A critical vulnerability was found in the AirDroid application that allows for MitM attacks.

Information security specialists from Zimperium have analyzed the popular AirDroid application and found that there is a critical vulnerability. This is reported in their official blog .
AirDroid is a popular application for remote control of Android devices through a PC. The current audience of the program has at least 10 million people, and the total AirDroid has been downloaded more than 50 million times.
The vulnerability is related to the possibility of a MitM-attack , the consequence of which could be the leakage of personal data and even the installation of a third-party APK by an attacker on the Android device of the attacked user. In this case, the attack uses the built-in functionality AirDroid.
Data transfer using AirDroid occurs, including, via an unprotected HTTP channel. The data is encrypted by the application itself using DES , a symmetric encryption algorithm approved by IBM back in 1977. The problem is that the encryption key is hard-coded in the AirDroid code itself (890jklms is the key itself obtained by parsing).
')
Having an encryption key, an attacker can easily perform a MitM attack and, in fact, gain access to AirDroid, and through it, to the user's Android device.
By sending a packet encrypted with DES using the above key, the attacker will receive a response from AirDroid with all the device information, as well as an email and password hash, as demonstrated by Zimperium experts:

Responding to an attacker's request from AirDroid
Using this vulnerability, you can redirect requests for updates and slip a malicious APK package onto a user device, the installation of which will be approved by the user under the guise of receiving updates.
Another attacker can obtain statistical information that is collected by AirDroid and transmitted to the address
http://stat3.airdroid.com/ via an unprotected HTTP protocol (for API and most functions, the application still uses HTTPS). On this communication channel, everything is also used minimally secure DES (apparently, to provide at least some encryption). Intercepted by the MitM attack, the information after decryption is as follows: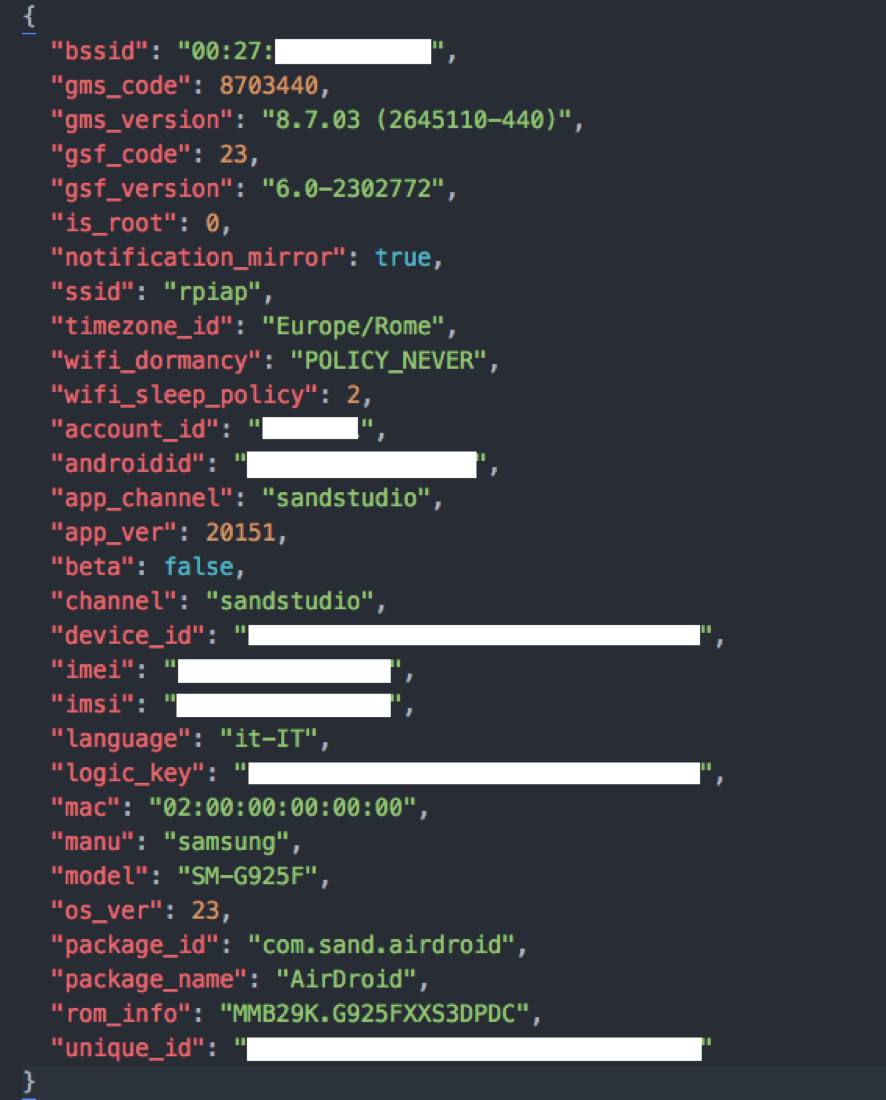
From important information, an attacker can get your
account_id , androidid , device_id , imei , imsi , logic_key and unique_id .Following the posting of vulnerability information on the Zimperium blog, the reaction of the AirDroid project management almost immediately followed. Here's how Betty Chen, marketing director, commented:
After posting to the Zimperium blog, we released an update for the AirDroid 4.0 mobile client. In this version, some fixes are made, but we are still waiting for full client optimization before we can improve encryption. We will begin to roll out the update on clients and servers over the next two weeks, as far as possible.
It should be noted that Zimperium is far from a Black Hat team. They transmitted information about the vulnerability to AirDroid more than six months ago, on May 24, 2016. In updates 4.0.0 (for November 28) and 4.0.1 (for November 30) and, respectively, in earlier versions, it was still present. We posted information about the threat in open access on December 1, 2016.
The current version of the application is 4.0.2, but there is still no information about whether the vulnerability was fixed. The latest entry in the official blog of the application announces the imminent release of version 4.0.0 and is dated November 18th.
Source: https://habr.com/ru/post/317152/
All Articles