Own traffic exchange point in the data center. Part 2. Tools for DataLine-IX participants
Today we continue to talk about the DataLine-IX traffic exchange point. The first part was devoted to the device of our traffic exchange point. In this post we will tell about a couple of tools that will be useful to its participants in the work.

One of the Meet-Me-Room premises at the OST site.
Personal office DataLine-IX is based on the open-source project IXP Manager . It collects statistics on participant traffic and information on connectivity with other participants.
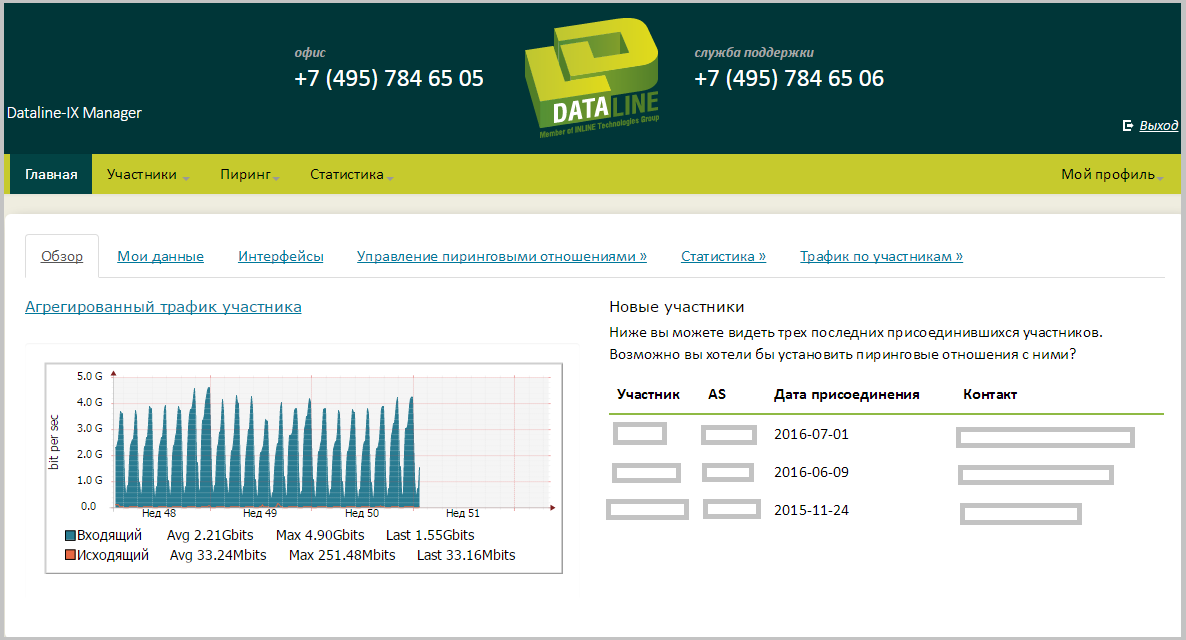
Home page of the Personal Cabinet.
Scrolling traffic statistics is grouped by 12 hours, days, weeks and months. You can analyze not only the bit rate, but also the packet rate, errors, the number of dropped packets.

')
Here you can also see statistics on the distribution of your traffic among other DataLine-IX participants.

Through the Personal Account, the participant can request direct accession ( private peering ) to other feasts.

The “Interfaces” tab contains information about the parameters for connecting a participant to the DataLine-IX.

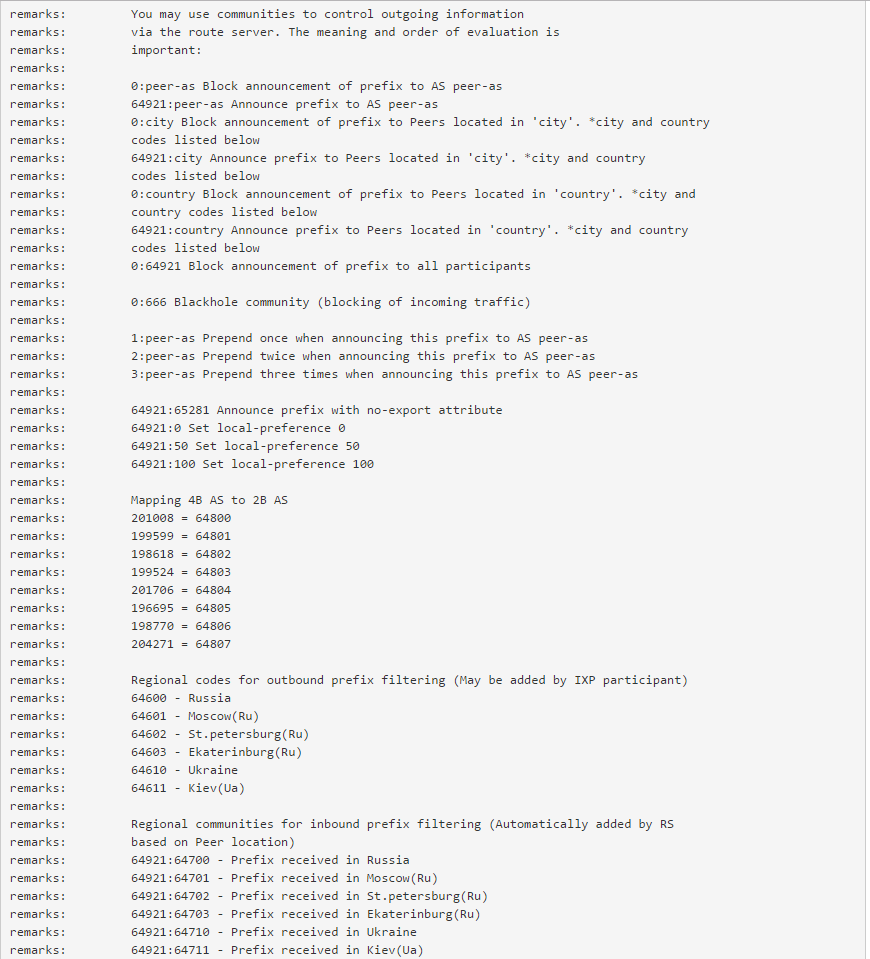
BGP ommunity is a kind of tag that marks the route. When an RS receives a route from a community, it can perform certain actions based on the value of the attribute.
Typically, the community is written as ASN: VALUE, i.e. autonomous system number and community value, which determines the traffic routing policy. For IX, a different format is usually used: ACTION: VARIABLE, i.e. action and variable. '0' as an action means a ban on announcement, the AS DataLine-IX number is a resolution.
According to the AS number of our IX, there is one nuance: initially it is 203921, but since the BGP standard community can only take 2 bytes as an ASN or Value, the mapping of four-byte ASNs to double-bytes is used. Therefore, the AS DataLine-IX number 203921 is mapped to 64921.
With the help of the BGP Community, DataLine-IX participants can manage outgoing and incoming route announcements and repel DDoS attacks.
Manage outgoing and incoming route announcements. On RS DataLine-IX, filters for managing inbound and outbound announcements are already configured. The participant can only register in their announcements the relevant community in the direction of the traffic exchange point.
Information on the community for DataLine-IX at the RIPE NCC .
Here is an example of filtering outgoing announcements using the community:
The participant of DataLine-IX - AS 49063 - wants to announce routes to all participants in Kiev, except for participant AS 35297, and prohibits the announcement to all participants throughout Ukraine.
BGP COMMUNITY in the announced prefixes will look like this:
0: 35297 - a ban on the announcement of routes for the participant AS 35297.
64921: 64611 - the announcement is allowed to all participants in Kiev.
0: 64610 - a ban on the announcement of the whole of Ukraine.
With incoming announcements easier. All routes arrive already with a certain community. Each corresponds to a city and region. The participant on his side simply decides whether to accept them or not:
64921: 64700 - announcements of routes from Russia.
It is worth noting that geolocation is determined solely by the location of the participant's equipment, which establishes a BGP session with the RS.
For a visual example, let's take a BGP configuration snippet on a Cisco router. Based on the above rules, the settings will look like this:

Protection against DDoS attacks in IX using BGP Blackhole. BGP Blackhole allows filtering malicious traffic before a participant enters AS, that is, on ports IX.
This method is designed to repel attacks on the channel bandwidth, in our case it is a link between the participant and DataLine-IX. When using BGP Blackhole, the participant sacrifices the availability of the host, but DDoS will not clog the entire channel and will not affect other services.
The BGP Blackhole implementation also uses the community: routes for the attacked host are marked with a special community - 0: 666. During the attack, the route with this community is announced on the RS, which spreads the route to the other participants, replacing Next-hop with a specially allocated value.
Consider the work of BGP Blackhole step by step. Imagine that the host to be attacked is in AS 64512 (IP 10.10.10.10):
And of course, DataLine-IX has its own Looking Glass . Here you can see online:
That's all we wanted to talk about DataLine-IX tools. Ask questions in the comments if something is left behind the scenes.

One of the Meet-Me-Room premises at the OST site.
Personal Area
Personal office DataLine-IX is based on the open-source project IXP Manager . It collects statistics on participant traffic and information on connectivity with other participants.
Home page of the Personal Cabinet.
Scrolling traffic statistics is grouped by 12 hours, days, weeks and months. You can analyze not only the bit rate, but also the packet rate, errors, the number of dropped packets.
')
Here you can also see statistics on the distribution of your traffic among other DataLine-IX participants.
Through the Personal Account, the participant can request direct accession ( private peering ) to other feasts.
The “Interfaces” tab contains information about the parameters for connecting a participant to the DataLine-IX.
BGP Community Tool
BGP ommunity is a kind of tag that marks the route. When an RS receives a route from a community, it can perform certain actions based on the value of the attribute.
Typically, the community is written as ASN: VALUE, i.e. autonomous system number and community value, which determines the traffic routing policy. For IX, a different format is usually used: ACTION: VARIABLE, i.e. action and variable. '0' as an action means a ban on announcement, the AS DataLine-IX number is a resolution.
According to the AS number of our IX, there is one nuance: initially it is 203921, but since the BGP standard community can only take 2 bytes as an ASN or Value, the mapping of four-byte ASNs to double-bytes is used. Therefore, the AS DataLine-IX number 203921 is mapped to 64921.
With the help of the BGP Community, DataLine-IX participants can manage outgoing and incoming route announcements and repel DDoS attacks.
Manage outgoing and incoming route announcements. On RS DataLine-IX, filters for managing inbound and outbound announcements are already configured. The participant can only register in their announcements the relevant community in the direction of the traffic exchange point.
Information on the community for DataLine-IX at the RIPE NCC .
Here is an example of filtering outgoing announcements using the community:
The participant of DataLine-IX - AS 49063 - wants to announce routes to all participants in Kiev, except for participant AS 35297, and prohibits the announcement to all participants throughout Ukraine.
BGP COMMUNITY in the announced prefixes will look like this:
0: 35297 - a ban on the announcement of routes for the participant AS 35297.
64921: 64611 - the announcement is allowed to all participants in Kiev.
0: 64610 - a ban on the announcement of the whole of Ukraine.
With incoming announcements easier. All routes arrive already with a certain community. Each corresponds to a city and region. The participant on his side simply decides whether to accept them or not:
64921: 64700 - announcements of routes from Russia.
It is worth noting that geolocation is determined solely by the location of the participant's equipment, which establishes a BGP session with the RS.
For a visual example, let's take a BGP configuration snippet on a Cisco router. Based on the above rules, the settings will look like this:

Protection against DDoS attacks in IX using BGP Blackhole. BGP Blackhole allows filtering malicious traffic before a participant enters AS, that is, on ports IX.
This method is designed to repel attacks on the channel bandwidth, in our case it is a link between the participant and DataLine-IX. When using BGP Blackhole, the participant sacrifices the availability of the host, but DDoS will not clog the entire channel and will not affect other services.
The BGP Blackhole implementation also uses the community: routes for the attacked host are marked with a special community - 0: 666. During the attack, the route with this community is announced on the RS, which spreads the route to the other participants, replacing Next-hop with a specially allocated value.
Consider the work of BGP Blackhole step by step. Imagine that the host to be attacked is in AS 64512 (IP 10.10.10.10):
- The AS 64512 administrator creates a route (10.10.10.10/32), marked community 0: 666, and announces this prefix towards RS.
- RS, seeing community 0: 666, replaces Next Hop with a specially reserved address 185.1.52.66 and distributes this signal to the other participants (in the picture AS 64513). In the future, RS will respond to ARP requests for host 185.1.52.66 with the MAC address 0066.0066.0066.
- If there is traffic from AS 64513 to the attacked IP on 10.10.10.10, then the router in AS 64513 sends traffic from DMAC 0066.0066.0066.
- Further, the traffic is “dropped” on the port to which AS 64513 is connected and does not reach the port of the attacked participant.
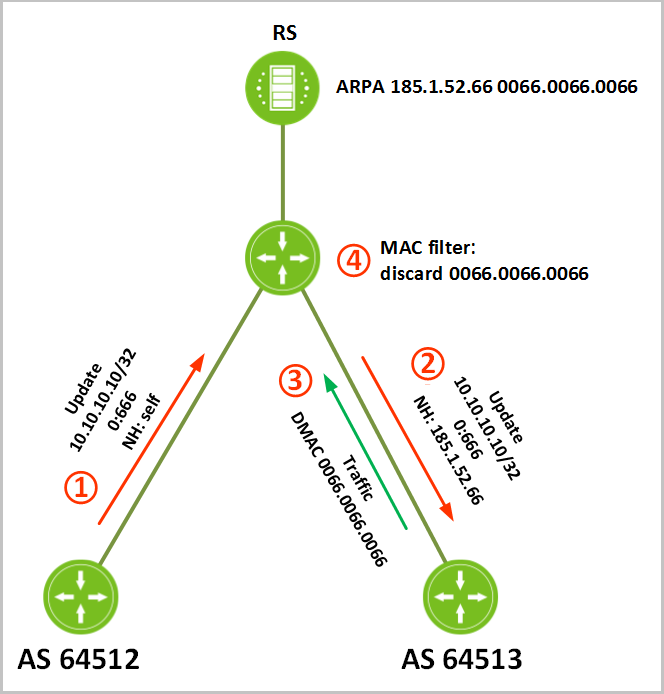
BGP Blackhole work scheme.
Looking glass
And of course, DataLine-IX has its own Looking Glass . Here you can see online:
- The state of BGP sessions for all participants.
UP - the session is established, Down - the session is not established, Start / Passive - the session is configured by the DataLine-IX, and we are waiting for the participant to send us a request to establish the session. - Detailed statistics on individual routes for IPv4 and IPv6.
- display AS PATH as a graph.
That's all we wanted to talk about DataLine-IX tools. Ask questions in the comments if something is left behind the scenes.
Source: https://habr.com/ru/post/317670/
All Articles