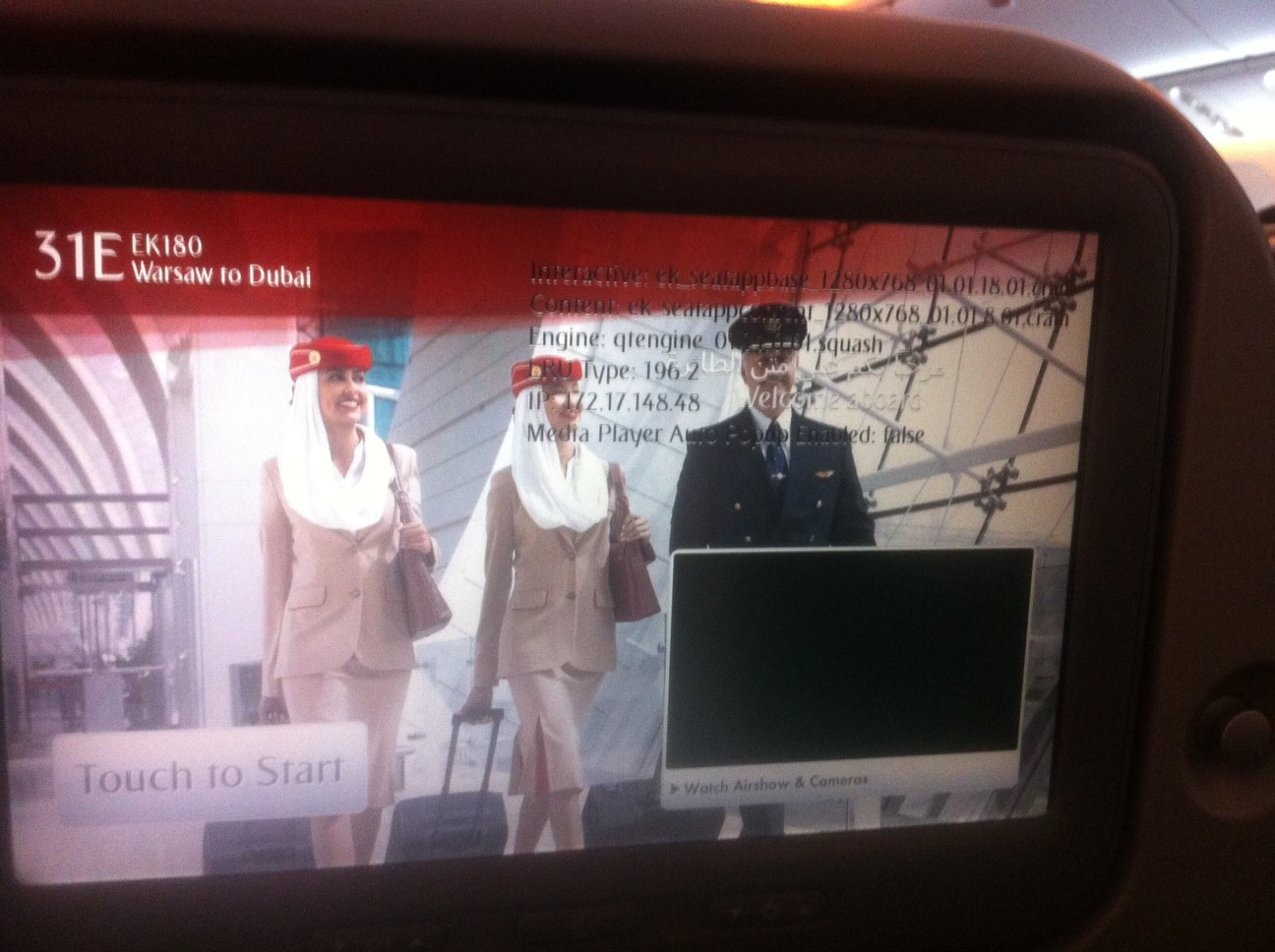
After arriving in Dubai and searching for keywords on Google, I found in the open access hundreds of firmware for various airlines.
')
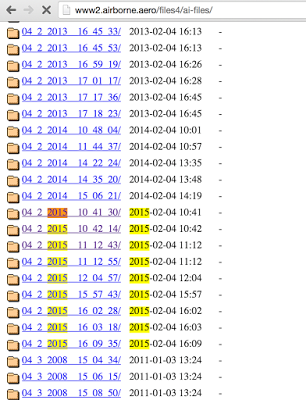
Obviously, the firmware is actively updated, so you can get access to the current one, which is installed on board. To date, the files are still there, but access to the list of directories is closed.
Below is a list of airlines for which I managed to find the firmware:
- Emirates
- Airfrance
- Aerolineas argentinas
- United
- Virgin
- Singapore
- Finnair
- Iberia
- Etihad
- Qatar
- Klm
- American airlines
- Scandinavian
The basic architecture of BRIS is as follows:
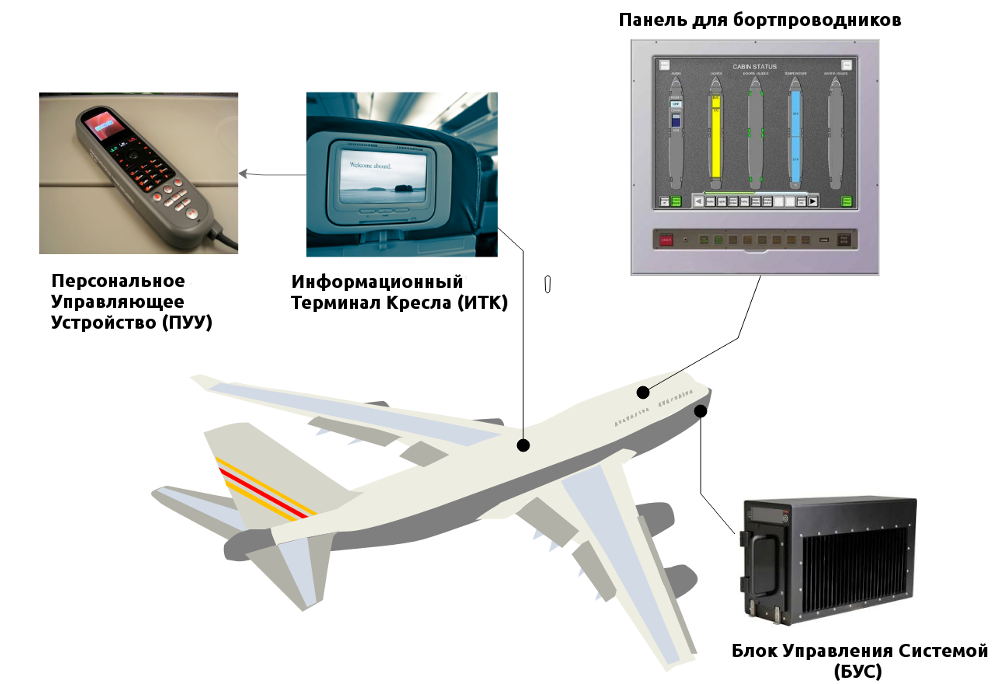
System Control Unit (BEAD)
This is a certified onboard server. Passengers, as a rule, can monitor in real time the current flight parameters, such as wind speed, latitude, longitude, altitude and temperature overboard. The BEADS receives all this information via the avionics bus (usually ARINC 429) and then the Informational Terminals Terminals (ITCs) can access it via Ethernet.
Information Terminal Chairs (ITK)
This is a removable line unit and through it passengers have access to passive and active BRIS functionality, such as watching movies, buying goods, reading articles or accessing the Internet. Simply put, it is a built-in touch screen device. Newer models use Android, while outdated ones are mostly Linux.

Removing ITK - this is Rave AIX, not a model from Panasonic Avionics ( source )
Personal Control Device (PUU)
This is an optional device. With the help of PUU, ITC can be managed and, as will be shown below, it can also work as a credit card terminal.
Panel for flight attendants
Flight attendants and other crew members can use this panel to control aircraft functions such as lights, drives (including beds), passenger announcements, onboard purchases, or a personnel call system. Cabin Management System [Cabin Management System] is usually integrated with BRIS. Panasonic Avionics does this with Global Communications Services [Global Communications Services], providing general functionality for simple cockpit operations (see here ). CrewApp crew app is available from the flight attendant panel.
Panasonic BRIS
Panasonic BRISS: outdated 3000 / 3000i and new XSeries eFX, eX2 and eX3 (on Android). The hardware component can vary, but in architecture they are similar and they have common characteristics.
More information on Panasonic's BRIS can be found on their website .
These systems can be customized, which allows the airlines to install BRIS in accordance with the policies of the airline, while the code base is almost the same.
After analyzing the firmware, I was not quite able to find out how to download data on the ground. Typically, the content is updated via Wi-Fi ad-hoc-network, or through a high-speed mobile connection as soon as the plane lands. Panasonic's BRIS is mainly updated via Floppinet . Communication with satellites or mobile networks in flight is available, but in most cases, BRIS works autonomously, with preloaded content. Normally, BRIS does not even check credit cards in real time.
Panasonic Avionics BRIS follows a client-server architecture with three main components:
- CrewApp
- Seatapp
- Backend
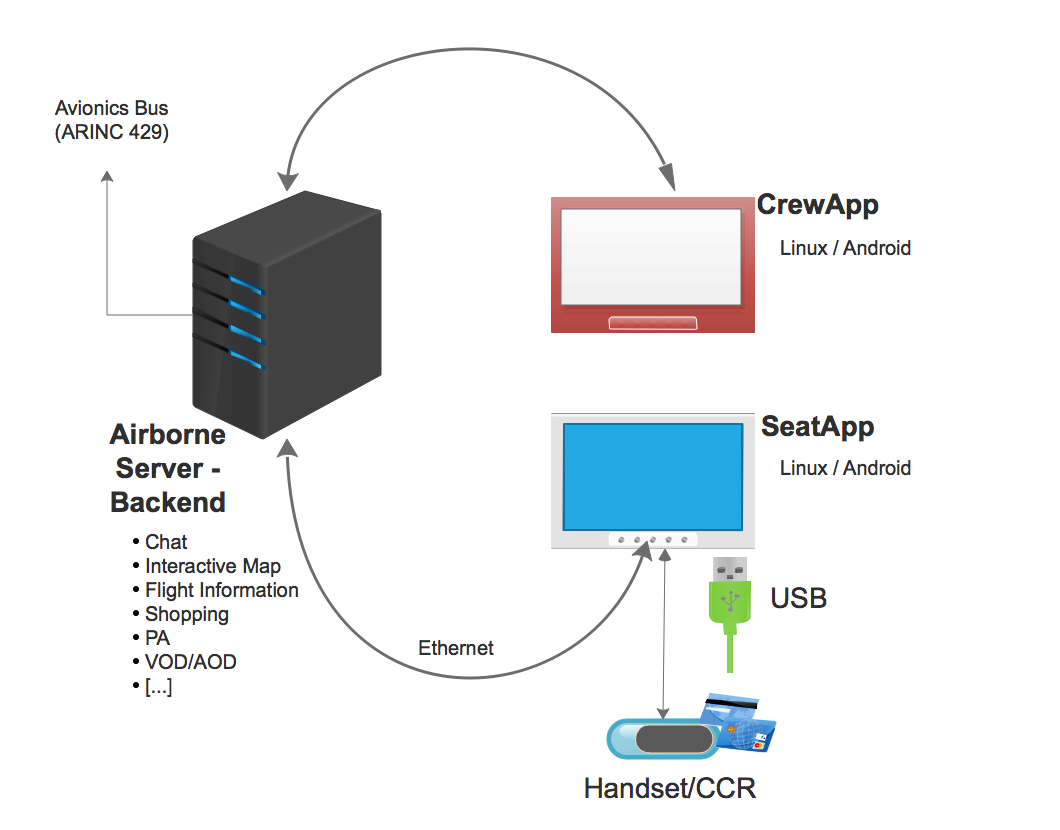
I found several versions of CrewApp and SeatApp on the above page. When I was googling keywords, I also managed to find a backend in open access on different .aero sites. Despite the fact that they have brand and unique data from the airlines, the code base in them is from the Panasonic backend.
It is impossible to cover all the options for BRIS in one article, as the airlines expand and adapt the framework, therefore, we’ll discuss further specific functions.
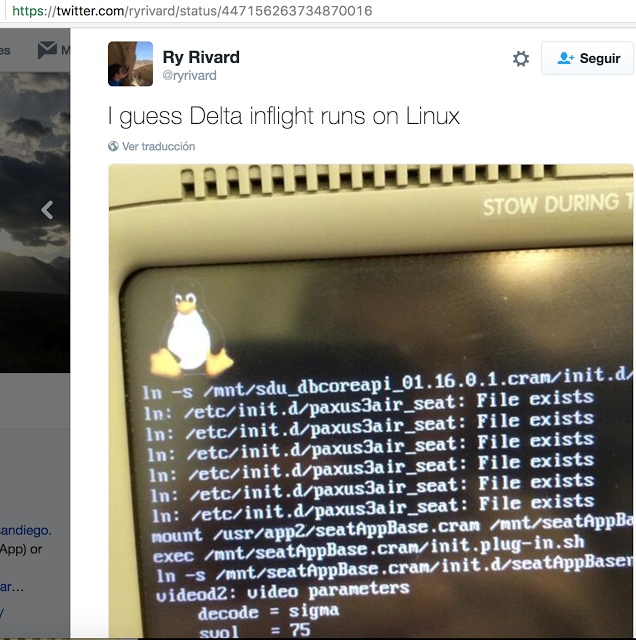
Reboot SeatApp on Linux
The firmware files (in this case, the program that runs on the device is not supported by the user), which I analyzed did not contain the entire system, but only the parts that need to be updated. It's sad because We could find out more information about the operation of these devices, but still some interesting points can be clarified using the available files.
Scripts
Panasonic Avionics has developed its declarative scripting programming language to interact with the user interface and main application functions. It supports dozens of teams and has good functionality.
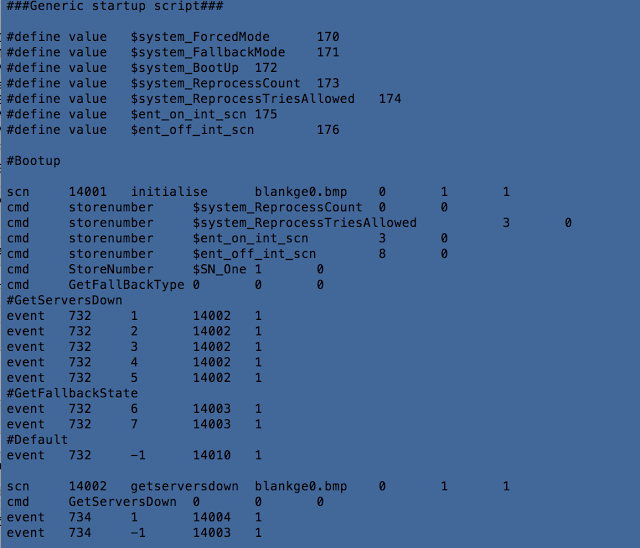
Sample code core / startup.txt
Reverse engineering of the main binary file (airsurf) will let you know how the parser of such scripts works. To demonstrate, let's look at #define .
The script is processed line by line and when the parser sees the #define construction, it tries to parse it in sub_80C2690 .
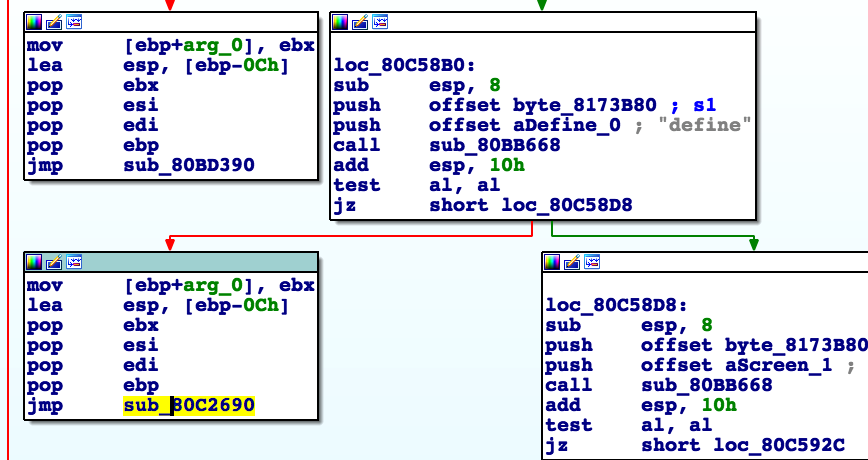
In this function, 5 types can be defined: flash, text, draw, timer, and value.

The first line of the script contains #define with the value [value], let's see how it is processed.
First of all, the string is parsed and the name of define is extracted. Then the parser checks whether the number (below the blue block) is the value that is after (below the green block).
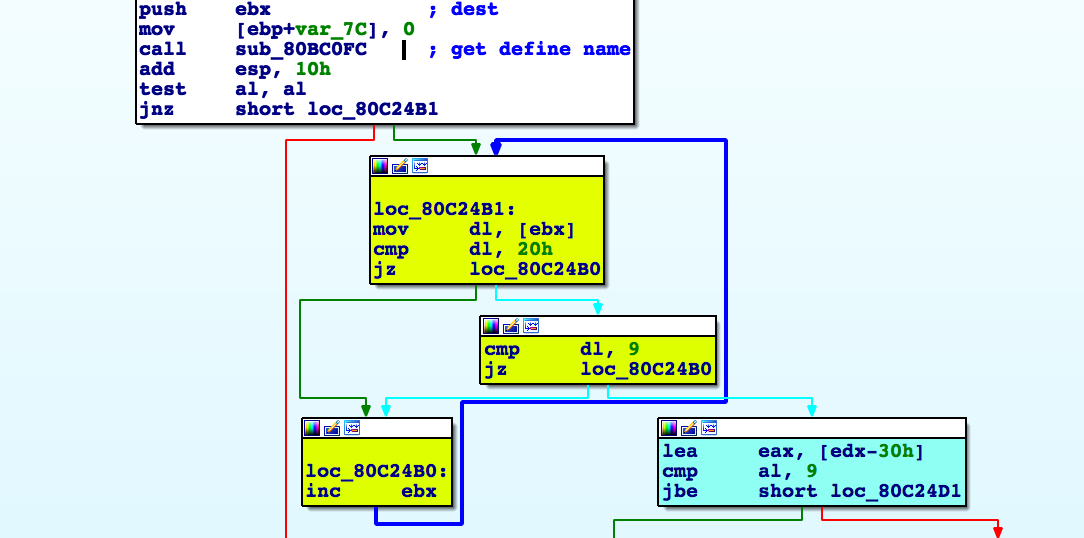
If the value is not a number, then it is compared with various variables and if a match is found, it is replaced with its value.
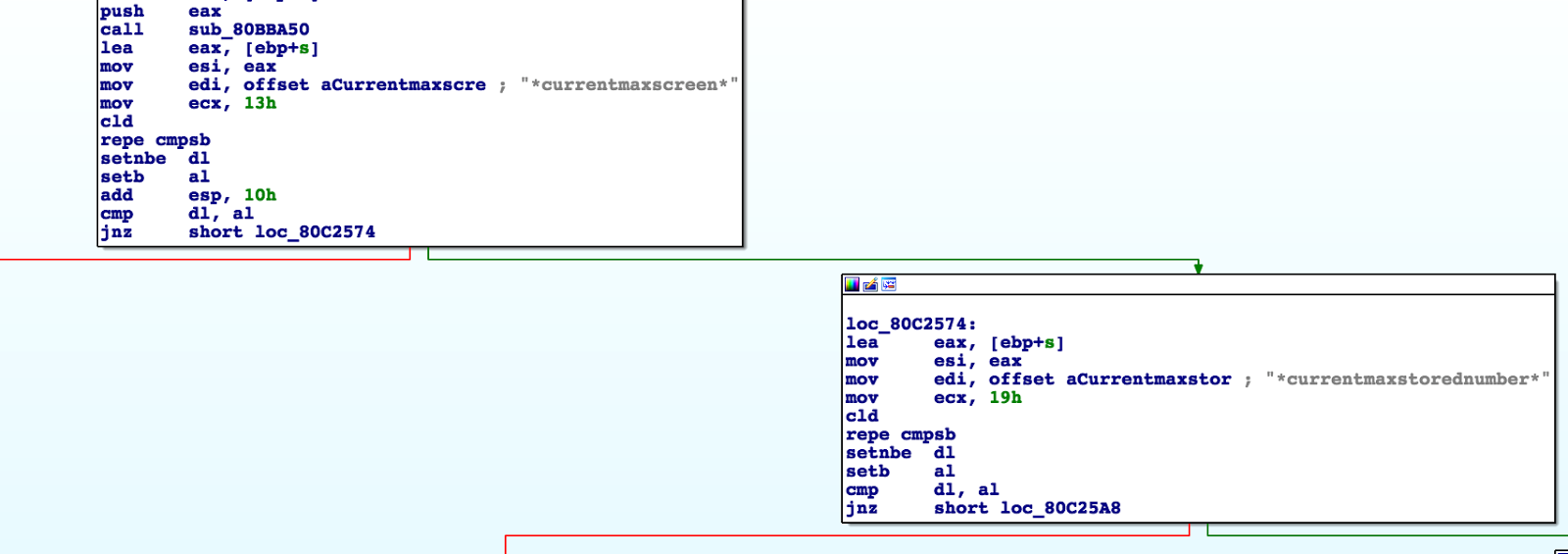
If the value is a number, then the name / value pair is added to the global array define (the blue block below)
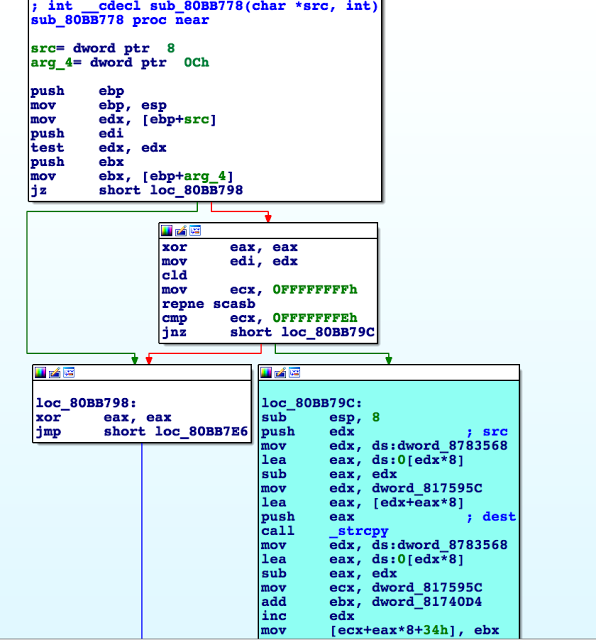
For the cmd command, the binary calls the desired function from the cmd table and passes the arguments.
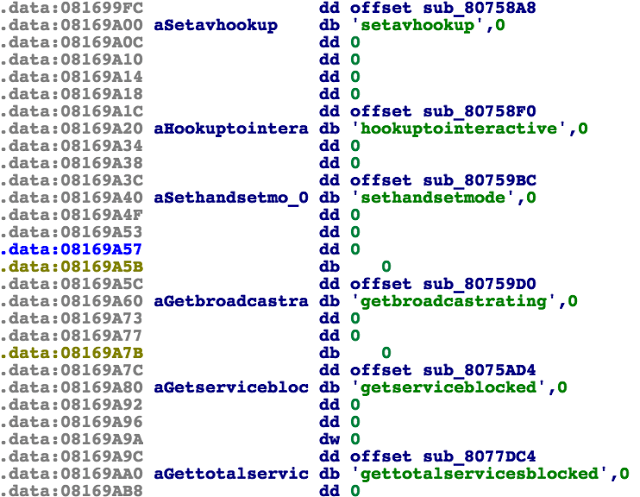
Here you can find some interesting features, for example, the one that reads information about a credit card after it is activated in the terminal.
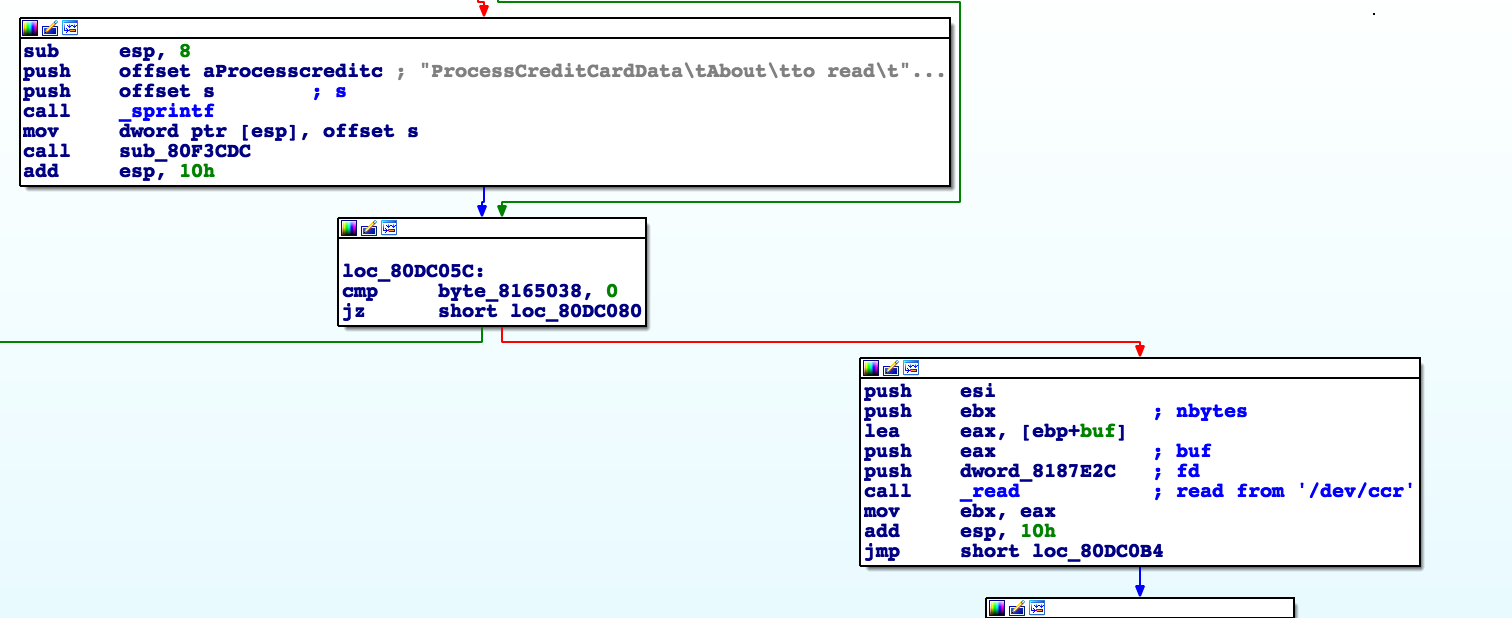
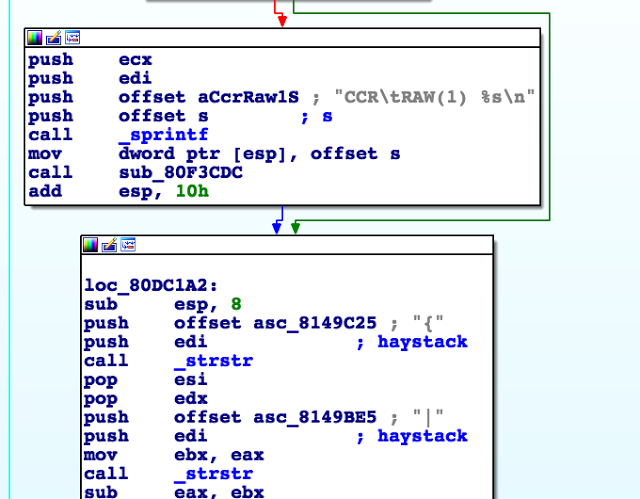
The data received from the card reader (/ dev / ccr) is parsed, printed and checked.
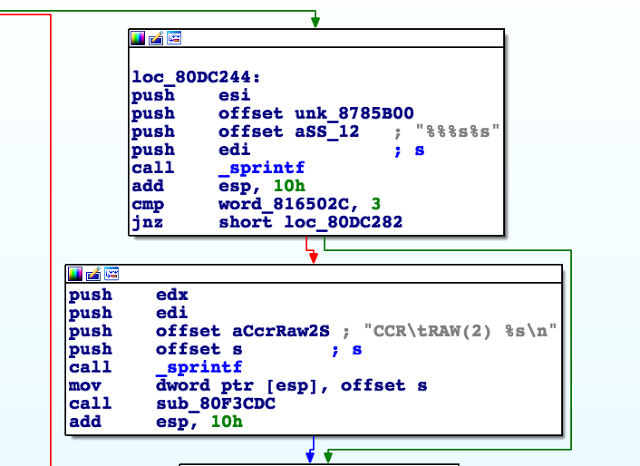
You can also find regular files, such as shell scripts, configuration files (containing embedded credentials), databases, resources and libraries.
In one of the tweets where the reboot of the Panasonic BRIS was removed from Panasonic, I saw the following information. SeatAppBase application files are the same as we are considering.
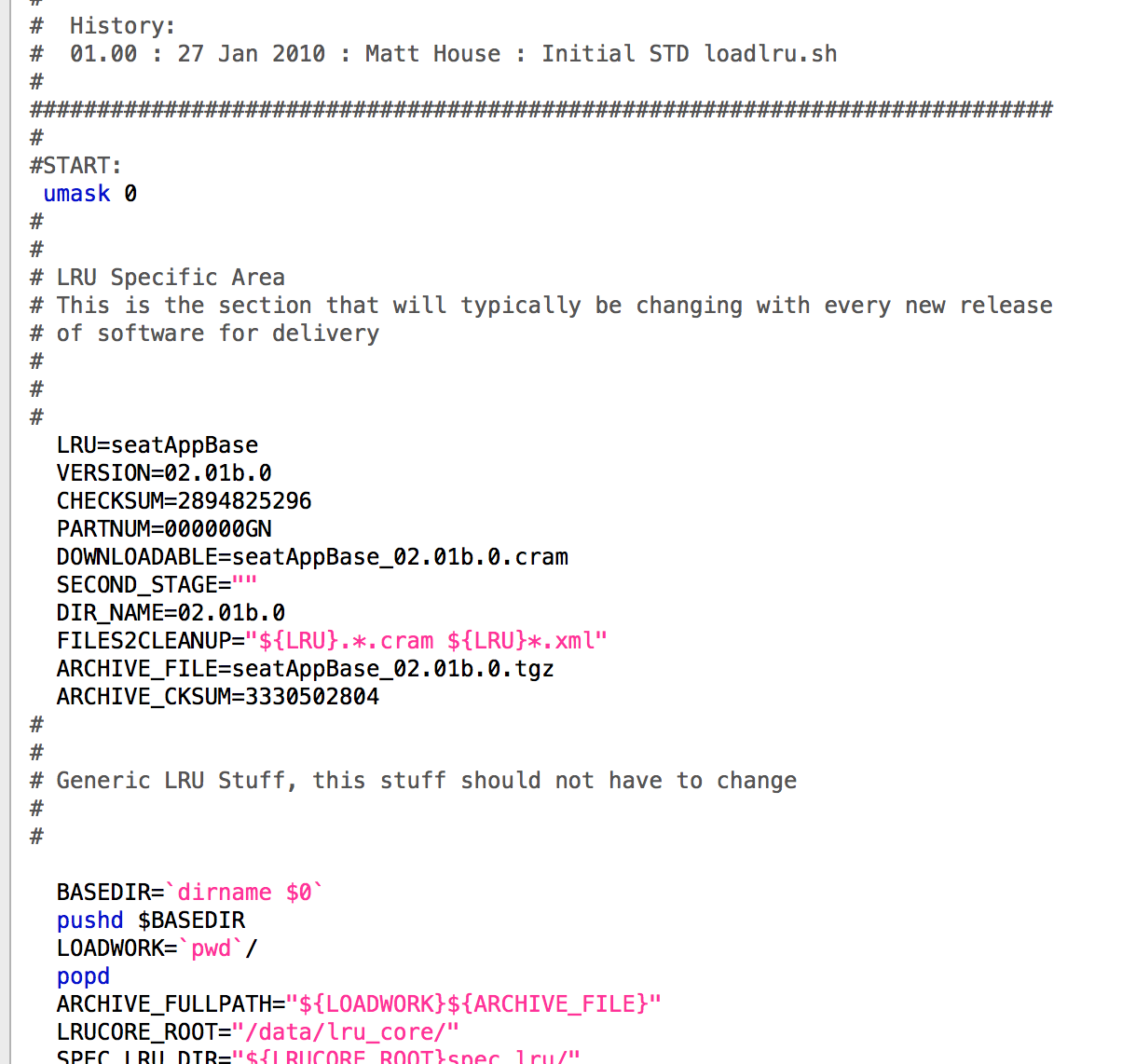
loadlru.h
In the new versions of BRIS X, Panasonic switched to Android and, accordingly, the old .txt scripts are replaced with the approach using QT QML:
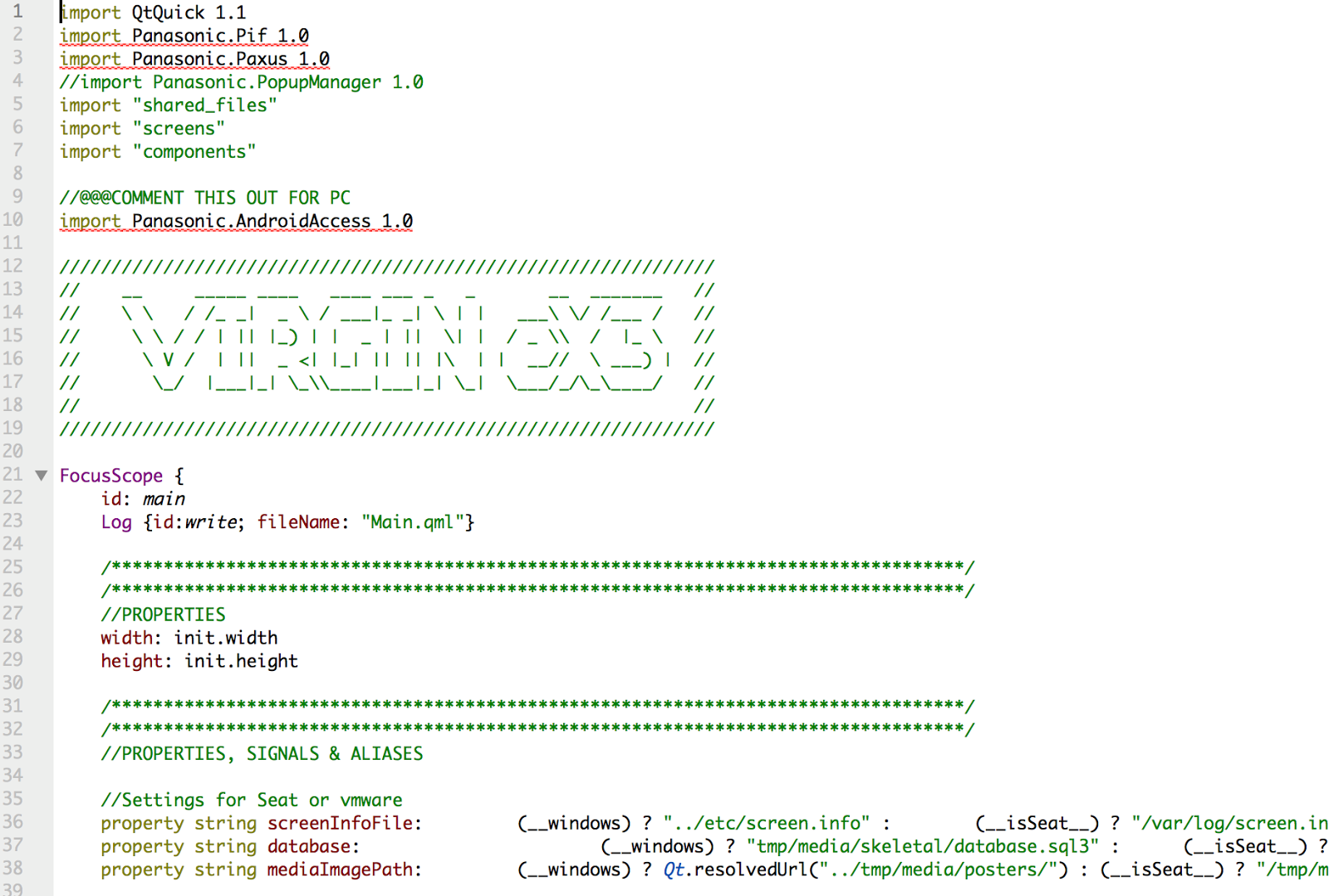
PHP is used in backend. At a glance, vulnerabilities are visible.
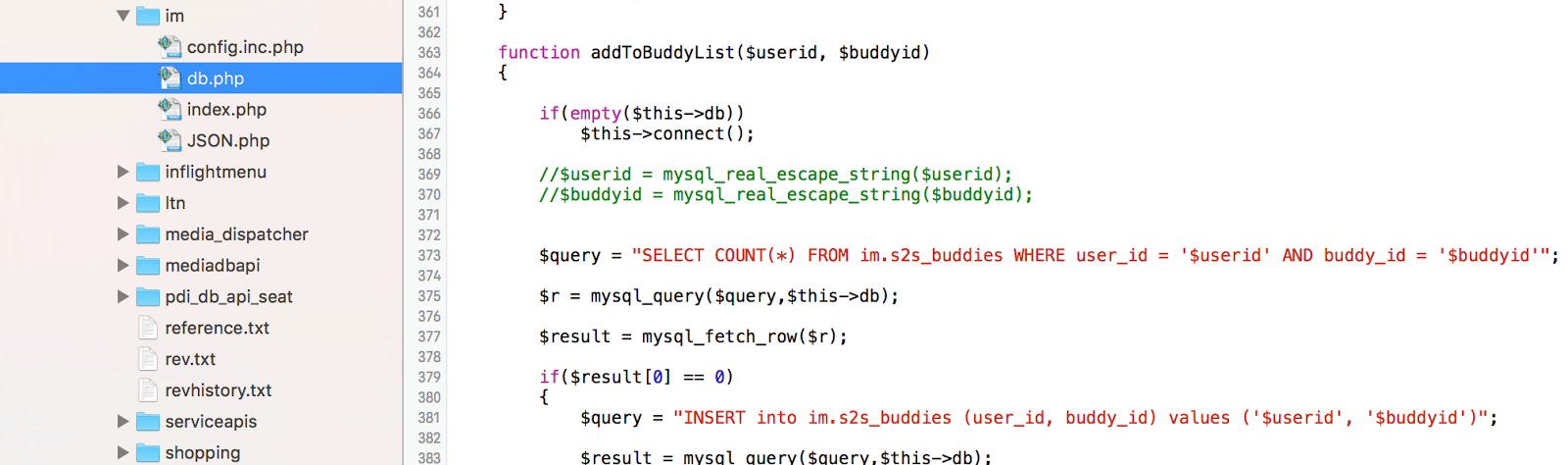
The image above refers to the chat functionality between the seats, where passengers can send messages to each other. You will not be hard to guess what is wrong here, and this is not the only problem.
The following videos demonstrate exploitation of vulnerabilities, but without causing damage.
- Bypass credit card verification
- File access (for example / dev / random)
- SQL injection
Potential threats
So how far can an attacker use such vulnerabilities in BRIS? There is no definitive answer to this question, but we will try to consider some general cases that are not specific to a particular system manufacturer, but we will do this by considering more aspects of the system’s operation.
According to the DO-178B standard, which defines the specifications of real-time operating systems in aviation, BRIS should be between levels D and E. Panasonic Avionics BRISS is certified at level E. This means that even if the whole system fails, this is nothing will change or create some inconvenience to passengers.
I would also like to note that the air vessel information network is divided into 4 parts, according to the type of data that they process: entertainment of passengers, passenger devices, airline information services and aircraft control.
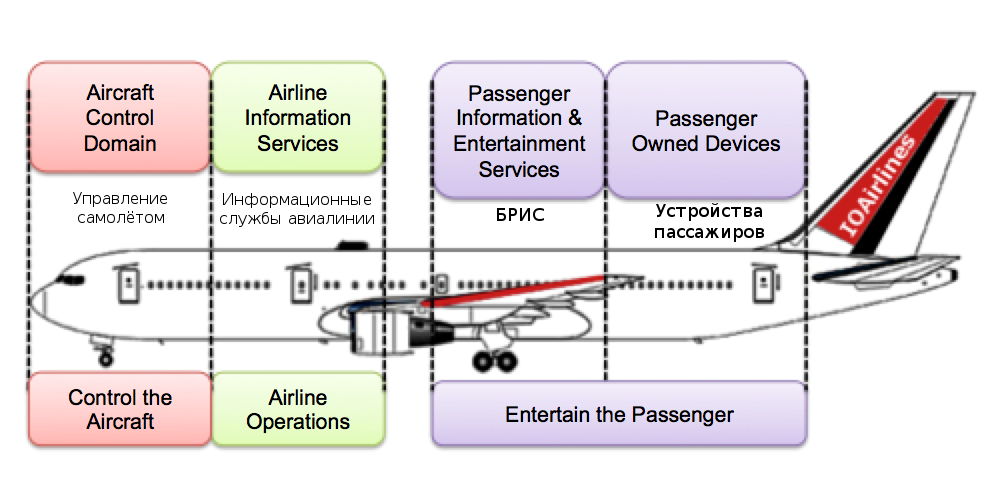
Control of the aircraft should belong to the same part of the network, which should be physically separated from the passenger part, but this is not always the case. Some ships use optical information diodes, while others prefer network gateway modules. This means that a potential threat cannot be excluded as long as the connection between the two parts exists.
BSID can be an attack vector. In some cases, this type of attack will not be possible due to the isolation of the systems, but in others the potential threat remains due to the physical connection of the systems. IOActive successfully compromised the gateways of other vehicles. The distinction between the passenger and control systems is strongly defined due to specific devices, software and aircraft settings.
In 2014, we published a series of vulnerabilities in satellite communication devices (SATCOM), including onboard terminals. Most worried about the fact that these devices are used in various areas of the system, which allows an attacker to use equipment to gain access to avionics through a compromised BRIS.
On the IT side, hacking BRIS means that an attacker can control the information that passengers receive on board. For example, you can change the flight data such as altitude or speed and show the fictitious route of the aircraft on the map. An attacker could compromise the CrewApp personnel application and control the lights or drives in the classes above. If these threats are combined, then passengers can be confused.
Receiving personal information, including credit card information, also takes place if the backend, which sometimes provides specific information about the frequency of flights or VIP membership, is not properly configured.
On the other hand, a Wi-Fi network can be configured securely without any security threats.
This would like to say that in our opinion, such systems will not be able to withstand a serious attack from an experienced attacker. Airlines need to be vigilant when it comes to BRIS, providing carefully separated systems and checking every aspect of security in stages. Responsibility for security does not lie on the shoulders of only the developer of BRIS, the manufacturer of the vessel or the operator. Each plays an important role in the security environment.
Responsibility for disclosure
We reported the found vulnerabilities of Panasonic Avionics in March 2015. We hope that there was enough time to close the found vulnerabilities, at least the most obvious ones. Nevertheless, we think it is difficult to say that all these problems have been solved in an area where different airlines and hundreds of product versions are involved.
Source: https://habr.com/ru/post/318228/
All Articles