Psychology in the service of information security. Tendency to crime
It is said that the best battle is that which was not. With regard to the problem of providing information security, one could say that the best leak is the one that did not happen. In order for this to become true, the security service needs to act proactively and be able to identify insiders even before they try to “merge” something. There are questions: how to put this into practice? Is it possible to identify the tendency to inside out in advance? Under the cut, I tried to give answers.
The idea of early identification of insiders did not arise from scratch. On the one hand, my colleague and I work in the training center of SearchInform and it is our direct responsibility to find various “suspicious” individuals. On the other hand, my colleague is a candidate of psychological sciences and for a long time was engaged in, let's say, recruitment for the needs of certain organizations. His achievements, in consequence, helped us a lot. But first it was necessary to decide what to base. Under the arm, the FBI and CIA joint review of information security problems for 2006 turned up, from which it followed that, as a matter of fact, an insider could be anyone:
It is clear that such an approach is too descriptive, and it’s not worthwhile to start from the profession / age / gender and other “socio-demographic” characteristics of the employee, suspecting him of belonging to insiders. bring us closer to the desired result.
As a result, in order to systematize “one and all,” it was decided to be guided by the ideas of Carl Gustav Jung, which formed the basis of the MBTI questionnaire.
')
The combination of human preferences for each scale allows you to select 16 different psychological types of personality, each of which for convenience is indicated by a formula that includes the names of the most pronounced poles.
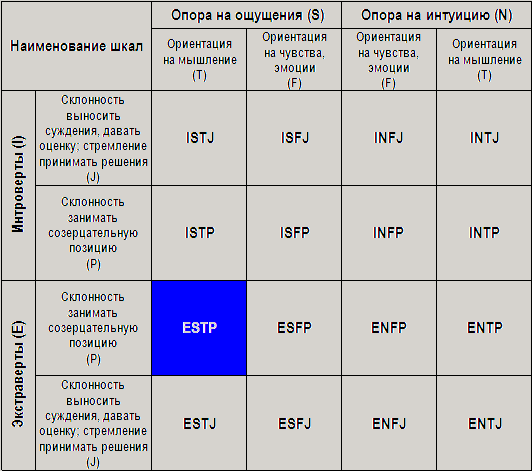
For example, ESTP is extroverted (E), preferring to receive information about the world through its senses (S), oriented to thinking (T), inclined to take a contemplative attitude (P). There are also “unofficial”, but rather capacious, reflecting everyday understanding, the totality of qualities that determine this or that type - “labels”. For example, ESTJ is an administrator, ISTJ is an inspector, ESTP is a marshal, ESFJ is an enthusiast, etc.
Of course, such a “label” cannot adequately replace the literal formula of the psychological type, and in some cases its excessively general nature completely ignores subtle differences and distorts the ideas about a person, however, these names are very tenacious and popular.
Preferences develop in a person at an early age, and subsequently he firmly adheres to them. And the more we use our preferences, both intentionally and unintentionally, the more confidently and willingly we will rely on them. This, of course, does not mean that from time to time we cannot use qualities that are not included in a number of preferences. On the contrary, the more mature a person becomes, the more rich and diverse such “non-priority” qualities make his life. At the same time, they are unable to replace preferences: for example, an extrovert will never become an introvert, and vice versa.
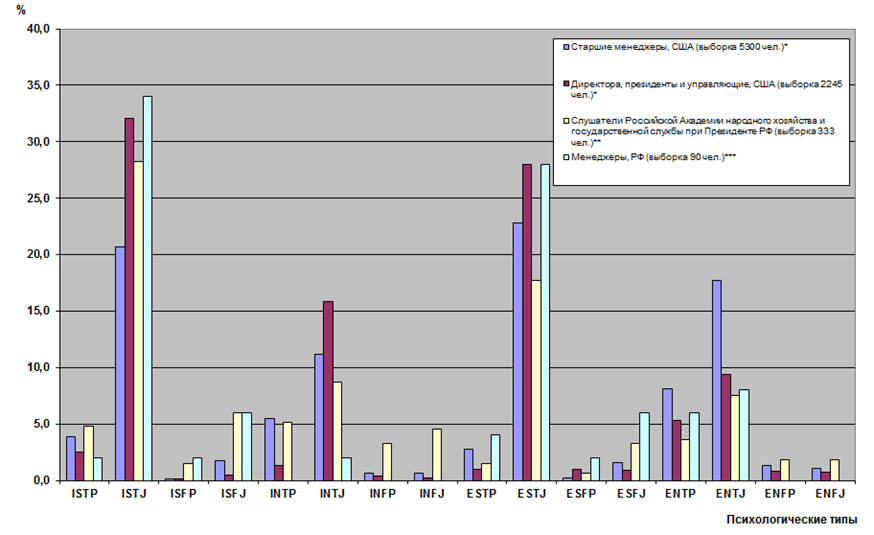
Moreover, according to the available data, belonging to one or another psychological type is closely connected with professional roles, status and other similar characteristics. For example, managers are usually “administrators” (ESTJ) or “inspectors” (ISTJ) and very rarely “lyricists” (INFP) (see figure below).
But if such a distribution exists for managers, it is logical to assume that there may be a similar distribution for insiders. In other words, people with one psychotype may be more prone to inside out than with another . An indirect confirmation of this idea can serve as the results of Eric Shaw and Harley Stock’s study “Behavioral risk indicators for identifying insider thefts of intellectual property”, which, in particular, describes the key behaviors inherent to insiders guilty of theft of intellectual property.
For each psychotype, there are both fairly complete descriptions and key characteristics. The more a person corresponds to them, the more clearly one or another psycho-type is expressed. But even a short list of characteristics allows us to draw conclusions about what a person may be capable of. Here is how, for example, the list of key characteristics of a person belonging to the psychological type of ESTP (“marshal”) or his alter ego to the socionic type of SLE (sensory-logical extrovert) looks like:
The content of paragraphs 8-10 (and some others) draws attention in the context of the conversation about ensuring information security. After analyzing all types from the point of view of their ethical and business qualities inherent in their carriers, my colleague and I identified the most “dangerous” ones, that is, those that imply a tendency to commit an insider.
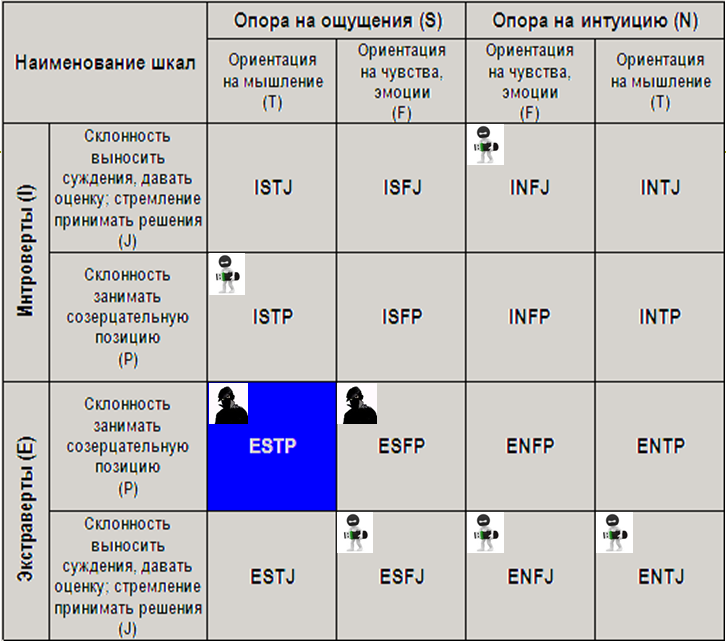
At the same time, the larger “intruder” figure (ESTP, ESFP) denotes a greater likelihood that a representative of this type will be an insider.
It remains "a trifle" - to determine the psycho types of employees. And here are a few questions:
As a method for identifying a psychological type, the already mentioned “Myers-Briggs Type Indicator” (MBTI) can be used, an adapted version of the Keirsey Temperament Sorter method of D. Kirsey can also be used, and the advocate of “socionic approach” Your socionic type "V. Gulenko. In practice, it is advisable to use the computer versions of these techniques, since there is no shortage of them either. As part of the post, a software product will be used to illustrate some of the provisions (the same ideas of colleagues that were useful) “The system of professional psychological testing”, which implements both these and some other psychological diagnostic tools. Slippers I will ask not to throw - this is not an advertisement of software, since It is not for sale (just own development).
So, from words to business. It was decided to test the theoretical reasoning in practice. Naturally, the first "experimental" were employees of their own department. Testing time for one candidate was about 30-40 minutes. The test results are shown in the figure (it is worth noting that only the “tip of the iceberg” is visible in the figure. A large amount of information is presented on the other tabs, but it will be superfluous to analyze it in this publication).
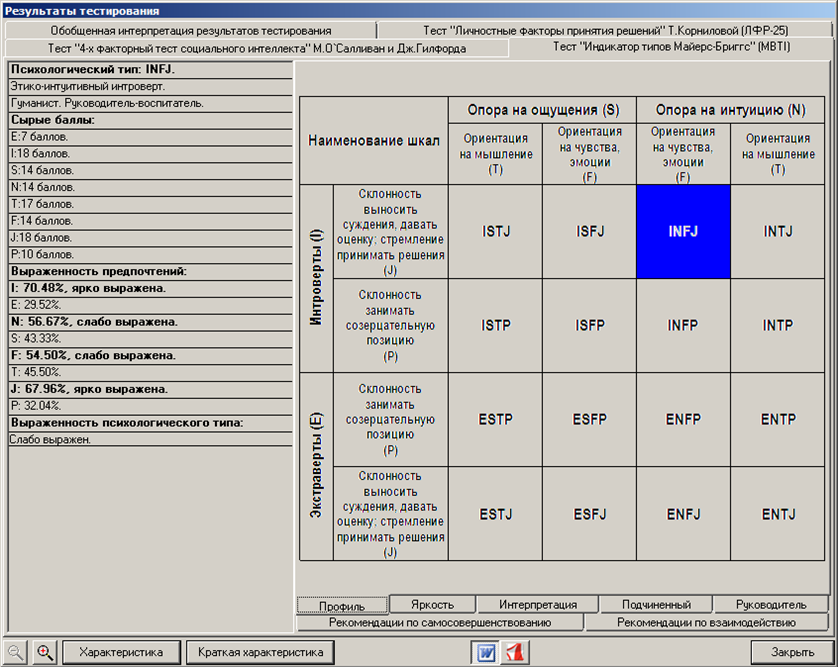
In addition to the most important result - a four-letter psychological type - it is imperative to pay attention to the severity of preferences, since the more pronounced the components of the psychotype, the more accurately the characteristic issued by the program will describe the person, and therefore, the more predictable will be his actions in a given situation.
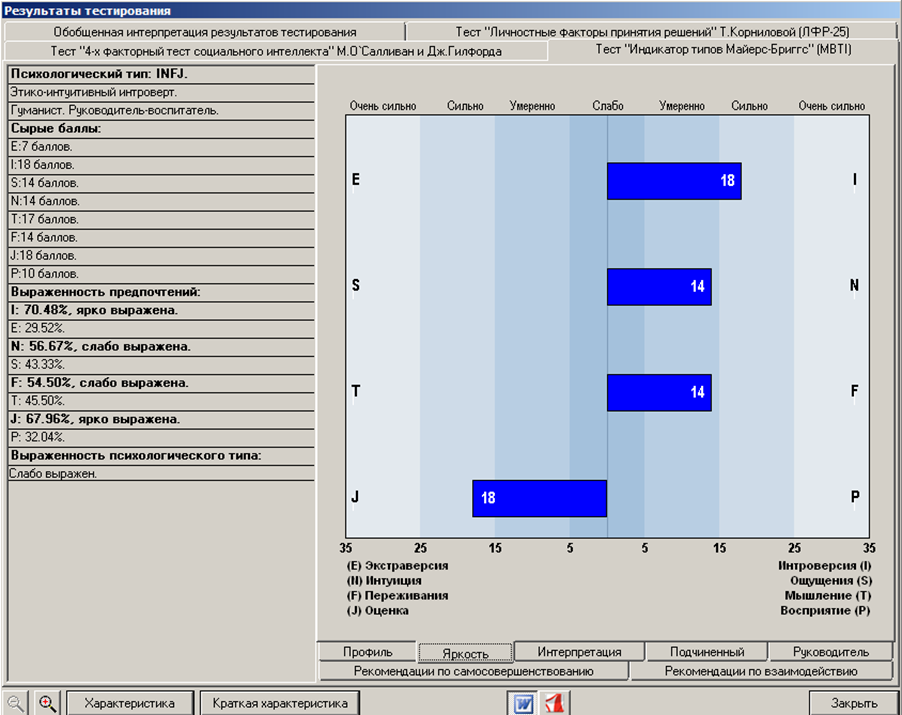
Alas, our employee was not lucky: he needs an eye and an eye :)
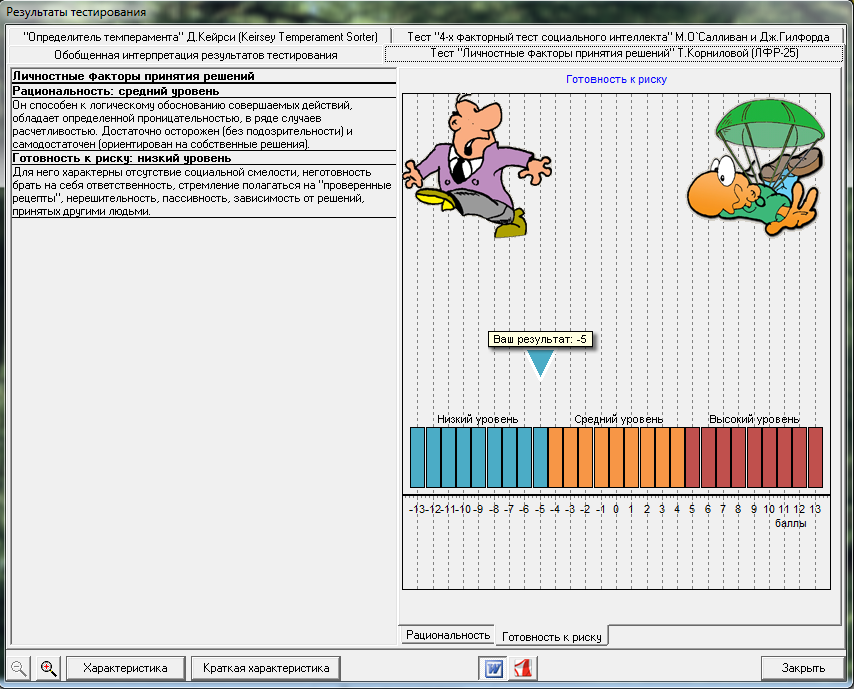
But the MBTI didn’t converge on the light. Therefore, for a more complete characterization, we decided not to limit ourselves to just one test, and as an “additional burden”, the test subject also had to pass a risk tolerance test (“Personality factors of decision making” by T. Kornilova) and a test for the level of social intelligence (“4 x factorial test of social intelligence M. O'Sullivan and J. Guilford).
The first defines two parameters: rationality and risk appetite. Most often they are antagonistic to each other. That is, the more a person is prone to one, the less prone to another. Insiders, as you know, tend to take risks.
A test for diagnosing social intelligence shows how the testee can “read” people, predict situations, interpret them correctly (and, consequently, “convert” them to their advantage).
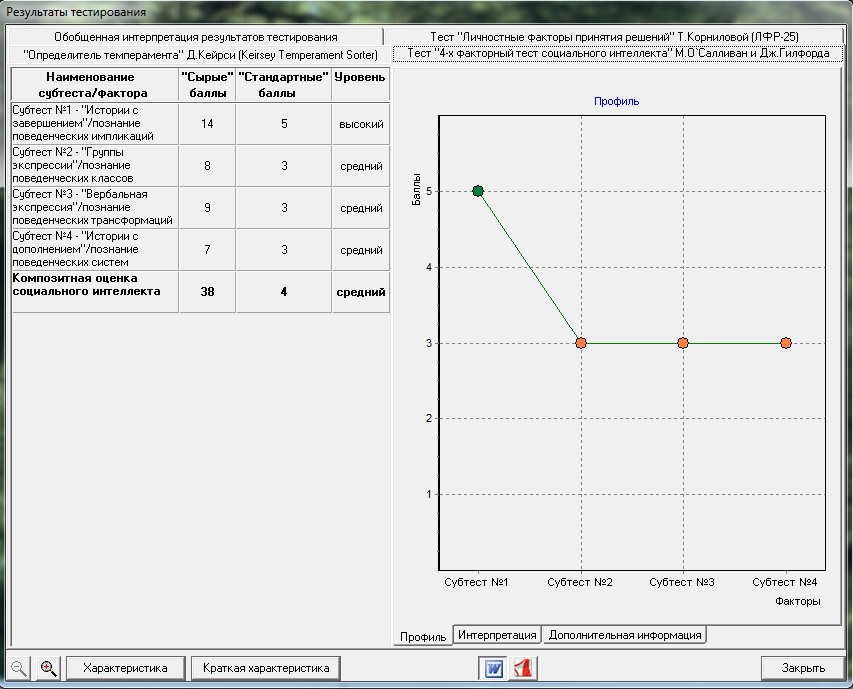
This parameter is also necessary to know, as many insiders are also “manipulators” (manipulate people to achieve their own goals).
In the test results, attention should be paid not so much to the interpretation, the profile and the “standard” points, but also to the “raw” points as well, since it is they that give a greater degree to judge the individual characteristics of the person being tested. You understand: an insider is a “commodity piece”.
Now it is time to answer the second question: who will do all this? Obviously, this should not be security officers ("do we have nothing more to do?"). The least suspicion will be caused by the HR department, so the "rough" work on testing can be entrusted to them. The information security service, in turn, will work with ready-made characteristics and identified psycho-types.
You can work on the following algorithm:
And finally, the third question: what to do with the results? Everything is quite simple here. If your employee is the owner of a pronounced psychological (socionic) type that is included in the “risk group”, then it is best to “look after” him.
As for the reliability of the results, there are no difficulties here either. The described approach is unlikely to completely replace the manager’s professional experience, expert evaluations, the results of using other methods of personality research. But on the other hand, such tests can compensate for the lack of sufficient professional experience of the above-mentioned persons, assist in the situation of the absence of experts and the inability to apply other methods.
Finally, I would like to note that the attempt to identify the potential inclination of the employee to inside out is not something out of the ordinary. Similar approaches are practiced in other "related" areas. For example, a well-founded method of psychological diagnosis of professional fitness for work in the law enforcement system began to be used more than 15 years ago in the Russian Federation.
One of the main documents regulating psychological testing in the legal practice of Russia is the “Guide to Professional Psychological Selection of Candidates for Service to the Prosecution Authorities of the Russian Federation”. This guide identifies five factors of professional suitability, including the corresponding complexes of professionally important qualities (PEC):
This article does not pretend to be the ultimate truth and is merely an attempt to put psychology on a “practical track” to ensure information security. With the right approach, you should at least use separate test suites specially designed for a particular industry (job category). But as they say, it is important to take the first step.
Questions and discussion in the comments are welcome.
PS If the community has an interest, in the following posts you can develop the topic of the fusion of psychology and information security.
Where is the firewood?
The idea of early identification of insiders did not arise from scratch. On the one hand, my colleague and I work in the training center of SearchInform and it is our direct responsibility to find various “suspicious” individuals. On the other hand, my colleague is a candidate of psychological sciences and for a long time was engaged in, let's say, recruitment for the needs of certain organizations. His achievements, in consequence, helped us a lot. But first it was necessary to decide what to base. Under the arm, the FBI and CIA joint review of information security problems for 2006 turned up, from which it followed that, as a matter of fact, an insider could be anyone:
- officer (civil or military);
- a contractor (for example, when engaging external organizations in performing work, including on a competitive basis);
- person working full time;
- part-time person;
- temporary worker;
- a user who has access to information through the network;
- colleague / partner (including foreign);
- employee of the state and municipal government;
- employee provider of information technology tools, systems and services.
It is clear that such an approach is too descriptive, and it’s not worthwhile to start from the profession / age / gender and other “socio-demographic” characteristics of the employee, suspecting him of belonging to insiders. bring us closer to the desired result.
As a result, in order to systematize “one and all,” it was decided to be guided by the ideas of Carl Gustav Jung, which formed the basis of the MBTI questionnaire.
')
Concept description with explanations and simplified examples
In the early 20s of the last century, this Swiss psychologist suggested that human behavior is not random, but predictable, and, therefore, classified. In his opinion, differences in behavior are determined by the basic mental functions inherent in a person throughout his life. In his work Psychological Types, Jung identified various psychological types of people in accordance with different individual ways of perceiving and evaluating information. In particular, he proposed three pairs of polar scales describing the mental processes of perception and information processing ( extraversion - introversion, sensation - intuition, thinking - emotion ).
A simplified example. You need to do any operation in the program, but you do not know how. Sitting next to a colleague who can give advice. The extrovert will ask for advice, the introvert will prefer not to disturb people and “climb” into a certificate or a search engine.
A simplified example. Freshly painted bench with the appropriate piece of paper with the inscription "Caution! Painted! Intuit "believe in the word," sensoric - pokes a finger.
A simplified example. The “mental” type of a person will say “I like him, because ...” (the arguments will be listed below). “Feeling” type will say “I like him and that's it!” I do not know why. ”
Young followers, Kathryn Briggs and Isabel Briggs-Myers, added another scale — evaluation — perception — and developed an MBTI questionnaire (Myers-Briggs Type Indicator) to diagnose a psychological personality type.
A simplified example. When discussing something, the “evaluating / decisive” type will prefer to express its own opinion on the issue rather than listen to the arguments of others. The “perceiving” type is the opposite: it will listen and can express its own considerations.
- The scale of "extraversion ( E ) - introversion" ( I ) describes the preferences of a person in relation to the sources of energy used. Jung proposed to distinguish between two basic attitudes of a person: the installation on the outside world, the world of the surrounding things (extraversion) and the installation on the inner world of one's own thoughts, experiences, ideas (introversion);
A simplified example. You need to do any operation in the program, but you do not know how. Sitting next to a colleague who can give advice. The extrovert will ask for advice, the introvert will prefer not to disturb people and “climb” into a certificate or a search engine.
- The scale “sensorics ( S ) - intuition ( N )” describes the human-preferred ways of collecting information. According to Jung, there are two different ways of perceiving reality: the path of sensations (sensation) and the path of intuition;
A simplified example. Freshly painted bench with the appropriate piece of paper with the inscription "Caution! Painted! Intuit "believe in the word," sensoric - pokes a finger.
- The scale “thinking ( T ) - emotions / feelings ( F )” describes the processes of making decisions by a person. The concept of Jung implies the existence of two basic preferences with regard to making any decisions or making judgments: a path based on logic, objective and impartial thinking and a path built on the basis of the subjective value system, personal preferences and feelings;
A simplified example. The “mental” type of a person will say “I like him, because ...” (the arguments will be listed below). “Feeling” type will say “I like him and that's it!” I do not know why. ”
Young followers, Kathryn Briggs and Isabel Briggs-Myers, added another scale — evaluation — perception — and developed an MBTI questionnaire (Myers-Briggs Type Indicator) to diagnose a psychological personality type.
- The scale “score ( J ) - perception ( P )” describes the preferred way of human interaction with the outside world. According to C. Briggs, there is another pair of installations: a setting for evaluating information and a setting for perceiving information. This pair determines which of the two functions - the function of gathering information or the function of making decisions - a person uses when communicating with the outside world.
A simplified example. When discussing something, the “evaluating / decisive” type will prefer to express its own opinion on the issue rather than listen to the arguments of others. The “perceiving” type is the opposite: it will listen and can express its own considerations.
The combination of human preferences for each scale allows you to select 16 different psychological types of personality, each of which for convenience is indicated by a formula that includes the names of the most pronounced poles.

For example, ESTP is extroverted (E), preferring to receive information about the world through its senses (S), oriented to thinking (T), inclined to take a contemplative attitude (P). There are also “unofficial”, but rather capacious, reflecting everyday understanding, the totality of qualities that determine this or that type - “labels”. For example, ESTJ is an administrator, ISTJ is an inspector, ESTP is a marshal, ESFJ is an enthusiast, etc.
Of course, such a “label” cannot adequately replace the literal formula of the psychological type, and in some cases its excessively general nature completely ignores subtle differences and distorts the ideas about a person, however, these names are very tenacious and popular.
Preferences develop in a person at an early age, and subsequently he firmly adheres to them. And the more we use our preferences, both intentionally and unintentionally, the more confidently and willingly we will rely on them. This, of course, does not mean that from time to time we cannot use qualities that are not included in a number of preferences. On the contrary, the more mature a person becomes, the more rich and diverse such “non-priority” qualities make his life. At the same time, they are unable to replace preferences: for example, an extrovert will never become an introvert, and vice versa.
Moreover, according to the available data, belonging to one or another psychological type is closely connected with professional roles, status and other similar characteristics. For example, managers are usually “administrators” (ESTJ) or “inspectors” (ISTJ) and very rarely “lyricists” (INFP) (see figure below).

Sources
* Kröger, O. Types of people and business / O. Kröger, J. M. Tuson - M .: Persey - Veche - AST, 1995. - 560 p.
** Menshikov, OR On the results of testing students of the Academy of National Economy in two tests: MBTI and Socionics / .R. Menshikov // Socionics. Collection of reports of the 4th Moscow Scientific Conference [Electronic resource]. - M., 2001. - Mode of access: socioniks.chat.ru/mens/sb_mens2.htm - Date of access: 12.03.2013.
*** Abelskaya, E.F. Typological study of the mental warehouse of personality: author. dis. ... Cand. psychol. Sciences: 19.00.01 / EF Abelian; Ural State. un-t them. A.M. Gorky - Ekaterinburg, 2006. - 27 p.
** Menshikov, OR On the results of testing students of the Academy of National Economy in two tests: MBTI and Socionics / .R. Menshikov // Socionics. Collection of reports of the 4th Moscow Scientific Conference [Electronic resource]. - M., 2001. - Mode of access: socioniks.chat.ru/mens/sb_mens2.htm - Date of access: 12.03.2013.
*** Abelskaya, E.F. Typological study of the mental warehouse of personality: author. dis. ... Cand. psychol. Sciences: 19.00.01 / EF Abelian; Ural State. un-t them. A.M. Gorky - Ekaterinburg, 2006. - 27 p.
But if such a distribution exists for managers, it is logical to assume that there may be a similar distribution for insiders. In other words, people with one psychotype may be more prone to inside out than with another . An indirect confirmation of this idea can serve as the results of Eric Shaw and Harley Stock’s study “Behavioral risk indicators for identifying insider thefts of intellectual property”, which, in particular, describes the key behaviors inherent to insiders guilty of theft of intellectual property.
For each psychotype, there are both fairly complete descriptions and key characteristics. The more a person corresponds to them, the more clearly one or another psycho-type is expressed. But even a short list of characteristics allows us to draw conclusions about what a person may be capable of. Here is how, for example, the list of key characteristics of a person belonging to the psychological type of ESTP (“marshal”) or his alter ego to the socionic type of SLE (sensory-logical extrovert) looks like:
- Well solves tactical problems.
- Hierarchical leader of a business orientation.
- The method of establishing contact is focused on objective indicators.
- The form of business activity is focused on the volitional overcoming of barriers and obstacles.
- The system of interaction with subordinates involves administrative control.
- Refers to competing behavior.
- Reaches major results in business activity without regard to human relationships.
- Prone to actively denying ethics in business. Believes that the end justifies the means.
- Motives and purpose: selfishness, careerist plans, the desire for success in life. Preoccupation with your own profits and the success of your company.
- Attitude towards the law: prone to criminal risk. If possible, tries to overcome legal barriers.
- Strategy: good orientation in the situation, focus on favorable opportunities for increasing profits.
The content of paragraphs 8-10 (and some others) draws attention in the context of the conversation about ensuring information security. After analyzing all types from the point of view of their ethical and business qualities inherent in their carriers, my colleague and I identified the most “dangerous” ones, that is, those that imply a tendency to commit an insider.

At the same time, the larger “intruder” figure (ESTP, ESFP) denotes a greater likelihood that a representative of this type will be an insider.
It remains "a trifle" - to determine the psycho types of employees. And here are a few questions:
- Which tool to use?
- Who will do this?
- What to do with the results?
As a method for identifying a psychological type, the already mentioned “Myers-Briggs Type Indicator” (MBTI) can be used, an adapted version of the Keirsey Temperament Sorter method of D. Kirsey can also be used, and the advocate of “socionic approach” Your socionic type "V. Gulenko. In practice, it is advisable to use the computer versions of these techniques, since there is no shortage of them either. As part of the post, a software product will be used to illustrate some of the provisions (the same ideas of colleagues that were useful) “The system of professional psychological testing”, which implements both these and some other psychological diagnostic tools. Slippers I will ask not to throw - this is not an advertisement of software, since It is not for sale (just own development).
Practice
So, from words to business. It was decided to test the theoretical reasoning in practice. Naturally, the first "experimental" were employees of their own department. Testing time for one candidate was about 30-40 minutes. The test results are shown in the figure (it is worth noting that only the “tip of the iceberg” is visible in the figure. A large amount of information is presented on the other tabs, but it will be superfluous to analyze it in this publication).

In addition to the most important result - a four-letter psychological type - it is imperative to pay attention to the severity of preferences, since the more pronounced the components of the psychotype, the more accurately the characteristic issued by the program will describe the person, and therefore, the more predictable will be his actions in a given situation.

Alas, our employee was not lucky: he needs an eye and an eye :)
But the MBTI didn’t converge on the light. Therefore, for a more complete characterization, we decided not to limit ourselves to just one test, and as an “additional burden”, the test subject also had to pass a risk tolerance test (“Personality factors of decision making” by T. Kornilova) and a test for the level of social intelligence (“4 x factorial test of social intelligence M. O'Sullivan and J. Guilford).
The first defines two parameters: rationality and risk appetite. Most often they are antagonistic to each other. That is, the more a person is prone to one, the less prone to another. Insiders, as you know, tend to take risks.

A test for diagnosing social intelligence shows how the testee can “read” people, predict situations, interpret them correctly (and, consequently, “convert” them to their advantage).

This parameter is also necessary to know, as many insiders are also “manipulators” (manipulate people to achieve their own goals).
In the test results, attention should be paid not so much to the interpretation, the profile and the “standard” points, but also to the “raw” points as well, since it is they that give a greater degree to judge the individual characteristics of the person being tested. You understand: an insider is a “commodity piece”.
Now it is time to answer the second question: who will do all this? Obviously, this should not be security officers ("do we have nothing more to do?"). The least suspicion will be caused by the HR department, so the "rough" work on testing can be entrusted to them. The information security service, in turn, will work with ready-made characteristics and identified psycho-types.
You can work on the following algorithm:
- HR service “chases” an employee according to a certain set of tests.
- Information is transmitted to the information security service.
- Knowing what type an employee belongs to, the specialist in the field of information security determines his potential propensity for insider trading (not only key characteristics of the psychotype should be taken into account, but also other variables: severity of preferences, risk appetite, level of social intelligence).
And finally, the third question: what to do with the results? Everything is quite simple here. If your employee is the owner of a pronounced psychological (socionic) type that is included in the “risk group”, then it is best to “look after” him.
As for the reliability of the results, there are no difficulties here either. The described approach is unlikely to completely replace the manager’s professional experience, expert evaluations, the results of using other methods of personality research. But on the other hand, such tests can compensate for the lack of sufficient professional experience of the above-mentioned persons, assist in the situation of the absence of experts and the inability to apply other methods.
findings
Finally, I would like to note that the attempt to identify the potential inclination of the employee to inside out is not something out of the ordinary. Similar approaches are practiced in other "related" areas. For example, a well-founded method of psychological diagnosis of professional fitness for work in the law enforcement system began to be used more than 15 years ago in the Russian Federation.
One of the main documents regulating psychological testing in the legal practice of Russia is the “Guide to Professional Psychological Selection of Candidates for Service to the Prosecution Authorities of the Russian Federation”. This guide identifies five factors of professional suitability, including the corresponding complexes of professionally important qualities (PEC):
- required level of social (professional adaptation);
- sufficient psychological stability (emotional);
- high level of intellectual development, cognitive activity;
- communicative activity and competence;
- adequate organizational skills.
This article does not pretend to be the ultimate truth and is merely an attempt to put psychology on a “practical track” to ensure information security. With the right approach, you should at least use separate test suites specially designed for a particular industry (job category). But as they say, it is important to take the first step.
Questions and discussion in the comments are welcome.
PS If the community has an interest, in the following posts you can develop the topic of the fusion of psychology and information security.
Source: https://habr.com/ru/post/317066/
All Articles